- 区块链发展史全景长图
boyedu
区块链区块链
序章:技术的觉醒(2008-2013)1.起源:比特币的诞生(2008-2009)2008年11月1日:中本聪在密码学邮件列表发布《比特币:一种点对点的电子现金系统》,提出基于P2P网络、非对称加密与工作量证明(PoW)的电子现金系统,标志着区块链技术的诞生。2009年1月3日:比特币创世区块诞生,中本聪在区块中嵌入《泰晤士报》头条“Chanelloronbrinkofsecondbailoutf
- 博人传:如果佐助保住轮回眼,九尾能顺势回来吗?
颚之巨人马赛尔
在动漫中,佐助失去在四战中收获的最大外挂,不知道什么时候才能恢复。文/颚之巨人马赛尔鸣人失去了九尾,作为对称,佐助自然也会失去点什么。当鸣人用不了六道/仙狐模式、以后只能使用仙人模式的情况下,佐助失去轮回眼,双方的战力再次呈现了微妙的平衡。而造成新平衡的原因,编剧不想回到旧平衡模式就是其中之一。如果佐助保住轮回眼,九尾能顺势回来吗?1.jpg1****、别忘了轮回天生佐助拥有轮回眼已经很多年了,但
- KL散度:信息差异的量化标尺 | 从概率分布对齐到模型优化的核心度量
不对称性、计算本质与机器学习的普适应用本文由「大千AI助手」原创发布,专注用真话讲AI,回归技术本质。拒绝神话或妖魔化。搜索「大千AI助手」关注我,一起撕掉过度包装,学习真实的AI技术!一、核心定义与数学本质KL散度(Kullback-LeiblerDivergence)用于衡量两个概率分布PPP和QQQ的差异程度,定义为:DKL(P∥Q)=∑x∈XP(x)logP(x)Q(x)(离散形式)D_
- 类风湿关节炎的关节症状
刘本胜老师
主要对称性侵犯小关节,尤其是手关节,其次是趾、膝、踩、肘、肩等关节。可分为滑膜炎症状和关节结构破坏的表现,前者经治疗后有一定可逆性,后者很难逆转。1.晨僵病变的关节在静止不动后可出现半小时甚至更长时间的僵硬,活动受限,如胶粘着的感觉,适度活动后逐渐减轻,尤以晨起时最明显,称为晨僵。约95%以上的类风湿关节炎病人,可出现晨僵,晨僵的程度和持续时间可作为判断病情活动度的指标。2.关节疼痛和肿胀往往是最
- 【加解密与C】Rot系列(二)Rot13
Rot13简介Rot13(Rotateby13places)是一种简单的字母替换加密算法,属于凯撒密码(Caesarcipher)的特例。它将字母表中的每个字母替换为字母表中距离它13个位置的字母。例如,字母A替换为N,B替换为O,以此类推。由于英文字母有26个字符,Rot13的特点是加密和解密使用相同的算法。Rot13算法规则对字母表中的每个字母,进行如下替换:大写字母A-Z:A→N,B→O,…
- 【算法训练营Day12】二叉树part2
十八岁讨厌编程
算法训练营算法
文章目录翻转二叉树对称二叉树二叉树的最大深度二叉树的最小深度翻转二叉树题目链接:226.翻转二叉树解题逻辑:翻转二叉树也就是将所有非叶节点的左右孩子相互交换,那么我们就可以采用层序遍历判断非叶节点进行翻转:初始化一个辅助队列将根节点添加到队列中去弹出队头元素如果该元素的两个子节点均不为null则翻转两个子节点然后将子节点入队如此循环往复直到队列为空代码如下:classSolution{public
- 洛谷 P11120 [ROIR 2024 Day 1] 登机 题解
殇之夜
洛谷c++c语言算法
