【Gorho】springboot整合Shiro+jwt 前后端分离 超级详细的shiro+jwt鉴权过程
shiro+jwt+springboot
- 说在前面
-
- 简介
- 项目环境(pom.xml)
- 项目结构(各种包和类)
- 鉴权流程
- 具体代码
-
- 配置Shiro
- 配置JWTUtils
- 定义JwtFilter
- 定义JwtToken
- 定义两个Realm
- 两个"工具人"
-
-
- **JwtCredentialsMatcher.java**
- **MultiRealmAuthenticator.java**
-
- 全局异常处理
- 两个controller
-
-
- LoginController.java
- ArticleController.java
-
- 接口测试
说在前面
简介
最近粗略地了解了一下shiro框架是怎么使用的,但是视频讲解的是前后端不分离的,虽然思路差不多,但还是好难受,而且没有讲解shiro怎么整合jwt,于是我学习了两天(四处看博客),终于找到一个良心教程,然后大概把demo给整出来了。就是springboot中整合shiro+jwt,实现token登录然后shiro保证安全什么的,希望能给过渡期的朋友们一点帮助(找不到好的文章是真的很难受的!!!!)具体的一些解释大家可以康康代码里面的注释噢!还有别导错包了!
项目环境(pom.xml)
jdk 14 + springboot + shiro1.5.3 + jwt3.3.0 +一些依赖
为了方便大家上手,这里没有用数据库,不然又一堆环境什么的问题跑不起来
```java
4.0.0
org.springframework.boot
spring-boot-starter-parent
2.4.4
com
szu
0.0.1-SNAPSHOT
szu
Demo project for Spring Boot
11
org.springframework.boot
spring-boot-starter-web
org.springframework.boot
spring-boot-devtools
runtime
true
org.projectlombok
lombok
true
org.springframework.boot
spring-boot-starter-test
test
com.auth0
java-jwt
3.3.0
org.apache.shiro
shiro-spring-boot-starter
1.5.3
commons-lang
commons-lang
2.6
org.springframework.boot
spring-boot-maven-plugin
org.projectlombok
lombok
项目结构(各种包和类)
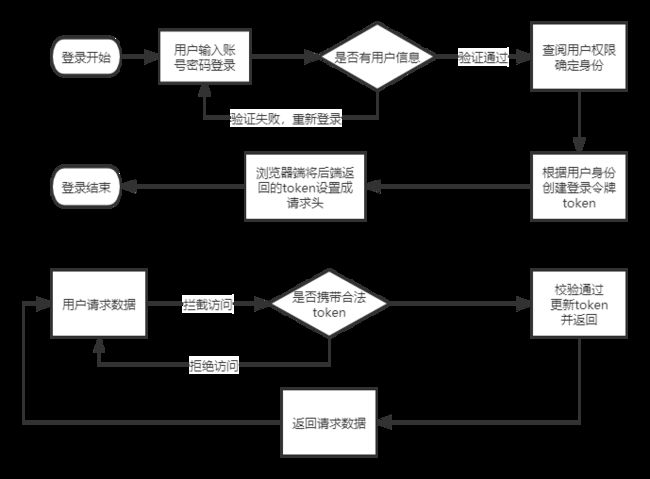
鉴权流程
具体代码
配置Shiro
1、我们这个ShiroConfig禁用了session
2、添加自定义的jwtFilter过滤器,用来拦截自定义的JWT token
3、使用自定义的MultiRealmAuthenticatoe多Realm认证器,解决认证异常无法正常返回的问题(这我不太懂,抱歉)
4、JwtRealm+ShiroRealm的双realm,JwtRealm专门处理 JWT token验证身份的请求
shiroConfig主要是配置shiro的一些基本策略,让shiro能被用起来。例如我们最基本的需要 shiroFilter、SecurityManager、自定义realm
`package com.szu.shiro.config;
import java.util.ArrayList;
import java.util.LinkedHashMap;
import java.util.List;
import java.util.Map;
import javax.servlet.Filter;
import com.szu.db.ShiroRealm;
import com.szu.filter.JwtFilter;
import com.szu.shiro.realm.JwtRealm;
import com.szu.shiro.realm.MultiRealmAuthenticator;
import com.szu.utils.JwtCredentialsMatcher;
import org.apache.shiro.authc.credential.CredentialsMatcher;
import org.apache.shiro.authc.credential.HashedCredentialsMatcher;
import org.apache.shiro.authc.pam.AuthenticationStrategy;
import org.apache.shiro.authc.pam.FirstSuccessfulStrategy;
import org.apache.shiro.authc.pam.ModularRealmAuthenticator;
import org.apache.shiro.authz.Authorizer;
import org.apache.shiro.authz.ModularRealmAuthorizer;
import org.apache.shiro.mgt.*;
import org.apache.shiro.mgt.SecurityManager;
import org.apache.shiro.realm.Realm;
import org.apache.shiro.session.mgt.SessionManager;
import org.apache.shiro.spring.LifecycleBeanPostProcessor;
import org.apache.shiro.spring.security.interceptor.AuthorizationAttributeSourceAdvisor;
import org.apache.shiro.spring.web.ShiroFilterFactoryBean;
import org.apache.shiro.web.mgt.DefaultWebSecurityManager;
import org.springframework.aop.framework.autoproxy.DefaultAdvisorAutoProxyCreator;
import org.springframework.boot.web.servlet.FilterRegistrationBean;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
@Configuration
public class ShiroConfig {
/**
* 交由 Spring 来自动地管理 Shiro-Bean 的生命周期
*/
@Bean
public static LifecycleBeanPostProcessor getLifecycleBeanPostProcessor() {
return new LifecycleBeanPostProcessor();
}
/**
* 为 Spring-Bean 开启对 Shiro 注解的支持
*/
@Bean
public AuthorizationAttributeSourceAdvisor authorizationAttributeSourceAdvisor(SecurityManager securityManager) {
AuthorizationAttributeSourceAdvisor authorizationAttributeSourceAdvisor = new AuthorizationAttributeSourceAdvisor();
authorizationAttributeSourceAdvisor.setSecurityManager(securityManager);
return authorizationAttributeSourceAdvisor;
}
@Bean
public DefaultAdvisorAutoProxyCreator defaultAdvisorAutoProxyCreator() {
DefaultAdvisorAutoProxyCreator app = new DefaultAdvisorAutoProxyCreator();
app.setProxyTargetClass(true);
return app;
}
/**
* 不向 Spring容器中注册 JwtFilter Bean,防止 Spring 将 JwtFilter 注册为全局过滤器
* 全局过滤器会对所有请求进行拦截,而本例中只需要拦截除 /login 和 /logout 外的请求
* 另一种简单做法是:直接去掉 jwtFilter()上的 @Bean 注解
*/
@Bean
