CEH v11 笔记总结 Module 3
CEH v11 笔记
Module 3 Scanning Networks
1. Network Scanning Concepts
As already discussed, footprinting is the first phase of hacking, in which the attacker gains primary information about a potential target. He/she then uses this information in the scanning phase to gather more details about the target.
1.1. Overview of Network Scanning
Scanning is the process of gathering additional detailed information about the target using highly complex and aggressive reconnaissance techniques. Network scanning refers to a set of procedures used for identifying hosts, ports, and services in a network. Network scanning is also used for discovering active machines in a network and identifying the OS running on the target machine. It is one of the most important phases of intelligence gathering for an attacker, which enables him/her to create a profile of the target organization. In the process of scanning, the attacker tries to gather information, including the specific IP addresses that can be accessed over the network, the target’s OS and system architecture, and the ports along with their respective services running on each computer.
The purpose of scanning is to discover exploitable communications channels, probe as many listeners as possible, and track the ones that are responsive or useful to an attacker’s particular needs. In the scanning phase of an attack, the attacker tries to find various ways to intrude into a target system. The attacker also tries to discover more information about the target system to determine the presence of any configuration lapses(失误). The attacker then uses the information obtained to develop an attack strategy.
1.2. Types of Scanning
a. Port Scanning
Lists the open ports and services. Port scanning is the process of checking the services running on the target computer by sending a sequence of messages in an attempt to break in. Port scanning involves connecting to or probing TCP and UDP ports of the target system to determine whether the services are running or are in a listening state. The listening state provides information about the OS and the application currently in use. Sometimes, active services that are listening may allow unauthorized users to misconfigure systems or to run software with vulnerabilities. A general rule for computer systems is that the greater the number of open ports on a system, the more vulnerable is the system. However, there are cases in which a system with fewer open ports than another machine presents a much higher level of vulnerability.
b. Network Scanning
Lists the active hosts and IP addresses. Network scanning is a procedure for identifying active hosts on a network, either to attack them or assess the security of the network.
c. Vulnerability Scanning
Shows the presence of known weaknesses. Vulnerability scanning is a method for checking whether a system is exploitable by identifying its vulnerabilities. A vulnerability scanner consists of a scanning engine and a catalog. The catalog includes a list of common files with known vulnerabilities and common exploits for a range of servers. A vulnerability scanner may, for example, look for backup files or directory traversal(目录遍历) exploits. The scanning engine maintains logic for reading the exploit list, transferring the request to the web server, and analysing the requests to ensure the safety of the server. These tools generally target vulnerabilities that secure host configurations can fix easily through updated security patches and a clean web document.
1.3. Objectives of Network Scanning
The more the information at hand about a target organization, the higher are the chances of knowing a network’s security loopholes, and, consequently, for gaining unauthorized access to it. Some objectives for scanning a network are as follows:
- Discover the network’s live hosts, IP addresses, and open ports of the live hosts. Using the open ports, the attacker will determine the best means of entering into the system.
- Discover the OS and system architecture of the target. This is also known as fingerprinting. An attacker can formulate an attack strategy based on the OS’s vulnerabilities.
- Discover the services running/listening on the target system. Doing so gives the attacker an indication of the vulnerabilities (based on the service) that can be exploited for gaining access to the target system.
- Identify specific applications or versions of a particular service.
- Identify vulnerabilities in any of the network systems. This helps an attacker to compromise the target system or network through various exploits.
1.4. TCP Communication Flags
The TCP header contains various flags that control the transmission of data across a TCP connection. Six TCP control flags manage the connection between hosts and give instructions to the system. Four of these flags (SYN, ACK, FIN, and RST) govern the establishment, maintenance, and termination of a connection. The other two flags (PSH and URG) provide instructions to the system. The size of each flag is 1 bit. As there are six flags in the TCP Flags section, the size of this section is 6 bits. When a flag value is set to “1,” that flag is automatically turned on.
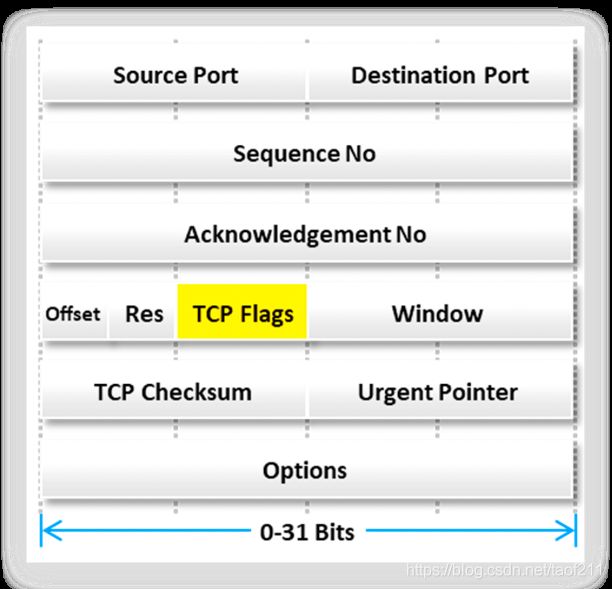

The following are details of the TCP communication flags:
a. SYN (Synchronize)
It notifies the transmission of a new sequence number. This flag generally represents the establishment of a connection (three-way handshake) between two hosts.
b. ACK (Acknowledgement)
It confirms the receipt of the transmission and identifies the next expected sequence number. When the system successfully receives a packet, it sets the value of its flag to “1,” thus implying that the receiver should pay attention to it.
c. PSH (Push)
When it is set to “1,” it indicates that the sender has raised the push operation to the receiver; this implies that the remote system should inform the receiving application about the buffered data coming from the sender. The system raises the PSH flag at the start and end of data transfer and sets it on the last segment of a file to prevent buffer deadlocks.
d. URG (Urgent)
It instructs the system to process the data contained in packets as soon as possible. When the system sets the flag to “1,” priority is given to processing the urgent data first and all the other data processing is stopped.
e. FIN (Finish)
It is set to “1” to announce that no more transmissions will be sent to the remote system and the connection established by the SYN flag is terminated.
f. RST (Reset)
When there is an error in the current connection, this flag is set to “1” and the connection is aborted in response to the error. Attackers use this flag to scan hosts and identify open ports.
SYN scanning mainly deals with three flags: SYN, ACK, and RST. You can use these three flags for gathering illegal information from servers during enumeration.
1.5. TCP/IP Communication
TCP is connection oriented, i.e., it prioritizes connection establishment before data transfer between applications. This connection between protocols is possible through the three-way handshake.
There are steps that a TCP session initiates using a three-way handshake mechanism:
- To launch a TCP connection, the source (10.0.0.2:21) sends a SYN packet to the destination (10.0.0.3:21).
- On receiving the SYN packet, the destination responds by sending a SYN/ACK packet back to the source.
- The ACK packet confirms the arrival of the first SYN packet to the source.
- Finally, the source sends an ACK packet for the ACK/SYN packet transmitted by the destination.
- This triggers an “OPEN” connection, thereby allowing communication between the source and destination, which continues until one of them issues a “FIN” or “RST” packet to close the connection.
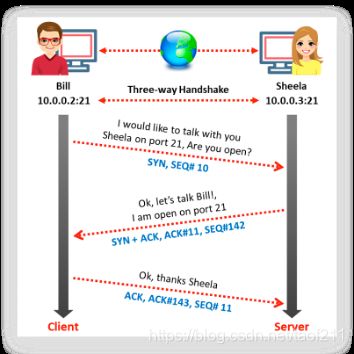
The TCP protocol maintains stateful connections for all connection-oriented protocols throughout the Internet and works similarly to ordinary telephone communication, in which one picks up a telephone receiver, hears a dial tone, and dials a number that triggers ringing at the other end until someone picks up the receiver and says, “Hello.”
There are steps that the system terminates the established TCP session as follows. After completing all the data transfers through the established TCP connection, the sender sends the connection termination request to the receiver through a FIN or RST packet. Upon receiving the connection termination request, the receiver acknowledges the termination request by sending an ACK packet to the sender and finally sends its own FIN packet. Then, the system terminates the established connection.

