Reversing file virus using IDA
Content
- 1. Open virus Maya in IDA
- 2. Analyse the Image Base of the file
- 3. Modify the program in IDA
- 4. Continue to reverse
- Appendix
-
- PE executable file format offsets
1. Open virus Maya in IDA
Open IDA from start menu (the second one)
Press OK
Press Go
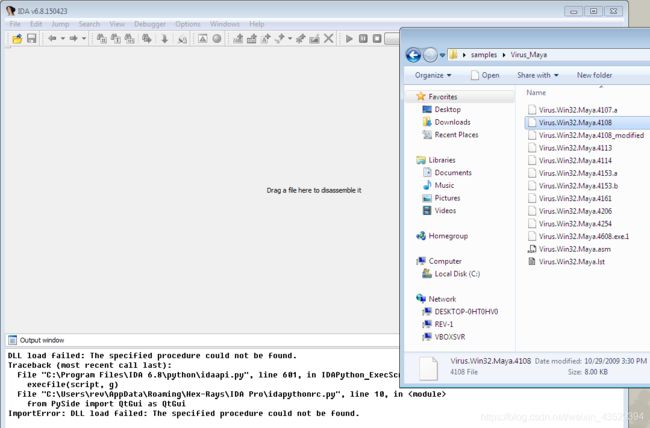
Drug Maya.4108 to IDA
Press OK
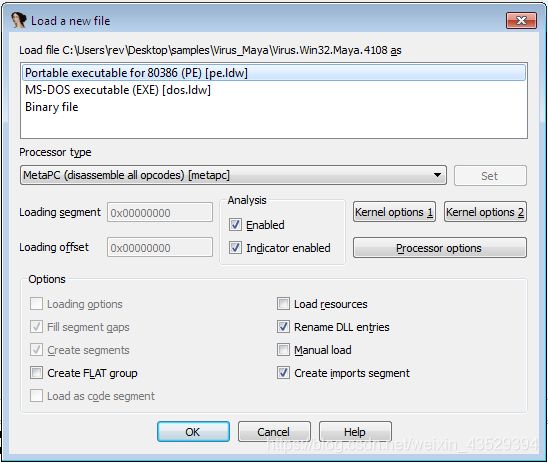
Press No
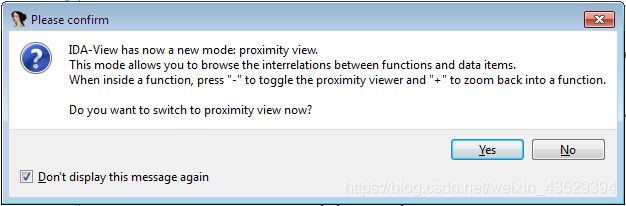
Then we can see the view of the file
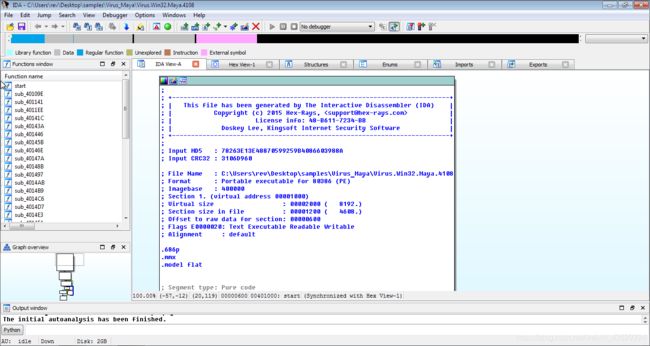
We can switch between graphic view and list view using SPACE key
2. Analyse the Image Base of the file
Open the virus with x32dbg as well.
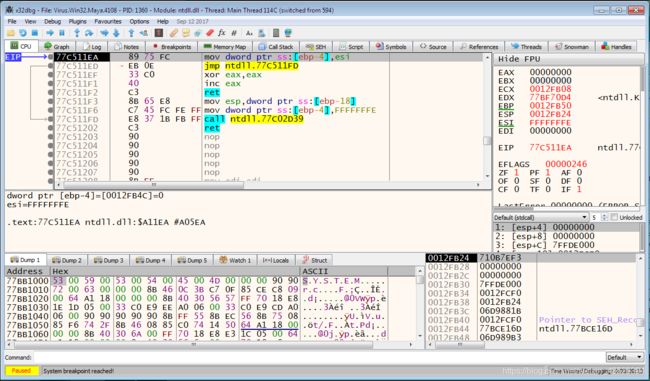
Press F9 to run.