public FilterRegistrationBean<Filter> registration(JwtFilter filter) {
FilterRegistrationBean<Filter> registration = new FilterRegistrationBean<Filter>(filter);
registration.setEnabled(false);
return registration;
}
@Bean
public JwtFilter jwtFilter() {
//过滤器如果加了@Compoent就没必要用这个方法了
return new JwtFilter();
}
/**
* 配置访问资源需要的权限
*/
@Bean
public ShiroFilterFactoryBean shiroFilterFactoryBean(SecurityManager securityManager) {
ShiroFilterFactoryBean shiroFilterFactoryBean = new ShiroFilterFactoryBean();
//给工厂bean设置web安全管理器
shiroFilterFactoryBean.setSecurityManager(securityManager);
shiroFilterFactoryBean.setLoginUrl("/login");
shiroFilterFactoryBean.setSuccessUrl("/authorized");
shiroFilterFactoryBean.setUnauthorizedUrl("/unauthorized");
// 添加 jwt 专用过滤器,拦截除 /login 和 /logout 外的请求
Map<String, Filter> filterMap = new LinkedHashMap<>();
filterMap.put("jwtFilter", jwtFilter());
shiroFilterFactoryBean.setFilters(filterMap);
//配置系统受限资源以及公共资源
LinkedHashMap<String, String> filterChainDefinitionMap = new LinkedHashMap<String, String>();
filterChainDefinitionMap.put("/login", "anon"); // 可匿名访问
filterChainDefinitionMap.put("/logout", "logout"); // 退出登录
filterChainDefinitionMap.put("/**", "jwtFilter,authc"); // 需登录才能访问
shiroFilterFactoryBean.setFilterChainDefinitionMap(filterChainDefinitionMap);
return shiroFilterFactoryBean;
}
/**
* 配置 ModularRealmAuthenticator
*/
@Bean
public ModularRealmAuthenticator authenticator() {
ModularRealmAuthenticator authenticator = new MultiRealmAuthenticator();
// 设置多 Realm的认证策略,默认 AtLeastOneSuccessfulStrategy
AuthenticationStrategy strategy = new FirstSuccessfulStrategy();
authenticator.setAuthenticationStrategy(strategy);
return authenticator;
}
/**
* 禁用session, 不保存用户登录状态。保证每次请求都重新认证
*/
@Bean
protected SessionStorageEvaluator sessionStorageEvaluator() {
DefaultSessionStorageEvaluator sessionStorageEvaluator = new DefaultSessionStorageEvaluator();
sessionStorageEvaluator.setSessionStorageEnabled(false);
return sessionStorageEvaluator;
}
/**
* JwtRealm 配置,需实现 Realm 接口
*/
@Bean
JwtRealm jwtRealm() {
JwtRealm jwtRealm = new JwtRealm();
// 设置加密算法
CredentialsMatcher credentialsMatcher = new JwtCredentialsMatcher();
// 设置加密次数
jwtRealm.setCredentialsMatcher(credentialsMatcher);
return jwtRealm;
}
/**
* ShiroRealm 配置,需实现 Realm 接口
*/
@Bean
ShiroRealm shiroRealm() {
//这里其实是模拟的数据库的类,但是也继承了AuthorizingRealm
ShiroRealm shiroRealm = new ShiroRealm();
// 设置加密算法
HashedCredentialsMatcher credentialsMatcher = new HashedCredentialsMatcher("SHA-1");
// 设置加密次数
credentialsMatcher.setHashIterations(16);
shiroRealm.setCredentialsMatcher(credentialsMatcher);
return shiroRealm;
}
/**
* 配置 DefaultWebSecurityManager
*/
@Bean
public DefaultWebSecurityManager securityManager() {
DefaultWebSecurityManager securityManager = new DefaultWebSecurityManager();
// 1.Authenticator
securityManager.setAuthenticator(authenticator());
// 2.Realm
List<Realm> realms = new ArrayList<Realm>(16);
realms.add(jwtRealm());
realms.add(shiroRealm());
securityManager.setRealms(realms); // 配置多个realm
// 3.关闭shiro自带的session
DefaultSubjectDAO subjectDAO = new DefaultSubjectDAO();
subjectDAO.setSessionStorageEvaluator(sessionStorageEvaluator());
securityManager.setSubjectDAO(subjectDAO);
return securityManager;
}
@Bean
public Authorizer authorizer(){
//这里是个坑,如果没有这个bean,启动会报错,所以得加上
return new ModularRealmAuthorizer();
}
}
配置JWTUtils
jwtutils作用主要是:
定义token过期时间,创建token的密钥(自定义),自定义存放token的请求头的名称
①签发token
②判断过期时间
③刷新token
package com.szu.utils;
import com.auth0.jwt.JWT;
import com.auth0.jwt.JWTCreator;
import com.auth0.jwt.JWTVerifier;
import com.auth0.jwt.algorithms.Algorithm;
import com.auth0.jwt.exceptions.JWTCreationException;
import com.auth0.jwt.exceptions.JWTDecodeException;
import com.auth0.jwt.exceptions.JWTVerificationException;
import com.auth0.jwt.interfaces.Claim;
import com.auth0.jwt.interfaces.DecodedJWT;
import org.apache.shiro.crypto.SecureRandomNumberGenerator;