2. Scanning Tools
Scanning tools are used to scan and identify live hosts, open ports, running services on a target network, location info, NetBIOS info, and information about all TCP/IP and UDP open ports. The information obtained from these tools will help an ethical hacker in creating the profile of the target organization and scanning the network for open ports of the devices connected.
2.1. Nmap
Nmap (“Network Mapper”) is a security scanner for network exploration and hacking. It allows you to discover hosts, ports, and services on a computer network, thus creating a “map” of the network. It sends specially crafted packets to the target host and then analyses the responses to accomplish its goal. It scans vast networks of literally hundreds of thousands of machines. Nmap includes many mechanisms for port scanning (TCP and UDP), OS detection, version detection, ping sweeps, and so on. Either a network administrator or an attacker can use this tool for their specific needs. Network administrators can use Nmap for network inventory, managing service upgrade schedules, and monitoring host or service uptime(正常运行时间). Attackers use Nmap to extract information such as live hosts on the network, open ports, services (application name and version), type of packet filters/firewalls, MAC details, and OSs along with their versions. The basic syntax of Nmap is:
# nmap
2.2. Hping2/Hping3
Hping2/Hping3 is a command-line-oriented network scanning and packet crafting tool for the TCP/IP protocol that sends ICMP echo requests and supports TCP, UDP, ICMP, and raw-IP protocols. It performs network security auditing, firewall testing, manual path MTU discovery, advanced traceroute, remote OS fingerprinting, remote uptime guessing, TCP/IP stacks auditing, and other functions. It can send custom TCP/IP packets and display target replies similarly to a ping program with ICMP replies. It handles fragmentation(破碎) as well as arbitrary(任意的) packet body and size, and it can be used to transfer encapsulated files under the supported protocols. It also supports idle host scanning. IP spoofing and network/host scanning can be used to perform an anonymous probe for services. Hping2/Hping3 also has a Traceroute mode, which enables attackers to send files between covert channels. It also determines whether the host is up even when the host blocks ICMP packets. Its firewalk-like usage allows the discovery of open ports behind firewalls. It performs manual path MTU discovery and enables attackers to perform remote OS fingerprinting. Using Hping, an attacker can study the behaviour of an idle host and gain information about the target, such as the services that the host offers, the ports supporting the services, and the OS of the target. This type of scan is a predecessor to either heavier probing or outright attacks. The basic syntax of Hping is:
# hping
ICMP Scanning
A ping sweep or Internet Control Message Protocol (ICMP) scanning is a process of sending an ICMP request or ping to all the hosts on the network to determine the ones that are up. The OS, router, switch, and IP-based devices use this protocol via the ping command for echo request and echo response as a connectivity tester between different hosts.
ACK Scanning on Port 80
This scanning technique can be used to probe the existence of a firewall and its rule sets. Simple packet filtering allows the establishment of a connection (packets with the ACKbitset), whereas a sophisticated stateful firewall does not allow the establishment of a connection.
Hping Commands
The various hping commands are as following:
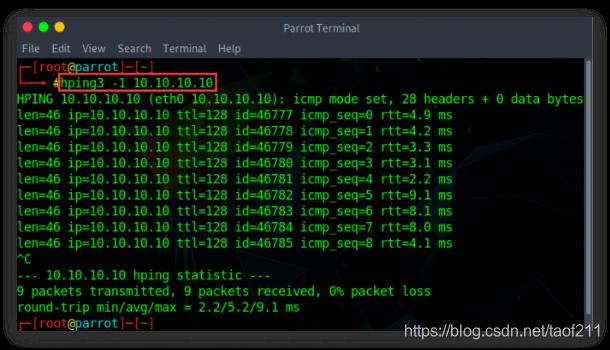
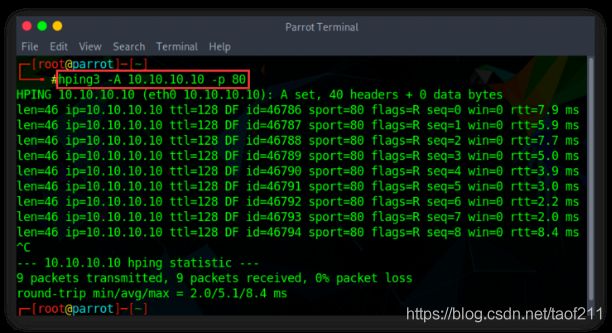
a. ICMP Ping
(Ex. hping3 -1 10.0.0.25)
Hping performs an ICMP ping scan by specifying the argument -1 in the command line. You may use --ICMP or -1 as the argument in the command line. By issuing the above command, hping sends an ICMP echo request to 10.0.0.25 and receives an ICMP reply similarly to a ping utility.
b. ACK Scan on Port 80
(Ex. hping3 –A 10.0.0.25 –p 80)
Hping can be configured to perform an ACK scan by specifying the argument -A in the command line. Here, you set the ACK flag in the probe packets and perform the scan. You perform this scan when a host does not respond to a ping request. By issuing this command, Hping checks if a host is alive on a network. If it finds a live host and an open port, it returns an RST response.
c. UDP Scan on Port 80
(Ex. hping3 -2 10.0.0.25 –p 80)
Hping uses TCP as its default protocol. Using the argument -2 in the command line specifies that Hping operates in the UDP mode. You may use either --udp or -2 as the argument in the command line. By issuing the above command, Hping sends UDP packets to port 80 on the host (10.0.0.25). It returns an ICMP port unreachable message if it finds the port closed and does not return a message if the port is open.
d. Collecting Initial Sequence Number
(Ex. hping3 192.168.1.103 -Q -p 139 –s)
Using the argument -Q in the command line, Hping collects all the TCP sequence numbers generated by the target host (192.168.1.103).
e. Firewalls and Timestamps
(Ex. hping3 -S 72.14.207.99 -p 80 --tcp-timestamp)
Many firewalls drop those TCP packets that do not have the TCP Timestamp option set. By adding the --tcp-timestamp argument in the command line, you can enable the TCP timestamp option in Hping and try to guess the timestamp update frequency and uptime of the target host (72.14.207.99).
f. SYN Scan on Port 50-60
(Ex. hping3 -8 50-60 –S 10.0.0.25 –V)
Using the argument -8 or --scan in the command line, you are operating Hping in the scan mode to scan a range of ports on the target host. Adding the argument -S allows you to perform a SYN scan. Therefore, the above command performs a SYN scan on ports 50–60 on the target host.
g. FIN, PUSH and URG Scan on Port 80
(Ex. hping3 –F –P –U 10.0.0.25 –p 80)
By adding the arguments –F, –P, and –U in the command line, you are setting FIN, PUSH, and URG packets in the probe packets. By issuing this command, you are performing FIN, PUSH, and URG scans on port 80 on the target host (10.0.0.25). If port 80 is open, you will not receive a response. If the port is closed, Hping will return an RST response.
h. Scan Entire Subnet for Live Host
(Ex. hping3 -1 10.0.1.x --rand-dest –I eth0)
By issuing this command, Hping performs an ICMP ping scan on the entire subnet 10.0.1.x; in other words, it sends an ICMP echo request randomly (–rand-dest) to all the hosts from 10.0.1.0 to 10.0.1.255 that are connected to the interface eth0. The hosts whose ports are open will respond with an ICMP reply. In this case, you have not set a port; hence, Hping sends packets to port 0 on all IP addresses by default.
i. Intercept All Traffic Containing HTTP Signature
(Ex. hping3 -9 HTTP –I eth0)
The argument -9 will set the Hping to the listen mode. Hence, by issuing the command -9 HTTP, Hping starts listening on port 0 (of all the devices connected in the network to interface eth0), intercepts all the packets containing the HTTP signature, and dumps from the signature end to the packet’s end. For example, on issuing the command hping2 -9 HTTP, if Hping reads a packet that contains data 234-09sdflkjs45-HTTPhello_world, it will display the result as hello_world.
j. SYN Flooding a Victim
(Ex. hping3 -S 192.168.1.1 -a 192.168.1.254 -p 22 --flood)
The attacker employs TCP SYN flooding techniques using spoofed IP addresses to perform a DoS attack.
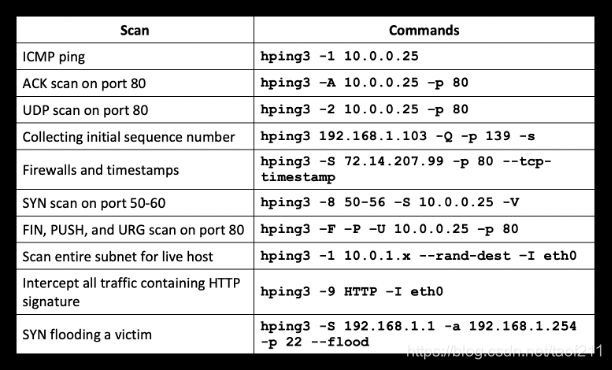
The following table lists the various scanning methods and their respective Hping commands:
2.3. Metasploit
Metasploit is an open-source project that provides the infrastructure, content, and tools to perform penetration tests and extensive security auditing. It provides information about security vulnerabilities and aids in penetration testing and IDS signature development. It facilitates the tasks of attackers, exploits writers, and payload writers. A major advantage of the framework is the modular approach, i.e., allowing the combination of any exploit with any payload. It enables you to automate the process of discovery and exploitation and provides you with the necessary tools to perform the manual testing phase of a penetration test. You can use Metasploit Pro to scan for open ports and services, exploit vulnerabilities, pivot further into a network, collect evidence, and create a report of the test results.
2.4. NetScanTools Pro
NetScanTools Pro is an investigation tool that allows you to troubleshoot, monitor, discover, and detect devices on your network. Using this tool, you can easily gather information about the local LAN as well as Internet users, IP addresses, ports, and so on. Attackers can find vulnerabilities and exposed ports in the target system. It helps the attackers to list IPv4/IPv6 addresses, hostnames, domain names, email addresses, and URLs automatically or manually (using manual tools). NetScanTools Pro combines many network tools and utilities categorized by their functions, such as active, passive, DNS, and local computer.
Some additional scanning tools are listed below:
- Unicornscan (https://sourceforge.net)
- SolarWinds Port Scanner (https://www.solarwinds.com)
- PRTG Network Monitor (https://www.paessler.com)
- OmniPeek Network Protocol Analyzer (https://www.savvius.com)
2.5. Scan Tools for Mobile
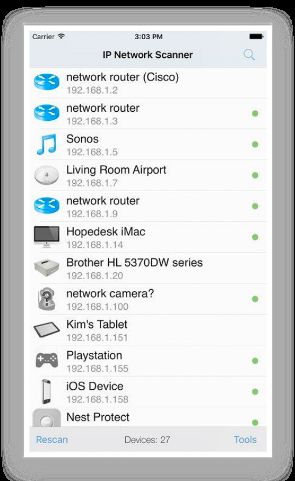
a. IP Scanner
IP Scanner for iOS scans your local area network to determine the identity of all its active machines and Internet devices. It allows attackers to perform network scanning activities along with ping and port scans.
b. Fing
Fing is a mobile app for Android and iOS that scans and provides complete network information, such as IP address, MAC address, device vendor, and ISP location. It allows attackers to discover all devices connected to a Wi-Fi network along with their IP and MAC address as well as the name of the vendor/device manufacturer. It also allows attackers to perform network pinging and traceroute activities through specific ports such as SSH, FTP, NetBIOS, etc.

