- Telegram是什么? 有什么优势
ZhangJiQun&MXP
教学2021论文2024大模型以及算力语言模型transformerpython人工智能自然语言处理
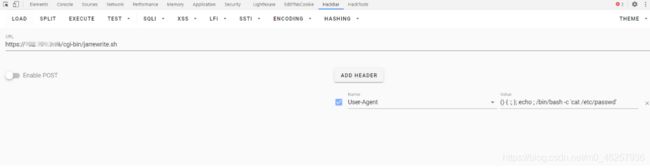
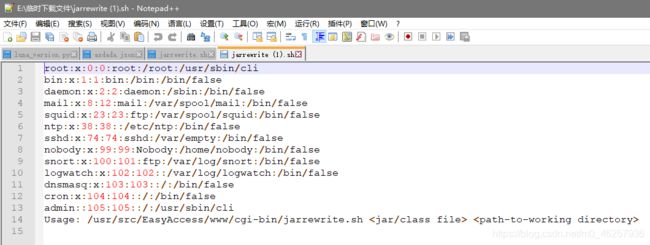
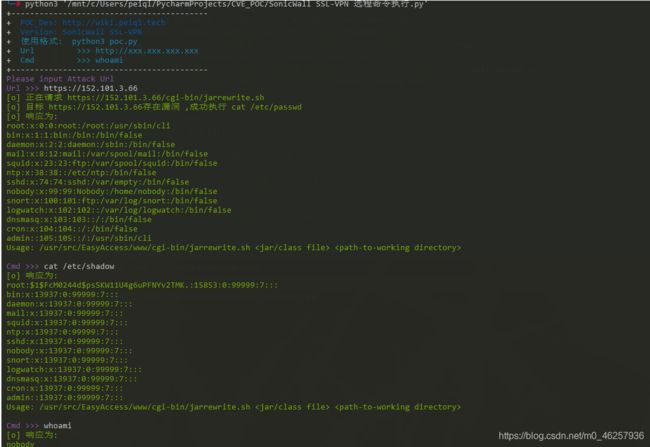
Telegram是什么?有什么优势是一款以安全、高效和多功能著称的即时通讯应用,以下从核心优势、聊天方法及实际案例展开说明:一、核心优势1.极致安全与隐私保护端到端加密:秘密聊天(SecretChats)使用端到端加密**,消息仅双方可见,且支持设置自毁时间(如10秒后自动删除)。**第三方账户验证:2025年新增功能允许监管机构或行业联盟对账户进行认证,验证后的账户显示专属徽标,防范诈骗。匿名性
- 【回溯法】n皇后问题 C/C++ (附代码)
haaaaaaarry
算法设计与分析c语言c++开发语言回溯法算法
问题描述在一个n*n的棋盘上放置彼此不受攻击的n个皇后,按照国际象棋规则,皇后可以攻击与其在同一行,同一列或者同一对角线的其他皇后,求合法摆放的方案数。问题分析通过递归和回溯的方法,逐行放置皇后,并在每一步检查当前位置是否安全。如果安全,则继续放置下一个皇后;如果不安全,则回溯到上一步,尝试其他位置。代码数据结构intx[]:存放解向量,即第i个皇后的位置intsum:记录解的个数#define_
- 选择了它,便选择了不离不弃
京东饭粒
知乎上有个问题:吸猫/撸狗是否会使人像毒品一样上瘾?答案是千篇一律的:是啊,会的,就是会上瘾啊……确实,宠物总能给我们极大的安全感和抚慰,一个人的时候,只要有它在身边,就什么烦恼事都没有了。自从有了它,遍有了牵挂。总想尽快完成工作,回家好好陪陪它;能不出差尽量不出差,怕它自己一人在家寂寞;因为交流问题,每次生病都急得心急火燎……所以别只顾着吸猫/撸狗,宠物的健康问题同样重要,为了让你更好的做好宠物
- 设备数据采集软件OPC Server和工业网关的区别是什么?
