- nodejs 安装node-sass
kino的编程笔记
vuenodejsnpmnode-sassvue
installnode-sass作用检验node-sass是否安装以及是否安装成功安装node-sass配置淘宝镜像安装node-sass的命令作用Sass是一种预处理器脚本语言,可以解释或编译成层叠样式表(CSS)检验node-sass是否安装以及是否安装成功node-sass-v表示已经安装或安装成功表示没有安装或者安装失败安装node-sass配置淘宝镜像设置淘宝镜像的二进制站点setSAS
- IEC60870-5-104项目应用
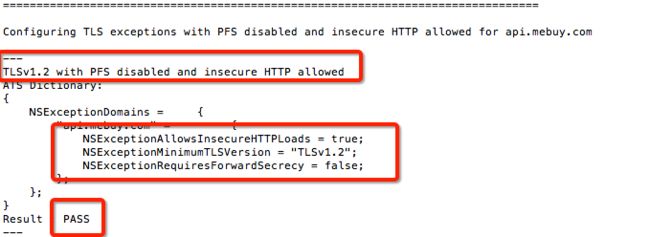
Spume--
C开源协议网络协议c++java
IEC60870-5-104项目应用前言1.准备工作2.实现步骤2.1引入必要的库和头文件2.2创建服务器实例2.3配置服务器的本地地址2.4设置服务器模式2.5获取应用层和连接参数2.6配置回调函数2.6.1时钟同步处理:2.6.2查询命令处理:2.6.3ASDU消息处理:2.6.4连接请求处理:2.6.5连接事件处理:2.7启动服务器服务2.8循环任务2.9停止服务器服务总结我是将军我一直都在
- Python 魔法学院 - 第32篇:Python ORM框架 ⭐⭐⭐
星核日记
《Python魔法学院》python数据库pycharm开发语言windows
目录引言1.ORM框架概述1.1什么是ORM?比喻:ORM就像一位翻译官1.2ORM的优势2.[SQLAlchemy](https://docs.sqlalchemy.org.cn/en/20/intro.html)2.1SQLAlchemy简介2.2SQLAlchemy的核心组件2.3SQLAlchemy示例2.3.1安装SQLAlchemy2.3.2定义模型2.3.3插入数据2.3.4查询数据
- c与python-Python与Cpython
weixin_37988176
甚至我在理解CPython,JPython,IronPython,PyPy之间的区别时也遇到了相同的问题。因此,在开始解释之前,我愿意清除三件事:Python:这是一门语言,它仅说明/描述如何向解释器(接受您的python代码的程序)传达/表达自己。实施:这完全与解释器的编写方式有关,特别是有关哪种语言以及最终使用的语言。字节码:它是由程序(通常称为虚拟机)而不是"真实”计算机(即硬件处理器)处理
- 悬浮按钮和可交互提示
巅峰小学生
MaterialDesignandroidMaterialDesign简体中文版
目录步骤导包布局文件中使用点击事件(和Button一样)步骤导包app.builddependencies{......implementation'com.android.support:design:28.0.0'}布局文件中使用说明:android:elevation=“8dp”设置高度值,高度值越大,投影范围越大,投影效果越淡;点击事件(和Button一样)mFloatBtn.setOnC
- CXCardView:打造流畅的卡片交互体验
裘珑鹏Island
CXCardView:打造流畅的卡片交互体验CXCardViewEasy,simpleandcard-styleoverlayonscreentodelivermessagetousers.项目地址:https://gitcode.com/gh_mirrors/cx/CXCardView随着移动应用界面设计向着更加动态和互动的方向发展,CXCardView——一个简洁而强大的Objective-C
- 探索ImGui Knobs:打造直观的交互式控制面板
倪澄莹George
探索ImGuiKnobs:打造直观的交互式控制面板imgui-knobsKnobwidgetsforDearImGui项目地址:https://gitcode.com/gh_mirrors/im/imgui-knobs在数字创意和应用程序开发的世界中,用户体验往往决定了一个应用的成功与否。今天,我们要介绍一款神器——ImGuiKnobs,它将为你的C++项目增添一抹创新的光彩。项目介绍ImGuiK
- mysql死锁排查_mysql 死锁问题排查
字节全栈_BjO
mysqlandroid数据库