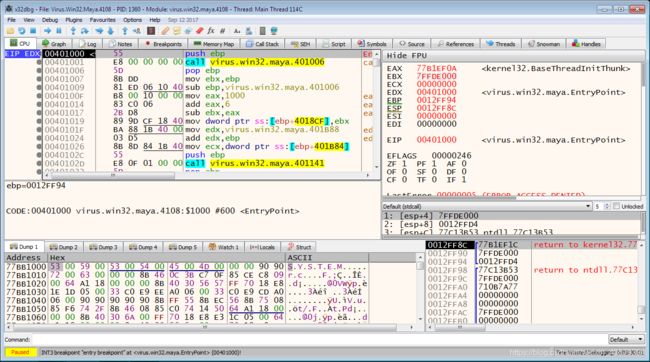
Press F8 to step over until “mov dword” line.
We can see that the register EBX is “MZP”. It is the PE header.
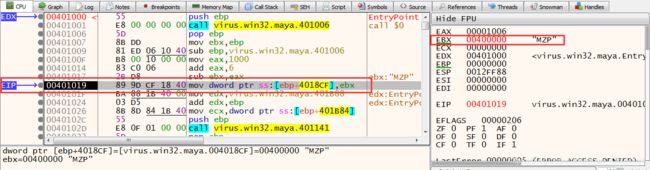
Right click on the EBX and select “follow in dump”
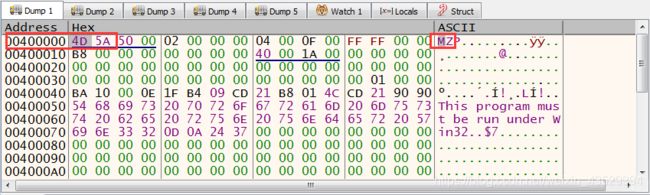
Then we can see the PE header in the dump 1. And we have known that the address of Image Base is the same as the sddress of “MZ”. It is 00400000.
3. Modify the program in IDA
The “mov dword” line in the x32dbg is the same in IDA.
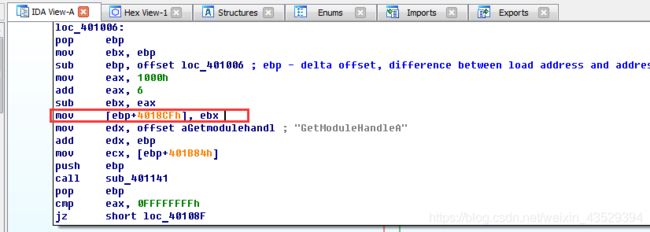
So we modify the variable.
Right click and select ss:dword_4018CF[edp].