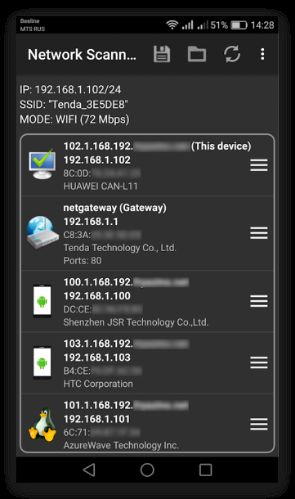
c. Network Scanner
Network Scanner is an Android mobile application that allows attackers to identify the active host in the range of possible addresses in a network. It also displays IP addresses, MAC addresses, host names, and vendor details of all the available devices in the network. This tool also allows attackers to port scan targets with specific port numbers.
3. Host Discovery
Host discovery is the first step in network scanning. Host discovery provides an accurate status of the systems in the network, which enables an attacker to avoid scanning every port on every system in a sea of IP addresses to identify whether the target host is up. As an ethical hacker, you must be aware of the various types of host discovery techniques. Some host discovery techniques are listed below:
3.1. ARP Ping Scan
In the ARP ping scan, the ARP packets are sent for discovering all active devices in the IPv4 range even though the presence of such devices is hidden by restrictive firewalls. In most networks, many IP addresses are unused at any given time, specifically in the private address ranges of the LAN. Hence, when the attackers try to send IP packets such as ICMP echo request to the target host, the OS must determine the hardware destination address (ARP) corresponding to the target IP for addressing the ethernet frame correctly. For this purpose, a series of ARP requests are issued. ARP scan is used to show the MAC address of the network interface on the device, and it can also show the MAC addresses of all devices sharing the same IPv4 address on the LAN. If the host IP with the respective hardware destination address is active, then the ARP response will be generated by the host; otherwise, after a certain number of ping attempts, the original OS gives up on the host. In other words, when attackers send ARP request probes to the target host, if they receive any ARP response, then the host is active. In case the destination host is found to be unresponsive, the source host adds an incomplete entry to the destination IP in its kernel ARP table.
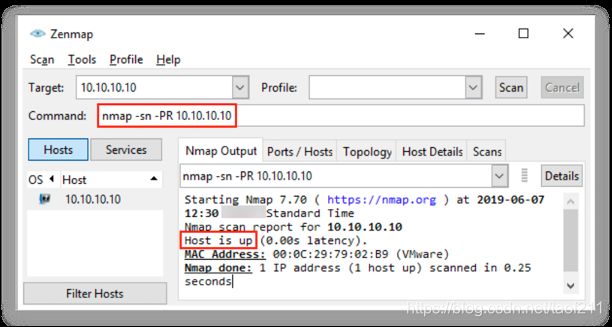
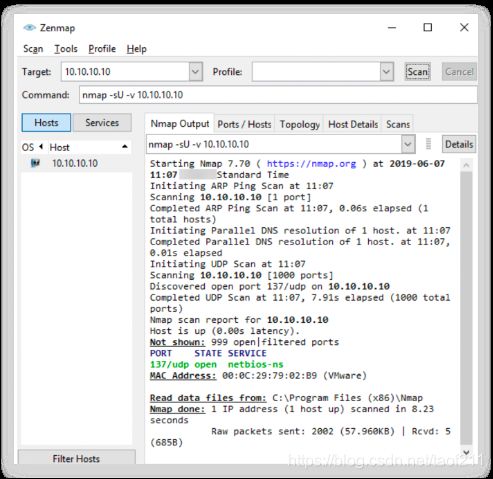
Attackers use the Nmap tool to perform ARP ping scan for discovering live hosts in the network. In Zenmap, the -PR option is used to perform ARP ping scan. Note: -sn is the Nmap command to disable the port scan. Since Nmap uses ARP ping scan as the default ping scan, to disable it and perform other desired ping scans, you can use --disable-arp-ping.

The advantages of ARP scan include:
- ARP ping scan is considered to be more efficient and accurate than other host discovery techniques
- ARP ping scan automatically handles ARP requests, retransmission, and timeout at its own discretion
- ARP ping scan is useful for system discovery, where you may need to scan large address spaces
- ARP ping scan can display the response time or latency of a device to an ARP packet
3.2. UDP Ping Scan
UDP ping scan is similar to TCP ping scan; however, in the UDP ping scan, Nmap sends UDP packets to the target host. The default port number used by Nmap for the UDP ping scan is 40,125. This highly uncommon port is used as the default for sending UDP packets to the target. This default port number can be configured using DEFAULT_UDP_PROBE_PORT_SPEC during compile time in Nmap. Attackers send UDP packets to the target host, and a UDP response means that the target host is active. If the target host is offline or unreachable, various error messages such as host/network unreachable or TTL exceeded could be returned. In Zenmap, the -PU option is used to perform the UDP ping scan.
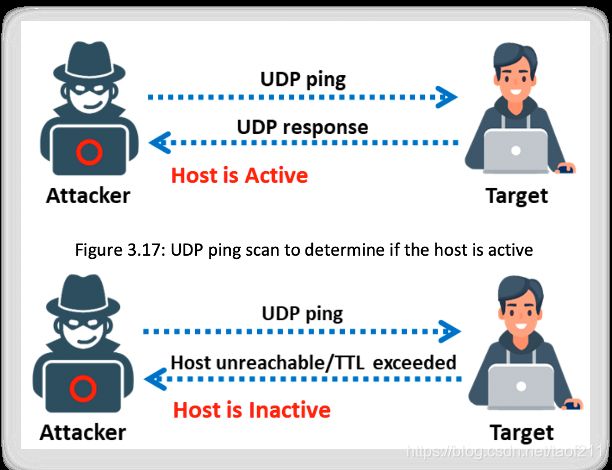
UDP ping scans have the advantage of detecting systems behind firewalls with strict TCP filtering, leaving the UDP traffic forgotten.

3.3. ICMP ECHO Ping Scan
Attackers use the ICMP ping scan to send ICMP packets to the destination system to gather all necessary information about it. This is because ICMP does not include port abstraction(抽象), and it is different from port scanning. However, it is useful to determine what hosts in a network are running by pinging them all. ICMP ECHO ping scan involves sending ICMP ECHO requests to a host. If the host is alive, it will return an ICMP ECHO reply. This scan is useful for locating active devices or determining if ICMP is passing through a firewall.

UNIX/Linux and BSD-based machines use ICMP echo scanning; the TCP/IP stack(栈) implementations in these OSs respond to the ICMP echo requests to the broadcast addresses. This technique does not work on Windows-based networks, as their TCP/IP stack implementation does not reply to ICMP probes directed at the broadcast address. Nmap uses the -P option to ICMP scan the target. The user can also increase the number of pings in parallel using the -L option. It may also be useful to tweak the ping timeout value using the - T option. In Zenmap, the -PE option is used to perform the ICMP ECHO ping scan. Active hosts are displayed as “Host is up,” as shown in the screenshot.
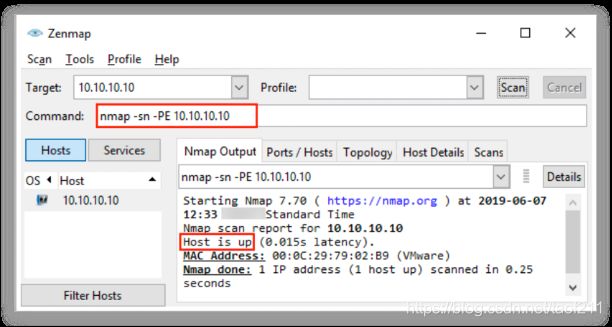
3.4. ICMP ECHO Ping Sweep
A ping sweep (also known as an ICMP sweep) is a basic network scanning technique that is adopted to determine the range of IP addresses that map to live hosts (computers). Although a single ping will tell the user whether a specified host computer exists on the network, a ping sweep consists of ICMP ECHO requests sent to multiple hosts. If a specified host is active, it will return an ICMP ECHO reply. Ping sweeps are among the oldest and slowest methods used to scan a network. This utility is distributed across nearly all platforms, and it acts as a roll call for systems; a system that is active on the network answers the ping query that another system sends out. ICMP echo scanning pings all the machines in the target network to discover live machines. Attackers send ICMP probes to the broadcast or network address, which relays to all the host addresses in the subnet. The live systems will send the ICMP echo reply message to the source of the ICMP echo probe.

To understand pings better, one should be able to understand the TCP/IP packet. When a system pings, it sends a single packet across the network to a specific IP address. This packet contains 64 bytes (56 data bytes and 8 bytes of protocol header information). The sender then waits or listens for a return packet from the target system. If the connections are good and the target computer is “alive,” a good return packet is expected. However, this will not be the case if there is a disruption in communication. Pings also detail the time taken for a packet to make a complete trip, called the “round-trip time.” They also help in resolving hostnames. In this case, if the packet bounces back when sent to the IP address, but not when sent to the name, then the system is unable to reconcile the name with the specific IP address. Attackers calculate subnet masks using subnet mask calculators to identify the number of hosts that are present in the subnet. They subsequently use ping sweep to create an inventory of live systems in the subnet.
Nmap helps an attacker to perform a ping sweep that determines live hosts from a range of IP addresses. In Zenmap, the -PE option with a list of IP addresses is used to perform ICMP ECHO ping sweep.
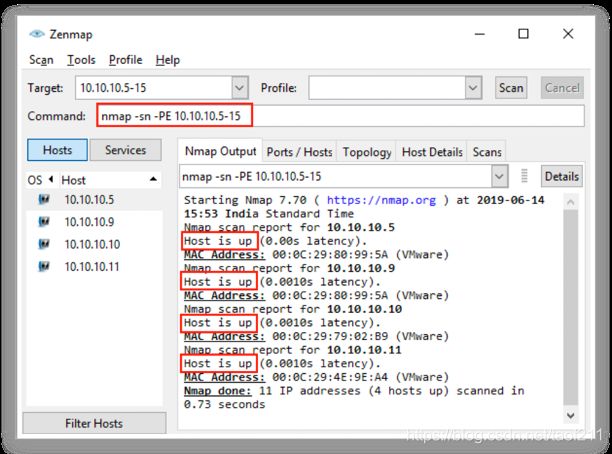
There’re more other ping sweep tools available:
a. Angry IP Scanner
Angry IP scanner is an IP address and port scanner. It can scan IP addresses in any range as well as any of their ports. It pings each IP address to check if it is alive; then, it optionally resolves its hostname, determines the MAC address, scans ports, and so on. The amount of data gathered about each host increases with plugins. Angry IP scanner has additional features, such as NetBIOS information (computer name, workgroup name, and currently logged in Windows user), favourite IP address ranges, web server detection, and customizable openers. The tool allows the user to save the scanning results to CSV, TXT, XML, or IP-Port list files. To increase the scanning speed, it uses a multithreaded approach: a separate scanning thread is created for each scanned IP address.


b. Additional tools
- SolarWinds Engineer’s Toolset (https://www.solarwinds.com)
- NetScanTools Pro (https://www.netscantools.com)
- Colasoft Ping Tool (https://www.colasoft.com)
- Visual Ping Tester (http://www.pingtester.net)
- OpUtils (https://www.manageengine.com)
Some countermeasures for avoiding ping sweep are as follows:
- Configure the firewall to detect and prevent ping sweep attempts instantaneously
- Use intrusion detection systems and intrusion prevention systems such as Snort (https://www.snort.org) to detect and prevent ping sweep attempts
- Carefully evaluate the type of ICMP traffic flowing through the enterprise networks
- Terminate the connection with any host that is performing more than 10 ICMP ECHO requests
- Use DMZ and allow only commands such as ICMP ECHO_REPLY, HOST UNREACHABLE, and TIME EXCEEDED in DMZ Zone
- Limit the ICMP traffic with Access Control Lists (ACLs) to your ISP’s specific IP addresses
3.5. ICMP Timestamp Ping Scan
Besides the traditional ICMP ECHO ping, there are some other types of ICMP pinging techniques such as ICMP timestamp ping scan and ICMP address mask ping scan, which an attacker can adopt in specific conditions. ICMP timestamp ping is an optional and additional type of ICMP ping whereby the attackers query a timestamp message to acquire(获得) the information related to the current time from the target host machine. The target machine responds with a timestamp reply to each timestamp query that is received. However, the response from the destination host is conditional, and it may or may not respond with the time value depending on its configuration by the administrator at the target’s end. This ICMP timestamp pinging is generally used for time synchronization. Such a ping method is effective in identifying whether the destination host machine is active, specifically in the condition where the administrator blocks the traditional ICMP ECHO ping requests. In Zenmap, the -PP option is used to perform an ICMP timestamp ping scan.