工控小J
OPC产品推荐设备数据采集软件网关kepwaretakebishiopcserver
在工业物联网和智能制造领域中,设备数据采集至关重要。企业通常需要高效、安全地采集设备运行状态、生产工艺参数等数据,用以支撑生产管理、设备维护及智能决策。常见的数据采集方式包括使用工业网关(Gateway)和OPCServer软件。本文将从形态、性能、管理方式、应用场景这几方面来详细分析两者的区别及各自优势,帮助企业选择合适的解决方案。一、工业网关(Gateway)工业网关通常是一种软硬件一体化设备
- java Script笔记
第一章,初始javascript1,javascript的基本概念JavaScript一种直译式脚本语言,一种基于对象和事件驱动并具有安全性的客户端脚本语言;也是一种广泛应用客户端web开发的脚本语言。简单地说,JavaScript是一种运行在浏览器中的解释型的编程语言。2,Javascript的特点解释性的脚本语言(代码不进行预编译)与其他脚本语言一样,JavaScript也是一种解释性语言,它
- 聚众识别漏检难题?陌讯多尺度检测实测提升 92%
一、开篇痛点:复杂场景下的聚众识别困境在安防监控、大型赛事等场景中,实时聚众识别是保障公共安全的核心技术。但传统视觉算法常面临三大难题:一是密集人群重叠导致小目标漏检率超30%,二是光照变化(如夜间逆光)引发误报率飙升,三是复杂背景干扰下实时性不足(FPS<15)。某景区监控项目曾反馈,开源模型在节假日人流高峰时,因漏检导致预警延迟达20秒,存在严重安全隐患。这些问题的根源在于传统算法的局限性:单
- 学生信息管理系统的VFP数据库设计与实现
溪水边小屋
本文还有配套的精品资源,点击获取简介:《学生管理系统vfp数据库》是一个基于VisualFoxPro(VFP)的学生信息管理软件,旨在帮助教育机构记录、管理学生数据并提供分析功能。该系统包括数据库设计、用户界面设计、数据操作、事务处理、报表统计、安全性管理、程序架构及代码优化等核心功能。学生管理系统是VFP数据库开发的学习和实践平台,适用于初学者。1.VisualFoxPro数据库开发基础Visu
- 【Bluedroid】蓝牙启动之 btm_acl_device_down 流程源码解析
byte轻骑兵
AndroidC++BluedriodAndriod
本文详细分析Android蓝牙协议栈在设备故障时的处理流程。当蓝牙设备发生硬件故障或系统异常时,协议栈通过btm_acl_device_down触发多层次的资源清理和状态重置,包括ACL连接终止、L2CAP通道释放、SCO连接清理、BLE拓扑更新、设备数据库重置等关键操作,确保系统安全恢复。一、概述1.1蓝牙核心控制块与故障处理框架蓝牙协议栈通过全局控制块tBTM_CB实现跨模块状态管理,其整合了
- “希望是比钻石更珍贵的,在当下最需要的东西”,袁明辉《六项精进》打卡学习273天
YuanWelldon
流浪地球流浪地球姓名:袁明辉公司:宁波惠尔顿婴童安全科技股份有限公司364期学员组别:利他一组403期志工组别:谦虚一组宁波盛和塾8月月度学习会《用数字经营企业》志工宁波盛和塾道盛哲学全国企业家践行成果发表会志工【知~学习】背诵《六项精进大纲》3遍,共761遍。背诵《大学》3遍,共761遍。【经典名句分享】今天开启2019年农历新年计划一、修身1、背诵《般若波罗蜜多心经》0遍,共808遍2、陪女儿
- 工服误检率高达40%?陌讯改进YOLOv7实战降噪50%
2501_92487859
YOLO算法视觉检测目标检测计算机视觉