应用访问Mysql数据库的时候,如果业务逻辑写的不严谨,不规范,就会发生死锁,如果此业务逻辑调用并发高,则业务日志经常会有死锁的错误日志产生。应用发生死锁,于是dba就去排查,看数据库的错误日志,就会发现,没有任何关于死锁的日志告警,这是因为默认配置情况下,数据库是不打印任何死锁的日志信息。那如何去排查应用的死锁问题呢,下面给大家详细介绍。先看看关于死锁信息打印的参数,默认是关闭mysql>sho
- 深度学习目标检测中的_单目测距原理与实现 关键点及改进建议
QQ_767172261
单目测距深度学习目标检测人工智能
深度学习目标检测中的_单目测距原理与实现关键点及改进建议文章目录单目测距的进一步解释1.焦距的确定2.物体宽度\(W\)的获取3.图像处理技巧4.提高性能的建议5.实现代码中的注释添加一、前言单目视觉测距:网上有很多关于单目测距的文章,主要借鉴的是OpenCV学习笔记(二十一)——简单的单目视觉测距尝试和单目摄像机测距(python+opencv)两篇文章,在这里特别作出说明。工作环境:Ubunt
- gitlab安装及邮箱配置和常用使用
Gen邓艮艮
gitlablinux环境软件gitlab
1.安装GitLab注意关闭网络防火墙和网络安全组#1.下载镜像wgethttps://mirrors.tuna.tsinghua.edu.cn/gitlab-ce/yum/el7/gitlab-ce-14.10.5-ce.0.el7.x86_64.rpm#2.安装依赖yuminstall-ypolicycoreutilsopenssh-serveropenssh-clientspostfixpo
- ROS学习笔记-roslaunch文件的编写&用sh脚本控制launch文件启动顺序
诗筱涵
ROS无人机-a-个人笔记
转载自:https://mp.weixin.qq.com/s?__biz=MzUyMTkxODQyOQ==&mid=2247484719&idx=1&sn=27b3a01c295ae256dc69d805fd5904ba&chksm=f9d2879dcea50e8b71b78d8b69750d282055173ea65494342e983088276859b7c4fe227f21f1&scene=
- MySQL底层概述—5.InnoDB参数优化
心上之秋
mysql数据库
大纲1.内存相关参数优化(1)缓冲池内存大小配置(2)配置多个BufferPool实例(3)Chunk(块)大小配置(4)InnoDB缓存性能评估(5)Page管理相关参数(6)ChangeBuffer相关参数优化2.日志相关参数优化(1)日志缓冲区相关参数配置(2)日志文件参数优化3.IO线程相关参数优化(1)查询缓存相关的参数(2)脏页刷盘相关的参数(3)LRU链表相关的参数(4)脏页刷盘相关
- CSDN原力值提升秘籍:解锁社区活跃新姿势
喜-喜
csdn原力值
在CSDN这个技术交流的大舞台上,原力值不仅是个人活跃度的象征,更是开启更多权益与福利的钥匙。最近,我出于自身需求,一头扎进了提升原力值的研究中,经过多方探索与资料整理,现在就迫不及待地把这些干货分享给大家。一、原力值提升指南(一)净化社区,举报先行 在信息洪流中,难免会有一些低质量内容鱼目混珠。当你发现低质量博客、下载资源等劣质内容时,CSDN的举报功能就是你的“清理武器”。 规则说明:
- 正则表达式 匹配特定字符后的所有字符
zzyh123456
正则表达式数据库mysql
在处理文本数据时,正则表达式(RegularExpressions,简称Regex)是一种非常强大的工具,它可以用来搜索、匹配和替换文本中符合特定模式的字符串。首先,明确我们的目标是匹配完整的URL,并获取它之后的所有字符。由于正则表达式默认是贪婪的(即尽可能多地匹配字符),我们可以直接编写一个模式来匹配这个URL后跟任意数量的任意字符。以下是一个可能的正则表达式示例:regexhttps:\/\
- 高通modem架构_高通神经网络处理引擎SNPE分析与评测
weixin_39811036
高通modem架构
骁龙(SnapDragon)神经处理引擎(SNPE)是一个针对高通骁龙加速深层神经网络的运行时软件,高通在CSDN和其官网都提供了下载。本文以SNPE1.23为基准,将结合高通官方的SDK说明文档(高通在CSDN也提供了开发者社区,中文社区论坛,以及SNPE部分文档),介绍SNPE这一高通官方的神经网络处理引擎开发包。开发中有疑问可在高通的CreatePoint检索相关文档或者在SNPE论坛提交疑