3.6. ICMP Address Mask Ping Scan
ICMP address mask ping is another alternative to the traditional ICMP ECHO ping, where the attackers send an ICMP address mask query to the target host to acquire information related to the subnet mask. However, the address mask response from the destination host is conditional, and it may or may not respond with the appropriate subnet value depending on its configuration by the administrator at the target’s end. This type of ping method is also effective in identifying the active hosts similarly to the ICMP timestamp ping, specifically when the administrator blocks the traditional ICMP Echo ping. In Zenmap, the -PM option is used to perform an ICMP address mask ping scan.
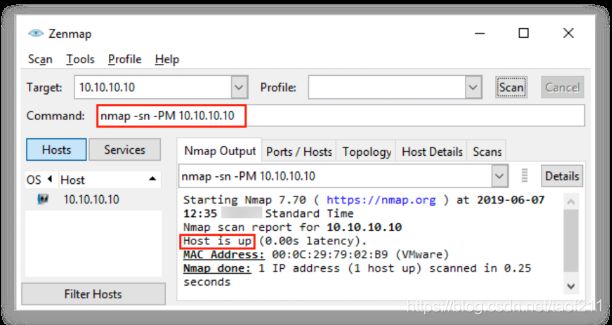
3.7. TCP SYN Ping Scan
TCP SYN ping is a host discovery technique for probing different ports to determine if the port is online and to check if it encounters any firewall rule sets. In this type of host discovery technique, an attacker uses the Nmap tool to initiate the three-way handshake by sending the empty TCP SYN flag to the target host. After receiving SYN, the target host acknowledges the receipt with an ACK flag. After reception of the ACK flag, the attacker confirms that the target host is active and terminates the connection by sending an RST flag to the target host machine (since his/her objective of host discovery is accomplished). Port 80 is used as the default destination port. A range of ports can also be specified in this type of pinging format without inserting a space between -PS and the port number (e.g., PS22-25,80,113,1050,35000), where the probe will be performed against each port parallelly. In Zenmap, the -PS option is used to perform a TCP SYN ping scan.
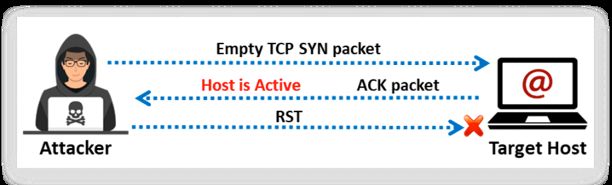
Advantages of TCP SYN ping scan include:
- As the machines can be scanned parallelly, the scan never gets the time-out error while waiting for the response.
- TCP SYN ping can be used to determine if the host is active without creating any connection. Hence, the logs are not recorded at the system or network level, enabling the attacker to leave no traces for detection.
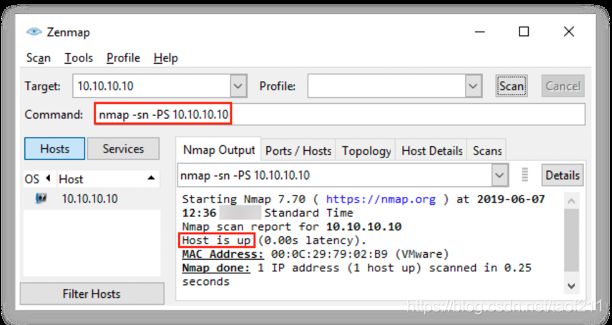
3.8. TCP ACK Ping Scan
TCP ACK ping is similar to TCP SYN ping, albeit with(尽管) minor variations. TCP ACK ping also uses the default port 80. In the TCP ACK ping technique, the attackers send an empty TCP ACK packet to the target host directly. Since there is no prior connection between the attacker and the target host, after receiving the ACK packet, the target host responds with an RST flag to terminate the request. The reception of this RST packet at the attacker’s end indicates that the host inactive. In Zenmap, the -PA option is used to perform a TCP ACK ping scan.
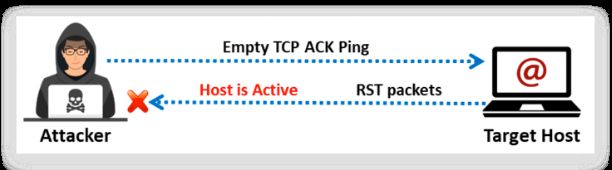
Both the SYN and the ACK packet can be used to maximize the chances of bypassing the firewall. However, firewalls are mostly configured to block the SYN ping packets, as they are the most common pinging technique. In such cases, the ACK probe can be effectively used to bypass these firewall rule sets easily.
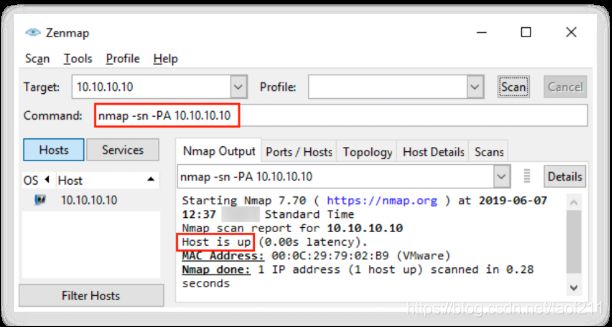
3.9. IP Protocol Ping Scan
IP protocol ping is the latest host discovery option that sends IP ping packets with the IP header of any specified protocol number. It has the same format as the TCP and UDP ping. This technique tries to send different packets using different IP protocols, hoping to get a response indicating that a host is online. Multiple IP packets for ICMP (protocol 1), IGMP (protocol 2), and IP-in-IP (protocol 4) are sent by default when no protocols are specified. For configuring the default protocols, change DEFAULT_PROTO_PROBE_PORT_SPEC in nmap.h during compile(编译) time. For specific protocols such as ICMP, IGMP, TCP (protocol 6), and UDP (protocol 17), the packets are to be sent with proper protocol headers, and for the remaining protocols, only the IP header data is to be sent with the packets.
![]()
In a nutshell, attackers send different probe packets of different IP protocols to the target host; any response from any probe indicates that a host is online. In Zenmap, the -PO option is used to perform an IP protocol ping scan.
4. Port & Service Discovery
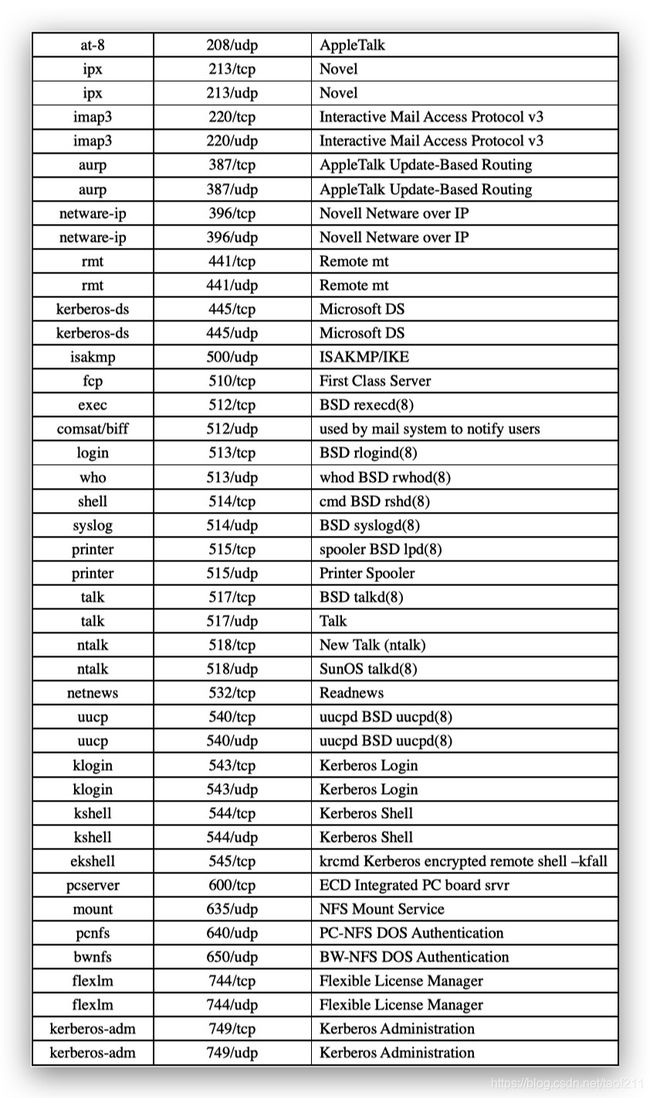
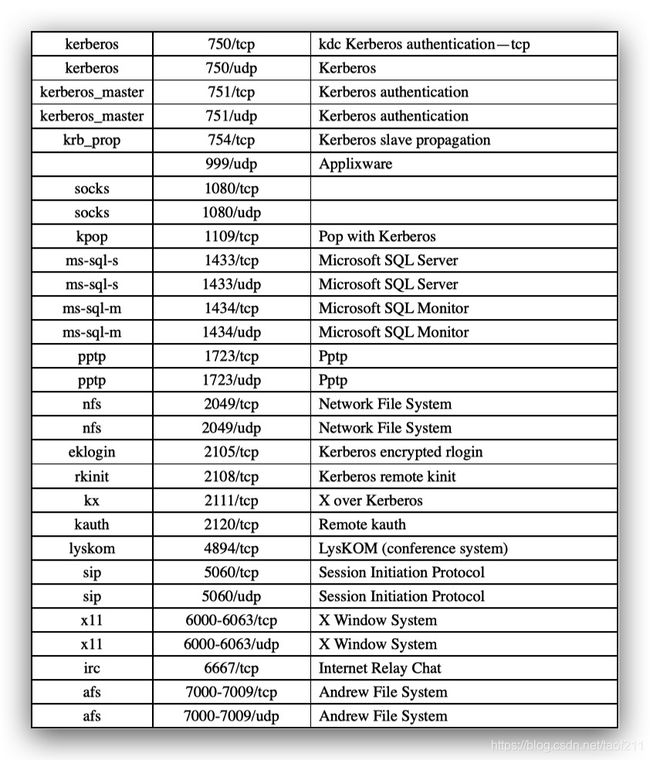
The next step in the network scanning process involves checking the open ports and services in live systems. After performing a ping scan, once attackers detect the live systems in the target network, they try to find open ports and services in the discovered live systems. This discovery of open ports and services can be performed via various port scanning techniques. Administrators often use port scanning techniques to verify the security policies of their networks, whereas attackers use them to identify open ports and running services on a host with the intent of compromising the network. Moreover, sometimes, users unknowingly keep unnecessary open ports on their systems. An attacker takes advantage of such open ports to launch attacks. Here’s a list of common ports and services.


