- windows docker-02-docker 最常用的命令汇总
老马啸西风
Docker容器学习实战笔记dockereureka容器ubuntumavenlinux运维
一、镜像管理命令说明常用参数示例dockerpull:拉取镜像dockerpullnginx:latestdockerimages查看本地镜像dockerimages-a(含中间层镜像)dockerrmi删除镜像dockerrmi-f$(dockerimages-q)(强制删除所有镜像)dockerbuild-t.构建镜像dockerbuild-tmyapp:v1-fDockerfile.prod
- Dockerfile 完全指南:从入门到精通
赵大仁
nodejs运维技术docker运维服务器node.js
Dockerfile完全指南:从入门到精通一、什么是Dockerfile?Dockerfile是一个文本文件,包含了一系列构建Docker镜像的指令。通过Dockerfile,开发者可以将应用程序的构建过程标准化、自动化,确保在任何环境中都能生成一致的镜像。使用Dockerfile构建镜像的核心优势:可重复性:相同的Dockerfile在任何环境下都能生成相同的镜像可维护性:以代码形式管理镜像构建
- Docker-compose:服务编排
Docker-compose介绍服务编排:按照一定的业务规则批量管理容器在微服务架构的应用系统中,一般包含N个微服务,且每个微服务一般都会部署多个实例。此时,如果每个微服务都要手动启停,维护的工作量会很大。要从Dockerfilebuildimage或者去dockerhub拉取image要创建多个container要管理这些container(启动/停止/删除)...Docker-composeD
- Docker 安装、常用命令、应用部署
Docker安装Docker可支持在Mac、Windows、Linux系统上安装,但是在Windows系统中Docker的安装包目前仅有win10专业版和企业版的。win10家庭版可以采用开启Hyper-V伪装成专业版绕过安装检测。还有一种方式是通过Dockertoolbox来安装(适用于win7/win8/win10家庭版),下载地址:docker-toolbox-windows-docker-
- 高阶知识库搭建实战五、(向量数据库Milvus安装)
伯牙碎琴
大模型数据库milvus大模型AI
以下是关于在Windows环境下直接搭建Milvus向量数据库的教程:本教程分两部分,第一部分是基于docker安装,在Windows环境下直接安装Milvus向量数据库,目前官方推荐的方式是通过Docker进行部署,因为Milvus的运行环境依赖于Linux系统。如果你希望在Windows上直接运行Milvus,可以考虑使用MilvusLite版本,这是一个轻量级的Python库,适用于快速原型
- 解决报错Error response from daemon: Get https://registry-1.docker.io/v2/: net/http: TLS handshaketimeout
[root@localhost/]#sudodockerpullubuntuErrorresponsefromdaemon:Gethttps://registry-1.docker.io/v2/library/ubuntu/manifests/2.04:Gethttps://auth.docker.io/token?scope=repository%3Alibrary%2Fubuntu%3Apul
- docker-compose部署java项目
小瞿慢慢跑
dockerdocker-compose
docker-compose是定义和运行多容器的工具。换句话说就是通过配置yml文件来运行容器,简化了每次输入dockerrun等命令,把这些命令配置在yml文件统一管理,而且可以用一个yml文件一次启动多个容器,启动时还可以设置各个容器的依赖关系等。如下为测试docker-compose启动java程序1.docker-compose.ymlversion:'3'services:java05:
- python docker
阿狸的家
SDNdocker
我们的开发人员和布署人员经常因环境问题,而使得安装过程困难重重,相比于虚拟机较少硬件资源的虚拟化,同时不需要加载虚拟机操作系统的耗时,因为docker共享宿主机的操作系统Centos和Ubunta共用内核kernel即bootfs相同,但是加载内核的rootfs不同,即文件的结构目录不同docker三要素docker可以看作为一个小型的linux系统,部署时秒级启动镜像:模板(应用程序代码),一个
- 【Java代码审计 | 第五篇】XSS漏洞成因+实战案例
秋说
Java代码审计javaxss