- Docker 容器网络问题排查与最佳实践 - PushGateway 部署案例分析
qustion1.问题背景在数据中心部署PrometheusPushGateway服务时,遇到了一个典型的容器网络访问问题。相同的部署配置在不同数据中心呈现出不同的网络访问结果,本文将详细分析问题的排查过程和解决方案。2.问题现象搭建典型的pushgateway服务,使用了nginx与pushgateway整合,为什么整合呢?主要原因是安全扫描扫描出来很多pushgateway的安全漏洞,也木有经
- Linux C++ 开发9 - 手把手教你使用gprof性能分析工具
c++
1.什么是gprof?2.gprof的用法2.1.编译程序2.2.运行程序2.3.生成分析报告2.4.gprof常用参数说明2.5.分析报告解读2.5.1.Flatprofile各个字段的含义2.5.2.Callgraph各个字段的含义3.Demo演示3.1.demo04.cpp源码3.2.编译、运行和分析3.3.查看分析报告1.什么是gprof?gprof这是一个GNU的性能分析工具,它是GCC
- Kubernetes 配置Pod使用代理上网
配置KubernetesPod使用代理上网在企业网络环境中进行Kubernetes集群的管理时,经常会遇到需要配置Pods通过HTTP代理服务器访问Internet的情况。这可能是由于各种原因,如安全策略限制、网络架构要求或者访问特定资源的需要。本文将介绍配置Kubernetes中Pod使用代理的两种常见方式:通过ConfigMap和直接在应用程序环境变量中设置。使用场景Kubernetes集群中
- STM32F103C8T6驱动HC-SR04超声波模块测距打印在串口上
单片机阿伟
单片机嵌入式硬件stm32
引言HC-SR04超声波测距模块因其成本低、精度高、使用简单,被广泛应用于机器人避障、液位检测等领域。本文将结合STM32F103C8T6的驱动代码,详细解析HC-SR04的工作原理及实现方法,帮助开发者快速上手。源码链接:https://share.weiyun.com/RJG4fPjyHC-SR04模块工作原理触发信号:向Trig引脚发送至少10μs的高电平脉冲,触发模块发射8个40kHz超声
- linux 安装python 3.10
处女座_三月
pythonlinux运维服务器
1下载对应的安装包下载地址:https://download.csdn.net/download/weixin_43401380/885196692上传服务器1步骤1:解压文件tar-xzfPython-3.10.13.tgz2步骤2:创建安装目录mkdirlocal3开始安装1安装gcc:你需要安装gcc,这是GNU编译器集合的一部分,用于编译C程序。执行以下命令来安装gcc:sudoaptup
- 揭秘 Fluss 架构组件
大圣数据星球
大数据Flink设计模式
这是Fluss系列的第四篇文章了,我们先回顾一下前面三篇文章主要说了哪些内容。Fluss部署,带领大家部署Fluss环境,体验一下Fluss的功能Fluss整合数据湖的操作,体验Fluss与数据湖的结合讲解了Fluss、Kafka、Paimon之间的区别和联系前面三篇文章可以让大家上手玩起来Fluss这个框架,并说明了它与Kafka、Paimon数据湖的关系,接下来的文章就深入Fluss细节来说一
- 用python绘制kde模型
若木胡
python开发语言
以下是使用Python绘制核密度估计(KernelDensityEstimation,KDE)模型的完整示例代码和说明:方法1:使用Seaborn快速绘制importnumpyasnpimportmatplotlib.pyplotaspltimportseabornassns#生成示例数据(混合高斯分布)data=np.concatenate([np.random.normal(0,1,500),
- 代码随想录算法训练营Day51 | 101.孤岛的总面积、102.沉没孤岛、103.水流问题、104.建造最大岛屿
Harryline-lx
代码随想录算法深度优先
文章目录101.孤岛的总面积思路与重点102.沉没孤岛思路与重点103.水流问题思路与重点104.建造最大岛屿思路与重点101.孤岛的总面积题目链接:101.孤岛的总面积讲解链接:代码随想录状态:直接看题解了。思路与重点nextx或者nexty越界了则说明当前的x或y处于边界处,所以当前的岛不是孤岛,不能记入总面积。#include#includeusingnamespacestd;intdir[