import org.springframework.stereotype.Component;
import java.io.UnsupportedEncodingException;
import java.util.Calendar;
import java.util.Date;
import java.util.Map;
@Component
public class JwtUtils {
// 过期时间5分钟
private static final long EXPIRE_TIME = 5*60*1000;
//自己定制密钥
public static final String SECRET = "SECRET_VALUE";
//请求头
public static final String AUTH_HEADER = "X-Authorization-With";
/**
* 验证token是否正确
* @param token
* @param username
* @param secret
* @return
*/
public static boolean verify(String token, String username, String secret){
try{
Algorithm algorithm = Algorithm.HMAC256(secret);
JWTVerifier verifier = JWT.require(algorithm).withClaim("username",username).build();
verifier.verify(token);
return true;
} catch (JWTVerificationException exception){
return false;
} catch (Exception e){
e.printStackTrace();
return false;
}
}
/**
* 获得token中的自定义信息,一般是获取token的username,无需secret解密也能获得
* @param token
* @param filed
* @return
*/
public static String getClaimFiled(String token, String filed){
try{
DecodedJWT jwt = JWT.decode(token);
return jwt.getClaim(filed).asString();
} catch (JWTDecodeException e){
e.printStackTrace();
return null;
}
}
/**
* 生成签名,准确地说是生成token
* @param username
* @param secret
* @return
*/
public static String sign(String username, String secret){
try{
Date date = new Date(System.currentTimeMillis() + EXPIRE_TIME);
Algorithm algorithm = Algorithm.HMAC256(secret);
//附带username,nickname信息
return JWT.create().withClaim("username",username).withExpiresAt(date).sign(algorithm);
} catch (JWTCreationException e){
e.printStackTrace();
return null;
} catch (Exception e){
e.printStackTrace();
return null;
}
}
/**
* 获取token的签发时间
* @param token
* @return
*/
public static Date getIssueAt(String token){
try{
DecodedJWT jwt = JWT.decode(token);
return jwt.getIssuedAt();
} catch (JWTDecodeException e){
e.printStackTrace();
return null;
}
}
/**
* 验证token是否过期
* @param token
* @return
*/
public static boolean isTokenExpired(String token){
Date now = Calendar.getInstance().getTime();
DecodedJWT jwt = JWT.decode(token);
return jwt.getExpiresAt().before(now);
}
/**
* 刷新token的有效期
* @param token
* @param secret
* @return
*/
public static String refreshTokenExpired(String token, String secret){
DecodedJWT jwt = JWT.decode(token); //解析token
Map<String, Claim> claims = jwt.getClaims(); //获取token的参数信息
try{
Date date = new Date(System.currentTimeMillis() + EXPIRE_TIME);
Algorithm algorithm = Algorithm.HMAC256(secret);
JWTCreator.Builder builder = JWT.create().withExpiresAt(date);
for(Map.Entry<String,Claim> entry : claims.entrySet()){
builder.withClaim(entry.getKey(),entry.getValue().asString());
}
return builder.sign(algorithm);
} catch (JWTCreationException | UnsupportedEncodingException e){
e.printStackTrace();
return null;
}
}
/**
* 生成16位随机盐,用在密码加密上面
* @return
*/
public static String generateSalt(){
SecureRandomNumberGenerator secureRandomNumberGenerator = new SecureRandomNumberGenerator();
String hex = secureRandomNumberGenerator.nextBytes(16).toHex();
return hex;
}
}
定义JwtFilter
jwtfilter的作用故名思义,就是一个专门用来拦截含有token请求的过滤器。
对于前端发来的请求,这个过滤器都会进行过滤,具体是咱们的前置拦截处理和后置拦截处理分别返回响应正常状态和添加跨域请求。
除此以外,我们的isAccessAllowed()方法会验证token的正确性,正确则继续往下请求,如果验证出错则返回错误信息,拒绝访问!【具体的流程大家可以康康代码,我都有写注释的噢,花点时间的话还算好理解,讲的话太长了,而我明天还有课啊啊啊】
package com.szu.filter;
import com.szu.shiro.token.JwtToken;
import com.szu.utils.JwtUtils;
import org.apache.shiro.authc.AuthenticationException;
import org.apache.shiro.authc.AuthenticationToken;
import org.apache.shiro.subject.Subject;
import org.apache.shiro.web.filter.authc.BasicHttpAuthenticationFilter;
import org.apache.shiro.web.util.WebUtils;
import org.springframework.http.HttpStatus;
import org.springframework.stereotype.Component;
import org.springframework.web.bind.annotation.RequestMethod;
import javax.servlet.ServletRequest;
import javax.servlet.ServletResponse;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.PrintWriter;
/**
* 自定义的认证过滤器,用来拦截Header中携带token的请求