未经许可,不得转载。文章目录XSS漏洞成因1、直接输出用户输入2、在JSP中使用EL表达式输出用户输入3、在Thymeleaf模板中输出用户输入4、在JavaScript中嵌入用户输入实战案例案例1案例2案例3XSSXSS(跨站脚本攻击,Cross-SiteScripting)是一种常见的Web安全漏洞,攻击者通过在网页中注入恶意脚本,使得这些脚本在用户的浏览器中执行。XSS攻击通常分为以下三种类
- 企业SRC漏铜挖掘思路
网络小安
漏洞挖掘网络安全web安全安全
目录src众测平台信息收集一,先看股权穿透图找到公司的名称二,这些公司对应的是一级域名三,用icp备案进行查找域名域名资产开始挖(抓包拦截)抓包分析js逆向src众测平台国内漏洞平台https://www.anquanke.com/src教育edu漏洞平台https://src.sjtu.edu.cn/提示:记得查看企业SRC的安全漏洞评分标准以及规范edu只打边缘拿证书信息收集爱企查一,先看股权
- docker容器中连接宿主机mysql数据库
最近要在docker中使用mysql数据库,首先考虑在ubuntu的镜像中安装mysql,这样的脚本和数据库都在容器中,直接访问localhost:3306,脚本很简单,如下:importpymysql#建立数据库连接db=pymysql.connect(port=3306,host="localhost",user="root",password="password",database="my_
- Docker环境搭建与使用:docker容器连接
@李思成
大数据docker后端linuxhadoop
文章目录Docker容器连接1网络端口映射2Docker容器互联2.1创建容器时起命名2.2新建网络2.3运行两个容器并连接到新建的`test-net`网络3配置DNS3.1设置全部容器的`DNS`3.2手动指定容器的配置Docker容器连接1网络端口映射上例中实现了通过网络端口来访问运行在docker容器内的服务。容器中可以运行某些网络应用,要让外部也可以访问这些应用,可以通过run命令的-p参
- docker容器连接Android设备,通过ADB连接到Docker容器中的USB Android设备
黄文瀚
我创建了一个包含AndroidSDK的Docker镜像,并试图在运行此图像的容器中公开我的Android手机.所以我使用了–privileged标志并安装了USB设备,如下所示:$dockerrun--privileged-v/dev/bus/usb:/dev/bus/usb-d-Pmy-android:0.0.1但是,当我运行ADB设备时,它没有显示USB设备:ubuntu@d56b666be4
- 【PostgreSQL】【第1章】入门&安装
cherry5230
数据库专栏postgresql数据库
1-PostgreSQL入门&安装1.今日安排核心内容:PostgreSQL简介与适用场景PostgreSQLvsMySQL核心差异Linux环境安装(非Docker)远程连接与日志配置基本操作:用户、数据库、权限管理2.PostgreSQL介绍2.1核心特性开源协议:基于BSD/MIT协议,支持二次封装商业化。版本选择:稳定版:12.x新特性版:14.x社区活跃:版本迭代快(约3个月一次),Bu
- buntu 22.04 上离线安装Docker 25.0.5(二)
努力一点948
底层ubuntu系统入门docker容器运维人工智能linux服务器gpu算力
以下有免费的4090云主机提供ubuntu22.04系统的其他入门实践操作地址:星宇科技|GPU服务器高性能云主机云服务器-登录相关兑换码星宇社区---4090算力卡免费体验、共享开发社区-CSDN博客兑换码要是过期了,可以私信我获取最新兑换码!!!之所以推荐给大家使用,是因为上面的云主机目前是免费使用的,不需要大家再去安装虚拟机,部署虚拟机,环境都搭配好了,非常适合新手入门,减少搭建的时间,把时
- Docker安装Elasticsearch 7.17.0和Kibana 7.17.0并配置基础安全
1.准备工作确保已安装Docker并启动服务创建必要的目录结构:mkdir-p/opt/es/{config,data,plugins}mkdir-p/opt/kibana/configchmod-R777/opt/es/opt/kibana2.安装Elasticsearch拉取镜像:dockerpullelasticsearch:7.17.0创建配置文件/opt/es/config/elasti
- 如何安全使用人工智能大模型
人工智能大模型的安全漏洞在推送,你只要有不一样的解决方案他就会通过学习学会,在别人讨论相同问题时,就会作为解决问题的推荐方案。这种机制是没办法防的。鉴于此我们只能采取如下措施:1.绝对本地部署,就是部署好以后断网,因为你使用时他还是会手机数据往后台传送,我本地部署的大模型在推理时看性能,网络也是有数据流的。也不知道在交换什么。2.既然搞不清楚那就彻底不相信,断网。那么我们要加快进度,快速完成任务,