Part0前言这种题一看就是签到题,也是特水,建议评红或橙。Part1思路就是先将已有位置先填对称,然后将剩余还未添加的乘客以对称方式填入。首先可以特判掉需要的位置大于空位的情况,直接输出Impossible。然后用数组记录.和X的位置,先遍历所有X的位置,然后看他的对称位置是否为空,若为空,则填入X,然后m--。最后若musingnamespacestd;chara[1010][10];stru
- .NET中的安全性之数字签名、数字证书、强签名程序集、反编译
hezudao25
NET.netassembly加密算法referenceheader
本文将探讨数字签名、数字证书、强签名程序集、反编译等以及它们在.NET中的运用(一些概念并不局限于.NET在其它技术、平台中也存在)。1.数字签名数字签名又称为公钥数字签名,或者电子签章等,它借助公钥加密技术实现。数字签名技术主要涉及公钥、私钥、非对称加密算法。1.1公钥与私钥公钥是公开的钥匙,私钥则是与公钥匹配的严格保护的私有密钥;私钥加密的信息只有公钥可以解开,反之亦然。在VisualStud
- macd的python代码同花顺_同花顺最牛MACD副图源码
再来一碗饭
DIFF:EMA(CLOSE,6)-EMA(CLOSE,16),ColorFFFF26;DEA:EMA(DIFF,5),Color8A15FF;MACD:=2*(DIFF-DEA);对DIFF:0-(EMA(CLOSE,6)-EMA(CLOSE,16));对DEA:0-(EMA(DIFF,5));对称:0-(2*(DIFF-DEA)),STICK,ColorFF6060,LINETHICK1;{D
- 12. 说一下 https 的加密过程
yqcoder
前端面试-服务协议https网络协议http
总结客户端发送一个http请求,告诉服务器支持哪些hash算法。服务端发送证书(公钥、网址、证书机构等)给客户端。验证证书生成随机密码(RSA签名):对称密码用公钥加密,服务器用私钥解密。进行传输生成对称加密算法说一下HTTPS的加密过程HTTPS(HyperTextTransferProtocolSecure)是HTTP协议的安全版本,通过SSL/TLS协议实现数据加密传输,确保客户端与服务器之
- SpringBoot + Logback 实现日志脱敏【手把手案例】
甘蓝聊Java
【更新中...】项目中的那些事springbootlogbackLogback日志脱敏Java日志脱敏
文章目录背景分析现有Logback配置了解PatternLayout中的Converter解决第1步:创建自定义Converter第2步:自定义logback配置文件第3步:调整yaml配置第4步:启动服务并验证参考背景SpringBoot+MyBatis+MySQL+Logback框架,使用MySQL的AES_DECRYPT()和AES_ENCRYPT()函数,由于日志设置为debug级别,导致
- 【JMeter】接口加密
QA媛_
JMeterjmeter
文章目录哈希对称加密非对称加密JMeter实现加密调用函数示例加密是信息安全的重要手段,常用在身份认证、访问控制等安全场景。原理:对原有内容的特殊变换,从而隐藏内容,无法伪造内容。常见的算法:哈希对称加密非对称加密哈希优点:速度快缺点:无法还原场景:签名、内容校验著名算法:MD5、SHA-512对称加密优点:速度相当快,可以还原,加密密钥和解密密钥相同(逻辑简单)缺点:安全系数不高,解密者完全可以