*/
@Component
public class JwtFilter extends BasicHttpAuthenticationFilter {
/**
* 前置拦截处理
* @param request
* @param response
* @return
* @throws Exception
*/
@Override
protected boolean preHandle(ServletRequest request, ServletResponse response) throws Exception {
//servlet请求与响应的转换
HttpServletRequest httpServletRequest = WebUtils.toHttp(request);
HttpServletResponse httpServletResponse = WebUtils.toHttp(response);
//跨域时会首先发送一个option请求,这里我们给option请求直接返回正常状态
if(httpServletRequest.getMethod().equals(RequestMethod.OPTIONS.name())){
httpServletResponse.setStatus(HttpStatus.OK.value());
return false;
}
return super.preHandle(request, response);
}
/**
* 后置拦截处理
* @param request
* @param response
* @throws Exception
*/
@Override
protected void postHandle(ServletRequest request, ServletResponse response) throws Exception {
//添加跨域支持
this.fillCorsHeader(WebUtils.toHttp(request),WebUtils.toHttp(response));
}
/**
* 过滤器拦截请求的入口方法,所有请求都会进入该方法
* 返回true则允许访问
* @param request
* @param response
* @param mappedValue
* @return
*/
@Override
protected boolean isAccessAllowed(ServletRequest request, ServletResponse response, Object mappedValue) {
// 原用来判断是否是登录请求,在本例中不会拦截登录请求,用来检测Header是否包含token字段
if(this.isLoginRequest(request,response)){
//看看源码,调用了isLoginAttempt()方法
return false; //返回false后进入onAccessDenied()方法,返回错误信息
}
boolean allowed = false;
try{
//检测header里的JWT Token内容是否正确,尝试使用token进行登录
allowed = this.executeLogin(request,response);
} catch (IllegalStateException e){
//未找到token
e.printStackTrace();
System.out.println("未找到token");
} catch (Exception e){
e.printStackTrace();
System.out.println("token检验出错");
}
return allowed || super.isPermissive(mappedValue);
}
/**
* 检测Header中是否包含token字段
* @param request
* @param response
* @return
*/
@Override
protected boolean isLoginAttempt(ServletRequest request, ServletResponse response) {
return ((HttpServletRequest) request).getHeader(JwtUtils.AUTH_HEADER) == null;
}
/**
* 身份验证,检查JWT token是否合法
* @param request
* @param response
* @return
* @throws Exception
*/
@Override
protected boolean executeLogin(ServletRequest request, ServletResponse response) throws Exception {
//从请求头里拿到token
AuthenticationToken token = createToken(request,response);
if(token == null){
String msg = "createToken method implementation returned null. A valid non-null AuthenticationToken must be created in order to execute a login attempt.";
throw new IllegalStateException(msg);
}
try{
Subject subject = getSubject(request,response);
subject.login(token); //让shiro进行登录验证
//没出错则验证成功
return onLoginSuccess(token,subject,request,response);
} catch (AuthenticationException e){
return onLoginFailure(token, e, request, response);
}
}
/**
* 从Header中提取 JWT token
* @param request
* @param response
* @return
*/
@Override
protected AuthenticationToken createToken(ServletRequest request, ServletResponse response) {
HttpServletRequest httpServletRequest = (HttpServletRequest) request;
String authorization = httpServletRequest.getHeader(JwtUtils.AUTH_HEADER);
JwtToken token = new JwtToken(authorization);
return token;
}
/**
* isAccessAllowed()方法返回false,会进入该方法,表示拒绝访问
* @param request
* @param response
* @return
* @throws Exception
*/
@Override
protected boolean onAccessDenied(ServletRequest request, ServletResponse response) throws Exception {
HttpServletResponse httpServletResponse = WebUtils.toHttp(response);
httpServletResponse.setCharacterEncoding("UTF-8");
httpServletResponse.setContentType("application/json;charset=UTF-8");
httpServletResponse.setStatus(HttpStatus.UNAUTHORIZED.value());
PrintWriter writer = httpServletResponse.getWriter();
writer.write("{\"errorCode\":401,\"msg\":\"UNAUTHORIZED\"}");
fillCorsHeader(WebUtils.toHttp(request),httpServletResponse);
return false;
}
/**
* shiro利用 JWT Token 登录成功后,进入该方法
* @param token
* @param subject
* @param request
* @param response
* @return
* @throws Exception
*/
@Override