开篇痛点:工业场景的视觉检测困境在工地、化工厂等高危场景,传统视觉算法面临三重挑战:环境干扰:强光/阴影导致工服颜色失真目标微小:安全帽反光标识仅占图像0.1%像素遮挡密集:工人簇拥时漏检率超35%(数据来源:CVPR2023工业检测白皮书)行业真相:某安监部门实测显示,开源YOLOv5在雾天场景误报率高达41%技术解析:陌讯算法的三大创新设计1.多模态特征融合架构#伪代码示例:可见光+红外特征融
- 路面裂缝漏检率高?陌讯多尺度检测降 30%
2501_92487936
计算机视觉opencv人工智能深度学习算法目标检测
在市政工程与公路养护领域,路面裂缝检测是保障交通安全的关键环节。传统人工巡检不仅效率低下(日均检测≤50公里),且受主观因素影响漏检率高达15-20%[1]。而主流开源视觉算法在面对阴影干扰、多类型裂缝混杂等场景时,往往陷入"精度与速度不可兼得"的困境。本文将结合实战案例,解析陌讯视觉算法在路面裂缝检测中的技术突破与落地经验。一、技术解析:从传统方法到多模态融合架构传统裂缝检测多采用"边缘检测+形
- 山水
山蓝水浅
山。相比于危险,山能给所有的生物安全感,而安全的另一面便是争斗,继而杀戮,沦为又一个危险之地,所以山既安全又危险。有多少生之贪婪,便有多少死之恐惧,山收容所有的流浪,也观看所有的死亡,所以山既不安全也不危险。山只是山,是一个世界。水。水是流动的吗?是的,因为水是河流。河流终年流淌,只会流淌,浑浊、清澈、平缓、湍急……它只往下流淌,顺着地力。直到出现了悬崖,突然站起了身,成了一张倒挂的瀑布,又以千钧
- 画圈圈
乐曦悦曦
图片发自App昨天睡了一天,今天上班依旧没有精神,像霜打的茄子,头痛人也发晕,午饭后趴在办公桌上睡着了,醒来精神好了一些,上三阶段后发现睡觉是我逃避现实的方式,也是自我疗愈的方式,睡饱醒来就会清晰一些。图片发自App晚上一个人静静独处时,想起中周末老A对我说的话,你在给同学们画圈圈,说我内心依然在拉扯着自己,像个边缘人,当时是不太理解的,意识到的只是把自己放在安全的位置上,其他的没有太多认识。有时
- 飞算JavaAI
一、产品简介飞算JavaAI是专为Java开发者打造的智能开发助手,深度适配Java技术栈。通过大语言模型(LLM)实现自然语言到代码的转换,覆盖需求分析、接口设计、表结构设计、业务逻辑生成、代码生成与合并等全流程开发环节。其核心优势在于:全流程自动化:从需求输入到完整工程代码生成,单日可完成传统数周的开发任务。代码质量保障:生成的代码符合阿里巴巴Java开发规范,支持静态代码分析工具自动检测安全
- 清远法兰枫情集成装饰市场价如何,火爆
法兰枫情集成墙饰
1绿色环保零甲醛释放采用绿色的竹木纤维材质,安装后房间无异味,零甲醛释放,又可以放心入住,保证家人居住环境的健康。2防火防潮安全省心产品设计时完全考虑了防火阻燃的要求,经国家权威检测部门检测达到B1级防火等级要求,不助燃无明火,给家庭安全筑起了一道屏障;同时该产品完全防水防潮,尤其适合南方潮湿环境的墙面装修,远离墙面渗漏产生霉变的困扰。
- 多租户SaaS系统中设计安全便捷的跨租户流程共享
Alex艾力的IT数字空间
安全功能测试架构中间件微服务网络安全代码规范
四维协同架构,结合动态授权、加密传输、行为审计和智能策略一、权限控制体系1.动态权限模型2.授权策略实现RBAC+ABAC混合模型在流程表增加shared_tenants字段存储授权信息,结合属性动态校验:CREATETABLEworkflow_process(process_idVARCHAR(36)PRIMARYKEY,tenant_idVARCHAR(36)NOTNULL,shared_te
- 临时节点授权方案实际应用中可能面临的安全问题和对应的防范策略