- python修改nginx配置文件_一个修改nginx.conf配置文件的开源工具
潜水小透明
发现一个修改nginx.conf配置文件的python开源工具,挺好用的,分享一下:这个工具可以读取,修改以及删除nginx的配置项,然后重新生成配置文件。这其中保留了大部分原始配置文件格式,有一些会改变;所以不保证新生成的文件格式完全一致,还需要用肉眼比较一下哦。基本用法:frompynginxconfigimportNginxConfignc=NginxConfig()nc.loadf('/e
- React常见面试题(2024最新版)
前端小小王
react.js前端前端框架面试
创建项目npxcreate-react-appmy-app启动项目npmstart目录结构目录/文件名描述README.md项目的自述文件node_modules/项目依赖包存放目录package.json包管理配置文件,记录项目信息和依赖package-lock.json锁定依赖版本,确保跨环境一致性public/公共资源目录public/index.html主HTML文件,React应用将被引
- 一文带你了解软件版本管理(GIT和SVN)
硬件学长森哥
gitsvn软件工程源代码管理软件需求软件构建
文章目录一、代码版本控制工具二、GIT2.1git工具特点2.2版本控制的基本步骤2.3基本介绍三、SVN3.1SVN工具特点3.2版本控制的基本步骤3.3基本介绍四、结尾总结一、代码版本控制工具版本控制适用于软件开发过程中对各种程序代码、配置文件及说明文档等文件变更的管理,是软件开发者的必备工具,也是软件公司的基础设施。是软件团队中完成代码提交和codereview以及代码集成的主要工具。使用软
- linux 配置Java环境变量
找个栗子
linuxjavapython
要在Linux上配置Java环境变量,可以按照以下步骤进行操作:首先,打开终端。确认是否已安装Java。在终端中运行以下命令:java-version如果已安装Java,则会显示Java的版本信息。如果没有安装Java,请先安装Java。找到Java的安装路径。在终端中运行以下命令:sudoupdate-alternatives--configjava这会显示Java的安装路径。记下此路径,后续会
- go分布式锁
alsarkc
redis分布式数据库golang
go-redis配置packageconfigimport("context""fmt""github.com/redis/go-redis/v9")varCtx=context.Background()varRdb*redis.Clientfuncinit(){Rdb=redis.NewClient(&redis.Options{Addr:"localhost:6379",//Redis服务器地
- 推荐开源项目:media-codec - 视频与音频编解码库
强妲佳Darlene
推荐开源项目:media-codec-视频与音频编解码库media-codecVideoandaudiodeconde/encodelibraries.项目地址:https://gitcode.com/gh_mirrors/me/media-codec1、项目介绍media-codec是一个强大的开源项目,专注于视频和音频的编解码库。它为开发者提供了一套完善的工具,帮助他们在各种平台上处理多媒体数
- nginx config 详解
筏镜
linuxnginx运维服务器
nginxconfig的整体布局如下...#全局块events{#events块...}http#http块{...#http全局块server#server块{...#server全局块location[PATTERN]#location块{...}location[PATTERN]{...}}server{...}...#http全局块}nginxconfig配置例子#配置用户或者组,默认为n
- ios内付费
374016526
ios内付费
近年来写了很多IOS的程序,内付费也用到不少,使用IOS的内付费实现起来比较麻烦,这里我写了一个简单的内付费包,希望对大家有帮助。
具体使用如下:
这里的sender其实就是调用者,这里主要是为了回调使用。