- Dify丝滑云或本地docker部署步骤 适用Linux & macOS
neon98
大模型前端docker容器aimacoslinux人工智能
服务器必须有超过4GB的内存!!!Step1:gitclonegitclonehttps://githubfast.com/langgenius/dify.git//从GitHub服务器直接克隆可能会失败。其他GitHub镜像也可以。Step2:docker登录dockerloginghcr.io-u[yourusername]-p[yourGitHubaccesstoken]//此命令用自己的的
- docker磁盘空间不足解决办法
win_zcj
dockereureka容器
摘抄自:https://www.cnblogs.com/jun-zhou/p/15086657.html说明:用yuminstalldocker安装的docker默认安装目录在/var/lib/docker/,/var目录很小,需要改换更大的磁盘空间存储1.查看docker镜像存放目录空间大小du-hs/var/lib/docker/2.停止docker服务。systemctlstopdocker
- 阿里云ssl证书自动安装及续订(acme)
cherishSpring
nginxlinux#docker容器阿里云ssl数据库
- docker命令
cherishSpring
#docker容器dockerjavaeureka
目录1、常用命令2、容器生命周期管理创建一个新容器并运行一个命令杀掉一个运行中的容器删除一个或多个容器3、容器操作列出容器获取容器/镜像的元数据从服务器获取实时事件将文件系统作为一个tar归档文件导出到STDOUT4、容器rootfs命令从容器创建一个新的镜像检查容器里文件结构的更改容器与主机之间的数据拷贝5、镜像仓库登陆到Docker镜像仓库登出Docker镜像仓库从镜像仓库中拉取或者更新指定镜
- Linux部署Milvus数据库及Attu UI工具完全指南
一、准备工作1.1环境要求操作系统:Ubuntu20.04/Debian11/CentOS7+硬件配置:至少8GB内存,4核CPU,50GB磁盘空间网络要求:可访问互联网(用于拉取Docker镜像)1.2安装Docker和DockerCompose1.2.1安装Dockersudoapt-getupdatesudoapt-getinstall-ydocker.iosudosystemctlstar
- ABP VNext + Kubernetes & Istio:微服务网格实战指南
ABPVNext+Kubernetes&Istio:微服务网格实战指南目录ABPVNext+Kubernetes&Istio:微服务网格实战指南一、引言二、环境与依赖️三、项目与基础部署3.1生成Kubernetes资源3.2构建Docker镜像3.3HelmChart目录结构与参数注入四、安装Istio&定义入口五、Mermaid全链路流程概览六、将服务注入IstioMesh七、流量管理与金丝雀
- Docker HAproxy 配置 & rsyslog 日志处理
环境CentOSLinuxrelease7.9.2009(Core)HAProxyversion2.3.6-7851701,released2021/03/03IP:192.168.0.1Docker安装Docker安装建立haproxy配置文件#新建目录mkdir-p/etc/haproxy#备份配置文件cp/etc/haproxy/haproxy.cfg/etc/haproxy/haproxy
- .NET CORE 分布式事务(四) CAP实现最终一致性
精神小伙就是猛
.netcore分布式架构微服务
目录引言:1.0最终一致性介绍2.0CAP2.0架构预览3.0.NETCORE结合CAP实现最终一致性分布式事务3.1准备工作(数据库,本文使用的是MySql)3.1.1数据模型3.1.2DbContext3.1.3数据库最终生成3.2Nuget引入3.3appsettings.json3.4docker启动一个RabbitMQ3.5Program.cs3.6用户1API控制器3.7用户2API控
- Docker:DockerHub 与 私有仓库Registry
聪明的奇瑞
一个完整的系统可能包含上百个微服务,可能对应着上百个镜像,如果考虑到微服务的版本则会构建更多的镜像,那么这些镜像该如何管理呢?使用DockerHub镜像管理DockerHub是Docker官方维护的DockerRegistry,上面存放着很多优秀的镜像,只需注册一个DockerHub账号就可以使用了通过dockerlogin命令登录DockerHub,并按提示输入账号密码#DockerHub该网站
- 绝佳组合 SpringBoot + Lua + Redis = 王炸!