Alex艾力的IT数字空间
网络架构中间件安全运维功能测试安全架构
一、核心安全风险与防御方案1.重放攻击(ReplayAttack)风险场景:攻击者截获有效授权令牌后重复发送请求,导致权限被恶意复用防御措施:动态令牌机制:在授权节点ID中嵌入时间戳(timestamp)和随机数(nonce),服务端校验时间差(如±5分钟)并记录已使用nonce值签名验证:使用HMAC-SHA256对nodeId+timestamp+secretKey生成签名,防止参数篡改示例代
- 九块九付费进群系统 wxselect SQL注入漏洞复现
0xSecl
漏洞复现v1安全web安全
0x01产品简介九块九付费进群系统是一种新的社群管理方式,用户通过支付9.9元人民币即可加入特定的微信群,享受群内提供的服务或资源。这种模式通常用于知识分享、资源下载、专业交流等社群,通过设置门槛来筛选成员,提高群组的专业性和互动质量。0x02漏洞概述九块九付费进群系统wxselect接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用SQL注入漏洞获取数据库中的信息(例如,管理员后台密码
- U盘直接拔出不在电脑上弹出有何影响
姜暮儿
单片机stm32嵌入式硬件
U盘直接拔出(未通过电脑系统“安全弹出”)可能会对U盘、电脑数据或设备本身造成多种影响,具体如下:一、数据丢失或损坏这是最常见的风险,原因在于:当U盘正在进行数据读写(如复制文件、保存修改、后台自动备份等)时,直接拔出会中断数据传输流程。此时,正在写入的文件可能只保存了部分内容,导致文件损坏(如文档打不开、图片/视频无法播放)。即使没有主动操作,系统可能在后台对U盘进行缓存读写(例如系统自动刷新文
- # 百万级OpenID自动化获取:高并发架构设计与微信生态实战
Loving_enjoy
计算机学科论文创新点人工智能深度学习经验分享facebook
>当你的小程序日活突破10万+,如何安全高效地管理海量用户身份?OpenID作为微信生态的"用户身份证",其获取效率直接影响业务增长!在微信生态开发中,OpenID是用户身份识别的核心密钥。然而传统获取方式存在三大痛点:1.**效率瓶颈**:单线程获取10万OpenID需27小时+2.**稳定性风险**:网络波动导致数据丢失3.**开发成本高**:需重复实现授权逻辑本文将揭秘百万级OpenID自动
- 微算法科技基于格密码的量子加密技术,融入LSQb算法的信息隐藏与传输过程中,实现抗量子攻击策略强化
MicroTech2025
量子计算区块链
随着量子计算技术的发展,传统加密算法面临被量子计算机破解的风险,LSQb算法也需考虑应对未来可能的量子攻击。微算法科技基于格密码的量子加密技术,融入LSQb算法的信息隐藏与传输过程中,实现抗量子攻击策略强化。格密码在面对量子攻击时具有较高的安全性,通过这种融合,能为LSQb算法提供更强大的抗攻击能力,确保信息在复杂的量子计算环境下的安全性。格密码是一种基于数学格结构的密码学方法,具有在量子计算环境
- Flink双流实时对账
在电商、金融、银行、支付等涉及到金钱相关的领域,为了安全起见,一般都有对账的需求。比如,对于订单支付事件,用户通过某宝付款,虽然用户支付成功,但是用户支付完成后并不算成功,我们得确认平台账户上是否到账了。针对上述的场景,我们可以采用批处理,或离线计算等技术手段,通过定时任务,每天结束后,扫描数据库中的数据,核对当天的支付数据和交易数据,进行对账。想要达到实时对账的效果,比如有的用户支付成功但是并没
- 3步搞定Java漏洞修复?别再让黑客当“家”!
