ros::time now_寻找漏洞:在NVIDIA GeForce NOW虚拟机上执行任意代码
ros::time now
介绍 (Introduction)
Against the backdrop of the coronavirus pandemic, the demand for cloud gaming services has noticeably increased. These services provide computing power to launch video games and stream gameplay to user devices in real-time. The most obvious advantage of this gaming type is that gamers do not need to have high-end hardware. An inexpensive computer is enough to run the client, spending time in self-isolation while the remote server carries out all calculations.
在冠状病毒大流行的背景下,对云游戏服务的需求明显增加。 这些服务提供了启动视频游戏并将游戏过程实时流式传输到用户设备的计算能力。 这种游戏类型最明显的优势是,游戏玩家无需拥有高端硬件。 一台便宜的计算机足以运行客户端,花费时间进行自我隔离,而远程服务器执行所有计算。
NVIDIA GeForce NOW is one of these cloud-based game streaming services. According to Google Trends, worldwide search queries for GeForce NOW peaked in February 2020. This correlates with the beginning of quarantine restrictions in many Asian, European, and North and South American countries, as well as other world regions. At the same time in Russia, where the self-isolation regime began in March, we see a similar picture with a corresponding delay.
NVIDIA GeForce NOW是这些基于云的游戏流服务之一。 根据Google趋势,GeForce NOW的全球搜索查询量在2020年达到顶峰。这与许多亚洲,欧洲,北美和南美国家以及其他世界地区开始实行隔离限制有关。 与此同时,在3月开始实行自我隔离制度的俄罗斯,我们看到了类似的情况,但有相应的延迟。
Given the high interest in GeForce NOW, we decided to explore this service from an information security standpoint.
鉴于对GeForce NOW的高度关注,我们决定从信息安全的角度来探索这项服务。
探索平台 (Exploring the platform)
When we began our research, GeForce NOW offered two membership options — free and the so-called Founders membership, which was available on a subscription basis. The free version has some limitations; for example, a player may have to wait in a queue to access servers. The paid version offers priority access and the player usually does not need to wait for available virtual machines. Both versions provide an identical security level. If the player somehow violates the service’s terms of use, runtime immediately shuts down and the guilty gamer’s account can be banned.
当我们开始研究时,GeForce NOW提供了两种成员资格选项-免费和所谓的Founders成员资格,可通过订阅获得。 免费版本有一些局限性。 例如,玩家可能必须在队列中等待访问服务器。 付费版本提供优先访问权,玩家通常不需要等待可用的虚拟机。 两种版本均提供相同的安全级别。 如果玩家某种程度上违反了服务的使用条款,则运行时将立即关闭,并且可以禁止有罪游戏者的帐户。
The menu contains a list of games supported by the service. To play a game, the gamer needs an account from one of the digital distribution services with a particular game linked to it. If the game is paid, it must be purchased in advance. In this study, we examine GeForce NOW in conjunction with the Steam digital store.
菜单包含服务支持的游戏列表。 为了玩游戏,游戏者需要来自数字发行服务之一的账户,该账户关联有特定的游戏。 如果游戏是付费的,则必须提前购买。 在这项研究中,我们结合Steam数字商店检查了GeForce NOW。
Upon clicking “Play”, a remote virtual environment is launched in the main window and real-time streaming from the server to the user's device begins.
单击“播放”后,将在主窗口中启动远程虚拟环境,并开始从服务器到用户设备的实时流传输。
If the selected game has already been purchased, it will run in full-screen mode and other features of the virtual environment should not be available to the player. However, if the game settings allow the game to be launched in the windowed mode, it becomes possible to access the Steam library. Another way to access the library is to select a game that is not yet present in the catalog.
如果已经购买了选定的游戏,它将在全屏模式下运行,并且虚拟环境的其他功能将对玩家不可用。 但是,如果游戏设置允许以窗口模式启动游戏,则可以访问Steam库。 访问库的另一种方法是选择目录中尚不存在的游戏。
It is already clear that one can execute arbitrary code by exploiting a vulnerability in a supported game. The only limitation is that the exploit must be delivered over the network. Several scenarios for further events exist. For example, if an exploit during its operation creates an executable file on the virtual machine’s disk, the service may theoretically prevent the payload from executing by tracking the executable file created by “kiosk” — the standard username in GeForce NOW virtual machines. On the other hand, if exploiting a vulnerability results in shellcode execution, the entire system will become vulnerable.