[KuroStoreApi kuroStoreProductId:@"产品ID" storeSender:self storeFinishCallBa
- 20 款优秀的 Linux 终端仿真器
brotherlamp
linuxlinux视频linux资料linux自学linux教程
终端仿真器是一款用其它显示架构重现可视终端的计算机程序。换句话说就是终端仿真器能使哑终端看似像一台连接上了服务器的客户机。终端仿真器允许最终用户用文本用户界面和命令行来访问控制台和应用程序。(LCTT 译注:终端仿真器原意指对大型机-哑终端方式的模拟,不过在当今的 Linux 环境中,常指通过远程或本地方式连接的伪终端,俗称“终端”。)
你能从开源世界中找到大量的终端仿真器,它们
- Solr Deep Paging(solr 深分页)
eksliang
solr深分页solr分页性能问题
转载请出自出处:http://eksliang.iteye.com/blog/2148370
作者:eksliang(ickes) blg:http://eksliang.iteye.com/ 概述
长期以来,我们一直有一个深分页问题。如果直接跳到很靠后的页数,查询速度会比较慢。这是因为Solr的需要为查询从开始遍历所有数据。直到Solr的4.7这个问题一直没有一个很好的解决方案。直到solr
- 数据库面试题
18289753290
面试题 数据库
1.union ,union all
网络搜索出的最佳答案:
union和union all的区别是,union会自动压缩多个结果集合中的重复结果,而union all则将所有的结果全部显示出来,不管是不是重复。
Union:对两个结果集进行并集操作,不包括重复行,同时进行默认规则的排序;
Union All:对两个结果集进行并集操作,包括重复行,不进行排序;
2.索引有哪些分类?作用是
- Android TV屏幕适配
酷的飞上天空
android
先说下现在市面上TV分辨率的大概情况
两种分辨率为主
1.720标清,分辨率为1280x720.
屏幕尺寸以32寸为主,部分电视为42寸
2.1080p全高清,分辨率为1920x1080
屏幕尺寸以42寸为主,此分辨率电视屏幕从32寸到50寸都有
适配遇到问题,已1080p尺寸为例:
分辨率固定不变,屏幕尺寸变化较大。
如:效果图尺寸为1920x1080,如果使用d
- Timer定时器与ActionListener联合应用
永夜-极光
java
功能:在控制台每秒输出一次
代码:
package Main;
import javax.swing.Timer;
import java.awt.event.*;
public class T {
private static int count = 0;
public static void main(String[] args){
- Ubuntu14.04系统Tab键不能自动补全问题解决
随便小屋
Ubuntu 14.04
Unbuntu 14.4安装之后就在终端中使用Tab键不能自动补全,解决办法如下:
1、利用vi编辑器打开/etc/bash.bashrc文件(需要root权限)
sudo vi /etc/bash.bashrc
接下来会提示输入密码
2、找到文件中的下列代码
#enable bash completion in interactive shells
#if
- 学会人际关系三招 轻松走职场
aijuans
职场
要想成功,仅有专业能力是不够的,处理好与老板、同事及下属的人际关系也是门大学问。如何才能在职场如鱼得水、游刃有余呢?在此,教您简单实用的三个窍门。
第一,多汇报
最近,管理学又提出了一个新名词“追随力”。它告诉我们,做下属最关键的就是要多请示汇报,让上司随时了解你的工作进度,有了新想法也要及时建议。不知不觉,你就有了“追随力”,上司会越来越了解和信任你。
第二,勤沟通
团队的力
- 《O2O:移动互联网时代的商业革命》读书笔记
aoyouzi
读书笔记
移动互联网的未来:碎片化内容+碎片化渠道=各式精准、互动的新型社会化营销。
O2O:Online to OffLine 线上线下活动
O2O就是在移动互联网时代,生活消费领域通过线上和线下互动的一种新型商业模式。
手机二维码本质:O2O商务行为从线下现实世界到线上虚拟世界的入口。
线上虚拟世界创造的本意是打破信息鸿沟,让不同地域、不同需求的人
- js实现图片随鼠标滚动的效果
百合不是茶
