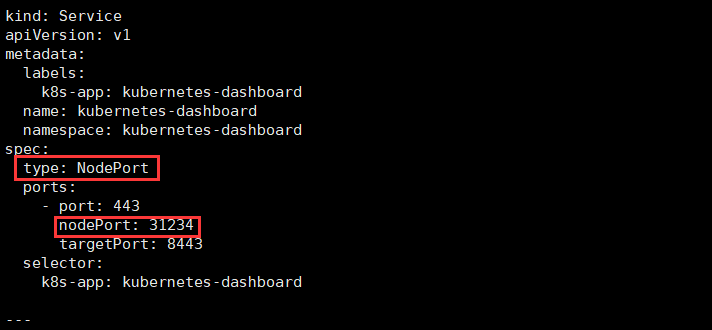
下载Dashboard所需要用到的yaml文件
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0/aio/deploy/recommended.yaml
##无法下载时候可用如下方法配置操作:
通过IPAddress.com首页,输入raw.githubusercontent.com查询到真实IP地址
sudo vim /etc/hosts
真实IP地址列如192.168.XXX.XXX raw.githubusercontent.com
wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta7/aio/deploy/recommended.yaml
1.自己拉一个镜像
docker pull mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.1
docker tag mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.1 k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
2.修改kubernetes-dashboard.yaml 并执行 kubectl apply -f kubernetes-dashboard.yaml
3.执行完之后 查看状态需要等待1-3分钟内 状态为Running时 基本ok
kubectl get pods --all-namespaces
kubernetes-dashboard dashboard-metrics-scraper-dc6947fbf-zqrwq 1/1 Running 0 93s
kubernetes-dashboard kubernetes-dashboard-5d4dc8b976-g5z4s 1/1 Running 0 93s
4.证书步骤操作:
mkdir key && cd key
#生成证书
openssl genrsa -out dashboard.key 2048
#我这里写的自己的node1节点,因为我是通过nodeport访问的;如果通过apiserver访问,可以写成自己的master节点ip
openssl req -new -out dashboard.csr -key dashboard.key -subj '/CN=192.168.1.244'
openssl x509 -req -in dashboard.csr -signkey dashboard.key -out dashboard.crt
#删除原有的证书secret
kubectl delete secret kubernetes-dashboard-certs -n kube-system
#创建新的证书secret
kubectl create secret generic kubernetes-dashboard-certs --from-file=dashboard.key --from-file=dashboard.crt -n kube-system
#查看pod
kubectl get pod -n kube-system
5.创建绑定用户
A.创建一个叫admin-user的服务账号:
[root@k8s01 ~]# cat admin-user.yaml
# admin-user.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kube-system
[root@k8s01 ~]# kubectl create -f admin-user.yaml
B.直接绑定admin角色:
[root@k8s01 ~]# cat admin-user-role-binding.yaml
# admin-user-role-binding.yaml
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kube-system
[root@k8s01 ~]# kubectl create -f admin-user-role-binding.yaml
C:最后查看一下绑定情况 命令:kubectl get clusterrolebinding
6.https://192.168.220.102:31234 ###这里ip输入你当时设置的node1节点ip
7.登陆所需要的token 获取方法:
kubectl -n kube-system get secret
8.查询该用户token认证,复制此token
kubectl -n kube-system describe secret admin-user-token-wvlxs ##替换自己查出来的token
谷歌搜索:https://192.168.220.101:31234
问题汇总:若master 指定nodeport 在node 查看端口没有起来,查看kube-proxy是否正常running
若端口起来,但是telnet 连不进去端口,开启路由转发
cat >> /etc/sysctl.conf << EOF
net.ipv4.ip_forward - 1
EOF
/sbin/sysctl -p
或者 sysctl -p
常用命令汇总:
kubectl get nodes
kubectl get nodes -o wide
kubectl get pods --all-namespaces
journalctl -f -u kubelet
kubectl -n kube-system get service
kubectl -n kubernetes-dashboard get service
kubectl get pods --v 6 #打开详细日志模式
kubectl get cs
kubectl cluster-info
kubectl -n kube-system get cm kubeadm-config -oyaml
kubectl run nginx --image=nginx --replicas=2 --port=80
kubectl describe pod
kubectl describe deployment
kubectl describe service
kubectl logs -f
kubectl delete deployment
kubectl delete service
kubectl create -f
kubectl delete -f
kubeadm config view
kubectl config view
参考文档:
https://www.jianshu.com/p/40c0405811ee