4.1. TCP Connect/Full Open Scan
TCP Connect/Full Open Scan is one of the most reliable forms of TCP scanning. In TCP Connect scanning, the OS’s TCP connect() system call tries to open a connection to every port of interest on the target machine. If the port is listening, the connect() call will result in a successful connection with the host on that particular port; otherwise, it will return an error message stating that the port is not reachable. TCP Connect scan completes a three-way handshake with the target machine.
Making a separate connect() call for every targeted port in a linear manner would take a long time over a slow connection. The attacker can accelerate the scan using many sockets in parallel. Using non-blocking, I/O allows the attacker to set a short time-out period and watch all the sockets simultaneously(同时). In Zenmap, the -sT option is used to perform TCP Connect/full open scan.
The drawback of this type of scan is that it is easily detectable and filterable. The logs in the target system will disclose the connection. Such scanning does not require superuser privileges.
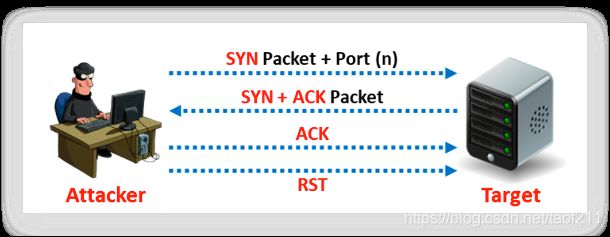
4.2. Stealth Scan (Half-open Scan)
The stealth(隐形) scan involves resetting the TCP connection between the client and the server abruptly(突然地) before completion of the three-way handshake signals, hence making the connection half-open. A stealth scan sends a single frame to a TCP port without any TCP handshaking or additional packet transfers. This type of scan sends a single frame with the expectation of a single response. The half-open scan partially opens a connection but stops halfway through. The stealth scan is also called a “SYN scan,” because it only sends the SYN packet. This prevents the service from notifying the incoming connection. TCP SYN or half-open scanning is a stealth method of port scanning. The stealth scan also implements the three-way handshake methodology. In the last stage, it examines the packets entering the interface and terminates the connection before triggering a new initialization to identify remote ports. The stealth scan process is described below.


Attackers use stealth scanning techniques to bypass firewall rules and logging mechanisms, and they hide themselves as usual under network traffic. In Zenmap, the -sS option is used to perform a stealth scan/TCP half-open scan.

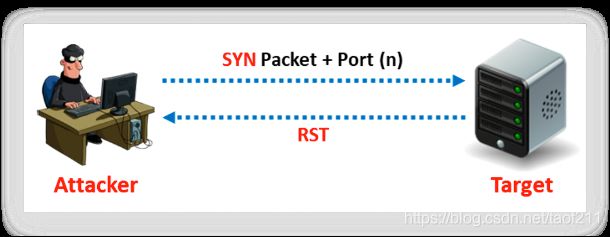
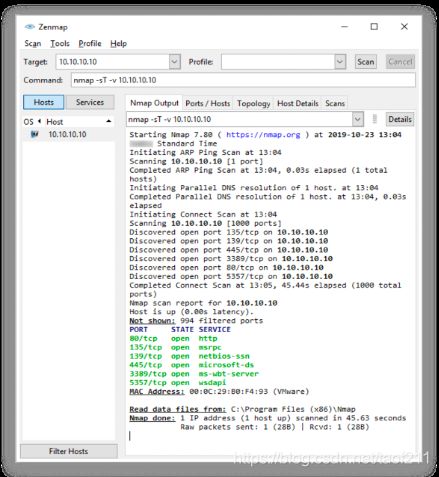
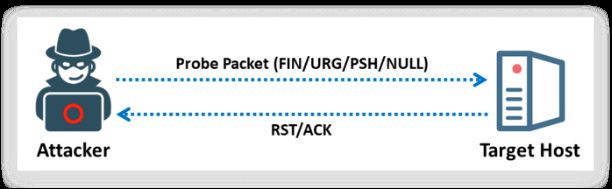
4.3. Inverse TCP Flag Scan
Attackers send TCP probe packets with a TCP flag (FIN, URG, PSH) set or with no flags. When the port is open, the attacker does not get any response from the host, whereas when the port is closed, he or she receives the RST from the target host.

Security mechanisms such as firewalls and IDS detect the SYN packets sent to the sensitive ports of the targeted hosts. Programs such as Synlogger and Courtney are available to log half-open SYN flag scan attempts. At times, the probe packets enabled with TCP flags can pass through filters undetected, depending on the security mechanisms installed. An inverted technique involves probing a target using a half-open SYN flag because the closed ports can only send the response back. According to RFC 793, an RST/ACK packet is sent for connection reset when the host closes a port. Attackers take advantage of this feature to send TCP probe packets to each port of the target host with various TCP flags set. Common flag configurations used for a probe packet include:
- A FIN probe with the FIN TCP flag set
- An Xmas probe with the FIN, URG, and PUSH TCP flags set
- A NULL probe with no TCP flags set
- A SYN/ACK probe
All closed ports on the targeted host will send an RST/ACK response. Since OSs such as Windows completely ignore the RFC 793 standard, you cannot see the RST/ACK response when connected to a closed port on the target host. However, this technique is effective when used with UNIX-based OSs.
The advantages of inverse TCP flag scan include:
- Avoids many IDS and logging systems.
- Highly stealthy.
The disadvantages of inverse TCP flag scan include:
- Needs raw access to network sockets, thus requiring super-user privileges
- Mostly effective against hosts using a BSD-derived TCP/IP stack (not effective against Microsoft Windows hosts, in particular)
Note: Inverse TCP flag scanning is known as FIN, URG, and PSH scanning based on the flag set in the probe packet. If there is no flag set, it is known as NULL scanning. If only the FIN flag is set, it is known as FIN scanning, and if all of FIN, URG, and PSH are set, it is known as Xmas scanning.
a. Xmas Scan
Xmas scan is a type of inverse TCP scanning technique with the FIN, URG, and PUSH flags set to send a TCP frame to a remote device. If the target has opened the port, then you will receive no response from the remote system. If the target has closed the port, then you will receive a remote system reply with an RST. You can use this port scanning technique to scan large networks and find which host is up and what services it is offering. This technique describes all TCP flag sets. When all flags are set, some systems hang; hence, the flags are often set in the nonsense pattern URG-PSH-FIN. Attackers use the TCP Xmas scan to determine if ports are closed on the target machine via the RST packet. This scan only works when systems are compliant with RFC 793-based TCP/IP implementation. It will not work against any current version of Microsoft Windows.
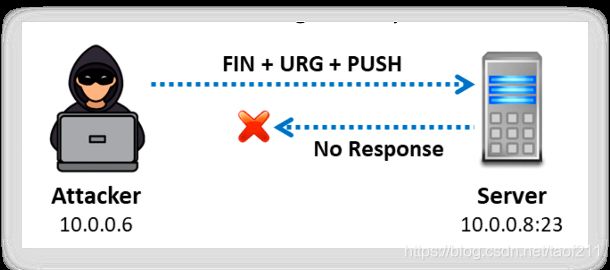

This method relies on the BSD networking code. Thus, you can use this only for UNIX hosts; it does not support Windows NT. If the user scans any Microsoft system, it will show that all the ports on the host are open. You can initialize all the flags when transmitting the packet to a remote host. If the target system accepts the packet and does not send any response, it means that the port is open. If the target system sends an RST flag, then it implies that the port is closed. The advantage of it is that it avoids IDS and TCP three-way handshake; while the disadvantage is that It works on the UNIX platform only.
In Zenmap, the -sX option is used to perform Xmas scan whereas the -sF and -sN options are used to perform FIN scan and NULL scan, respectively.
![]()
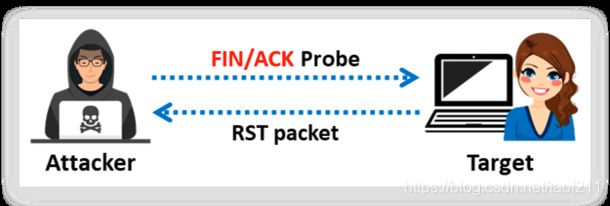
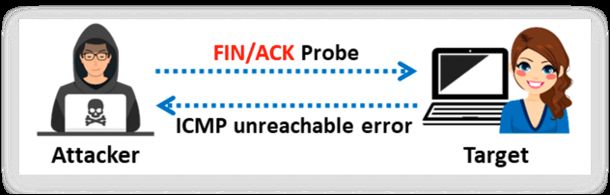
b. TCP Maimon scan
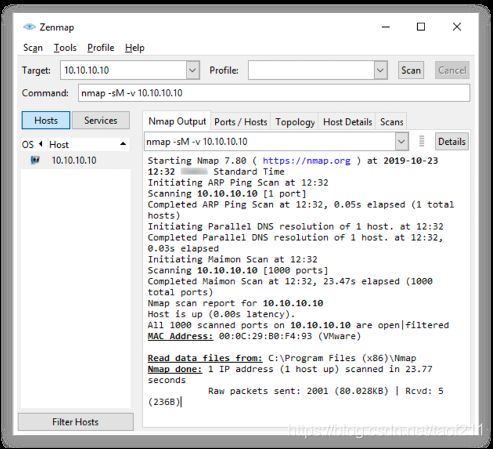
This scan technique is very similar to NULL, FIN, and Xmas scan, but the probe used here is FIN/ACK. In most cases, to determine if the port is open or closed, the RST packet should be generated as a response to a probe request. However, in many BSD systems, the port is open if the packet gets dropped in response to a probe. Nmap interprets a port as open/filtered when there is no response from the Maimon scan probe even after many retransmissions. The port is closed if the probe gets a response as an RST packet. The port is filtered when the ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13) is returned from the target host. In Zenmap, the -sM option is used to perform the TCP Maimon scan.