Java精选面试题(微信小程序):5000+道面试题和选择题,真实面经,简历模版,包含Java基础、并发、JVM、线程、MQ系列、Redis、Spring系列、Elasticsearch、Docker、K8s、Flink、Spark、架构设计、大厂真题等,在线随时刷题!前言曾经有一位魔术师,他擅长将SpringBoot和Redis这两个强大的工具结合成一种令人惊叹的组合。他的魔法武器是Redis的
- Microsoft 紧急修补 SharePoint 远程代码执行漏洞,应对持续网络攻击
微软紧急修复SharePoint高危漏洞并提供安全建议周日,微软发布了一个关键补丁,用于修复SharePoint中正在被恶意利用的安全漏洞,同时公布了另一个已通过"增强防护措施"修复的漏洞细节。这家科技巨头确认,目前已发现攻击者正针对本地部署的SharePointServer用户发起攻击,利用的是7月安全更新中未完全修复的漏洞。漏洞详情当前被利用的漏洞编号为CVE-2025-53770(CVSS评
- C#程序唯一性守护:用互斥锁(Mutex)实现进程级安全控制的实战指南
为什么程序重复启动是个"毒瘤"?在软件开发中,程序重复启动可能导致以下灾难性后果:资源冲突:多个实例争夺数据库连接、文件句柄等有限资源数据污染:并发写入配置文件导致内容错乱界面混乱:多个窗口同时弹出,用户体验崩坏安全漏洞:恶意程序通过伪造实例窃取数据而互斥锁(Mutex)是Windows/Linux系统提供的原生机制,能完美解决这些问题。相比文件锁、注册表标记等传统方案,Mutex具有以下不可替代
- Docker 部署的 GitLab备份和恢复
码上有约
经验分享dockergitlabeureka
Docker部署的GitLab备份和恢复数据使用Docker部署的GitLab可以通过Docker命令来进行备份和恢复。以下是具体步骤:1.停止GitLab容器在进行备份之前,最好先停止GitLab容器以确保数据一致性:dockerstop2.创建备份启动GitLab容器并执行备份命令:dockerexec-tgitlab-backupcreate备份文件将存储在GitLab容器内的/var/op
- iOS http封装
374016526
ios服务器交互http网络请求
程序开发避免不了与服务器的交互,这里打包了一个自己写的http交互库。希望可以帮到大家。
内置一个basehttp,当我们创建自己的service可以继承实现。
KuroAppBaseHttp *baseHttp = [[KuroAppBaseHttp alloc] init];
[baseHttp setDelegate:self];
[baseHttp
- lolcat :一个在 Linux 终端中输出彩虹特效的命令行工具
brotherlamp
linuxlinux教程linux视频linux自学linux资料
那些相信 Linux 命令行是单调无聊且没有任何乐趣的人们,你们错了,这里有一些有关 Linux 的文章,它们展示着 Linux 是如何的有趣和“淘气” 。
在本文中,我将讨论一个名为“lolcat”的小工具 – 它可以在终端中生成彩虹般的颜色。
何为 lolcat ?