JavaScript滚动属性的获取图片滚动属性获取页面加载
1,获取样式属性值
top 与顶部的距离
left 与左边的距离
right 与右边的距离
bottom 与下边的距离
zIndex 层叠层次
例子:获取左边的宽度,当css写在body标签中时
<div id="adver" style="position:absolute;top:50px;left:1000p
- ajax同步异步参数async
bijian1013
jqueryAjaxasync
开发项目开发过程中,需要将ajax的返回值赋到全局变量中,然后在该页面其他地方引用,因为ajax异步的原因一直无法成功,需将async:false,使其变成同步的。
格式:
$.ajax({ type: 'POST', ur
- Webx3框架(1)
Bill_chen
eclipsespringmaven框架ibatis
Webx是淘宝开发的一套Web开发框架,Webx3是其第三个升级版本;采用Eclipse的开发环境,现在支持java开发;
采用turbine原型的MVC框架,扩展了Spring容器,利用Maven进行项目的构建管理,灵活的ibatis持久层支持,总的来说,还是一套很不错的Web框架。
Webx3遵循turbine风格,velocity的模板被分为layout/screen/control三部
- 【MongoDB学习笔记五】MongoDB概述
bit1129
mongodb
MongoDB是面向文档的NoSQL数据库,尽量业界还对MongoDB存在一些质疑的声音,比如性能尤其是查询性能、数据一致性的支持没有想象的那么好,但是MongoDB用户群确实已经够多。MongoDB的亮点不在于它的性能,而是它处理非结构化数据的能力以及内置对分布式的支持(复制、分片达到的高可用、高可伸缩),同时它提供的近似于SQL的查询能力,也是在做NoSQL技术选型时,考虑的一个重要因素。Mo
- spring/hibernate/struts2常见异常总结
白糖_
Hibernate
Spring
①ClassNotFoundException: org.aspectj.weaver.reflect.ReflectionWorld$ReflectionWorldException
缺少aspectjweaver.jar,该jar包常用于spring aop中
②java.lang.ClassNotFoundException: org.sprin
- jquery easyui表单重置(reset)扩展思路
bozch
formjquery easyuireset
在jquery easyui表单中 尚未提供表单重置的功能,这就需要自己对其进行扩展。
扩展的时候要考虑的控件有:
combo,combobox,combogrid,combotree,datebox,datetimebox
需要对其添加reset方法,reset方法就是把初始化的值赋值给当前的组件,这就需要在组件的初始化时将值保存下来。
在所有的reset方法添加完毕之后,就需要对fo
- 编程之美-烙饼排序
bylijinnan
编程之美
package beautyOfCoding;
import java.util.Arrays;
/*
*《编程之美》的思路是:搜索+剪枝。有点像是写下棋程序:当前情况下,把所有可能的下一步都做一遍;在这每一遍操作里面,计算出如果按这一步走的话,能不能赢(得出最优结果)。
*《编程之美》上代码有很多错误,且每个变量的含义令人费解。因此我按我的理解写了以下代码:
*/
- Struts1.X 源码分析之ActionForm赋值原理
chenbowen00
struts
struts1在处理请求参数之前,首先会根据配置文件action节点的name属性创建对应的ActionForm。如果配置了name属性,却找不到对应的ActionForm类也不会报错,只是不会处理本次请求的请求参数。
如果找到了对应的ActionForm类,则先判断是否已经存在ActionForm的实例,如果不存在则创建实例,并将其存放在对应的作用域中。作用域由配置文件action节点的s
- [空天防御与经济]在获得充足的外部资源之前,太空投资需有限度
comsci
资源
这里有一个常识性的问题:
地球的资源,人类的资金是有限的,而太空是无限的.....
就算全人类联合起来,要在太空中修建大型空间站,也不一定能够成功,因为资源和资金,技术有客观的限制....
