k8s——kubernetes 部署dashboard
1.dashboard概述
在 Kubernetes 社区中,有一个很受欢迎的 Dashboard 项目,它可以给用户提供一个可视化的 Web 界面来查看当前集群的各种信息。用户可以用 Kubernetes Dashboard 部署容器化的应用、监控应用的状态、执行故障排查任务以及管理 Kubernetes 各种资源。
2.部署dashboard实验
1.实验环境
多节点k8s,master01,node01,node02
2. 实验目的
通过搭建的dashboard来通过web界面直观显示参数
3.实验步骤
1.master01
[root@master01 ~]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
192.168.200.110 Ready 13h v1.12.3
192.168.200.120 Ready 13h v1.12.3
[root@master01 ~]# cd k8s/
[root@master01 k8s]# mkdir dashboard
[root@master01 k8s]# cd dashboard/
[root@master01 dashboard]# ls
[root@master01 dashboard]# rz -E
rz waiting to receive.
[root@master01 dashboard]# ls
dashboard-configmap.yaml dashboard-rbac.yaml dashboard-service.yaml
dashboard-controller.yaml dashboard-secret.yaml k8s-admin.yaml
2.查看各文件内容
[root@master01 dashboard]# vim dashboard-rbac.yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard-minimal
namespace: kube-system
rules:
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics from heapster.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:"]
verbs: ["get"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard-minimal
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system
[root@master01 dashboard]# vim dashboard-secret.yaml
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
# Allows editing resource and makes sure it is created first.
addonmanager.kubernetes.io/mode: EnsureExists
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
# Allows editing resource and makes sure it is created first.
addonmanager.kubernetes.io/mode: EnsureExists
name: kubernetes-dashboard-key-holder
namespace: kube-system
type: Opaque
[root@master01 dashboard]# vim dashboard-configmap.yaml
apiVersion: v1
kind: ConfigMap
metadata:
labels:
k8s-app: kubernetes-dashboard
# Allows editing resource and makes sure it is created first.
addonmanager.kubernetes.io/mode: EnsureExists
name: kubernetes-dashboard-settings
namespace: kube-system
[root@master01 dashboard]# vim dashboard-controller.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
annotations:
scheduler.alpha.kubernetes.io/critical-pod: ''
seccomp.security.alpha.kubernetes.io/pod: 'docker/default'
spec:
priorityClassName: system-cluster-critical
containers:
- name: kubernetes-dashboard
image: siriuszg/kubernetes-dashboard-amd64:v1.8.3
resources:
limits:
cpu: 100m
memory: 300Mi
requests:
cpu: 50m
memory: 100Mi
ports:
- containerPort: 8443
protocol: TCP
args:
# PLATFORM-SPECIFIC ARGS HERE
- --auto-generate-certificates
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
- name: tmp-volume
mountPath: /tmp
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {
}
serviceAccountName: kubernetes-dashboard
tolerations:
- key: "CriticalAddonsOnly"
operator: "Exists"
[root@master01 dashboard]# vim dashboard-service.yaml
apiVersion: v1
kind: Service