Lolcat 是一个针对 Linux,BSD 和 OSX 平台的工具,它类似于 cat 命令,并为 cat
- MongoDB索引管理(1)——[九]
eksliang
mongodbMongoDB管理索引
转载请出自出处:http://eksliang.iteye.com/blog/2178427 一、概述
数据库的索引与书籍的索引类似,有了索引就不需要翻转整本书。数据库的索引跟这个原理一样,首先在索引中找,在索引中找到条目以后,就可以直接跳转到目标文档的位置,从而使查询速度提高几个数据量级。
不使用索引的查询称
- Informatica参数及变量
18289753290
Informatica参数变量
下面是本人通俗的理解,如有不对之处,希望指正 info参数的设置:在info中用到的参数都在server的专门的配置文件中(最好以parma)结尾 下面的GLOBAl就是全局的,$开头的是系统级变量,$$开头的变量是自定义变量。如果是在session中或者mapping中用到的变量就是局部变量,那就把global换成对应的session或者mapping名字。
[GLOBAL] $Par
- python 解析unicode字符串为utf8编码字符串
酷的飞上天空
unicode
php返回的json字符串如果包含中文,则会被转换成\uxx格式的unicode编码字符串返回。
在浏览器中能正常识别这种编码,但是后台程序却不能识别,直接输出显示的是\uxx的字符,并未进行转码。
转换方式如下
>>> import json
>>> q = '{"text":"\u4
- Hibernate的总结
永夜-极光
Hibernate
1.hibernate的作用,简化对数据库的编码,使开发人员不必再与复杂的sql语句打交道
做项目大部分都需要用JAVA来链接数据库,比如你要做一个会员注册的 页面,那么 获取到用户填写的 基本信后,你要把这些基本信息存入数据库对应的表中,不用hibernate还有mybatis之类的框架,都不用的话就得用JDBC,也就是JAVA自己的,用这个东西你要写很多的代码,比如保存注册信
- SyntaxError: Non-UTF-8 code starting with '\xc4'
随便小屋
python
刚开始看一下Python语言,传说听强大的,但我感觉还是没Java强吧!
写Hello World的时候就遇到一个问题,在Eclipse中写的,代码如下
'''
Created on 2014年10月27日
@author: Logic
'''
print("Hello World!");
运行结果
SyntaxError: Non-UTF-8
- 学会敬酒礼仪 不做酒席菜鸟
aijuans
菜鸟
俗话说,酒是越喝越厚,但在酒桌上也有很多学问讲究,以下总结了一些酒桌上的你不得不注意的小细节。
细节一:领导相互喝完才轮到自己敬酒。敬酒一定要站起来,双手举杯。
细节二:可以多人敬一人,决不可一人敬多人,除非你是领导。
细节三:自己敬别人,如果不碰杯,自己喝多少可视乎情况而定,比如对方酒量,对方喝酒态度,切不可比对方喝得少,要知道是自己敬人。
细节四:自己敬别人,如果碰杯,一
- 《创新者的基因》读书笔记
aoyouzi
读书笔记《创新者的基因》
创新者的基因
创新者的“基因”,即最具创意的企业家具备的五种“发现技能”:联想,观察,实验,发问,建立人脉。
第一部分破坏性创新,从你开始
第一章破坏性创新者的基因
如何获得启示:
发现以下的因素起到了催化剂的作用:(1) -个挑战现状的问题;(2)对某项技术、某个公司或顾客的观察;(3) -次尝试新鲜事物的经验或实验;(4)与某人进行了一次交谈,为他点醒
- 表单验证技术
百合不是茶
JavaScriptDOM对象String对象事件
js最主要的功能就是验证表单,下面是我对表单验证的一些理解,贴出来与大家交流交流 ,数显我们要知道表单验证需要的技术点, String对象,事件,函数
一:String对象;通常是对字符串的操作;
1,String的属性;
字符串.length;表示该字符串的长度;
var str= "java"
- web.xml配置详解之context-param
bijian1013
javaservletweb.xmlcontext-param
一.格式定义:
<context-param>
<param-name>contextConfigLocation</param-name>
<param-value>contextConfigLocationValue></param-value>
</context-param>
作用:该元
- Web系统常见编码漏洞(开发工程师知晓)
Bill_chen
sqlPHPWebfckeditor脚本
1.头号大敌:SQL Injection
原因:程序中对用户输入检查不严格,用户可以提交一段数据库查询代码,根据程序返回的结果,
获得某些他想得知的数据,这就是所谓的SQL Injection,即SQL注入。
本质:
对于输入检查不充分,导致SQL语句将用户提交的非法数据当作语句的一部分来执行。
示例:
String query = "SELECT id FROM users
- 【MongoDB学习笔记六】MongoDB修改器
bit1129
mongodb
本文首先介绍下MongoDB的基本的增删改查操作,然后,详细介绍MongoDB提供的修改器,以完成各种各样的文档更新操作 MongoDB的主要操作
show dbs 显示当前用户能看到哪些数据库
use foobar 将数据库切换到foobar
show collections 显示当前数据库有哪些集合
db.people.update,update不带参数,可
- 提高职业素养,做好人生规划
白糖_
人生
培训讲师是成都著名的企业培训讲师,他在讲课中提出的一些观点很新颖,在此我收录了一些分享一下。注:讲师的观点不代表本人的观点,这些东西大家自己揣摩。
1、什么是职业规划:职业规划并不完全代表你到什么阶段要当什么官要拿多少钱,这些都只是梦想。职业规划是清楚的认识自己现在缺什么,这个阶段该学习什么,下个阶段缺什么,又应该怎么去规划学习,这样才算是规划。
- 国外的网站你都到哪边看?