已经很清楚,可以通过利用受支持的游戏中的漏洞来执行任意代码。 唯一的限制是该漏洞必须通过网络传递。 存在进一步事件的几种情况。 例如,如果漏洞利用程序在其运行期间在虚拟机的磁盘上创建了可执行文件,则该服务从理论上可以通过跟踪由“ kiosk”(GeForce NOW虚拟机中的标准用户名)创建的可执行文件来阻止有效负载执行。 另一方面,如果利用漏洞导致执行Shellcode,则整个系统将变得脆弱。
To perform proper exploration of the virtual machine’s environment, access to cmd.exe or powershell.exe would be useful. But how to get it? A brief browse through the Steam library helped find a way to launch an arbitrary executable file that already exists in the system. To do this we used the “Add a Non-Steam Game...” option.
为了对虚拟机的环境进行适当的探索,访问cmd.exe或powershell.exe将很有用。 但是如何获得呢? 简短浏览Steam库有助于找到一种方法来启动系统中已存在的任意可执行文件。 为此,我们使用了“添加非蒸汽游戏...”选项。
In regular conditions, it would not be a problem to add cmd.exe to the library as a Non-Steam game. But in the GeForce Now environment this option is blocked and clicking the “Browse” button does not lead to anything. Nevertheless, it is possible to select one of the existing applications (and at the same time see what programs are installed in the virtual machine). The 7-Zip file archiver will be used as an example, but any of the listed programs will work.
在常规情况下,将cmd.exe作为非Steam游戏添加到库中不会有问题。 但是在GeForce Now环境中,此选项被阻止,单击“浏览”按钮不会导致任何结果。 但是,可以选择现有的应用程序之一(同时查看虚拟机中安装了哪些程序)。 以7-Zip文件存档器为例,但是列出的任何程序都可以使用。
After adding 7-Zip to the Steam library, the program settings can be changed. At this stage the path can be altered to point to cmd.exe. Ready. Let’s launch the “Non-Steam game” and get the working shell:
将7-Zip添加到Steam库后,可以更改程序设置。 在此阶段,路径可以更改为指向cmd.exe。 准备。 让我们启动“非蒸汽游戏”并获得有效的外壳程序:
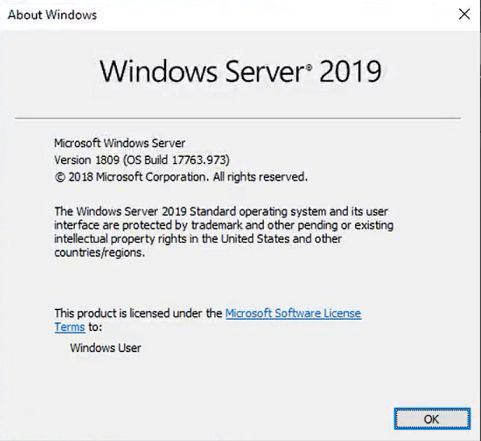
Now it is possible to look around and locate some of the system parameters. Launching winver:
现在可以环顾四周并找到一些系统参数。 启动winver:
As it turned out, the service’s virtual machine runs on Windows Server 2019.
事实证明,该服务的虚拟机在Windows Server 2019上运行。
As a result, we can already do things that GeForce NOW virtual machines are not supposed to do. What else can be done and how dangerous would it be?
结果,我们已经可以做GeForce NOW虚拟机不应该做的事情。 还有什么可以做的,会有多危险?
According to the FAQ located on the NVIDIA webpage designed to report vulnerabilities, obtaining access to cmd.exe on the GeForce NOW virtual machine is not considered a vulnerability. The default user has minimal permissions in the virtual environment, and there is filtering for running applications. For example, the virtual machine immediately shuts down immediately after launching powershell.exe.
根据旨在报告漏洞的NVIDIA网站上的常见问题解答,在GeForce NOW虚拟机上获得对cmd.exe的访问权限不视为漏洞。 默认用户在虚拟环境中具有最小权限,并且对正在运行的应用程序进行了筛选。 例如,启动powershell.exe后,虚拟机将立即关闭。
Thus, to make this study topical we need to solve two tasks:
因此,要使本研究成为主题,我们需要解决两个任务:
1. Deliver the payload to the virtual machine
1.将有效负载交付给虚拟机
2. Launch it by bypassing the application allowlist
2.通过绕过应用程序允许列表启动它
We tried popular LOLBins such as regsvr32, bitsadmin and some others to deliver the payload, but in all cases, the virtual machine crashed:
我们尝试使用流行的LOLBins(例如regsvr32,bitsadmin等)来交付有效负载,但是在所有情况下,虚拟机都崩溃了:
The decision came naturally. GeForce NOW is a service for gaming, including multiplayer online gaming where a client connects to the game server to download sounds, models, maps and other files. Therefore, we should choose a game that allows one to deliver an arbitrary file to the client. At the same time, we do not need to worry about the file extension since we have access to the shell and we can move the downloaded file to a location where we can use it.
