华为DSVPN配置练习
华为DSVPN配置练习
- 一、写在前面
-
- (1)什么是DSVPN?
- (2)为什么需要DSVPN?
- 二、拓扑以及需求
- 三、配置思路
-
- (1)在ISP区域配置OSPF打通公网
- (3)配置mGRE-Hub
- (3)配置mGRE-Spoke
- (4)打通中心、分支
- (5)连通性检查
- (6)用IPSec对通信数据加密
- 四、本拓扑中所有路由器的配置
-
- R1
- R2
- R3
- ISP1
- ISP2
一、写在前面
(1)什么是DSVPN?
动态智能VPN(Dynamic Smart Virtual Private Network),简称DSVPN,是一种在Hub-Spoke组网方式下为公网地址动态变化的分支之间建立VPN隧道的解决方案。
需注意的一点是:DSVPN是华为私有协议
(2)为什么需要DSVPN?
依照我们之前的MPLSVPN、GRE over IPSec技术,它们均有着自己的缺陷。
MPLSVPN需要公网区域经过的所有路由器均支持MPLS,对硬件要求较高。
GRE over IPSec集中在Hub点,所有流量都穿越Hub点,且每增加一个新的Sopke点,Hub点都必须被配置。
基于这些缺陷,我们的DSVPN就应运而生。它通过将下一跳解析协议NHRP(Next Hop Resolution Protocol)和mGRE(multipoint Generic Routing Encapsulation)技术与IPSec相结合解决了GRE over IPSec的缺陷。
分支与分支之间可建立智能动态VPN,不用的时候会自行拆除,由此维护也显得更加智能化。
二、拓扑以及需求
某公司有现有两个分支需要和总部实现通信,且两个支部也需要通信,除此之外公司正在扩张期,还会建立其他分支。
经过分析研究,最终采用DSVPN实现此需求。它的优势在于分支之间通信会建立动态VPN,减少Hub的流量压力;除此以外建立其他分支时无需再去Hub进行配置。最终拓扑如下:

三、配置思路
(1)在ISP区域配置OSPF打通公网
以ISP1为例,配置如下:
OSPF不再多赘述,详情点击快速通道:华为OSPF配置练习
isp1设备起OSPF协议:
[isp1]ospf 1 router-id 10.10.10.10
[isp1-ospf-1]area 0 //进入区域0
# 宣告接口
[isp1-ospf-1-area-0.0.0.0]network 10.0.11.1 0.0.0.0
[isp1-ospf-1-area-0.0.0.0]network 10.0.21.1 0.0.0.0
[isp1-ospf-1-area-0.0.0.0]network 10.12.0.1 0.0.0.0
(3)配置mGRE-Hub
R1配置如下:
R1中心站点配置如下:
[r1]interface Tunnel 0/0/0 //进入隧道口
[r1-Tunnel0/0/0]ip address 100.1.0.1 24 //配置IP地址
[r1-Tunnel0/0/0]tunnel-protocol gre p2mp //修改接口类型为多点GRE
[r1-Tunnel0/0/0]source 10.0.11.2 //公网源地址
# 本地成为NHRP的中心,同时可进行伪广播
[r1-Tunnel0/0/0]nhrp entry multicast dynamic
[r1-Tunnel0/0/0]nhrp network-id 100
(3)配置mGRE-Spoke
R2配置如下:
R2分支站点配置如下:
[r2]interface Tunnel 0/0/0 //进入隧道
[r2-Tunnel0/0/0]ip ad 100.1.0.2 24 //配置IP
[r2-Tunnel0/0/0]tunnel-protocol gre p2mp
[r2-Tunnel0/0/0]source GigabitEthernet 0/0/0 //假设公网地址不确定,可声明为接口
[r2-Tunnel0/0/0]ospf network-type broadcast //由于底层跑了OSPF,OSPF默认为p2mp
[r2-Tunnel0/0/0]nhrp network-id 100
[r2-Tunnel0/0/0]nhrp entry 100.1.0.1 10.0.11.2 register //分支需要去中心站点注册
(4)打通中心、分支
以R3为例,我们选择起RIP:
[r3]rip 1
[r3-rip-1]version 2
[r3-rip-1]undo summary
[r3-rip-1]net 100.0.0.0
特别注意:
#若这一步使用RIP,一定要在Hub处站点关闭水平分割
[r1-Tunnel0/0/0]undo rip split-horizon
#若这一步使用OSPF,一定要更改网络类型
# Hub配置
[r1-Tunnel0/0/0]ospf network-type broadcast //由于底层跑了OSPF,OSPF默认为p2mp
[r1-Tunnel0/0/0]ospf dr-priority 0 //调整优先级,保证Hnb是DR
# Spoke配置
[r1-Tunnel0/0/0]ospf network-type broadcast //由于底层跑了OSPF,OSPF默认为p2mp
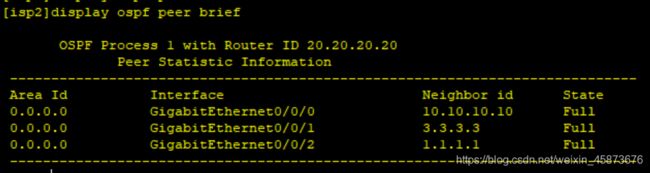
(5)连通性检查
(6)用IPSec对通信数据加密
这一部分配置不多做赘述,有兴趣学习可点击链接:华为IPsce以及GRE over IPSec配置练习学习对隧道数据加密的配置命令以及需求。
四、本拓扑中所有路由器的配置
R1
R1配置如下:
[r1]display current-configuration
[V200R003C00]
#
sysname r1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 10.0.11.2 255.255.255.0
undo rip split-horizon
#
interface GigabitEthernet0/0/1