4.4. ACK Flag Probe Scan
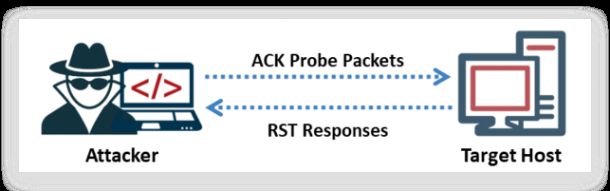
Attackers send TCP probe packets with the ACK flag set to a remote device and then analyse the header information (TTL and WINDOW field) of the received RST packets to find out if the port is open or closed. The ACK flag probe scan exploits the vulnerabilities within the BSD-derived TCP/IP stack. Thus, such scanning is effective only on those OSs and platforms on which the BSD derives TCP/IP stacks. Categories of ACK flag probe scanning include:
a. TTL-based ACK Flag Probe Scanning
In this scanning technique, you will first need to send ACK probe packets (several thousands) to different TCP ports and then analyse the TTL field value of the RST packets received. In Zenmap, the syntax nmap –ttl [time] [target] is used to perform TTL-based scan.

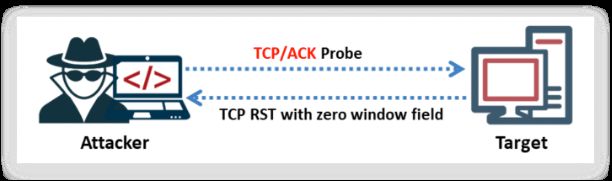
If the TTL value of the RST packet on a particular port is less than the boundary value of 64, then that port is open. An example showing a log of the first four RST packets received is presented below:
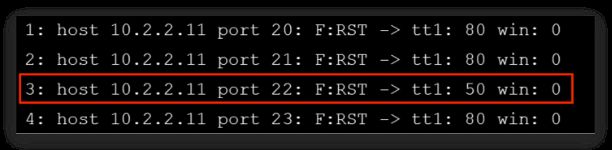
In this example, port 22 returned a TTL value of 50, which is less than 64; all other ports returned a TTL value of 80, which is greater than 64. Therefore, port 22 is open.
b. Window-based ACK Flag Probe Scanning
In this scanning technique, you will first need to send ACK probe packets (several thousands) to different TCP ports and then analyse the window field value of the received RST packets. The user can use this scanning technique when all the ports return the same TTL value. In Zenmap, the -sW option is used to perform a window scan.
If the window value of the RST packet on a particular port is non-zero, then that port is open. An example showing a log of the first four RST packets received is presented below:
![]()
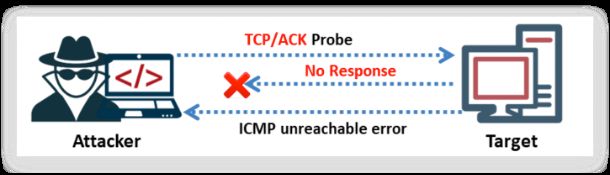
The above figure shows that the TTL value returned for each packet is the same; hence, you cannot perform TTL-based ACK flag probe scanning to find the open ports. Therefore, when you observe the window value, the third packet has a non-zero window value, which means that the port is open. When the returned RST value is zero, then the port is closed. If there is no response even after many retransmissions and an ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13) is returned, then the port is inferred to be a filtered port.

The advantage of ACK flag probe scan is that this type of scan can evade(逃避) IDS in most cases; while the disadvantage is that it is extremely slow and can exploit only older OSs with vulnerable BSD-derived TCP/IP stacks.
The ACK flag probe scanning technique also helps in checking the filtering systems of target networks. The attacker sends an ACK probe packet to check the filtering mechanism (firewalls) of packets employed by the target network. Sending an ACK probe packet with a random sequence number and getting no response from the target means that the port is filtered (stateful firewall is present); an RST response from the target means that the port is not filtered (no firewall is present).

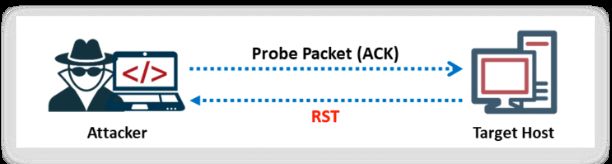
In Zenmap, the -sA option is used to perform an ACK flag probe scan.

4.5. IDLE/IPID Header Scan
The IDLE/IPID Header scan is a TCP port scan method that you can use to send a spoofed source address to a computer to find out what services are available. It offers complete blind scanning of a remote host. Most network servers listen on TCP ports, such as web servers on port 80 and mail servers on port 25. A port is considered “open” if an application is listening on the port. One way to determine whether a port is open is to send a “SYN” (session establishment) packet to the port. The target machine will send back a “SYN-ACK” (session request acknowledgement) packet if the port is open or an “RST” (Reset) packet if the port is closed. A machine that receives an unsolicited SYN-ACK packet will respond with an RST. An unsolicited RST will be ignored. Every IP packet on the Internet has a “fragment identification” number (IPID). The OS increases the IPID for each packet sent; thus, probing an IPID gives an attacker the number of packets sent since the last probe. In Zenmap, the -sI option is used to perform the IDLE scan.
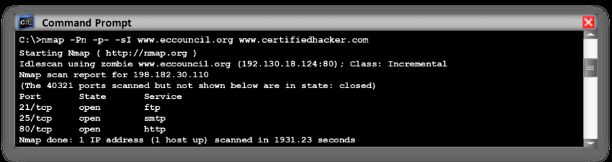
The attacker performs this scan by impersonating another computer via spoofing. The attacker does not send a packet from her/his IP address; instead, he/she uses another host, often called a “zombie,” to scan the remote host and identify any open ports. In this attack, the attacker expects the sequence numbers of the zombie host, and if the remote host checks the IP of the scanning party, the IP of the zombie machine will be displayed.
Every IP packet on the Internet has a fragment Internet protocol identification (IPID) number that uniquely identifies fragments of an original IP datagram. As many OSs simply increase this number for each packet that they send, probing the IPID can tell an attacker how many packets the user sent since the last probe.
a. Step 1 - Choose a “Zombie” & Probe its Current IPID
The first step in performing an idle scan is to find an appropriate zombie. A zombie that assigns IPID packets incrementally on a global basis is an appropriate or idle zombie for performing the idle scan. The shorter the time interval for request/response between the attacker-zombie and the zombie-target, the faster is the scan. In the first step, you will send the SYN+ACK packet to the zombie machine to probe its IPID number. Here, the SYN+ACK packet is sent to probe the IPID number but not establish a TCP connection (three-way handshake).
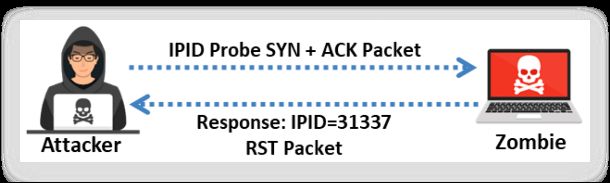
As the zombie does not expect a SYN+ACK packet, it will deny the connection by sending back an RST packet. Analyse the RST packet sent by the zombie machine to extract the IPID. In the diagram shown in the slide above, assume that the zombie responds with IPID=31337. Furthermore, assume that this IPID is X.
b. Step 2 - Idle Scan
The attacker sends a SYN packet to the target machine on port 80, spoofing the IP address of the zombie. If the port is open, the target will send the SYN+ACK packet to the zombie (as the IP address was spoofed) to proceed with the three-way handshake. Since the zombie did not expect a SYN+ACK packet from the target machine, it will respond with an RST packet.
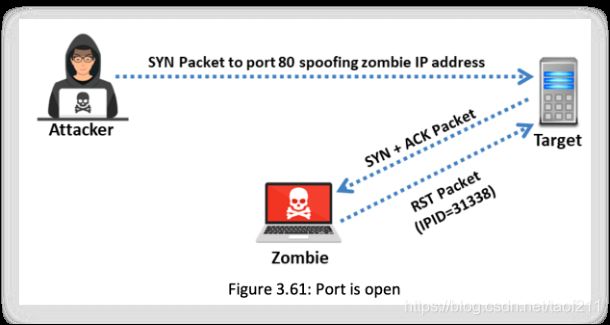
Since every IP packet has a “fragment identification” number, which increases by one for every packet transmission, the zombie will now use its next available IPID, i.e., 31338 (X + 1).
Assume that the port on the target is closed. Subsequently, on receiving the SYN packet from the attacker (you), the target will respond with an RST, and the zombie will remain idle without taking any further action.
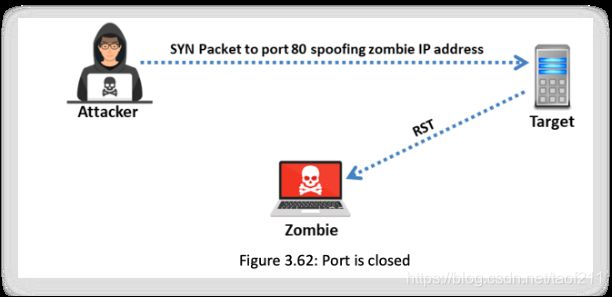
c. Step 3
Now, follow step 1 again to probe the IPID number.