决定自然而然。 GeForce NOW是一种游戏服务,包括多人在线游戏,其中客户端连接到游戏服务器以下载声音,模型,地图和其他文件。 因此,我们应该选择一种允许向客户端交付任意文件的游戏。 同时,我们不必担心文件扩展名,因为我们可以访问外壳程序,并且可以将下载的文件移动到可以使用它的位置。
But how to deal with the application allowlist? After all, even if we manage to put a third-party application onto a virtual machine, it will crash the moment the application starts. One possible solution is to find an application from the allowlist, perform a DLL hijacking attack and inject the code into that app. The most obvious target is the game’s process.
但是如何处理申请许可清单? 毕竟,即使我们设法将第三方应用程序放置到虚拟机上,也将在应用程序启动时崩溃。 一种可能的解决方案是从允许列表中找到一个应用程序,执行DLL劫持攻击,然后将代码注入该应用程序。 最明显的目标是游戏的过程。
Counter-Strike: Source game (CS:S) will be used as a working example. The first thing to do is create a custom CS:S game server that will deliver the DLL file disguised as the game model (d.mdl). We then launch CS:S within GeForce NOW and join our server to automatically download the prepared d.mdl onto the virtual machine. Now we minimize the game and launch cmd.exe. Then we move the d.mdl file to “Counter-Strike Source/bin/user32.dl” and restart the game with the console command. We have just run arbitrary code within the context of a trusted process.
反恐精英:源游戏(CS:S)将用作工作示例。 首先要做的是创建一个自定义CS:S游戏服务器,该服务器将提供伪装成游戏模型(d.mdl)的DLL文件。 然后,我们在GeForce NOW中启动CS:S,并加入我们的服务器以将准备好的d.mdl自动下载到虚拟机上。 现在我们最小化游戏并启动cmd.exe。 然后,将d.mdl文件移动到“ Counter-Strike Source / bin / user32.dl”,然后使用控制台命令重新启动游戏。 我们只是在受信任进程的上下文中运行任意代码。
And even make a video clip:
甚至制作一个视频剪辑:
结论 (Conclusion)
Although attacks on the service’s users are potentially possible, they are still questionable. Additionlly, in the event of an attack on a single virtual machine, the risks to other users will be minimal. For each new game session, GeForce NOW launches a clean virtual environment. After the player finishes his session, the virtual machine shuts down and resets. With that, even if the vulnerability is successfully exploited, the malicious code will run only as long as the compromised virtual machine runs. To attack other users, hackers will need to go beyond the virtual environment by utilizing the “virtual machine escape” exploit. These kinds of exploits are rare and difficult to implement. Still, if successful, the attack will threaten not only individual players, but also users who began the game session after the initial infection through one of the GeForce NOW virtual machines.
尽管可能会攻击该服务的用户,但它们仍然值得怀疑。 此外,如果攻击单个虚拟机,则对其他用户的风险将降至最低。 对于每个新游戏会话,GeForce NOW都会启动一个干净的虚拟环境。 播放器结束会话后,虚拟机将关闭并重置。 这样,即使漏洞被成功利用,只要受感染的虚拟机运行,恶意代码也只会运行。 为了攻击其他用户,黑客将需要通过利用“虚拟机逃逸”漏洞来超越虚拟环境。 这类攻击很少见且难以实施。 即使成功,该攻击将不仅威胁单个玩家,而且还威胁通过GeForce NOW虚拟机之一进行初始感染后开始游戏的用户。
However, a more straightforward and realistic attack scenario is to use a compromised virtual machine for mining, conducting DDoS attacks, and performing other illegal actions that require computing power.
但是,一种更直接,更现实的攻击方案是使用受损的虚拟机进行挖掘,进行DDoS攻击以及执行其他需要计算能力的非法行为。
After our report, NVIDIA confirmed the problem and released a corresponding fix for its service.
报告发布后,NVIDIA确认了问题并发布了相应的服务修复程序。
事件的年代: (Chronology of events:)
20.04.2020 — NVIDIA PSIRT confirmed receiving the report and reproduced the bug.
2020年4月20日-NVIDIA PSIRT确认已收到报告并重现了该错误。
13.05.2020 — NVIDIA PSIRT informed us that developers were working on the problem.
2020年5月13日-NVIDIA PSIRT通知我们开发人员正在解决此问题。
21.08.2020 — NVIDIA PSIRT informed that the fix would be released before 30.08.
2020年8月21日-NVIDIA PSIRT通知此修复程序将在30.08之前发布。
02.09.2020 — We requested a clarification about the release date.
2020年9月2日-我们要求澄清发布日期。
03.09.2020 — NVIDIA released the fix.
2020年3月9日-NVIDIA发布了此修复程序。
04.09.2020 — NVIDIA made an announcement about the vulnerability.
2020年4月9日-NVIDIA发布了关于此漏洞的公告。
07.09.2020 — We published our report.
2020年7月7日-我们发布了报告。
翻译自: https://habr.com/en/company/drweb/blog/518052/
ros::time now