关注墨瑾轩,带你探索编程的奥秘!超萌技术攻略,轻松晋级编程高手技术宝库已备好,就等你来挖掘订阅墨瑾轩,智趣学习不孤单即刻启航,编程之旅更有趣Java城堡的“裂缝”与程序员的救赎想象一下:你的Java应用是一座巍峨的城堡,而安全漏洞就是那些悄悄蔓延的裂缝。SQL注入:像是小偷从窗户溜进来,偷偷改写数据库的账本。XSS攻击:像在城堡里偷偷放了一张带毒的地毯,路过的人会被“刺”伤。SSRF漏洞:像让城堡
- 容器中敏感信息泄露路径排查与修复机制:构建、运行与发布全链条实战指南
观熵
DockerDocker安全
容器中敏感信息泄露路径排查与修复机制:构建、运行与发布全链条实战指南关键词:容器安全、敏感信息泄露、环境变量、构建路径排查、Dockerfile安全、CI/CD安全、镜像扫描、密钥管理摘要:在容器化构建与交付流程中,敏感信息泄露问题屡见不鲜,覆盖了硬编码密钥、构建残留、环境变量注入、配置文件外泄等多个维度。本文将基于真实的工程实践,梳理容器生命周期中潜在的敏感信息泄露路径,结合Trivy、Dock
- Agent架构解析及分布式Agent协作方案
来源:AI大模型应用实践AIAgent(智能体)系统发展迅猛,且关注点已经不再局限在Agent的规划推理等基本能力,智能体系统在扩展性、互操作、安全性等工程化方面的挑战也越来越引起重视,比如最近的MCP和A2A。上一篇我们介绍了A2A,今天接着再聊聊分布式Agent系统的话题。Agent模式架构解析Agent有效减少人类工作总量,人与AI协作才是最终形态。人类与AI交互可大致分为三种模式。Embe
- Java的CopyOnWriteArrayList
xbmchina
简介ArrayList并不是线程安全的,在读线程在读取ArrayList的时候如果有写线程在写数据的时候,基于fast-fail机制,会抛出ConcurrentModificationException异常,也就是说ArrayList并不是一个线程安全的容器。那么并发的情况下,这就有了CopyOnWriteArrayList这个东西。下面主要以下几个方面学习CopyOnWriteArrayList
- 国内第一梯队终端安全产品解析:技术与场景实践
粤海科技君
安全腾讯iOA零信任终端安全
国内终端安全市场的第一梯队产品,通常具备技术领先性、场景覆盖度和规模化落地能力。结合2025年最新行业动态与实战案例,以下从技术架构、核心能力和典型应用三个维度,解析当前市场的头部产品及其差异化价值。一、技术架构与市场格局国内终端安全市场呈现"平台化、智能化、场景化"三大趋势。根据赛迪顾问2023年数据,奇安信以18.7%的终端安全市场份额位居首位,其天擎系统通过"终端检测与响应(EDR)+主动防
- 如何抉择HTTPS&Proxy?
彬彬醤
https网络协议http网络chatgpt服务器数据库
HTTPS(超文本传输安全协议)通过TLS/SSL加密保护数据传输,而Proxy(也就是我们常说的网络代理)作为网络中间节点转发请求,二者结合形成“加密传输+灵活转发”的双重保障。这种协同机制的核心价值在于:安全增强:HTTPS加密避免数据被窃听或篡改,代理隐藏真实IP降低直接攻击风险;访问控制:通过代理实现跨地域访问,同时HTTPS确保代理节点与客户端/目标服务器的通信安全。无论是企业跨境数据传
- 如何将 iPhone 备份到笔记本电脑?
将iPhone备份到电脑是一种明智的方式,可以在手机丢失、损坏或无法使用时保护数据安全。此外,它还可以方便您将数据转移到新的iPhone或安卓设备。无论您使用的是Windows还是Mac系统,都可以通过iTunes、Finder(Mac)、iCloud或可靠的第三方应用程序等工具将iPhone备份到笔记本电脑。在本指南中,我们将逐一介绍这些方法,并为您提供详细的iPhone备份到笔记本电脑的说明。
- 云手机隐私保护指南:如何保障账号与数据的云端安全?
Clownseven
智能手机安全
用云手机,担心账号被盗?数据泄露?其实,你不是一个人。只要是把设备和数据放在“云端”,很多人都会下意识问一句:“安全吗?”云手机虽方便,但毕竟是基于虚拟化的云服务,本地可控性差,安全隐患看似无处不在。那么,云手机到底安不安全?如何才能确保账号和数据的云端安全?这篇文章,我们不谈空洞理论,直接从实战角度帮你拆解云手机的隐私保护问题。云手机为什么会有隐私风险?很多人把云手机想得过于“透明安全”,但事实
- Hadoop(一)
朱辉辉33
hadooplinux
今天在诺基亚第一天开始培训大数据,因为之前没接触过Linux,所以这次一起学了,任务量还是蛮大的。
首先下载安装了Xshell软件,然后公司给了账号密码连接上了河南郑州那边的服务器,接下来开始按照给的资料学习,全英文的,头也不讲解,说锻炼我们的学习能力,然后就开始跌跌撞撞的自学。这里写部分已经运行成功的代码吧.