- LeetCode Top100特训
九筒-
LeetCode算法力扣
更新中……两数相加盛水最多的容器电话号码的字母组合删除链表的倒数第N个结点字母异位词分组寻找两个正序数组的中位数合并区间不同路径(与最小路径和类似)正则表达式匹配颜色分类单词搜索只出现一次的数字合并K个升序链表接雨水移除元素最长有效括号不同的二叉搜索树验证二叉搜索树对称二叉树从前序与中序遍历序列构造二叉树最长连续序列排序链表乘积最大子数组编辑距离最小栈最小覆盖子串计算右侧小于当前元素的个数柱状图中
- 【力扣(LeetCode)】数据挖掘面试题0003: 356. 直线镜像
文章大纲题目描述**坐标变化规律**解题方案题目描述在一个二维平面空间中,给你n个点的坐标。问,是否能找出一条平行于y轴的直线,让这些点关于这条直线成镜像排布?平行于y轴的直线(即垂直于x轴的直线,其方程形式为(x=a),其中(a)为常数)的对称点具有以下显著特点:坐标变化规律设直线为(x=a),平面内任意一点(P(x,y))关于该直线的对称点为(P’(x’,y’)),则两者坐标满足:纵坐标不变:
- 详解Python实现DES加密解密方法
创新梦想无限
python网络开发语言Python
DES(DataEncryptionStandard)是一种常用的对称加密算法,它使用相同的密钥进行加密和解密。在本文中,我们将详细介绍如何使用Python实现DES加密和解密,并提供相应的源代码。DES算法使用了一个64位的密钥,但实际上只有56位被用于加密操作。剩下的8位用于奇偶校验,即每个字节的最高位用于校验。DES加密过程中,明文按照64位进行分组,经过一系列的置换、替代和置换运算后得到密
- 《扩散模型:AI图像生成革命背后的魔法》
Liudef06小白
人工智能人工智能
文章目录摘要引言一、扩散模型的基本概念与发展历程二、扩散模型的数学原理与工作机制三、扩散模型在图像生成中的革命性突破四、扩散模型面临的挑战与未来发展方向五、结论摘要本文系统阐述了扩散模型在AI图像生成领域的革命性作用及其核心原理。首先,梳理了扩散模型的基本概念、发展脉络及其相较于GANs、VAEs等传统生成模型的优势。其次,深入解析了其基于马尔可夫链和变分推断的数学基础,以及前向扩散/反向生成的核
- 【论文笔记ing】Pointerformer: Deep Reinforced Multi-Pointer Transformer for the Traveling Salesman Problem
Booksort
online笔记论文论文阅读transformer深度学习
论文中使用一个PointerFormer模型编码器部分:可逆残差模型堆叠解码器部分:指针网络自回归对于一次任务而言,推理阶段:编码器部分:一次解码器部分:循环N次,直至任务结束在训练阶段,使用强化学习,对于一个N个节点的TSP实例,算法中会以不同的起点,跑N次,得到N个轨迹,以满足TSP的对称特性,表示这都是属于一个TSP问题的(真实)解然后会计算这样表示归一化奖励,得到一个advantage,然
- KTO(Kahneman-Tversky Optimization)技术详解与工程实现
DK_Allen
大模型深度学习pytorch人工智能KTO