bozch
技术网站国外
学习软件开发技术,如果没有什么英文基础,最好还是看国内的一些技术网站,例如:开源OSchina,csdn,iteye,51cto等等。
个人感觉如果英语基础能力不错的话,可以浏览国外的网站来进行软件技术基础的学习,例如java开发中常用的到的网站有apache.org 里面有apache的很多Projects,springframework.org是spring相关的项目网站,还有几个感觉不错的
- 编程之美-光影切割问题
bylijinnan
编程之美
package a;
public class DisorderCount {
/**《编程之美》“光影切割问题”
* 主要是两个问题:
* 1.数学公式(设定没有三条以上的直线交于同一点):
* 两条直线最多一个交点,将平面分成了4个区域;
* 三条直线最多三个交点,将平面分成了7个区域;
* 可以推出:N条直线 M个交点,区域数为N+M+1。
- 关于Web跨站执行脚本概念
chenbowen00
Web安全跨站执行脚本
跨站脚本攻击(XSS)是web应用程序中最危险和最常见的安全漏洞之一。安全研究人员发现这个漏洞在最受欢迎的网站,包括谷歌、Facebook、亚马逊、PayPal,和许多其他网站。如果你看看bug赏金计划,大多数报告的问题属于 XSS。为了防止跨站脚本攻击,浏览器也有自己的过滤器,但安全研究人员总是想方设法绕过这些过滤器。这个漏洞是通常用于执行cookie窃取、恶意软件传播,会话劫持,恶意重定向。在
- [开源项目与投资]投资开源项目之前需要统计该项目已有的用户数
comsci
开源项目
现在国内和国外,特别是美国那边,突然出现很多开源项目,但是这些项目的用户有多少,有多少忠诚的粉丝,对于投资者来讲,完全是一个未知数,那么要投资开源项目,我们投资者必须准确无误的知道该项目的全部情况,包括项目发起人的情况,项目的维持时间..项目的技术水平,项目的参与者的势力,项目投入产出的效益.....
- oracle alert log file(告警日志文件)
daizj
oracle告警日志文件alert log file
The alert log is a chronological log of messages and errors, and includes the following items:
All internal errors (ORA-00600), block corruption errors (ORA-01578), and deadlock errors (ORA-00060)
- 关于 CAS SSO 文章声明
denger
SSO
由于几年前写了几篇 CAS 系列的文章,之后陆续有人参照文章去实现,可都遇到了各种问题,同时经常或多或少的收到不少人的求助。现在这时特此说明几点:
1. 那些文章发表于好几年前了,CAS 已经更新几个很多版本了,由于近年已经没有做该领域方面的事情,所有文章也没有持续更新。
2. 文章只是提供思路,尽管 CAS 版本已经发生变化,但原理和流程仍然一致。最重要的是明白原理,然后
- 初二上学期难记单词
dcj3sjt126com
englishword
lesson 课
traffic 交通
matter 要紧;事物
happy 快乐的,幸福的
second 第二的
idea 主意;想法;意见
mean 意味着
important 重要的,重大的
never 从来,决不
afraid 害怕 的
fifth 第五的
hometown 故乡,家乡
discuss 讨论;议论
east 东方的
agree 同意;赞成
bo
- uicollectionview 纯代码布局, 添加头部视图
dcj3sjt126com
Collection
#import <UIKit/UIKit.h>
@interface myHeadView : UICollectionReusableView
{
UILabel *TitleLable;
}
-(void)setTextTitle;
@end
#import "myHeadView.h"
@implementation m
- N 位随机数字串的 JAVA 生成实现
FX夜归人
javaMath随机数Random
/**