protected boolean onLoginSuccess(AuthenticationToken token, Subject subject, ServletRequest request, ServletResponse response) throws Exception {
HttpServletResponse httpResponse = WebUtils.toHttp(response);
String newToken = null;
//登录成功后刷新token
if(token instanceof JwtToken) {
newToken = JwtUtils.refreshTokenExpired(token.getCredentials().toString(),JwtUtils.SECRET);
}
if(newToken != null){
httpResponse.setHeader(JwtUtils.AUTH_HEADER,newToken);
}
return true;
}
/**
* 利用 JWT token 登录失败,会进入该方法
* @param token
* @param e
* @param request
* @param response
* @return
*/
@Override
protected boolean onLoginFailure(AuthenticationToken token, AuthenticationException e, ServletRequest request, ServletResponse response) {
return false;//直接返回false,交给后面的 onAccessDenied()方法处理
}
//跨域请求的解决方案之一
protected void fillCorsHeader(HttpServletRequest request, HttpServletResponse response){
response.setHeader("Access-control-Allow-Origin", request.getHeader("Origin"));
response.setHeader("Access-Control-Allow-Methods", "GET,POST,OPTIONS,HEAD");
response.setHeader("Access-Control-Allow-Headers",
request.getHeader("Access-Control-Request-Headers"));
}
}
定义JwtToken
JwtToken这个类实现了AuthenticationToken,如果我们将token作为参数构造出JwtToken对象的话,shiro的主体对象subject进行登录验证时就不用再new 一个UsernamePasswordToken 对象了,毕竟 JwtToken和UsernamePasswordToken 都继承了同一个接口。
所以,说到这JwtToken的作用就显而易见了,目的就是构造一个AuthenticationToken对象以供shiro登录验证
package com.szu.shiro.token;
import com.szu.utils.JwtUtils;
import org.apache.shiro.authc.AuthenticationToken;
/**
* 该类与UsernamePasswordToken差不多,都是AuthenticationToken接口的实现类
* 目的是封装成UsernamePasswordToken让shiro进行登录、登出等操作
*/
public class JwtToken implements AuthenticationToken {
private static final long serialVersionUID = 1L;
//加密后的 JWT token
private String token;
private String username;
public JwtToken(String token){
this.token = token;
this.username = JwtUtils.getClaimFiled(token,"username");
}
@Override
public Object getPrincipal() {
return this.username;
}
@Override
public Object getCredentials() {
return token;
}
}
定义两个Realm
ShiroRealm:其实是模拟的数据库以及查询
JwtRealm:这个自定义的realm就比较关键了。它实现了认证和授权的两个方法。
认证的方法里面,我们获取到JwtToken类的token后,获取token里面的参数信息(暂时只有username),然后查询“数据库”判断,没有则返回错误信息,即抛出异常,让subject.login(token)所在的方法捕获到异常进行处理。认证通过,即用户名所对应的对象存在,则返回SimpleAuthenticationInfo对象,让请求能够继续请求loginController
授权的方法中,则是获取到token携带的的username信息来查询其拥有的权限,然后进行设置即可,至此,我们的shiro作用就发挥得差不多了
[realm是由shiroConfig中的securityManager调用的]
JwtRealm.java
package com.szu.shiro.realm;
import com.szu.db.ShiroRealm;
import com.szu.entity.User;
import com.szu.entity.UserEntity;
import com.szu.mapper.UserMapper;
import com.szu.shiro.token.JwtToken;
import org.apache.shiro.SecurityUtils;
import org.apache.shiro.authc.AccountException;
import org.apache.shiro.authc.AuthenticationException;
import org.apache.shiro.authc.AuthenticationInfo;
import org.apache.shiro.authc.AuthenticationToken;
import org.apache.shiro.authc.LockedAccountException;
import org.apache.shiro.authc.SimpleAuthenticationInfo;
import org.apache.shiro.authc.UnknownAccountException;
import org.apache.shiro.authz.AuthorizationInfo;
import org.apache.shiro.authz.SimpleAuthorizationInfo;
import org.apache.shiro.realm.AuthorizingRealm;
import org.apache.shiro.subject.PrincipalCollection;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.stereotype.Component;
import java.util.Set;
@Component
public class JwtRealm extends AuthorizingRealm {
/**
* 限定这个 Realm 只处理我们自定义的 JwtToken
*/
@Override
public boolean supports(AuthenticationToken token) {
return token instanceof JwtToken;
}
/**
* 此处的 SimpleAuthenticationInfo 可返回任意值,密码校验时不会用到它
*/
@Override
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken authcToken)
throws AuthenticationException {
JwtToken jwtToken = (JwtToken) authcToken;
if (jwtToken.getPrincipal() == null) {
throw new AccountException("JWT token参数异常!");
}
// 从 JwtToken 中获取当前用户
String username = jwtToken.getPrincipal().toString();
// 查询数据库获取用户信息,此处使用 Map 来模拟数据库
UserEntity user = ShiroRealm.userMap.get(username);
// 用户不存在