在hdfs下,运行hadoop fs -mkdir /u
- maven An error occurred while filtering resources
blackproof
maven报错
转:http://stackoverflow.com/questions/18145774/eclipse-an-error-occurred-while-filtering-resources
maven报错:
maven An error occurred while filtering resources
Maven -> Update Proje
- jdk常用故障排查命令
daysinsun
jvm
linux下常见定位命令:
1、jps 输出Java进程
-q 只输出进程ID的名称,省略主类的名称;
-m 输出进程启动时传递给main函数的参数;
&nb
- java 位移运算与乘法运算
周凡杨
java位移运算乘法
对于 JAVA 编程中,适当的采用位移运算,会减少代码的运行时间,提高项目的运行效率。这个可以从一道面试题说起:
问题:
用最有效率的方法算出2 乘以8 等於几?”
答案:2 << 3
由此就引发了我的思考,为什么位移运算会比乘法运算更快呢?其实简单的想想,计算机的内存是用由 0 和 1 组成的二
- java中的枚举(enmu)
g21121
java
从jdk1.5开始,java增加了enum(枚举)这个类型,但是大家在平时运用中还是比较少用到枚举的,而且很多人和我一样对枚举一知半解,下面就跟大家一起学习下enmu枚举。先看一个最简单的枚举类型,一个返回类型的枚举:
public enum ResultType {
/**
* 成功
*/
SUCCESS,
/**
* 失败
*/
FAIL,
- MQ初级学习
510888780
activemq
1.下载ActiveMQ
去官方网站下载:http://activemq.apache.org/
2.运行ActiveMQ
解压缩apache-activemq-5.9.0-bin.zip到C盘,然后双击apache-activemq-5.9.0-\bin\activemq-admin.bat运行ActiveMQ程序。
启动ActiveMQ以后,登陆:http://localhos
- Spring_Transactional_Propagation
布衣凌宇
springtransactional
//事务传播属性
@Transactional(propagation=Propagation.REQUIRED)//如果有事务,那么加入事务,没有的话新创建一个
@Transactional(propagation=Propagation.NOT_SUPPORTED)//这个方法不开启事务
@Transactional(propagation=Propagation.REQUIREDS_N
- 我的spring学习笔记12-idref与ref的区别
aijuans
spring
idref用来将容器内其他bean的id传给<constructor-arg>/<property>元素,同时提供错误验证功能。例如:
<bean id ="theTargetBean" class="..." />
<bean id ="theClientBean" class=&quo
- Jqplot之折线图
antlove
jsjqueryWebtimeseriesjqplot
timeseriesChart.html
<script type="text/javascript" src="jslib/jquery.min.js"></script>
<script type="text/javascript" src="jslib/excanvas.min.js&
- JDBC中事务处理应用
百合不是茶
javaJDBC编程事务控制语句
解释事务的概念; 事务控制是sql语句中的核心之一;事务控制的作用就是保证数据的正常执行与异常之后可以恢复
事务常用命令:
Commit提交
- [转]ConcurrentHashMap Collections.synchronizedMap和Hashtable讨论
bijian1013
java多线程线程安全HashMap
在Java类库中出现的第一个关联的集合类是Hashtable,它是JDK1.0的一部分。 Hashtable提供了一种易于使用的、线程安全的、关联的map功能,这当然也是方便的。然而,线程安全性是凭代价换来的――Hashtable的所有方法都是同步的。此时,无竞争的同步会导致可观的性能代价。Hashtable的后继者HashMap是作为JDK1.2中的集合框架的一部分出现的,它通过提供一个不同步的
- ng-if与ng-show、ng-hide指令的区别和注意事项
bijian1013
JavaScriptAngularJS
angularJS中的ng-show、ng-hide、ng-if指令都可以用来控制dom元素的显示或隐藏。ng-show和ng-hide根据所给表达式的值来显示或隐藏HTML元素。当赋值给ng-show指令的值为false时元素会被隐藏,值为true时元素会显示。ng-hide功能类似,使用方式相反。元素的显示或
- 【持久化框架MyBatis3七】MyBatis3定义typeHandler
bit1129
TypeHandler
什么是typeHandler?