ip address 10.0.12.2 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 100.0.0.2 255.255.255.0
#
interface NULL0
#
interface Tunnel0/0/0
ip address 100.1.0.1 255.255.255.0
undo rip split-horizon
tunnel-protocol gre p2mp
source GigabitEthernet0/0/0
nhrp entry multicast dynamic
nhrp network-id 100
#
ospf 1 router-id 1.1.1.1
area 0.0.0.0
network 10.0.11.2 0.0.0.0
network 10.0.12.2 0.0.0.0
#
rip 1
undo summary
version 2
network 100.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R2
R2配置如下:
[r2]display current-configuration
[V200R003C00]
#
sysname r2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 10.0.21.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 100.0.1.2 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface Tunnel0/0/0
ip address 100.1.0.2 255.255.255.0
ip address 100.2.0.2 255.255.255.0 sub
tunnel-protocol gre p2mp
source GigabitEthernet0/0/0
ospf network-type broadcast
nhrp network-id 100
nhrp entry 100.1.0.1 10.0.11.2 register
#
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 10.0.21.2 0.0.0.0
#
rip 1
undo summary
version 2
network 100.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R3
R3配置如下:
[V200R003C00]
#
sysname r3
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 10.0.32.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 100.0.2.2 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface Tunnel0/0/0
ip address 100.1.0.3 255.255.255.0
tunnel-protocol gre p2mp
source GigabitEthernet0/0/0
nhrp network-id 100
nhrp entry 100.1.0.1 10.0.11.2 register
#
ospf 1 router-id 3.3.3.3
area 0.0.0.0
network 10.0.32.2 0.0.0.0
#
rip 1
undo summary
version 2
network 100.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
ISP1
ISP1配置如下:
[isp1]display current-configuration
[V200R003C00]
#
sysname isp1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 10.12.0.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.0.21.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 10.0.11.1 255.255.255.0
#
interface NULL0
#
ospf 1 router-id 10.10.10.10
area 0.0.0.0
network 10.0.11.1 0.0.0.0
network 10.0.21.1 0.0.0.0
network 10.12.0.1 0.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
ISP2
ISP2配置如下:
[isp2]display current-configuration
[V200R003C00]
#
sysname isp2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 10.12.0.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.0.32.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 10.0.12.1 255.255.255.0
#
interface NULL0
#
ospf 1 router-id 20.20.20.20
area 0.0.0.0
network 10.0.12.1 0.0.0.0
network 10.0.32.1 0.0.0.0
network 10.12.0.2 0.0.0.0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return