KTO(Kahneman-TverskyOptimization)技术详解与工程实现一、KTO核心思想KTO是基于行为经济学前景理论(ProspectTheory)的偏好优化方法,突破传统偏好学习需要成对数据的限制,仅需单样本绝对标注(好/坏)即可优化模型。其创新性在于:损失函数设计:将人类对"收益"和"损失"的非对称心理反应量化数据效率:无需构建偏好对(y_w>y_l),直接利用松散标注二、KT
- 构建安全密码存储策略:核心原则与最佳实践
weixin_47233946
信息安全安全
密码是用户身份认证的第一道防线,其存储安全性直接关系到用户隐私和企业信誉。近年来频发的数据泄露事件揭示了密码管理的关键性。本文将深入探讨从加密算法到系统性防护的完整密码存储方案,帮助开发者构建企业级安全防御体系。一、密码存储基本准则绝对禁止明文存储:即使采用数据库加密措施,直接存储用户原始密码仍存在不可逆泄露风险。运维人员权限滥用或备份文件泄露都可能成为突破口。加密≠安全:AES等对称加密存在密钥
- 第十五届蓝桥杯嵌入式客观题真题(第二场)(个人错点总结)
lo卖火柴的小熊猫
电子相关竞赛分享蓝桥杯职场和发展嵌入式硬件
题目忘记拷贝了--,回忆到的写一下1.常见放大器的功能有(ABCD)A.放大B.滤波C.振荡D.比较X.stm32的ADC功能描述正确的是(ABCD)A.自校准B.12位采样精度C.单/多采集设置D.软件设置左靠右靠数据阵列X.RS485旁路的对称电阻作用.(D)A.B.静电保护C.防止浪涌D.防止信号反射X.BUCK电路的电平转换功能(D)A.AC/ACB.AC/DCC.DC/ACD.DC/DC
- Springboot计算机毕业设计协同过滤的就业系统的设计与实现qd11f(程序+源码+数据库+调试部署+开发环境)带论文文档1万字以上,文末可获取,系统界面在最后面。
系统程序文件列表项目功能:学生,企业单位,岗位信息,春招信息,应聘信息,应聘通知,秋招信息,实训项目,项目选择,学院信息开题报告内容SpringBoot计算机毕业设计协同过滤的就业系统的设计与实现开题报告一、研究背景与意义1.1研究背景随着高等教育的普及与就业市场的多元化发展,高校毕业生数量逐年攀升,2025年全国毕业生预计突破1200万人。然而,传统就业服务模式存在以下问题:信息不对称:招聘信息
- CentOS服务器SSH远程连接全指南
Sally璐璐
运维服务器centosssh
CentOS服务器SSH远程连接全攻略|从安装到安全配置保姆级教程作为运维新手第一次接触CentOS服务器时,被SSH配置搞得焦头烂额!整理了从安装到高级安全设置的全流程,附超详细命令和避坑指南,手把手教你搞定远程连接基础概念扫盲SSH(SecureShell):Linux服务器最常用的远程管理协议,通过加密传输防止数据窃听。它采用非对称加密技术,在客户端和服务器之间建立安全通道,可以有效防止中间
- 【MyBatis插件全解析】动态代理+拦截链,打造你的专属ORM扩展
你是否想过在MyBatis执行SQL时自动添加分页功能?或者统一加密数据库敏感字段?MyBatis插件就是实现这些黑科技的终极武器!本文将带你彻底掌握插件开发的核心原理与实战技巧!一、插件能做什么?应用场景一览️1.典型应用场景场景实现效果代表插件SQL分页自动添加LIMIT/OFFSETPageHelper字段加解密出入参自动加解密CryptoInterceptorSQL性能监控记录慢查询并告警
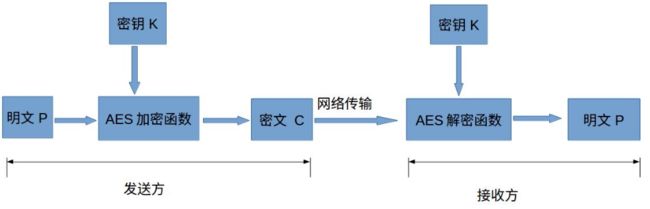
- 鸿蒙安全实战:三步实现AES加密,让你的用户密码坚不可摧!
