CentOS8搭建实现私有CA和证书申请
选项说明
-new:生成新证书签署请求
-x509:专用于CA生成自签证书
-key:生成请求时用到的私钥文件
-days n:证书的有效期限
-out /PATH/TO/SOMECERTFILE: 证书的保存路
注意:默认要求 国家,省,公司名称三项必须和CA一致
创建CA相关目录,centos8没有以下的目录
[root@CentOS-8 ~]# mkdir -p /etc/pki/CA/{certs,crl,newcerts,private}
[root@CentOS-8 ~]# tree /etc/pki/CA/
/etc/pki/CA/
├── certs
├── crl
├── newcerts
└── private
4 directories, 0 files
[root@CentOS-8 ~]# touch /etc/pki/CA/index.txt
[root@CentOS-8 /]# echo 0F > /etc/pki/CA/serial
index.txt和serial文件在颁发证书时需要使用
创建CA的私钥
[root@CentOS-8 /]# (umask 066; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
给CA颁发自签名证书
[root@CentOS-8 /]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:guangdong
Locality Name (eg, city) [Default City]:shenzhen
Organization Name (eg, company) [Default Company Ltd]:longxuan
Organizational Unit Name (eg, section) []:it
Common Name (eg, your name or your server's hostname) []:www.longxuan.vip
Email Address []:
查看生成的CA证书以文本格式显示
[root@CentOS-8 /]# openssl x509 -in /etc/pki/CA/cacert.pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
6a:8c:4d:6d:8b:23:be:74:7f:61:14:98:b5:d4:3c:dc:2e:53:32:9f
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = guangdong, L = shenzhen, O = longxuan, OU = it, CN = www.longxuan.vip
Validity
Not Before: Apr 29 09:22:26 2021 GMT
Not After : Apr 27 09:22:26 2031 GMT
Subject: C = CN, ST = guangdong, L = shenzhen, O = longxuan, OU = it, CN = www.longxuan.vip
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
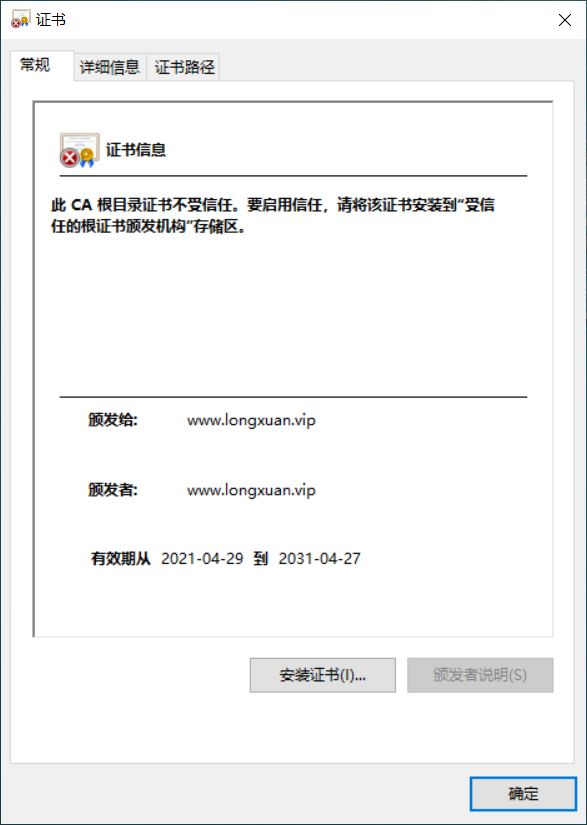
#将文件cacert.pem传到windows上,修改文件名为cacert.pem.crt,双击可以看到下面显示
[root@CentOS-8 /]# sz /etc/pki/CA/cacert.pem
用户生成私钥和证书申请(实验用的路径/data/app1)
[root@centos8 ~]# mkdir /data/app1 -p
[root@CentOS-8 app1]# (umask 066; openssl genrsa -out /data/app1/app1.key 2048)
生成证书申请文件
[root@CentOS-8 app1]# openssl req -new -key /data/app1/app1.key -out /data/app1/app1.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:guangdong
Locality Name (eg, city) [Default City]:guangzhou
Organization Name (eg, company) [Default Company Ltd]:longxuan
Organizational Unit Name (eg, section) []:sale
Common Name (eg, your name or your server's hostname) []:sale.longxuan.vip
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
默认有三项内容必须和CA一致:国家,省份,组织
CA颁发证书
[root@CentOS-8 app1]# openssl ca -in /data/app1/app1.csr -out /etc/pki/CA/certs/app1.crt -days 1000
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 15 (0xf)
Validity
Not Before: Apr 29 09:44:06 2021 GMT
Not After : Jan 24 09:44:06 2024 GMT
Subject:
countryName = CN
stateOrProvinceName = guangdong
organizationName = longxuan
organizationalUnitName = sale
commonName = sale.longxuan.vip
emailAddress = [email protected]
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
03:75:89:97:58:ED:81:58:4C:34:1C:3F:27:0B:50:17:3C:CD:47:C0
X509v3 Authority Key Identifier:
keyid:01:91:5E:E7:F7:C4:AA:9D:6C:E7:66:77:4B:F3:D3:49:21:63:07:09
Certificate is to be certified until Jan 24 09:44:06 2024 GMT (1000 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
查看下次生成的编号
[root@CentOS-8 app1]# cat /etc/pki/CA/serial
10
指定编号有效性
[root@CentOS-8 app1]# openssl ca -status 0F
Using configuration from /etc/pki/tls/openssl.cnf
0F=Valid (V)
制作完成所有的文件如下:
[root@localhost app1]# tree /etc/pki/CA/
/etc/pki/CA/
├── cacert.pem
├── certs
│ └── app1.crt
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old
├── newcerts
│ └── 0F.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old
4 directories, 9 files
证书相关文件发送到用户端使用
[root@CentOS-8 app1]# ls
app1.csr app1.key
[root@CentOS-8 app1]# cp /etc/pki/CA/certs/app1.crt /data/app1/
[root@CentOS-8 app1]# ls
app1.crt app1.csr app1.key
没有安装证书
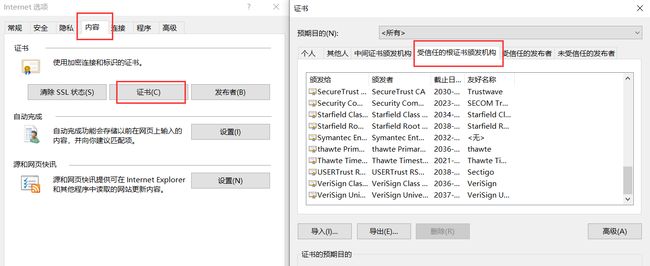
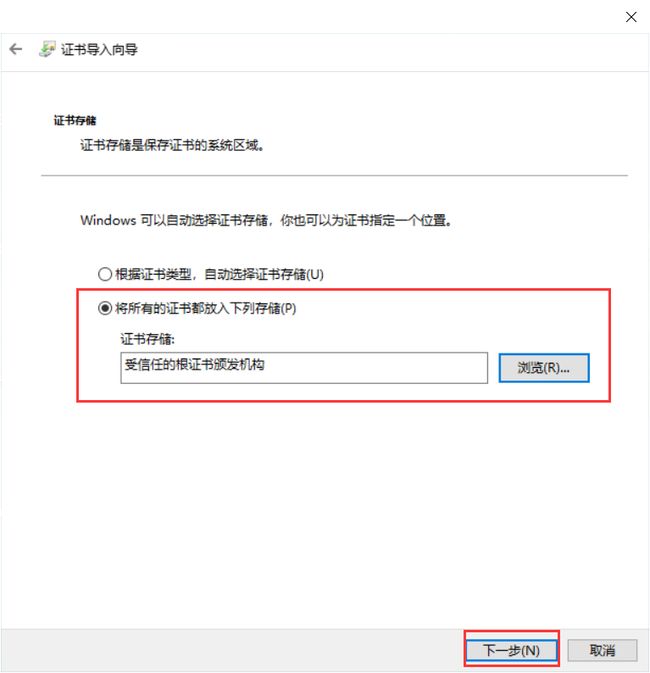
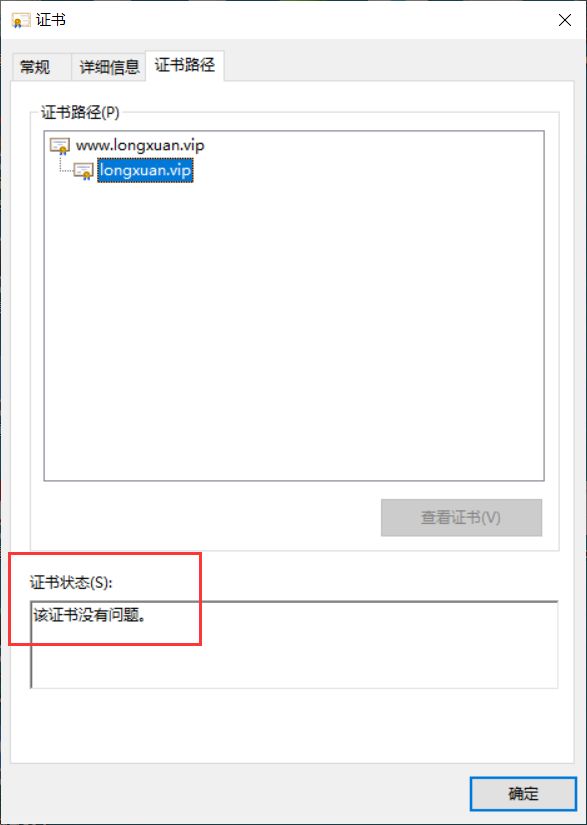
Windows安装证书
安装证书后
吊销证书
跨国家地区配置
[root@localhost ~]# vim /etc/pki/tls/openssl.cnf
#policy = policy_match
policy = policy_anything
# For the CA policy
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
# For the 'anything' policy
# At this point in time, you must list all acceptable 'object'
# types.
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
#重复使用一个证书
[root@localhost app1]# openssl ca -in /data/app1/app1.csr -out /etc/pki/CA/certs/app1-new.crt -days 1000
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 16 (0x10)
Validity
Not Before: Apr 29 13:22:36 2021 GMT
Not After : Jan 24 13:22:36 2024 GMT
Subject:
countryName = CN
stateOrProvinceName = beijing
localityName = beijing
organizationName = longxuan
organizationalUnitName = sale
commonName = sale.longxuan.vip
emailAddress = [email protected]
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
E1:44:D6:E9:D9:D1:A0:D2:F1:0A:B0:DA:E9:E3:5D:DB:7C:B4:B0:3B
X509v3 Authority Key Identifier:
keyid:FE:1E:0F:C5:43:BC:0F:F8:42:0B:43:25:81:75:B4:30:CE:60:D8:94
Certificate is to be certified until Jan 24 13:22:36 2024 GMT (1000 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