if (user == null) {
throw new UnknownAccountException("用户不存在!");
}
// 用户被锁定
if (user.getLocked()) {
throw new LockedAccountException("该用户已被锁定,暂时无法登录!");
}
SimpleAuthenticationInfo info = new SimpleAuthenticationInfo(user, username, getName());
return info;
}
@Override
protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principals) {
// 获取当前用户
UserEntity currentUser = (UserEntity) SecurityUtils.getSubject().getPrincipal();
// UserEntity currentUser = (UserEntity) principals.getPrimaryPrincipal();
// 查询数据库,获取用户的角色信息
Set<String> roles = ShiroRealm.roleMap.get(currentUser.getName());
// 查询数据库,获取用户的权限信息
Set<String> perms = ShiroRealm.permMap.get(currentUser.getName());
SimpleAuthorizationInfo info = new SimpleAuthorizationInfo();
info.setRoles(roles);
info.setStringPermissions(perms);
return info;
}
}
ShiroRealm.java
此处存储的密码都是被shiro加密过的
String password = new SimpleHash("MD5", user.getPassword(), user.getUserName()
package com.szu.db;
import java.util.HashMap;
import java.util.HashSet;
import java.util.Map;
import java.util.Set;
import com.szu.entity.UserEntity;
import org.apache.shiro.SecurityUtils;
import org.apache.shiro.authc.AuthenticationException;
import org.apache.shiro.authc.AuthenticationInfo;
import org.apache.shiro.authc.AuthenticationToken;
import org.apache.shiro.authc.LockedAccountException;
import org.apache.shiro.authc.SimpleAuthenticationInfo;
import org.apache.shiro.authc.UnknownAccountException;
import org.apache.shiro.authc.UsernamePasswordToken;
import org.apache.shiro.authz.AuthorizationInfo;
import org.apache.shiro.authz.SimpleAuthorizationInfo;
import org.apache.shiro.realm.AuthorizingRealm;
import org.apache.shiro.subject.PrincipalCollection;
import org.apache.shiro.util.ByteSource;
/**
* 同时开启身份验证和权限验证,需要继承 AuthorizingRealm
* 并实现其 doGetAuthenticationInfo()和 doGetAuthorizationInfo 两个方法
*/
@SuppressWarnings("serial")
public class ShiroRealm extends AuthorizingRealm {
public static Map<String, UserEntity> userMap = new HashMap<String, UserEntity>(16);
public static Map<String, Set<String>> roleMap = new HashMap<String, Set<String>>(16);
public static Map<String, Set<String>> permMap = new HashMap<String, Set<String>>(16);
static {
UserEntity user1 = new UserEntity(1L, "gorho", "dd524c4c66076d1fa07e1fa1c94a91233772d132", "灰先生", false);
UserEntity user2 = new UserEntity(2L, "plum", "cce369436bbb9f0325689a3a6d5d6b9b8a3f39a0", "李先生", false);
userMap.put("gorho", user1);
userMap.put("plum", user2);
roleMap.put("gorho", new HashSet<String>() {
{
add("admin");
}
});
roleMap.put("plum", new HashSet<String>() {
{
add("guest");
}
});
permMap.put("plum", new HashSet<String>() {
{
add("article:read");
}
});
}
/**
* 限定这个 Realm 只处理 UsernamePasswordToken
*/
@Override
public boolean supports(AuthenticationToken token) {
return token instanceof UsernamePasswordToken;
}
/**
* 查询数据库,将获取到的用户安全数据封装返回
*/
@Override
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken token) throws AuthenticationException {
// 从 AuthenticationToken 中获取当前用户
String username = (String) token.getPrincipal();
// 查询数据库获取用户信息,此处使用 Map 来模拟数据库
UserEntity user = userMap.get(username);
// 用户不存在
if (user == null) {
throw new UnknownAccountException("用户不存在!");
}
// 用户被锁定
if (user.getLocked()) {
throw new LockedAccountException("该用户已被锁定,暂时无法登录!");
}
// 使用用户名作为盐值
ByteSource credentialsSalt = ByteSource.Util.bytes(username);
/**
* 将获取到的用户数据封装成 AuthenticationInfo 对象返回,此处封装为 SimpleAuthenticationInfo 对象。
* 参数1. 认证的实体信息,可以是从数据库中获取到的用户实体类对象或者用户名
* 参数2. 查询获取到的登录密码
* 参数3. 盐值
* 参数4. 当前 Realm 对象的名称,直接调用父类的 getName() 方法即可
*/
SimpleAuthenticationInfo info = new SimpleAuthenticationInfo(user, user.getPassword(), credentialsSalt,
getName());
return info;
}
/**
* 查询数据库,将获取到的用户的角色及权限信息返回
*/
@Override
protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principals) {
// 获取当前用户
UserEntity currentUser = (UserEntity) SecurityUtils.getSubject().getPrincipal();