typeHandler用于将某个类型的数据映射到表的某一列上,以完成MyBatis列跟某个属性的映射
内置typeHandler
MyBatis内置了很多typeHandler,这写typeHandler通过org.apache.ibatis.type.TypeHandlerRegistry进行注册,比如对于日期型数据的typeHandler,
- 上传下载文件rz,sz命令
bitcarter
linux命令rz
刚开始使用rz上传和sz下载命令:
因为我们是通过secureCRT终端工具进行使用的所以会有上传下载这样的需求:
我遇到的问题:
sz下载A文件10M左右,没有问题
但是将这个文件A再传到另一天服务器上时就出现传不上去,甚至出现乱码,死掉现象,具体问题
解决方法:
上传命令改为;rz -ybe
下载命令改为:sz -be filename
如果还是有问题:
那就是文
- 通过ngx-lua来统计nginx上的虚拟主机性能数据
ronin47
ngx-lua 统计 解禁ip
介绍
以前我们为nginx做统计,都是通过对日志的分析来完成.比较麻烦,现在基于ngx_lua插件,开发了实时统计站点状态的脚本,解放生产力.项目主页: https://github.com/skyeydemon/ngx-lua-stats 功能
支持分不同虚拟主机统计, 同一个虚拟主机下可以分不同的location统计.
可以统计与query-times request-time
- java-68-把数组排成最小的数。一个正整数数组,将它们连接起来排成一个数,输出能排出的所有数字中最小的。例如输入数组{32, 321},则输出32132
bylijinnan
java
import java.util.Arrays;
import java.util.Comparator;
public class MinNumFromIntArray {
/**
* Q68输入一个正整数数组,将它们连接起来排成一个数,输出能排出的所有数字中最小的一个。
* 例如输入数组{32, 321},则输出这两个能排成的最小数字32132。请给出解决问题
- Oracle基本操作
ccii
Oracle SQL总结Oracle SQL语法Oracle基本操作Oracle SQL
一、表操作
1. 常用数据类型
NUMBER(p,s):可变长度的数字。p表示整数加小数的最大位数,s为最大小数位数。支持最大精度为38位
NVARCHAR2(size):变长字符串,最大长度为4000字节(以字符数为单位)
VARCHAR2(size):变长字符串,最大长度为4000字节(以字节数为单位)
CHAR(size):定长字符串,最大长度为2000字节,最小为1字节,默认
- [强人工智能]实现强人工智能的路线图
comsci
人工智能
1:创建一个用于记录拓扑网络连接的矩阵数据表
2:自动构造或者人工复制一个包含10万个连接(1000*1000)的流程图
3:将这个流程图导入到矩阵数据表中
4:在矩阵的每个有意义的节点中嵌入一段简单的
- 给Tomcat,Apache配置gzip压缩(HTTP压缩)功能
cwqcwqmax9
apache
背景:
HTTP 压缩可以大大提高浏览网站的速度,它的原理是,在客户端请求网页后,从服务器端将网页文件压缩,再下载到客户端,由客户端的浏览器负责解压缩并浏览。相对于普通的浏览过程HTML ,CSS,Javascript , Text ,它可以节省40%左右的流量。更为重要的是,它可以对动态生成的,包括CGI、PHP , JSP , ASP , Servlet,SHTML等输出的网页也能进行压缩,
- SpringMVC and Struts2
dashuaifu
struts2springMVC
SpringMVC VS Struts2
1:
spring3开发效率高于struts
2:
spring3 mvc可以认为已经100%零配置
3:
struts2是类级别的拦截, 一个类对应一个request上下文,
springmvc是方法级别的拦截,一个方法对应一个request上下文,而方法同时又跟一个url对应
所以说从架构本身上 spring3 mvc就容易实现r
- windows常用命令行命令
dcj3sjt126com
windowscmdcommand
在windows系统中,点击开始-运行,可以直接输入命令行,快速打开一些原本需要多次点击图标才能打开的界面,如常用的输入cmd打开dos命令行,输入taskmgr打开任务管理器。此处列出了网上搜集到的一些常用命令。winver 检查windows版本 wmimgmt.msc 打开windows管理体系结构(wmi) wupdmgr windows更新程序 wscrip