前端世界
harmonyosharmonyos安全华为
摘要在鸿蒙应用中,数据加密是保护敏感信息(如用户密码)的核心手段。本文通过一个用户登录系统的实际场景,详细解析如何使用AES对称加密算法实现密码的安全存储与验证。我们将从密钥生成、加密存储到解密验证逐步展开,并提供完整代码实现和性能分析。描述当用户注册时,系统需将密码加密后存储;登录时需解密验证。直接存储明文密码存在严重安全隐患,而AES-256作为行业标准对称加密算法,能有效解决这一问题。鸿蒙通
- 【加解密与C】非对称加解密(二)ELGamel
阿捏利
加解密与Cc语言加解密ELGamel
ELGamel加密算法概述ELGamel是一种基于离散对数问题的公钥加密算法,由TaherElgamal在1985年提出。它是Diffie-Hellman密钥交换协议的扩展,广泛应用于数字签名和加密场景。ELGamel的安全性依赖于有限域上离散对数问题的计算难度。ELGamel密钥生成选择一个大素数(p)和一个生成元(g)(即(g)是(\mathbb{Z}_p^*)的生成元)。选择一个私钥(x),
- [创业之路-484]:企业经营层 - 职场人如何识别积极的工作环境:信任机制:从「分工协作」到「全能防御」;目标聚焦:从「价值创造」到「风险规避」;系统进化:从「熵减秩序」到「熵增混乱」。
前言:在一个分工明确安全可靠公平化的系统中,每个人只需要认真完成自己的目标,把其他环节交给受信任的队友,技术人只要关注技术,不需要防范被别人算计和坑害或吃亏。在一个不可靠不安全人治危机四伏的系统中,每个人不仅需要完成自己的目标,还需要把自己变成全才,以避免自己的付出在脱节的环节被淹没,还要关注各种无关的隐情,以避免在信息不对称时别忽悠,技术人员不仅仅要关注技术,还要人事,以防止一不小心暗算与坑害。
- 网络安全协议之SSL协议
北邮23级网安
sslweb安全网络
SSL协议简介什么是SSL协议?SSL协议是一种安全套接层协议,它可以在TCP协议的基础上提供数据的加密、身份验证和完整性保护。SSL协议主要由两部分组成:握手协议和记录协议。握手协议负责建立安全连接,交换公钥和证书,商定对称密钥等;记录协议负责使用对称密钥对数据进行加密和解密,以及检测数据的完整性。SSL协议常用于Web浏览器和Web服务器之间的通信,例如HTTPS。(HTTPS是一种安全的HT
- 你懂安全优化SSL嘛?
巴依老爷coder
安全安全ssl网络协议
一文带你了解SSL全部内容CIA?SSL概述加密算法对比数字签名与证书RSA加密算法代码实操1.更完善的错误处理2.证书验证3.资源管理改进常见的面试问题CIA?在信息安全领域,CIA(保密性、完整性、可用性)是核心原则,各有其实现方法与面临的威胁:保密性:实现方法:运用加密技术,对称加密(如AES)适合大量数据快速加密,非对称加密(如RSA)用于密钥交换与数字签名;借助访问控制手段,像基于角色的
- 宽带有哪几种接入方式
weixin_30252709
转:https://zhidao.baidu.com/question/1025089.html目前的家庭接入方式主要有三种:一是普通电话线的非对称数字用户环路技术(ADSL)方式、二是基于光纤IP网的FTTB+LAN技术方式(小区宽带),三是有线电视的CableModem技术方式(有线通)。ADSL使用一种调制解调传输技术,在普通电话线上将现有电话线路的频宽经由调制解调技术处理后扩大,其中较高容
- 区块链技术核心组件及应用架构的全面解析
区块链技术是一套融合密码学、分布式系统与经济激励的复合型技术体系,以下是其核心组件及应用架构的全面解析:一、区块链核心技术栈1.分布式账本技术(DLT)核心原理:多节点共同维护不可篡改的数据链数据结构:哈希指针哈希指针区块N区块N+1区块N+2关键创新:默克尔树(MerkleTree)实现高效数据验证2.密码学保障技术算法示例应用场景非对称加密ECC/secp256k1,RSA数字签名(设备身份认
- Java 并发包之线程池和原子计数
lijingyao8206
Java计数ThreadPool并发包java线程池
对于大数据量关联的业务处理逻辑,比较直接的想法就是用JDK提供的并发包去解决多线程情况下的业务数据处理。线程池可以提供很好的管理线程的方式,并且可以提高线程利用率,并发包中的原子计数在多线程的情况下可以让我们避免去写一些同步代码。
这里就先把jdk并发包中的线程池处理器ThreadPoolExecutor 以原子计数类AomicInteger 和倒数计时锁C
- java编程思想 抽象类和接口
百合不是茶
java抽象类接口
接口c++对接口和内部类只有简介的支持,但在java中有队这些类的直接支持
1 ,抽象类 : 如果一个类包含一个或多个抽象方法,该类必须限定为抽象类(否者编译器报错)
抽象方法 : 在方法中仅有声明而没有方法体
package com.wj.Interface;
- [房地产与大数据]房地产数据挖掘系统
comsci
数据挖掘
随着一个关键核心技术的突破,我们已经是独立自主的开发某些先进模块,但是要完全实现,还需要一定的时间...