// UserEntity currentUser = (UserEntity)principals.getPrimaryPrincipal();
// 查询数据库,获取用户的角色信息
Set<String> roles = roleMap.get(currentUser.getName());
// 查询数据库,获取用户的权限信息
Set<String> perms = permMap.get(currentUser.getName());
SimpleAuthorizationInfo info = new SimpleAuthorizationInfo();
info.setRoles(roles);
info.setStringPermissions(perms);
return info;
}
}
两个"工具人"
JwtCredentialsMatcher.java
该类的主要作用就是验证JwtToken的内容是否合法,是realm的凭证校验器,不自定义也可以的,换成HashedCredentialsMatcher并设置加密方式,散列次数什么的就行了
package com.szu.utils;
import com.auth0.jwt.JWT;
import com.auth0.jwt.JWTVerifier;
import com.auth0.jwt.algorithms.Algorithm;
import com.auth0.jwt.exceptions.JWTVerificationException;
import org.apache.shiro.authc.AuthenticationInfo;
import org.apache.shiro.authc.AuthenticationToken;
import org.apache.shiro.authc.credential.CredentialsMatcher;
import org.springframework.stereotype.Component;
@Component
public class JwtCredentialsMatcher implements CredentialsMatcher {
/**
* JwtCredentialsMatcher只需验证JwtToken内容是否合法
*/
@Override
public boolean doCredentialsMatch(AuthenticationToken authenticationToken, AuthenticationInfo authenticationInfo) {
String token = authenticationToken.getCredentials().toString();
String username = authenticationToken.getPrincipal().toString();
try {
Algorithm algorithm = Algorithm.HMAC256(JwtUtils.SECRET);
JWTVerifier verifier = JWT.require(algorithm).withClaim("username", username).build();
verifier.verify(token);
return true;
} catch (JWTVerificationException e) {
e.printStackTrace();
} catch (Exception e){
e.printStackTrace();
}
return false;
}
}
MultiRealmAuthenticator.java
MultiRealmAuthenticator 用来解决Shiro中出现的具体的认证异常无法正常返回,仅返回父类 AuthenticationException 的问题。
package com.szu.shiro.realm;
import org.apache.shiro.authc.AuthenticationException;
import org.apache.shiro.authc.AuthenticationInfo;
import org.apache.shiro.authc.AuthenticationToken;
import org.apache.shiro.authc.pam.AuthenticationStrategy;
import org.apache.shiro.authc.pam.ModularRealmAuthenticator;
import org.apache.shiro.realm.Realm;
import org.slf4j.Logger;
import org.slf4j.LoggerFactory;
import org.springframework.stereotype.Component;
import java.util.Collection;
@Component
public class MultiRealmAuthenticator extends ModularRealmAuthenticator {
private static final Logger log = LoggerFactory.getLogger(MultiRealmAuthenticator.class);
@Override
protected AuthenticationInfo doMultiRealmAuthentication(Collection<Realm> realms, AuthenticationToken token)
throws AuthenticationException {
AuthenticationStrategy strategy = getAuthenticationStrategy();
AuthenticationInfo aggregate = strategy.beforeAllAttempts(realms, token);
if (log.isTraceEnabled()) {
log.trace("Iterating through {} realms for PAM authentication", realms.size());
}
AuthenticationException authenticationException = null;
for (Realm realm : realms) {
aggregate = strategy.beforeAttempt(realm, token, aggregate);
if (realm.supports(token)) {
log.trace("Attempting to authenticate token [{}] using realm [{}]", token, realm);
AuthenticationInfo info = null;
try {
info = realm.getAuthenticationInfo(token);
} catch (AuthenticationException e) {
authenticationException = e;
if (log.isDebugEnabled()) {
String msg = "Realm [" + realm
+ "] threw an exception during a multi-realm authentication attempt:";
log.debug(msg, e);
}
}
aggregate = strategy.afterAttempt(realm, token, info, aggregate, authenticationException);
} else {
log.debug("Realm [{}] does not support token {}. Skipping realm.", realm, token);
}
}
if (authenticationException != null) {
throw authenticationException;
}
aggregate = strategy.afterAllAttempts(token, aggregate);
return aggregate;
}
}
全局异常处理
这个类主要是用来捕获异常并返回不同异常的错误信息,方便前端判断并处理。但是这里只是简单提了,具体的教程我会以后写一篇的哈,大家先有这个前后端分离的概念就行
package com.szu.exception;
import com.szu.entity.dto.BaseResponse;
import org.apache.shiro.ShiroException;
import org.springframework.web.bind.annotation.RestControllerAdvice;
import org.springframework.web.bind.annotation.ExceptionHandler;