&
- ORACLE临时表—ON COMMIT PRESERVE ROWS
daizj
oracle临时表
ORACLE临时表 转
临时表:像普通表一样,有结构,但是对数据的管理上不一样,临时表存储事务或会话的中间结果集,临时表中保存的数据只对当前
会话可见,所有会话都看不到其他会话的数据,即使其他会话提交了,也看不到。临时表不存在并发行为,因为他们对于当前会话都是独立的。
创建临时表时,ORACLE只创建了表的结构(在数据字典中定义),并没有初始化内存空间,当某一会话使用临时表时,ORALCE会
- 基于Nginx XSendfile+SpringMVC进行文件下载
denger
应用服务器Webnginx网络应用lighttpd
在平常我们实现文件下载通常是通过普通 read-write方式,如下代码所示。
@RequestMapping("/courseware/{id}")
public void download(@PathVariable("id") String courseID, HttpServletResp
- scanf接受char类型的字符
dcj3sjt126com
c
/*
2013年3月11日22:35:54
目的:学习char只接受一个字符
*/
# include <stdio.h>
int main(void)
{
int i;
char ch;
scanf("%d", &i);
printf("i = %d\n", i);
scanf("%
- 学编程的价值
dcj3sjt126com
编程
发一个人会编程, 想想以后可以教儿女, 是多么美好的事啊, 不管儿女将来从事什么样的职业, 教一教, 对他思维的开拓大有帮助
像这位朋友学习:
http://blog.sina.com.cn/s/articlelist_2584320772_0_1.html
VirtualGS教程 (By @林泰前): 几十年的老程序员,资深的
- 二维数组(矩阵)对角线输出
飞天奔月
二维数组
今天在BBS里面看到这样的面试题目,
1,二维数组(N*N),沿对角线方向,从右上角打印到左下角如N=4: 4*4二维数组
{ 1 2 3 4 }
{ 5 6 7 8 }
{ 9 10 11 12 }
{13 14 15 16 }
打印顺序
4
3 8
2 7 12
1 6 11 16
5 10 15
9 14
13
要
- Ehcache(08)——可阻塞的Cache——BlockingCache
234390216
并发ehcacheBlockingCache阻塞
可阻塞的Cache—BlockingCache
在上一节我们提到了显示使用Ehcache锁的问题,其实我们还可以隐式的来使用Ehcache的锁,那就是通过BlockingCache。BlockingCache是Ehcache的一个封装类,可以让我们对Ehcache进行并发操作。其内部的锁机制是使用的net.
- mysqldiff对数据库间进行差异比较
jackyrong
mysqld
mysqldiff该工具是官方mysql-utilities工具集的一个脚本,可以用来对比不同数据库之间的表结构,或者同个数据库间的表结构
如果在windows下,直接下载mysql-utilities安装就可以了,然后运行后,会跑到命令行下:
1) 基本用法
mysqldiff --server1=admin:12345
- spring data jpa 方法中可用的关键字
lawrence.li
javaspring
spring data jpa 支持以方法名进行查询/删除/统计。
查询的关键字为find
删除的关键字为delete/remove (>=1.7.x)
统计的关键字为count (>=1.7.x)
修改需要使用@Modifying注解
@Modifying
@Query("update User u set u.firstna
- Spring的ModelAndView类
nicegege
spring
项目中controller的方法跳转的到ModelAndView类,一直很好奇spring怎么实现的?
/*
* Copyright 2002-2010 the original author or authors.
*
* Licensed under the Apache License, Version 2.0 (the "License");
* yo
- 搭建 CentOS 6 服务器(13) - rsync、Amanda
rensanning
centos
(一)rsync
Server端
# yum install rsync
# vi /etc/xinetd.d/rsync
service rsync
{
disable = no
flags = IPv6
socket_type = stream
wait
- Learn Nodejs 02
toknowme
nodejs
(1)npm是什么
npm is the package manager for node
官方网站:https://www.npmjs.com/
npm上有很多优秀的nodejs包,来解决常见的一些问题,比如用node-mysql,就可以方便通过nodejs链接到mysql,进行数据库的操作
在开发过程往往会需要用到其他的包,使用npm就可以下载这些包来供程序调用
&nb
- Spring MVC 拦截器
xp9802
spring mvc
Controller层的拦截器继承于HandlerInterceptorAdapter
HandlerInterceptorAdapter.java 1 public abstract class HandlerInterceptorAdapter implements HandlerIntercep