所以,除了代码工作以外,我们还需要关心一下非技术领域的事件..比如说房地产
&nb
- 数组队列总结
沐刃青蛟
数组队列
数组队列是一种大小可以改变,类型没有定死的类似数组的工具。不过与数组相比,它更具有灵活性。因为它不但不用担心越界问题,而且因为泛型(类似c++中模板的东西)的存在而支持各种类型。
以下是数组队列的功能实现代码:
import List.Student;
public class
- Oracle存储过程无法编译的解决方法
IT独行者
oracle存储过程
今天同事修改Oracle存储过程又导致2个过程无法被编译,流程规范上的东西,Dave 这里不多说,看看怎么解决问题。
1. 查看无效对象
XEZF@xezf(qs-xezf-db1)> select object_name,object_type,status from all_objects where status='IN
- 重装系统之后oracle恢复
文强chu
oracle
前几天正在使用电脑,没有暂停oracle的各种服务。
突然win8.1系统奔溃,无法修复,开机时系统 提示正在搜集错误信息,然后再开机,再提示的无限循环中。
无耐我拿出系统u盘 准备重装系统,没想到竟然无法从u盘引导成功。
晚上到外面早了一家修电脑店,让人家给装了个系统,并且那哥们在我没反应过来的时候,
直接把我的c盘给格式化了 并且清理了注册表,再装系统。
然后的结果就是我的oracl
- python学习二( 一些基础语法)
小桔子
pthon基础语法
紧接着把!昨天没看继续看django 官方教程,学了下python的基本语法 与c类语言还是有些小差别:
1.ptyhon的源文件以UTF-8编码格式
2.
/ 除 结果浮点型
// 除 结果整形
% 除 取余数
* 乘
** 乘方 eg 5**2 结果是5的2次方25
_&
- svn 常用命令
aichenglong
SVN版本回退
1 svn回退版本
1)在window中选择log,根据想要回退的内容,选择revert this version或revert chanages from this version
两者的区别:
revert this version:表示回退到当前版本(该版本后的版本全部作废)
revert chanages from this versio
- 某小公司面试归来
alafqq
面试
先填单子,还要写笔试题,我以时间为急,拒绝了它。。时间宝贵。
老拿这些对付毕业生的东东来吓唬我。。
面试官很刁难,问了几个问题,记录下;
1,包的范围。。。public,private,protect. --悲剧了
2,hashcode方法和equals方法的区别。谁覆盖谁.结果,他说我说反了。
3,最恶心的一道题,抽象类继承抽象类吗?(察,一般它都是被继承的啊)
4,stru
- 动态数组的存储速度比较 集合框架
百合不是茶
集合框架
集合框架:
自定义数据结构(增删改查等)
package 数组;
/**
* 创建动态数组
* @author 百合
*
*/
public class ArrayDemo{
//定义一个数组来存放数据
String[] src = new String[0];
/**
* 增加元素加入容器
* @param s要加入容器
- 用JS实现一个JS对象,对象里有两个属性一个方法
bijian1013
js对象
<html>
<head>
</head>
<body>
用js代码实现一个js对象,对象里有两个属性,一个方法
</body>
<script>
var obj={a:'1234567',b:'bbbbbbbbbb',c:function(x){
- 探索JUnit4扩展:使用Rule
bijian1013
java单元测试JUnitRule
在上一篇文章中,讨论了使用Runner扩展JUnit4的方式,即直接修改Test Runner的实现(BlockJUnit4ClassRunner)。但这种方法显然不便于灵活地添加或删除扩展功能。下面将使用JUnit4.7才开始引入的扩展方式——Rule来实现相同的扩展功能。
1. Rule
&n
- [Gson一]非泛型POJO对象的反序列化
bit1129
POJO
当要将JSON数据串反序列化自身为非泛型的POJO时,使用Gson.fromJson(String, Class)方法。自身为非泛型的POJO的包括两种:
1. POJO对象不包含任何泛型的字段