import javax.servlet.http.HttpServletRequest;
@RestControllerAdvice
public class MyExceptionHandler {
// 捕捉shiro的异常
@ExceptionHandler(ShiroException.class)
public Object handleShiroException(ShiroException e) {
BaseResponse<Object> ret = new BaseResponse<Object>();
ret.setErrCode(401);
ret.setMsg(e.getMessage());
return ret;
}
// 捕捉其他所有异常
@ExceptionHandler(Exception.class)
public Object globalException(HttpServletRequest request, Throwable ex) {
BaseResponse<Object> ret = new BaseResponse<Object>();
ret.setErrCode(401);
ret.setMsg(ex.getMessage());
return ret;
}
}
两个controller
LoginController.java
登录的控制器,在controller中用shiro进行登录的验证判断
该控制器方法主要想体现身份的权限控制
package com.szu.controller;
import com.szu.entity.dto.BaseResponse;
import com.szu.utils.JwtUtils;
import org.apache.shiro.SecurityUtils;
import org.apache.shiro.authc.*;
import org.apache.shiro.subject.Subject;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.PostMapping;
import org.springframework.web.bind.annotation.RequestParam;
import org.springframework.web.bind.annotation.RestController;
import javax.servlet.ServletResponse;
import javax.servlet.http.HttpServletResponse;
@RestController
public class LoginController {
@PostMapping(value = "/login")
public Object userLogin(@RequestParam(name = "username", required = true) String userName,
@RequestParam(name = "password", required = true) String password, ServletResponse response) {
// 获取当前用户主体
Subject subject = SecurityUtils.getSubject();
String msg = null;
boolean loginSuccess = false;
// 将用户名和密码封装成 UsernamePasswordToken 对象
UsernamePasswordToken token = new UsernamePasswordToken(userName, password);
try {
subject.login(token);
msg = "登录成功。";
loginSuccess = true;
} catch (UnknownAccountException uae) {
// 账号不存在
msg = "用户名与密码不匹配,请检查后重新输入!";
} catch (IncorrectCredentialsException ice) {
// 账号与密码不匹配
msg = "用户名与密码不匹配,请检查后重新输入!";
} catch (LockedAccountException lae) {
// 账号已被锁定
msg = "该账户已被锁定,如需解锁请联系管理员!";
} catch (AuthenticationException ae) {
// 其他身份验证异常
msg = "登录异常,请联系管理员!";
}
BaseResponse<Object> ret = new BaseResponse<Object>();
if (loginSuccess) {
// 若登录成功,签发 JWT token
String jwtToken = JwtUtils.sign(userName, JwtUtils.SECRET);
// 将签发的 JWT token 设置到 HttpServletResponse 的 Header 中
((HttpServletResponse) response).setHeader(JwtUtils.AUTH_HEADER, jwtToken);
//
ret.setErrCode(0);
ret.setMsg(msg);
return ret;
} else {
ret.setErrCode(401);
ret.setMsg(msg);
return ret;
}
}
@GetMapping("/logout")
public Object logout() {
BaseResponse<Object> ret = new BaseResponse<Object>();
ret.setErrCode(0);
ret.setMsg("退出登录");
return ret;
}
}
ArticleController.java
这个控制器类方法可以在用户登录后返回简单的示意信息
主要想体现对用户权限的控制
package com.szu.controller;
import com.szu.entity.dto.BaseResponse;
import org.apache.shiro.authz.annotation.RequiresPermissions;
import org.apache.shiro.authz.annotation.RequiresRoles;
import org.springframework.ui.ModelMap;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.RestController;
@RestController
@RequestMapping("/article")
public class ArticleController {
@GetMapping("/delete")
@RequiresRoles(value = {
"admin" })
public Object deleteArticle(ModelMap model) {
BaseResponse<Object> ret = new BaseResponse<Object>();
ret.setErrCode(0);
ret.setMsg("文章删除成功!");
return ret;
}
@GetMapping("/read")
@RequiresPermissions(value = {
"article:read" })
public Object readArticle(ModelMap model) {
BaseResponse<Object> ret = new BaseResponse<Object>();
ret.setErrCode(0);
ret.setMsg("请您鉴赏!");
return ret;
}
}
接口测试
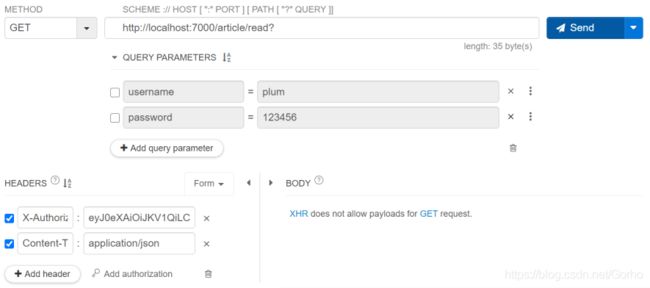
启动springboot后,任意选一个你喜欢的接口测试工具,首先进行登录测试
如图,post请求登录

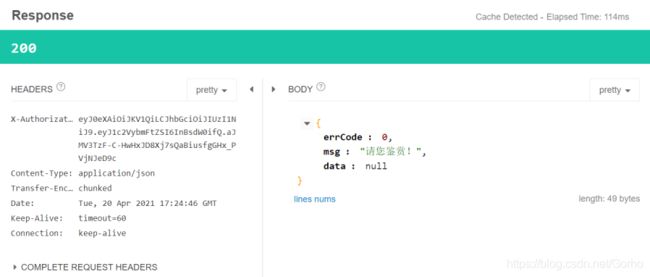
返回结果如下:
注意,左侧的请求头里面出现了我们的token数据,说明咱们的代码没有白写(crtl c+v)

然后复制我们的token,加到请求头中,我们就可以在时效内访问文章啦【电脑要没电了,剩下的不演示了】
 返回成功!!!
返回成功!!!
兄弟们,这就是简单的前后端分离的shiro+jwt的鉴权控制了,代码只要复制就能跑的,大家不妨尝试一下!!重要地方都有注释
如果有用的话记得给文章点赞、收藏、转发哈,下一篇我们讲《前后端分离之全局异常处理并返回状态码》或者 《mybatis-plus的crud》
文章参考自https://blog.csdn.net/pengjunlee/article/details/95600843!良心教程,帮助我成功理解了!!