* 功能描述 随机数工具类<br />
* @author FengXueYeGuiRen
* 创建时间 2014-7-25<br />
*/
public class RandomUtil {
// 随机数生成器
private static java.util.Random random = new java.util.R
- Ehcache(09)——缓存Web页面
234390216
ehcache页面缓存
页面缓存
目录
1 SimplePageCachingFilter
1.1 calculateKey
1.2 可配置的初始化参数
1.2.1 cach
- spring中少用的注解@primary解析
jackyrong
primary
这次看下spring中少见的注解@primary注解,例子
@Component
public class MetalSinger implements Singer{
@Override
public String sing(String lyrics) {
return "I am singing with DIO voice
- Java几款性能分析工具的对比
lbwahoo
java
Java几款性能分析工具的对比
摘自:http://my.oschina.net/liux/blog/51800
在给客户的应用程序维护的过程中,我注意到在高负载下的一些性能问题。理论上,增加对应用程序的负载会使性能等比率的下降。然而,我认为性能下降的比率远远高于负载的增加。我也发现,性能可以通过改变应用程序的逻辑来提升,甚至达到极限。为了更详细的了解这一点,我们需要做一些性能
- JVM参数配置大全
nickys
jvm应用服务器
JVM参数配置大全
/usr/local/jdk/bin/java -Dresin.home=/usr/local/resin -server -Xms1800M -Xmx1800M -Xmn300M -Xss512K -XX:PermSize=300M -XX:MaxPermSize=300M -XX:SurvivorRatio=8 -XX:MaxTenuringThreshold=5 -
- 搭建 CentOS 6 服务器(14) - squid、Varnish
rensanning
varnish
(一)squid
安装
# yum install httpd-tools -y
# htpasswd -c -b /etc/squid/passwords squiduser 123456
# yum install squid -y
设置
# cp /etc/squid/squid.conf /etc/squid/squid.conf.bak
# vi /etc/
- Spring缓存注解@Cache使用
tom_seed
spring
参考资料
http://www.ibm.com/developerworks/cn/opensource/os-cn-spring-cache/
http://swiftlet.net/archives/774
缓存注解有以下三个:
@Cacheable @CacheEvict @CachePut
- dom4j解析XML时出现"java.lang.noclassdeffounderror: org/jaxen/jaxenexception"错误
xp9802
java.lang.NoClassDefFoundError: org/jaxen/JaxenExc
关键字: java.lang.noclassdeffounderror: org/jaxen/jaxenexception
使用dom4j解析XML时,要快速获取某个节点的数据,使用XPath是个不错的方法,dom4j的快速手册里也建议使用这种方式
执行时却抛出以下异常:
Exceptio

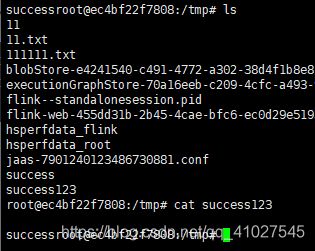
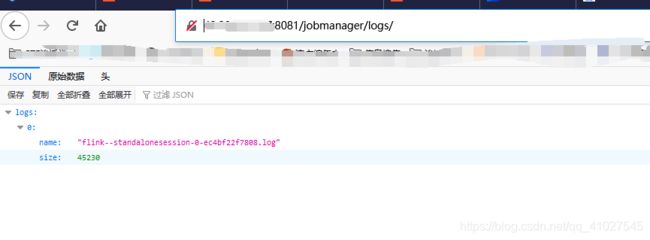
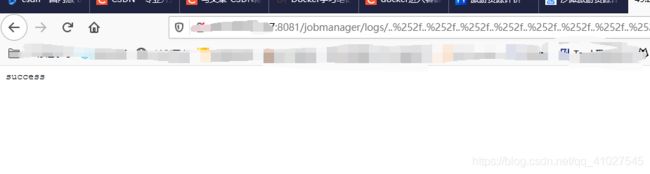
 5.进入docker环境,查看是否创建成功
5.进入docker环境,查看是否创建成功 也可直接在页面操作
也可直接在页面操作