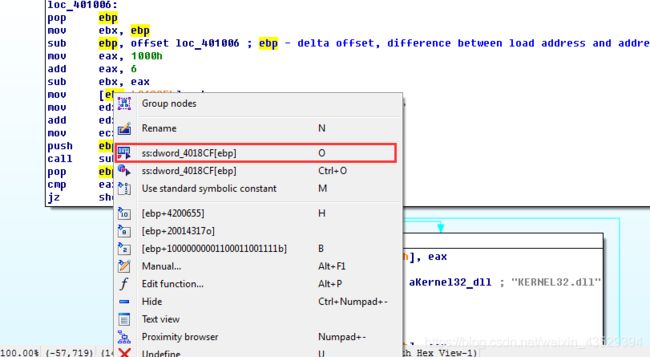
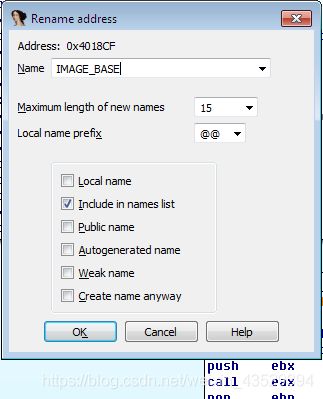
Then right click on the “ss:dword_4018CF[edp]” and select “Rename” to rename the variable to “IMAGE_BASE”
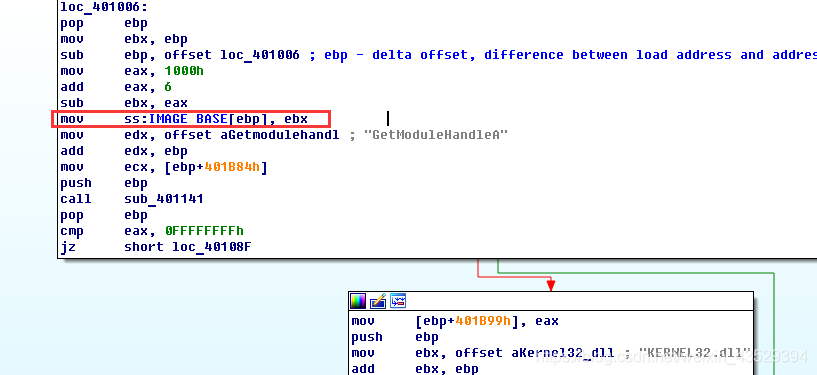
Then we knowthe program stores Image Base variable at here.
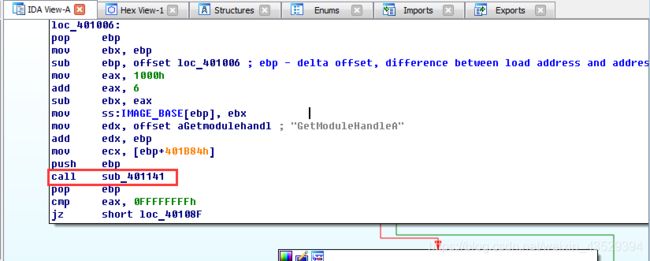
4. Continue to reverse
“call” command always call a fuction. Double left click on “sub_401141” to go to this function.
The function of sub_401141:
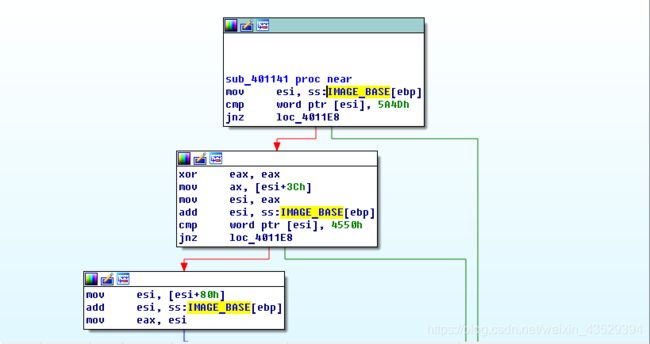
We should know the sentence “mov a, b” gives the value of b to a.
We have known the value of “ss:IMAGE_BASE[ebp]” is “MZ”
“cmp” means “compare”. “cmp word ptr [esi], 5A4Dh” means comparing the data of esi with 5A4Dh.
Right click on “5A4Dh” and select " ‘ZM’ R " to convert it to ASCII code.
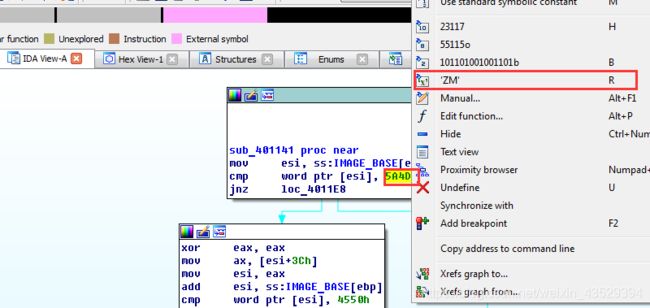
“5A4Dh” is “ZM”. We should read it from right to left. “ZM” is “MZ”.