实验:跨地区国家制作私有CA
[root@localhost app1]# mkdir /data/app2 -p
[root@localhost app1]# (umask 066; openssl genrsa -out /data/app2/app2.key 2048)
Generating RSA private key, 2048 bit long modulus (2 primes)
.............................................................................+++++
............................................................................................+++++
e is 65537 (0x010001)
[root@localhost app1]# openssl req -new -key /data/app2/app2.key -out /data/app2/app2.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:US
State or Province Name (full name) []:newyork
Locality Name (eg, city) [Default City]:newyork
Organization Name (eg, company) [Default Company Ltd]:longxuan
Organizational Unit Name (eg, section) []:it
Common Name (eg, your name or your server's hostname) []:longxuan.vip
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@localhost app1]# openssl ca -in /data/app2/app2.csr -out /etc/pki/CA/certs/app2.crt -days 1000
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 17 (0x11)
Validity
Not Before: Apr 29 13:32:38 2021 GMT
Not After : Jan 24 13:32:38 2024 GMT
Subject:
countryName = US
stateOrProvinceName = newyork
localityName = newyork
organizationName = longxuan
organizationalUnitName = it
commonName = longxuan.vip
emailAddress = [email protected]
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
73:B7:DD:C8:1F:A0:19:F9:D9:63:90:06:99:99:5C:61:33:41:3A:C1
X509v3 Authority Key Identifier:
keyid:FE:1E:0F:C5:43:BC:0F:F8:42:0B:43:25:81:75:B4:30:CE:60:D8:94
Certificate is to be certified until Jan 24 13:32:38 2024 GMT (1000 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