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
type: NodePort
selector:
k8s-app: kubernetes-dashboard
ports:
- port: 443
targetPort: 8443
nodePort: 30001
[root@master01 dashboard]# vim k8s-admin.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: dashboard-admin
namespace: kube-system
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: dashboard-admin
subjects:
- kind: ServiceAccount
name: dashboard-admin
namespace: kube-system
roleRef:
kind: ClusterRole
name: cluster-admin
apiGroup: rbac.authorization.k8s.io
3.通过yaml文件创建资源
[root@master01 dashboard]# kubectl create -f dashboard-rbac.yaml #授权管理创建资源
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
[root@master01 dashboard]# kubectl create -f dashboard-secret.yaml #证书验证创建资源
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-key-holder created
[root@master01 dashboard]# kubectl create -f dashboard-configmap.yaml #配置文件创建资源
configmap/kubernetes-dashboard-settings created
[root@master01 dashboard]# kubectl create -f dashboard-controller.yaml #控制创建资源
serviceaccount/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
[root@master01 dashboard]# kubectl create -f dashboard-service.yaml #服务创建服务资源
service/kubernetes-dashboard created
4.查看资源
[root@master01 dashboard]# kubectl get pods -n kube-system #完成后查看创建在指定的kube-system命名空间下
NAME READY STATUS RESTARTS AGE
kubernetes-dashboard-7dffbccd68-n4hgt 1/1 Running 0 3h23m #查看如何访问
[root@master01 dashboard]# kubectl get pods,svc -n kube-system #同时查看pods和service
NAME READY STATUS RESTARTS AGE
pod/kubernetes-dashboard-7dffbccd68-n4hgt 1/1 Running 0 3h23m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes-dashboard NodePort 10.0.0.238 443:30001/TCP 3h28m
[root@master01 dashboard]# kubectl get pods -n kube-system -o wide #查看创建在哪个节点
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE
kubernetes-dashboard-7dffbccd68-n4hgt 1/1 Running 0 3h23m 172.17.4.2 192.168.200.120
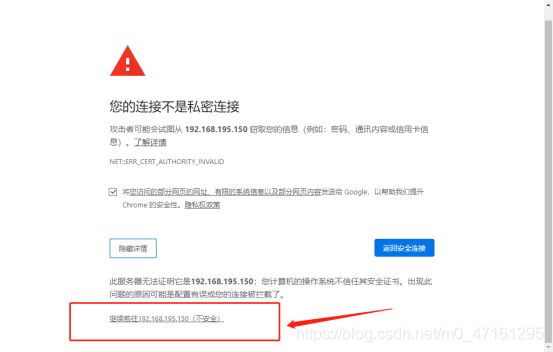
使用谷歌浏览器访问https://192.168.200.120:30001/
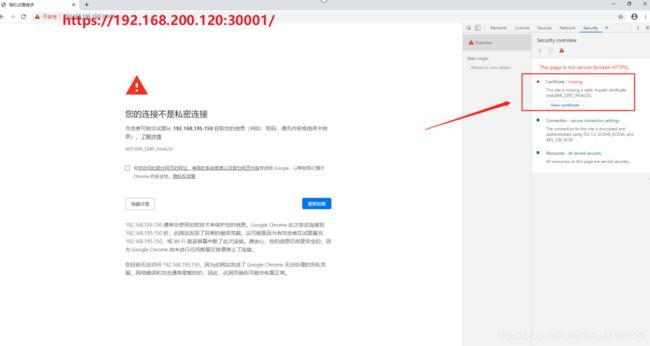
谷歌浏览器无法访问的问题
[root@localhost dashboard]# vim dashboard-cert.sh
cat > dashboard-csr.json <{
"CN": "Dashboard",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "BeiJing",
"ST": "BeiJing"
}
]
}
EOF
K8S_CA=$1
cfssl gencert -ca=$K8S_CA/ca.pem -ca-key=$K8S_CA/ca-key.pem -config=$K8S_CA/ca-config.json -profile=kubernetes dashboard-csr.json | cfssljson -bare dashboard
kubectl delete secret kubernetes-dashboard-certs -n kube-system
kubectl create secret generic kubernetes-dashboard-certs --from-file=./ -n kube-system
dashboard-controller.yaml 增加证书两行
[root@localhost dashboard]# vim dashboard-controller.yaml
args:
# PLATFORM-SPECIFIC ARGS HERE
- --auto-generate-certificates
- --tls-key-file=dashboard-key.pem ###
- --tls-cert-file=dashboard.pem ###
[root@localhost dashboard]# bash dashboard-cert.sh /root/k8s/k8s-cert/