Send a SYN+ACK packet to the zombie, and it will respond with an RST packet containing the IPID. Assume that the port on the target was open and that the zombie has already sent an RST packet to the target; then, the IPID number is increased by 1. Now, the zombie responds with an RST packet to the attacker using its next IPID, i.e., 31339 (X + 2). Consequently, the IPID is increased by 2, which implies that the port on the target machine was open. Thus, using an idle scan, an attacker can find out the open ports and services on the target machine by spoofing his/her IP address with a zombie’s IP address.
4.6. UDP Scanning
UDP port scanners use the UDP protocol instead of TCP. There is no three-way handshake for the UDP scan. The UDP protocol can be more challenging to use than TCP scanning because you can send a packet, but you cannot determine whether the host is alive, dead, or filtered. However, you can use one ICMP that checks for open or closed ports. If you send a UDP packet to a port without an application bound to it, the IP stack will return an ICMP port unreachable packet. If any port returns an ICMP error, it will be closed, leaving the ports that did not answer if they are open or filtered through the firewall.
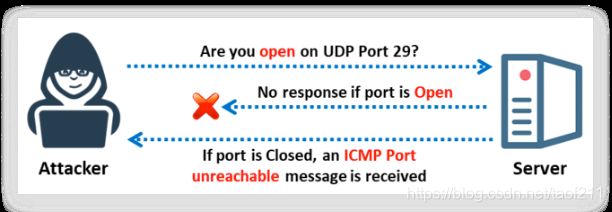
This happens because open ports do not have to send an acknowledgement in response to a probe, and closed ports are not even required to send an error packet. When you send a packet to a closed UDP port, most of the hosts send an ICMP_PORT_UNREACH error. Thus, you can determine whether a port is not open if UDP packets or ICMP errors are not guaranteed to arrive. Thus, UDP scanners of this type must implement retransmission of packets that appear lost. UDP scanners interpret lost traffic as open ports. In Zenmap, the -sU option is used to perform a UDP scan.
In addition, this scanning technique is slow because it limits the ICMP error message rate as a form of compensation to machines that apply RFC 1812 section 4.3.2.8. A remote host will require access to the raw ICMP socket to distinguish closed ports from unreachable ports.
UDP RECVFROM () and WRITE () Scanning
Although non-root users cannot read unreachable port errors directly, Linux informs you indirectly when it receives messages. For example, a second write () call to a closed port will usually fail. Various scanners, such as Netcat and Pluvial pscan.c, perform recvfrom () on non-blocking UDP sockets, and they usually return EAGAIN (“Try Again,” errno 13) if the ICMP error has not been received or ECONNREFUSED (“Connection refused,” errno 111) otherwise. This technique is used for determining open ports when non-root users use - u (UDP). Root users can also use the -l (lamer UDP scan) option to force this process.
Advantage
The UDP scan is less informal with regard to an open port because there is no overhead of a TCP handshake. However, if ICMP is responding to each unavailable port, the total number of frames(帧数) can exceed that from a TCP scan. Microsoft-based OSs do not usually implement any ICMP rate limiting; hence, this scan operates very efficiently on Windows-based devices.
Disadvantage
The UDP scan provides port information only. If additional information of the version is needed, the scan must be supplemented with a version detection scan (-sV) or the OS fingerprinting option (-O). The UDP scan requires privileged access; hence, this scan option is only available on systems with the appropriate user permissions. Most networks have massive amounts of TCP traffic; as a result, the efficiency of the UDP scan is low. The UDP scan will locate open ports and provide the security manager with valuable information for identifying successful attacker invasions(侵犯) on open UDP ports owing to spyware applications, Trojan horses, and other malicious software.
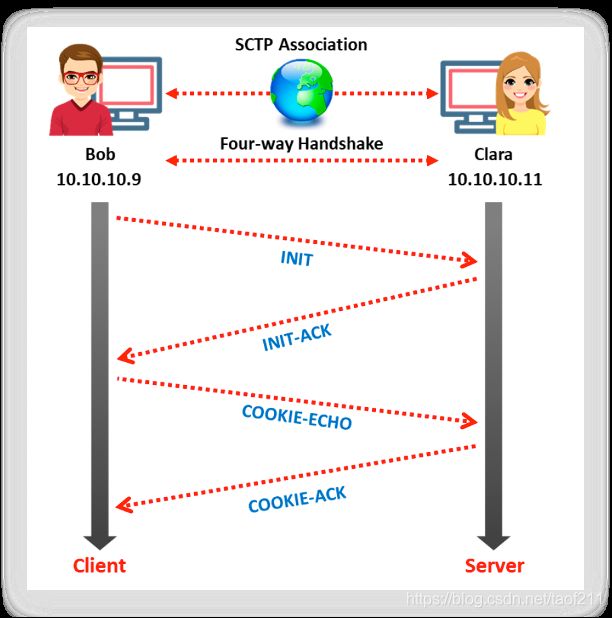
4.7. SCTP INIT Scanning
Stream Control Transport Protocol (SCTP) is a reliable message-oriented transport layer protocol. It is used as an alternative to the TCP and UDP protocols, as its characteristics are similar to those of TCP and UDP. SCTP is specifically used to perform multi-homing and multi-streaming activities. Some SCTP applications include discovering VoIP, IP telephony, and Signaling System 7/SIGnaling TRANsport (SS7/SIGTRAN)-related services. SCTP association comprises a four-way handshake method, as shown in the screenshot below.
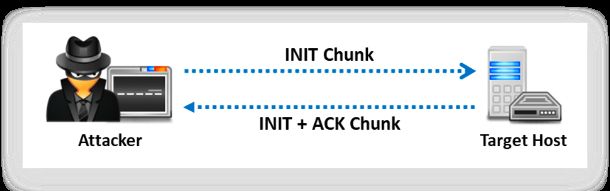
In SCTP, the INIT scan is performed quickly by scanning thousands of ports per second on a fast network not obstructed(阻碍) by a firewall offering a stronger sense of security. The SCTP INIT scan is very similar to the TCP SYN scan; comparatively, it is also stealthy and unobtrusive, as it cannot complete SCTP associations, hence making the connection half-open. Attackers send INIT chunk(大块) to the target host. If the port is listening or open, it sends an acknowledgement as an INIT+ACK chunk. If the target is inactive and it is not listening, then it sends an acknowledgement as an ABORT chunk.
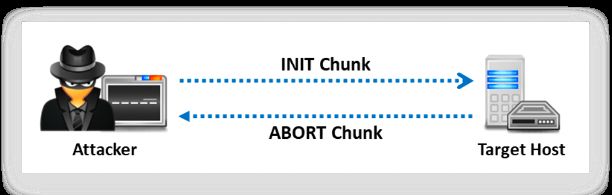
After several retransmissions, if there is no response, then the port is indicated as a filtered port. The port is also indicated as a filtered port if the target server responds with an ICMP unreachable exception (type 3, code 0, 1, 2, 3, 9, 10, or 13). In Zenmap, the -sY option is used to perform the SCTP INIT scan. INIT scan can clearly differentiate between various ports such as open, closed, and filtered states.
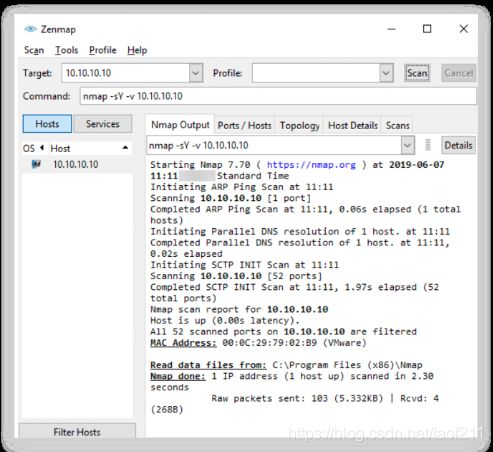
4.8. SCTP COOKIE ECHO Scanning
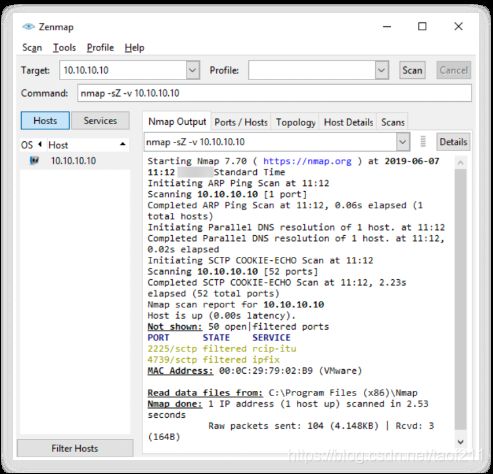
SCTP COOKIE ECHO scan is a more advanced type of scan. In this type of scan, attackers send the COOKIE ECHO chunk to the target, and if the target port is open, it will silently drop the packets onto the port, and you will not receive any response from the target. If the target sends back the ABORT chunk response, then the port is considered as a closed port. The COOKIE ECHO chunk is not blocked by non-stateful firewall rule sets as in the INIT scan. Only an advanced IDS can detect the SCTP COOKIE ECHO scan. In Zenmap, the -sZ option is used to perform the SCTP COOKIE ECHO scan.
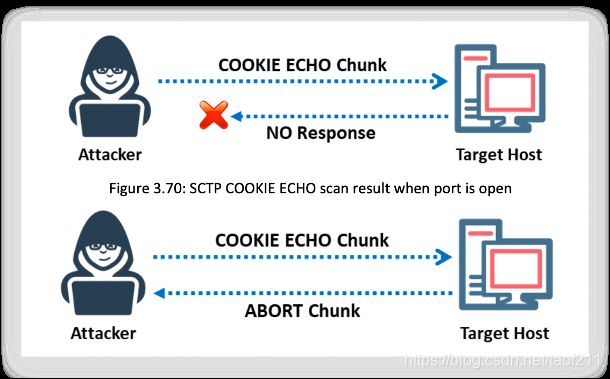
The SCTP COOKIE ECHO scan is not as conspicuous(显眼的) as the INIT scan, however, it cannot differentiate clearly between open and filtered ports, and it shows the output as open|filtered in both cases.
4.9. SSDP and List Scanning
Simple Service Discovery Protocol (SSDP) is a network protocol that generally communicates with machines when querying them with routable IPv4 or IPv6 multicast addresses. The SSDP service controls communication for the Universal Plug and Play (UPnP) feature. It generally works when the machine is not firewalled; however, it can sometimes work through a firewall. The SSDP service will respond to a query sent over IPv4 or IPv6 broadcast addresses. This response includes information about the UPnP feature associated with it. The attacker uses SSDP scanning to detect UPnP vulnerabilities that may allow him/her to launch buffer overflow or DoS attacks.
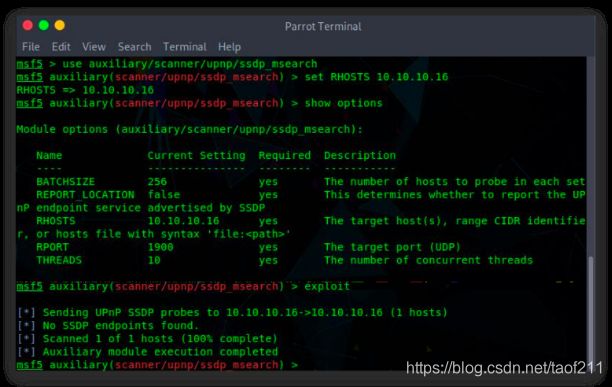
The attacker may use the UPnP SSDP M-SEARCH information discovery tool to check whether the machine is vulnerable to UPnP exploits. The UPnP SSDP M-SEARCH information discovery tool gleans(收集) information from UPnP-enabled systems, as shown in the figure.
In a list scan, the discovery of the active network host is indirect. A list scan simply generates and prints a list of IPs/Names without actually pinging or scanning the hosts. As a result, the list scan shows all IP addresses as “not scanned” (0 hosts up). By default, a reverse DNS resolution is still carried out on each host by Nmap to learn their names. In Zenmap, the -sL option is used to perform a list scan.
A list scan can perform a good sanity check(合理性检验), and the list scan detects incorrectly defined IP addresses in the command line or in an option file. It primarily repairs the detected errors to run any “active” scan.
4.10. IPv6 Scanning
IPv6 increases the size of the IP address space from 32 bits to 128 bits to support higher levels of the addressing hierarchy. Traditional network scanning techniques are computationally less feasible(可行的) because of the larger search space (64 bits of host address space, or 264 addresses) provided by IPv6 in a subnet. Scanning the IPv6 network is more difficult and complex compared to IPv4. Additionally, a number of scanning tools do not support ping sweeps on IPv6 networks. Attackers need to harvest(收割) IPv6 addresses from network traffic, recorded logs, or “Received from” and other header lines in archived email or Usenet news messages to identify IPv6 addresses for subsequent port scanning. However, scanning an IPv6 network provides a large number of hosts in a subnet; if an attacker can compromise one subnet host, he/she can probe the “all hosts” link local multicast address if the hosts numbers are sequential or use any regular scheme. An attacker needs to analyse 264 addresses to verify if a particular open service is running on a host in that subnet. At a conservative rate of one probe per second, such a scan would take about 5 billion years to complete. Attackers can use Nmap to perform IPv6 scanning. In Zenmap, the -6 option is used to perform the IPv6 scan.

