下载地址:
https://github.com/J4sp3r/j4sp3r.github.io/tree/master/files/hacktm-ctf-2020/strange-pcap/challenge
1、binwalk 分析
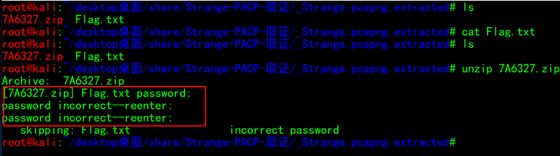
binwalk Strange.pcapng
发现有zip压缩文件,内含有flag
2、binwalk 提取
binwalk -e Strange.pcapng
解压时需要密码,只能从pacp流量中获取了
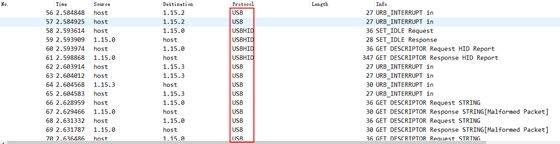
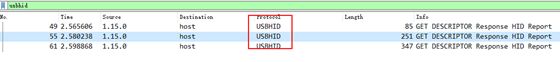
很明显这是USB传输的数据流
那么zip的解压密码应该是隐藏了USB数据流USB-HID之中的
3、tshark 提取
先tshark 提取pacp数据流
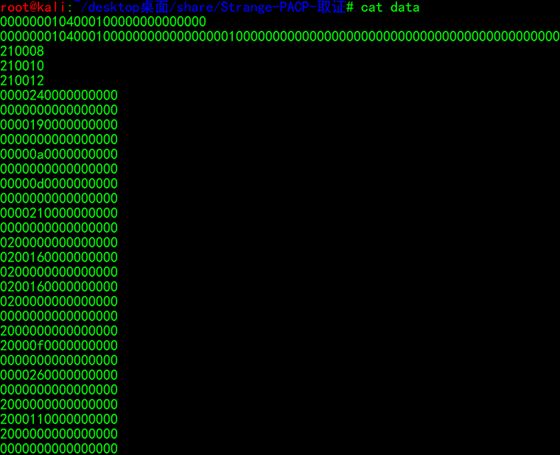
tshark -r Strange.pcapng -T fields -e usb.capdata | sed '/^\s*$/d' > data
我们知道USB是8字节的数据流,两位两位看,可以大胆删除长短不一的其他行
通过脚本提取其中的输入数据
#!/usr/bin/env python3
usb_codes = {
0x04:"aA", 0x05:"bB", 0x06:"cC", 0x07:"dD", 0x08:"eE", 0x09:"fF",
0x0A:"gG", 0x0B:"hH", 0x0C:"iI", 0x0D:"jJ", 0x0E:"kK", 0x0F:"lL",
0x10:"mM", 0x11:"nN", 0x12:"oO", 0x13:"pP", 0x14:"qQ", 0x15:"rR",
0x16:"sS", 0x17:"tT", 0x18:"uU", 0x19:"vV", 0x1A:"wW", 0x1B:"xX",
0x1C:"yY", 0x1D:"zZ", 0x1E:"1!", 0x1F:"2@", 0x20:"3#", 0x21:"4$",
0x22:"5%", 0x23:"6^", 0x24:"7&", 0x25:"8*", 0x26:"9(", 0x27:"0)",
0x2C:" ", 0x2D:"-_", 0x2E:"=+", 0x2F:"[{", 0x30:"]}", 0x32:"#~",
0x33:";:", 0x34:"'\"", 0x36:",<", 0x37:".>", 0x4f:">", 0x50:"<"
}
buff = ""
pos = 0
for x in open("strokes","r").readlines():
code = int(x[4:6],16)
if code == 0:
continue
if code == 0x28:
buff += "[ENTER]"
continue
if int(x[0:2],16) == 2 or int(x[0:2],16) == 0x20:
buff += usb_codes[code][1]
else:
buff += usb_codes[code][0]
print(buff)
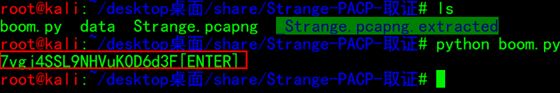
执行py脚本后,成功获取密码数据,并以ENTER回车结尾
7vgj4SSL9NHVuK0D6d3F
尝试解压zip
获取Flag成功
参考
https://bitvijays.github.io/LFC-Forensics.html