2020/10/05 15:29:08 [INFO] generate received request
2020/10/05 15:29:08 [INFO] received CSR
2020/10/05 15:29:08 [INFO] generating key: rsa-2048
2020/10/05 15:29:09 [INFO] encoded CSR
2020/10/05 15:29:09 [INFO] signed certificate with serial number 150066859036029062260457207091479364937405390263
2020/10/05 15:29:09 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
secret "kubernetes-dashboard-certs" deleted
secret/kubernetes-dashboard-certs created
重新部署
[root@localhost dashboard]# kubectl apply -f dashboard-controller.yaml
Warning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl apply
serviceaccount/kubernetes-dashboard configured
Warning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl apply
deployment.apps/kubernetes-dashboard configured
[root@localhost dashboard]# kubectl create -f k8s-admin.yaml
serviceaccount/dashboard-admin created
clusterrolebinding.rbac.authorization.k8s.io/dashboard-admin created
保存
[root@master01 dashboard]# kubectl get secret -n kube-system
NAME TYPE DATA AGE
dashboard-admin-token-q88zn kubernetes.io/service-account-token 3 4h7m
default-token-d2l4p kubernetes.io/service-account-token 3 20h
kubernetes-dashboard-certs Opaque 11 3h42m
kubernetes-dashboard-key-holder Opaque 2 3h45m
kubernetes-dashboard-token-l722w kubernetes.io/service-account-token 3 3h40m
查看令牌
[root@master01 dashboard]# kubectl describe secret dashboard-admin-token-q88zn -n kube-system
Name: dashboard-admin-token-q88zn
Namespace: kube-system
Labels:
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: 333fffd2-0954-11eb-b56a-000c296df6f1
Type: kubernetes.io/service-account-token
Data
====
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tcTg4em4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMzMzZmZmZDItMDk1NC0xMWViLWI1NmEtMDAwYzI5NmRmNmYxIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.AMUqiDTTZjJWmkUK72hh59XqyzBt_wGc_h7w9zOadtBLZQM21UDjNaowAuJlbjapKv0M63KjGk9Tv_UDPvQiFICNtu-JcVAokCpuB92xv-kED_pgbHCMLLyF8o2m0DPuZ6Ph6evpdX3mDEL7aNZ-wNBrlbLqJPKquEaBS0fb3UNLfkMNMznPNjFBuWe36ekxbXlBRZhCq0REz74q-MAa-2IwE2qxlUTyJOp3sccgivc6LafHZG0lUagLDqAxc9jdK5g2VYnXJHLSeZLUgcFStTllVTBKdl4wUHpfz_hssOjrivLZOZRr_aeRyKYDjG3r94q0C1eDOGL38pNpiSWdTQ
ca.crt: 1359 bytes
namespace: 11 bytes
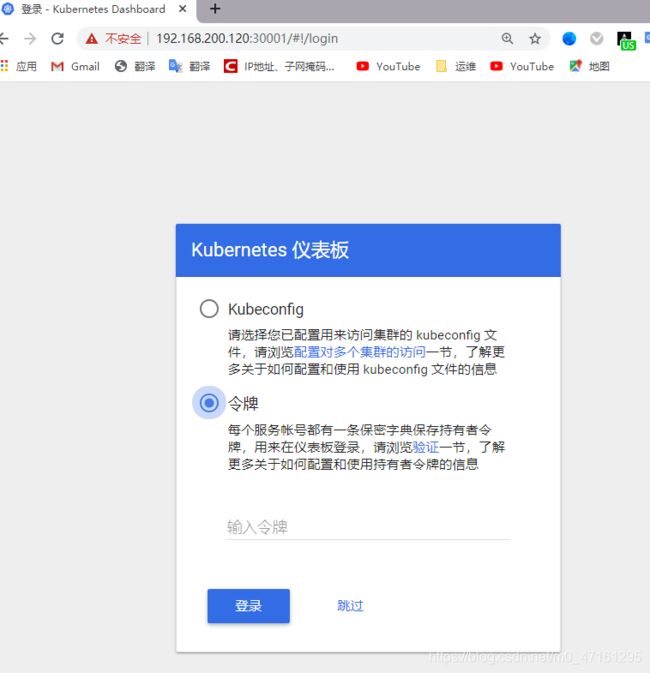
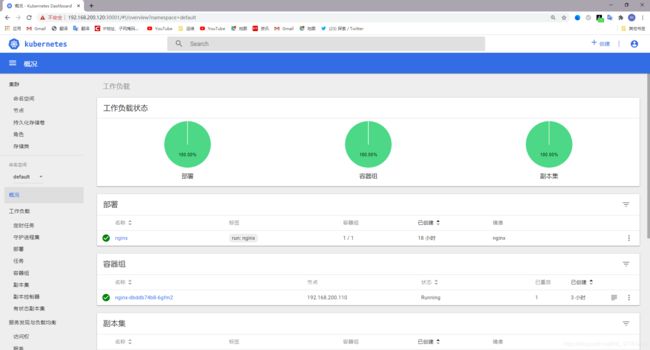
输入令牌秘钥
eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tcTg4em4iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMzMzZmZmZDItMDk1NC0xMWViLWI1NmEtMDAwYzI5NmRmNmYxIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.AMUqiDTTZjJWmkUK72hh59XqyzBt_wGc_h7w9zOadtBLZQM21UDjNaowAuJlbjapKv0M63KjGk9Tv_UDPvQiFICNtu-JcVAokCpuB92xv-kED_pgbHCMLLyF8o2m0DPuZ6Ph6evpdX3mDEL7aNZ-wNBrlbLqJPKquEaBS0fb3UNLfkMNMznPNjFBuWe36ekxbXlBRZhCq0REz74q-MAa-2IwE2qxlUTyJOp3sccgivc6LafHZG0lUagLDqAxc9jdK5g2VYnXJHLSeZLUgcFStTllVTBKdl4wUHpfz_hssOjrivLZOZRr_aeRyKYDjG3r94q0C1eDOGL38pNpiSWdTQ