2. POJO对象包含泛型字段,例如泛型集合或者泛型类
Data类 a.不是泛型类, b.Data中的集合List和Map都是泛型的 c.Data中不包含其它的POJO
- 【Kakfa五】Kafka Producer和Consumer基本使用
bit1129
kafka
0.Kafka服务器的配置
一个Broker,
一个Topic
Topic中只有一个Partition() 1. Producer:
package kafka.examples.producers;
import kafka.producer.KeyedMessage;
import kafka.javaapi.producer.Producer;
impor
- lsyncd实时同步搭建指南——取代rsync+inotify
ronin47
1. 几大实时同步工具比较 1.1 inotify + rsync
最近一直在寻求生产服务服务器上的同步替代方案,原先使用的是 inotify + rsync,但随着文件数量的增大到100W+,目录下的文件列表就达20M,在网络状况不佳或者限速的情况下,变更的文件可能10来个才几M,却因此要发送的文件列表就达20M,严重减低的带宽的使用效率以及同步效率;更为要紧的是,加入inotify
- java-9. 判断整数序列是不是二元查找树的后序遍历结果
bylijinnan
java
public class IsBinTreePostTraverse{
static boolean isBSTPostOrder(int[] a){
if(a==null){
return false;
}
/*1.只有一个结点时,肯定是查找树
*2.只有两个结点时,肯定是查找树。例如{5,6}对应的BST是 6 {6,5}对应的BST是
- MySQL的sum函数返回的类型
bylijinnan
javaspringsqlmysqljdbc
今天项目切换数据库时,出错
访问数据库的代码大概是这样:
String sql = "select sum(number) as sumNumberOfOneDay from tableName";
List<Map> rows = getJdbcTemplate().queryForList(sql);
for (Map row : rows
- java设计模式之单例模式
chicony
java设计模式
在阎宏博士的《JAVA与模式》一书中开头是这样描述单例模式的:
作为对象的创建模式,单例模式确保某一个类只有一个实例,而且自行实例化并向整个系统提供这个实例。这个类称为单例类。 单例模式的结构
单例模式的特点:
单例类只能有一个实例。
单例类必须自己创建自己的唯一实例。
单例类必须给所有其他对象提供这一实例。
饿汉式单例类
publ
- javascript取当月最后一天
ctrain
JavaScript
<!--javascript取当月最后一天-->
<script language=javascript>
var current = new Date();
var year = current.getYear();
var month = current.getMonth();
showMonthLastDay(year, mont
- linux tune2fs命令详解
daizj
linuxtune2fs查看系统文件块信息
一.简介:
tune2fs是调整和查看ext2/ext3文件系统的文件系统参数,Windows下面如果出现意外断电死机情况,下次开机一般都会出现系统自检。Linux系统下面也有文件系统自检,而且是可以通过tune2fs命令,自行定义自检周期及方式。
二.用法:
Usage: tune2fs [-c max_mounts_count] [-e errors_behavior] [-g grou
- 做有中国特色的程序员
dcj3sjt126com
程序员
从出版业说起 网络作品排到靠前的,都不会太难看,一般人不爱看某部作品也是因为不喜欢这个类型,而此人也不会全不喜欢这些网络作品。究其原因,是因为网络作品都是让人先白看的,看的好了才出了头。而纸质作品就不一定了,排行榜靠前的,有好作品,也有垃圾。 许多大牛都是写了博客,后来出了书。这些书也都不次,可能有人让为不好,是因为技术书不像小说,小说在读故事,技术书是在学知识或温习知识,有
- Android:TextView属性大全
dcj3sjt126com
textview
