re学习笔记(72)HGAME2021 Level - Week1 - RE WP
文章目录
-
- apacha
- helloRe
- pypy
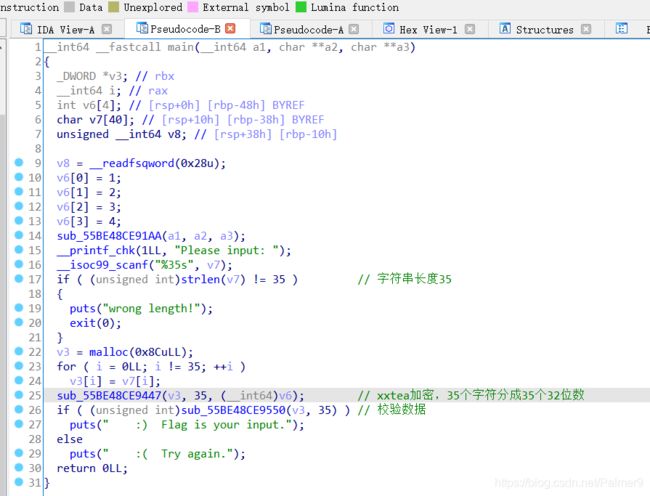
apacha
#include 其中头文件mycrypto.h在github
helloRe
l = [0x97, 0x99, 0x9C, 0x91, 0x9E, 0x81, 0x91, 0x9D, 0x9B, 0x9A, 0x9A, 0xAB, 0x81, 0x97, 0xAE, 0x80, 0x83, 0x8F, 0x94, 0x89, 0x99, 0x97]
flag = ""
n = 255
for i in range(22):
flag += chr(l[i]^n)
n -= 1
print(flag)
# hgame{hello_re_player}
pypy
python字节码,手动参考文档还原
得到还原后代码
raw_flag = input('give me your flag:\n')
cipher = list(raw_flag[6:-1])
length = len(cipher)
for i in range(length//2):
cipher[2*i],cipher[i*2+1]=cipher[2*i+1],cipher[i*2]
res = []
for i in range(length):
res.append(ord(cipher[i])^i)
res = bytes(res).hex()
print('your flag: '+res)
写解密脚本
flag = "30466633346f59213b4139794520572b45514d61583151576638643a"
flag = list(bytearray.fromhex(flag))
length = len(flag)
for i in range(length):
flag[i] = flag[i]^i
for i in range(length//2):
flag[2*i],flag[i*2+1]=flag[2*i+1],flag[i*2]
f = ""
for i in flag:
f += chr(i)
print('hgame{'+f+"}")
# hgame{G00dj0&_H3r3-I$Y@Ur_$L@G!~!~}