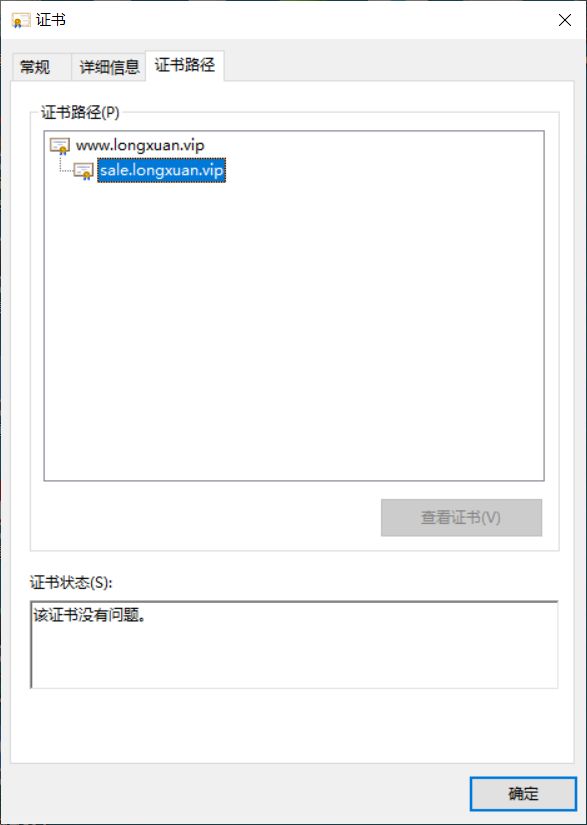
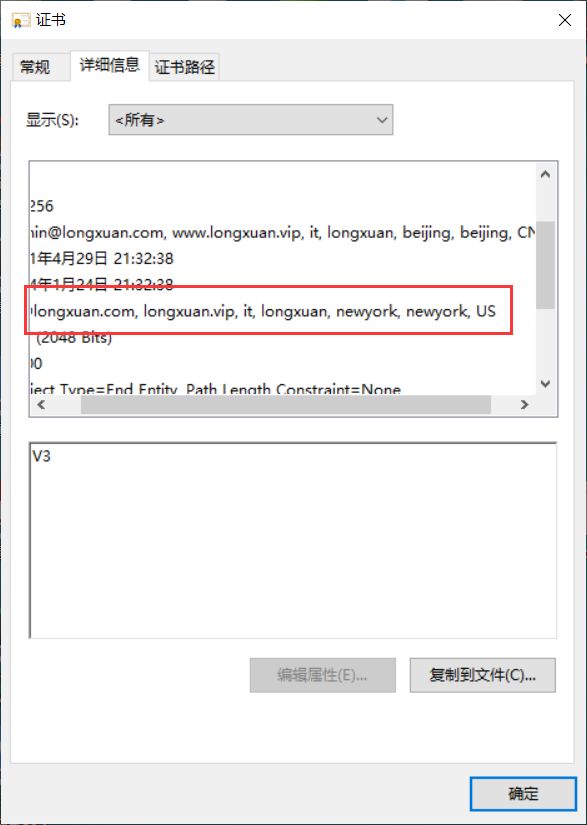
上传到Windows系统查看跨国家地区的证书
查看有多少
[root@localhost app1]# cat /etc/pki/CA/index.txt
V 240124120434Z 0F unknown /C=CN/ST=beijing/O=longxuan/OU=sale/CN=sale.longxuan.vip/[email protected]
V 240124132236Z 10 unknown /C=CN/ST=beijing/L=beijing/O=longxuan/OU=sale/CN=sale.longxuan.vip/[email protected]
V 240124133238Z 11 unknown /C=US/ST=newyork/L=newyork/O=longxuan/OU=it/CN=longxuan.vip/[email protected]
吊销
[root@localhost app1]# openssl ca -revoke /etc/pki/CA/newcerts/10.pem
Using configuration from /etc/pki/tls/openssl.cnf
Revoking Certificate 10.
Data Base Updated
查看,看到R 就表示吊销
[root@localhost app1]# cat /etc/pki/CA/index.txt
V 240124120434Z 0F unknown /C=CN/ST=beijing/O=longxuan/OU=sale/CN=sale.longxuan.vip/[email protected]
R 240124132236Z 210429133538Z 10 unknown /C=CN/ST=beijing/L=beijing/O=longxuan/OU=sale/CN=sale.longxuan.vip/[email protected]
V 240124133238Z 11 unknown /C=US/ST=newyork/L=newyork/O=longxuan/OU=it/CN=longxuan.vip/[email protected]
生成证书吊销列表文件
[root@localhost app1]# echo 01 > /etc/pki/CA/crlnumber
[root@localhost app1]# openssl ca -gencrl -out /etc/pki/CA/crl.pem
Using configuration from /etc/pki/tls/openssl.cnf
完成的目录
[root@localhost app1]# tree /etc/pki/CA/
/etc/pki/CA/
├── cacert.pem
├── certs
│ ├── app1.crt
│ ├── app1-new.crt
│ └── app2.crt
├── crl
├── crlnumber
├── crlnumber.old
├── crl.pem
├── index.txt
├── index.txt.attr
├── index.txt.attr.old
├── index.txt.old
├── newcerts
│ ├── 0F.pem
│ ├── 10.pem
│ └── 11.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old
4 directories, 17 files
将此文件crl.pem传到windows上并改后缀为crl.pem.crl,双击可以查看以下显示
[root@localhost app1]# sz /etc/pki/CA/crl.pem