android:autoLink 设置是否当文本为URL链接/email/电话号码/map时,文本显示为可点击的链接。可选值(none/web/email/phone/map/all) android:autoText 如果设置,将自动执行输入值的拼写纠正。此处无效果,在显示输入法并输
- tomcat虚拟目录安装及其配置
eksliang
tomcat配置说明tomca部署web应用tomcat虚拟目录安装
转载请出自出处:http://eksliang.iteye.com/blog/2097184
1.-------------------------------------------tomcat 目录结构
config:存放tomcat的配置文件
temp :存放tomcat跑起来后存放临时文件用的
work : 当第一次访问应用中的jsp
- 浅谈:APP有哪些常被黑客利用的安全漏洞
gg163
APP
首先,说到APP的安全漏洞,身为程序猿的大家应该不陌生;如果抛开安卓自身开源的问题的话,其主要产生的原因就是开发过程中疏忽或者代码不严谨引起的。但这些责任也不能怪在程序猿头上,有时会因为BOSS时间催得紧等很多可观原因。由国内移动应用安全检测团队爱内测(ineice.com)的CTO给我们浅谈关于Android 系统的开源设计以及生态环境。
1. 应用反编译漏洞:APK 包非常容易被反编译成可读
- C#根据网址生成静态页面
hvt
Web.netC#asp.nethovertree
HoverTree开源项目中HoverTreeWeb.HVTPanel的Index.aspx文件是后台管理的首页。包含生成留言板首页,以及显示用户名,退出等功能。根据网址生成页面的方法:
bool CreateHtmlFile(string url, string path)
{
//http://keleyi.com/a/bjae/3d10wfax.htm
stri
- SVG 教程 (一)
天梯梦
svg
SVG 简介
SVG 是使用 XML 来描述二维图形和绘图程序的语言。 学习之前应具备的基础知识:
继续学习之前,你应该对以下内容有基本的了解:
HTML
XML 基础
如果希望首先学习这些内容,请在本站的首页选择相应的教程。 什么是SVG?
SVG 指可伸缩矢量图形 (Scalable Vector Graphics)
SVG 用来定义用于网络的基于矢量
- 一个简单的java栈
luyulong
java数据结构栈
public class MyStack {
private long[] arr;
private int top;
public MyStack() {
arr = new long[10];
top = -1;
}
public MyStack(int maxsize) {
arr = new long[maxsize];
top
- 基础数据结构和算法八:Binary search
sunwinner
AlgorithmBinary search
Binary search needs an ordered array so that it can use array indexing to dramatically reduce the number of compares required for each search, using the classic and venerable binary search algori
- 12个C语言面试题,涉及指针、进程、运算、结构体、函数、内存,看看你能做出几个!
刘星宇
c面试
12个C语言面试题,涉及指针、进程、运算、结构体、函数、内存,看看你能做出几个!
1.gets()函数
问:请找出下面代码里的问题:
#include<stdio.h>
int main(void)
{
char buff[10];
memset(buff,0,sizeof(buff));
- ITeye 7月技术图书有奖试读获奖名单公布
ITeye管理员
活动ITeye试读
ITeye携手人民邮电出版社图灵教育共同举办的7月技术图书有奖试读活动已圆满结束,非常感谢广大用户对本次活动的关注与参与。
7月试读活动回顾:
http://webmaster.iteye.com/blog/2092746
本次技术图书试读活动的优秀奖获奖名单及相应作品如下(优秀文章有很多,但名额有限,没获奖并不代表不优秀):
《Java性能优化权威指南》