- 再看知名应用背后的第三方开源项目
dcj3sjt126com
ios
知名应用程序的设计和技术一直都是开发者需要学习的,同样这些应用所使用的开源框架也是不可忽视的一部分。此前《
iOS第三方开源库的吐槽和备忘》中作者ibireme列举了国内多款知名应用所使用的开源框架,并对其中一些框架进行了分析,同样国外开发者
@iOSCowboy也在博客中给我们列出了国外多款知名应用使用的开源框架。另外txx's blog中详细介绍了
Facebook Paper使用的第三
- Objective-c单例模式的正确写法
jsntghf
单例iosiPhone
一般情况下,可能我们写的单例模式是这样的:
#import <Foundation/Foundation.h>
@interface Downloader : NSObject
+ (instancetype)sharedDownloader;
@end
#import "Downloader.h"
@implementation
- jquery easyui datagrid 加载成功,选中某一行
hae
jqueryeasyuidatagrid数据加载
1.首先你需要设置datagrid的onLoadSuccess
$(
'#dg'
).datagrid({onLoadSuccess :
function
(data){
$(
'#dg'
).datagrid(
'selectRow'
,3);
}});
2.onL
- jQuery用户数字打分评价效果
ini
JavaScripthtmljqueryWebcss
效果体验:http://hovertree.com/texiao/jquery/5.htmHTML文件代码:
<!DOCTYPE html>
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<title>jQuery用户数字打分评分代码 - HoverTree</
- mybatis的paramType
kerryg
DAOsql
MyBatis传多个参数:
1、采用#{0},#{1}获得参数:
Dao层函数方法:
public User selectUser(String name,String area);
对应的Mapper.xml
<select id="selectUser" result
- centos 7安装mysql5.5
MrLee23
centos
首先centos7 已经不支持mysql,因为收费了你懂得,所以内部集成了mariadb,而安装mysql的话会和mariadb的文件冲突,所以需要先卸载掉mariadb,以下为卸载mariadb,安装mysql的步骤。
#列出所有被安装的rpm package rpm -qa | grep mariadb
#卸载
rpm -e mariadb-libs-5.
- 利用thrift来实现消息群发
qifeifei
thrift
Thrift项目一般用来做内部项目接偶用的,还有能跨不同语言的功能,非常方便,一般前端系统和后台server线上都是3个节点,然后前端通过获取client来访问后台server,那么如果是多太server,就是有一个负载均衡的方法,然后最后访问其中一个节点。那么换个思路,能不能发送给所有节点的server呢,如果能就
- 实现一个sizeof获取Java对象大小
teasp
javaHotSpot内存对象大小sizeof
由于Java的设计者不想让程序员管理和了解内存的使用,我们想要知道一个对象在内存中的大小变得比较困难了。本文提供了可以获取对象的大小的方法,但是由于各个虚拟机在内存使用上可能存在不同,因此该方法不能在各虚拟机上都适用,而是仅在hotspot 32位虚拟机上,或者其它内存管理方式与hotspot 32位虚拟机相同的虚拟机上 适用。
- SVN错误及处理
xiangqian0505
SVN提交文件时服务器强行关闭
在SVN服务控制台打开资源库“SVN无法读取current” ---摘自网络 写道 SVN无法读取current修复方法 Can't read file : End of file found
文件:repository/db/txn_current、repository/db/current
其中current记录当前最新版本号,txn_current记录版本库中版本