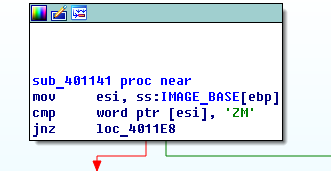
Obviously “cmp word ptr [esi], 5A4Dh” varifies MZ signature.
Press “;” key to comment it.
We got that.
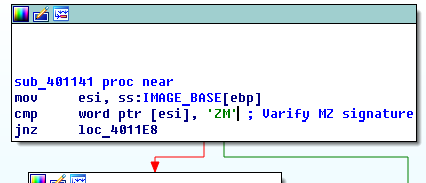
The next command “jnz loc_4011E8” judges the varification above. If the varification is true, go to the left red arrow, otherwise go to the right green arrow.
Look at the next procedure.
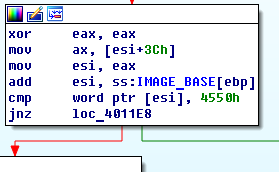
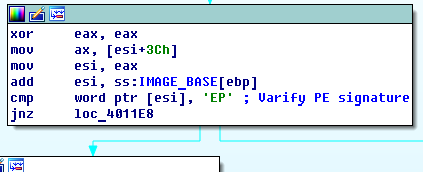
“esi+3Ch” adds the address of “MZ” and “3Ch” up. We can know from the appendix that offset 3C from MZ signature means file address of new exe header. It is the location of “PE”. And “4550h” can be converted to “EP”.
Obviously this procedure varifies PE signature. Comment it.
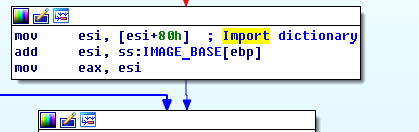
In the next procedure, we can know from the appendix that the offset 80 from MZ signature is ImportDictionary.

Comment it. Attention that the value of esi changes to the address of ImportDictionary.
In the next procedure, “esi+0Ch” goes to the address of Name in ImportDictionary.
“cmp” judges if the words of esi equals to KERN(Obviously “kernal”). It is to find KERNEL32.dll.
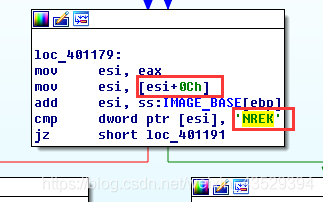
Comment it.
Appendix
PE executable file format offsets
OLD EXE (MZ header)
+0 WORD e_magic; // Magic number MZ
2 WORD e_cblp; // Bytes on last page of file
4 WORD e_cp; // Pages in file
6 WORD e_crlc; // Relocations
8 WORD e_cparhdr; // Size of header in paragraphs
A WORD e_minalloc; // Minimum extra paragraphs needed
C WORD e_maxalloc; // Maximum extra paragraphs needed
E WORD e_ss; // Initial (relative) SS value
10 WORD e_sp; // Initial SP value
12 WORD e_csum; // Checksum
14 WORD e_ip; // Initial IP value
16 WORD e_cs; // Initial (relative) CS value
18 WORD e_lfarlc; // File address of relocation table
1A WORD e_ovno; // Overlay number
1C WORD e_res[4]; // Reserved words
24 WORD e_oemid; // OEM identifier (for e_oeminfo)
26 WORD e_oeminfo; // OEM information; e_oemid specific
28 WORD e_res2[10]; // Reserved words
3C DWORD e_lfanew; // File address of new exe header
:
:
\/
NEW EXE
+0 PE
4 WORD Machine;
6 WORD NumberOfSections;
8 DWORD TimeDateStamp;
C DWORD PointerToSymbolTable;
10 DWORD NumberOfSymbols;
14 WORD SizeOfOptionalHeader;
16 WORD Characteristics;
18 Optional Header
18 WORD Magic;
1a UCHAR MajorLinkerVersion;
1b UCHAR MinorLinkerVersion;
1c DWORD SizeOfCode;
20 DWORD SizeOfInitializedData;
24 DWORD SizeOfUninitializedData;
28 DWORD AddressOfEntryPoint;
2c DWORD BaseOfCode;
