搭建一个springboot工程测试md5加密
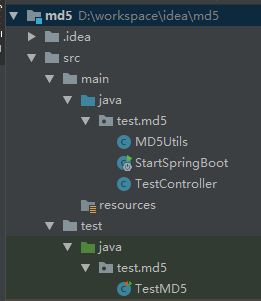
1、展示搭建本次测试所用的springboot工程结构
其中,TestController模拟的是服务端接收post请求,TestMD5模拟的是客户端使用单元测试发送http请求
2、展示pom.xml文件
4.0.0
com.csii.test
md5
1.0-SNAPSHOT
org.springframework.boot
spring-boot-starter-parent
1.5.2.RELEASE
UTF-8
UTF-8
1.8
org.springframework.boot
spring-boot-starter-test
test
org.springframework.boot
spring-boot-starter-web
org.apache.httpcomponents
httpclient
4.5.2
3、StartSpringBoot为常规的启动类
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
@SpringBootApplication
public class StartSpringBoot {
public static void main(String[] args) {
SpringApplication.run(StartSpringBoot.class, args);
}
}4、MD5工具类
import java.security.MessageDigest;
public class MD5Utils {
public static String strMD5ByUTF8(String originString){
if (originString != null) {
try {
MessageDigest md= MessageDigest.getInstance("MD5");
byte[] results=md.digest(originString.getBytes("UTF-8"));
String resultString=byteArrayToHexString(results);
return resultString.toUpperCase();
} catch (Exception e) {
e.printStackTrace();
}
}
return null;
}
private static String byteArrayToHexString(byte[] b) {
StringBuffer resultSb=new StringBuffer();
for (int i = 0; i < b.length; i ++){
resultSb.append(byteToHexString(b[i]));
}
return resultSb.toString();
}
private static String byteToHexString(byte b) {
int n=b;
if(n<0){
n=256+n;
}
int d1=n/16;
int d2=n%16;
return hexDigits[d1]+hexDigits[d2];
}
private final static String[] hexDigits={"0","1","2","3","4","5","6","7","8","9","a","b","c","d","e","f"};
}5、TestMD5采用的是httpclient对象来向服务端发送post请求
import org.apache.http.client.methods.CloseableHttpResponse;
import org.apache.http.client.methods.HttpPost;
import org.apache.http.entity.StringEntity;
import org.apache.http.impl.client.CloseableHttpClient;
import org.apache.http.impl.client.HttpClientBuilder;
import org.junit.Test;
import java.io.IOException;
public class TestMD5 {
@Test
public void sendMD5Data(){
CloseableHttpClient httpClient = HttpClientBuilder.create().build();
CloseableHttpResponse response = null;
try {
// 创建Post请求
String sendUrl = "http://localhost:8080/testMD5";
HttpPost httpPost = new HttpPost(sendUrl);
// 处理MD5加密分别获取到明文串和密文串
String plainText = "testMD5"; // 明文串
String key = "key"; // 秘钥
String keyPlainText = key + plainText; // 组装成要加密的串
MD5Utils md5Utils = new MD5Utils();
String cipherText = md5Utils.strMD5ByUTF8(keyPlainText); // 密文串
System.out.println("客户端本次上送的明文串为:" + plainText + ",本次上送的密文串为:" + cipherText);
// 将原明文串放入请求体中
StringEntity entity = new StringEntity(plainText, "UTF-8");
httpPost.setEntity(entity);
// 设置ContentType
httpPost.setHeader("Content-Type", "text/html;charset=utf8");
// 将密文串放入到请求头中
httpPost.setHeader("sign", cipherText);
// 发送post请求
response = httpClient.execute(httpPost);
System.out.println("获取响应状态为:" + response.getStatusLine());
} catch (Exception e) {
e.printStackTrace();
} finally {
try {
// 释放资源
if (httpClient != null) {
httpClient.close();
}
if (response != null) {
response.close();
}
} catch (IOException e) {
e.printStackTrace();
}
}
}
}6、TestController模拟的是服务端接收请求
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.*;
import javax.servlet.http.HttpServletRequest;
@Controller
public class TestController {
@RequestMapping(value = "testMD5", method = RequestMethod.POST)
@ResponseBody
public void test(HttpServletRequest request, @RequestBody String plainText){
// 从请求头中获取签名串
String sign = request.getHeader("sign");
System.out.println("服务端本次获取的明文串为:" + plainText + ",本次上送的密文串为:" + sign);
// 约定的秘钥
String key = "key";
// 组装成待加密的串
String keyPlainText = key + plainText;
// 将keyPlainText进行MD5加密
MD5Utils md5Utils = new MD5Utils();
String cipherText = md5Utils.strMD5ByUTF8(keyPlainText); // 密文串
// 将再次MD5加密后获得的密文串与上送的密文串做比较,如果完全一致,则证明此次传输数据成功
boolean result = sign.equals(cipherText);
System.out.println("此次传输数据结果:" + result);
}
}7、执行顺序,先执行StartSpringBoot将项目启动起来,然后再run TestMD5类
TestMD5的控制台打印结果,打印比较多,我只展示了本次需要的日志
客户端本次上送的明文串为:testMD5,本次上送的密文串为:B5B94ED2D2D375450196E6DC5AB9DE69
获取响应状态为:HTTP/1.1 200服务器端展示结果:
服务端本次获取的明文串为:testMD5,本次上送的密文串为:B5B94ED2D2D375450196E6DC5AB9DE69
此次传输数据结果:true可以发现本次两次MD5之后得到的串是一致的,证明本次传输数据成功,没有被篡改。