【CTF】ASM-Pico CTF 2014 Snippet
【Title】Pico CTF 2014 Write-up snippet
【Description】
We found this program snippet.txt, but we're having some trouble figuring it out. What's the value of %eax when the last instruction (the NOP) runs?
Hint: You may want to convert the assembly into some equivalent C code, which will be easier to read!
# This file is in AT&T syntax - see http://www.imada.sdu.dk/Courses/DM18/Litteratur/IntelnATT.htm
# and http://en.wikipedia.org/wiki/X86_assembly_language#Syntax. Both gdb and objdump produce
# AT&T syntax by default.
MOV $10814,%ebx
MOV $2972,%eax
MOV $10017,%ecx
CMP %eax,%ebx
JL L1
JMP L2
L1:
IMUL %eax,%ebx
ADD %eax,%ebx
MOV %ebx,%eax
SUB %ecx,%eax
JMP L3
L2:
IMUL %eax,%ebx
SUB %eax,%ebx
MOV %ebx,%eax
ADD %ecx,%eax
L3:
NOP
【Solution】
Let's walk through the program step-by-step. The first actions that occur is that 15329 is moved into %ebx (%ebx = 15329), 21674 is moved into %eax, and 25704 is moved into %ecx. The next operation is a CMP operation, where in AT&T syntax, the operation checks if the second element is less than the first element. If this is true it follows the first jump statement, and if it is false, it jumps to the second jump statement. In this case %ebx is less than %eax (15329 < 21674), so the program follows the path into the L1 function. The next thing that occurs is that %eax and %ebx are multiplied, and the value is stored into %ebx. At the end of this %ebx = 332240746. %eax is then added to %ebx and stored in %ebx, making %ebx = 332262420. The value of %ebx is then moved into %eax, making %eax = 332262420. Next %ecx is subtracted from %eax and stored into %eax, which makes %eax = 332236716. A jump to the L3 function is then called, which calls NOP and ends the program. The flag is the value of %eax at the end of the program which is 332236716.
【Appendix】
There's another solution from vulnhub:
Just save the code in basic.s with a few small changes:
.global main
.text
main:
MOV $119,%ebx
MOV $28557,%eax
MOV $8055,%ecx
CMP %eax,%ebx
JL L1
JMP L2
L1:
IMUL %eax,%ebx
ADD %eax,%ebx
MOV %ebx,%eax
SUB %ecx,%eax
JMP L3
L2:
IMUL %eax,%ebx
SUB %eax,%ebx
MOV %ebx,%eax
ADD %ecx,%eax
L3:
INT3 # <--- set a breakpoint here
NOP
And compile it with gcc: gcc –basic basic.s
Run in gdb and get the value of EAX:
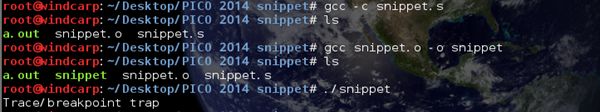
gdb ./basic -q -batch -n -ex 'r' -ex 'p $eax'
最近有很多英语的活要做,所以文章也就倾向于用英文写了,这样提升更快^_^。
顺便补习一下gcc的知识吧(cv自网络):
下面我们以C语言为例来谈一下不同阶段的输入和输出情况。
在预处理阶段,输入的是C语言的源文件,通常为*.c。它们通常带有.h之类头文件的包含文件。这个阶段主要处理源文件中的#ifdef、 #include和#define命令。该阶段会生成一个中间文件*.i,但实际工作中通常不用专门生成这种文件,因为基本上用不到;若非要生成这种文件不可,可以利用下面的命令:
gcc -E test.c -o test.i
在编译阶段,输入的是中间文件*.i,编译后生成汇编语言文件*.s 。这个阶段对应的GCC命令如下所示:
GCC -S test.i -o test.s
在汇编阶段,将输入的汇编文件*.s转换成机器语言*.o。这个阶段对应的GCC命令如下所示:GCC -c test.s -o test.o
最后,在连接阶段将输入的机器代码文件*.s(与其它的机器代码文件和库文件)汇集成一个可执行的二进制代码文件。这一步骤,可以利用下面的示例命令完成:
GCC test.o -o test
上面的gdb命令看懂了吗?一开始我是没看懂的:-D如果要是我估计只会拿p eax试一下了,还是要多多学习~
【Reference】
https://ctf-team.vulnhub.com/picoctf-2014-basic-asm/
http://en.wikipedia.org/wiki/X86_assembly_language#Syntax
http://ehsandev.com/pico2014/reverse_engineering/basic_asm.html