30 DWORD BaseOfData; // // NT additional fields.
//
34 DWORD ImageBase;
38 DWORD SectionAlignment;
3c DWORD FileAlignment;
40 WORD MajorOperatingSystemVersion;
42 WORD MinorOperatingSystemVersion;
44 WORD MajorImageVersion;
46 WORD MinorImageVersion;
48 WORD MajorSubsystemVersion;
4a WORD MinorSubsystemVersion;
4c DWORD Reserved1;
50 DWORD SizeOfImage;
54 DWORD SizeOfHeaders;
58 DWORD CheckSum;
5c WORD Subsystem;
5e WORD DllCharacteristics;
60 DWORD SizeOfStackReserve;
64 DWORD SizeOfStackCommit;
68 DWORD SizeOfHeapReserve;
6c DWORD SizeOfHeapCommit;
70 DWORD LoaderFlags;
74 DWORD NumberOfRvaAndSizes;
IMAGE_DATA_DIRECTORY DataDirectory[IMAGE_NUMBEROF_DIRECTORY_ENTRIES];
/* IMAGE_NUMBEROF_DIRECTORY_ENTRIES = 16 */
78 DWORD ExportDirectory VA
7c DWORD ExportDirectory Size
80 DWORD ImportDirectory VA
84 DWORD ImportDirectory Size
88 DWORD ResourceDirectory VA
8c DWORD ResourceDirectory Size
90 DWORD ExceptionDirectory VA
94 DWORD ExceptionDirectory Size
98 DWORD SecurityDirectory VA
9c DWORD SecurityDirectory Size
a0 DWORD BaseRelocationTable VA
a4 DWORD BaseRelocationTable Size
a8 DWORD DebugDirectory VA
ac DWORD DebugDirectory Size
b0 DWORD ArchitectureSpecificData VA
b4 DWORD ArchitectureSpecificData Size
b8 DWORD RVAofGP VA
bc DWORD RVAofGP Size
c0 DWORD TLSDirectory VA
c4 DWORD TLSDirectory Size
c8 DWORD LoadConfigurationDirectory VA
cc DWORD LoadConfigurationDirectory Size
d0 DWORD BoundImportDirectoryinheaders VA
d4 DWORD BoundImportDirectoryinheaders Size
d8 DWORD ImportAddressTable VA
dc DWORD ImportAddressTable Size
e0 DWORD DelayLoadImportDescriptors VA
e4 DWORD DelayLoadImportDescriptors Size
e8 DWORD COMRuntimedescriptor VA
ec DWORD COMRuntimedescriptor Size
f0 DWORD 0
f4 DWORD 0
SectionHeaders
first starts straight after the 'optional' header
at +f8h, this is an array so they just keep coming ;)
+0 8byte ANSI name
+8 dword misc (actual size)
+C dword virtual address (an rva to where it should bee mapped)
10 dword sizeofrawdata
14 dword pointerToRawData (file based offset)
18 dword pointerToRelocations
1C dword PointerToLinenumbers
20 word NumberOfRelocations
22 word NumberOfLineNumbers
24 dword Characteristics
- some of the flags in this are ;-
0x00000020 contains code
0x00000040 contains initialized data
0x00000080 contains uninitialized data
0x00000200 contains comments
0x02000000 can be discarded
0x10000000 This section is shareable.
0x20000000 This section is executable.
0x40000000 This section is readable.
0x80000000 The section is writeable.
Export Directory
+0 DWORD Characteristics;
4 DWORD TimeDateStamp;
8 WORD MajorVersion;
a WORD MinorVersion;
c DWORD Name;
10 DWORD Base;
14 DWORD NumberOfFunctions;
18 DWORD NumberOfNames;
1c DWORD *AddressOfFunctions;
20 DWORD *AddressOfNames;
24 DWORD *AddressOfNameOrdinals;
Import Directory
+0 DWORD OriginalFirstThunk;
4 DWORD TimeDateStamp;
8 DWORD ForwarderChain;
c DWORD Name;
10 DWORD FirstThunk;