4.11. Service Version Discovery
Every port is assigned a specific service, and every service has its own version. Some versions of the protocols are insecure, and they can allow attackers to compromise the machine by exploiting this vulnerability. Service version detection helps attackers to obtain information about the running services and their versions on a target system. By obtaining accurate service version numbers, an attacker can determine which exploits the target system is vulnerable to. For example, when the attacker detects the SMBv1 protocol as a running service on the target Windows machine, then he/she can easily perform a WannaCry ransomware attack with the help of the eternalblue and doublepulsar backdoor combination in Metasploit. The version detection technique is nothing but examination of the TCP and UDP ports. The probes from the Nmap service-probes database are used for querying various services and matching expressions for recognizing and parsing responses. In Zenmap, the -sV option is used to detect service versions.

4.12. Nmap Scan Time Reduction Techniques
In Nmap, performance and accuracy take high priority, and this only be achieved only by reducing the long scan time. The important techniques for reducing the scan time are as follows:
a. Omit(省略) Non-critical Tests
While performing the Nmap scan, the time complexity can be reduced by the following methods:
- Avoiding an intense(密集的) scan if only a minimal amount of information is required.
- The number of ports scanned can be limited using specific commands.
- The port scan (-sn) can be skipped if and only if one has to check whether the hosts are online or not.
- Advanced scan types (-sC, -sV, -O, --traceroute, and -A) can be avoided.
- The DNS resolution should be turned on only when it is necessary.
b. Optimize Timing Parameters
To control the scan activity, Nmap provides the -T option for scanning ranging from high-level to low-level timing aggressiveness. This can be extremely useful for scanning highly filtered networks.
c. Separate and Optimize UDP Scans
As many vulnerable services use the UDP protocol, scanning the UDP protocol is vital, and it should be scanned separately, as TCP scans have different performance requirements and timing characteristics. Moreover, the UDP scan is more affected by the ICMP error rate-limiting compared to the TCP scan.
d. Upgrade Nmap
It is always advisable to use the upgraded version of Nmap as it contains many bug fixes, important algorithmic enhancements, and high-performance features such as local network ARP scanning.
e. Execute Concurrent(同时存在的) Nmap Instances
Running Nmap against the whole network usually makes the system slower and less efficient. Nmap supports parallelization(平行化) and it can also be customized according to specific needs. It becomes very efficient by getting an idea of the network reliability while scanning a larger group. The overall speed of the scan can be improved by dividing it into many groups and running them simultaneously.
f. Scan from a Favourable Network Location
It is always advisable to run Nmap from the host’s local network to the target while in the internal network, as it offers defense-in-depth security. External scanning is obligatory(必要的) when performing firewall testing or when the network should be monitored from the external attacker’s viewpoint.
g. Increase Available Bandwidth and CPU Time
By increasing the available bandwidth or CPU power, the Nmap scan time can be reduced. This can be done by installing a new data line or stopping any running applications. Nmap is controlled by its own congestion(拥堵) control algorithms, so that network flooding can be prevented. This improves its accuracy. The Nmap bandwidth usage can be tested by running it in the verbose(冗长的) mode -v.
4.13. Port Scanning Countermeasures
As discussed previously, port scanning provides a large amount of useful information to the attacker, such as IP addresses, host names, open ports, and services running on ports. Open ports specifically offer an easy means for the attacker to break into the network. However, there is no cause for concern, provided that you secure your system or network against port scanning by adopting the following countermeasures:
- Configure firewall and IDS rules to detect and block probes.
- The firewall should be capable of detecting probes sent by the attackers using port scanning tools. It should not allow traffic to pass through it after simply inspecting the TCP header. The firewall should be able to examine the data contained in each packet before allowing the traffic to pass through it.
- Run the port scanning tools against hosts on the network to determine whether the firewall accurately detects the port scanning activity.
- Some firewalls do a better job than others in terms of detecting stealth scans. For example, many firewalls have specific options to detect SYN scans, while others completely ignore FIN scans.
- Ensure that the router, IDS, and firewall firmware are updated with their latest releases/versions.
- Configure commercial firewalls to protect your network against fast port scans and SYN floods. You can run tools such as port entry to detect and stop port scan attempts on Linux/UNIX systems.
- Hackers use tools such as Nmap and perform OS detection to sniff the details of a remote OS. Thus, it is important to employ intrusion detection systems in such cases. Snort (https://www.snort.org) is an intrusion detection and prevention technology that is very useful, mainly because signatures are frequently available from the public authors.
- Keep as few ports open as possible and filter the rest, as the intruder will try to enter through any open port. Use a custom rule set to lock down the network, block unwanted ports at the firewall, and filter the following ports: 135–159, 256–258, 389, 445, 1080, 1745, and 3268.
- Block unwanted services running on the ports and update the service versions.
- Ensure that the versions of services running on the ports are non-vulnerable.
- Block inbound ICMP message types and all outbound ICMP type-3 unreachable messages at border routers arranged in front of a company’s main firewall.
- Attackers try to perform source routing and send packets to the targets (which may not be reachable via the Internet) using an intermediate host that can interact with the target. Hence, it is necessary to ensure that your firewall and router can block such source-routing techniques.
- Ensure that the mechanism used for routing and filtering at the routers and firewalls, respectively, cannot be bypassed using a particular source port or source-routing methods.
- Test your IP address space using TCP and UDP port scans as well as ICMP probes to determine the network configuration and accessible ports.
- Ensure that the anti-scanning and anti-spoofing rules are configured.
- If a commercial firewall is in use, then ensure that: it is patched with the latest updates; it has correctly defined anti-spoofing rules; and its fast-mode services are unusable in Check Point Firewall-1 environments.
5. OS Discovery
5.1. OS Discovery/Banner Grabbing
Banner grabbing, or “OS fingerprinting,” is a method used to determine the OS that is running on a remote target system. It is an important scanning method, as the attacker will have a higher probability of success if the OS of the target system is known (many vulnerabilities are OS-specific). The attacker can then formulate an attack strategy based on the OS of the target system. There are two methods for banner grabbing: spotting the banner while trying to connect to a service, such as an FTP site, and downloading the binary file/bin/ls to check the system architecture. A more advanced fingerprinting technique depends on stack querying, which transfers the packets to the network host and evaluates them by the reply. The first stack-querying method designed with regard to the TCP mode of communication evaluates the response to connection requests. The next method, known as initial sequence number (ISN) analysis, identifies the differences in random number generators found in the TCP stack. ICMP response analysis is another method used to fingerprint an OS. It consists of sending ICMP messages to a remote host and evaluating the reply. Two types of banner grabbing techniques are described below:
a. Active Banner Grabbing
Active banner grabbing applies the principle that an OS’s IP stack has a unique way of responding to specially crafted TCP packets. This happens because of different interpretations that vendors apply while implementing the TCP/IP stack on a particular OS. In active banner grabbing, the attacker sends a variety of malformed(畸形的) packets to the remote host, and the responses are compared with a database. Responses from different OS vary because of differences in TCP/IP stack implementation. For instance, the scanning utility Nmap uses a series of nine tests to determine an OS fingerprint or banner grabbing. The tests listed below provide some insights into an active banner grabbing attack, as described at www.packetwatch.net:
- Test 1
A TCP packet with the SYN and ECN-Echo flags enabled is sent to an open TCP port. - Test 2
A TCP packet with no flags enabled is sent to an open TCP port. This type of packet is a NULL packet. - Test 3
A TCP packet with the URG, PSH, SYN, and FIN flags enabled is sent to an open TCP port. - Test 4
A TCP packet with the ACK flag enabled is sent to an open TCP port. - Test 5
A TCP packet with the SYN flag enabled is sent to a closed TCP port. - Test 6
A TCP packet with the ACK flag enabled is sent to a closed TCP port. - Test 7
A TCP packet with the URG, PSH, and FIN flags enabled is sent to a closed TCP port. - Test 8 PU (Port Unreachable)
A UDP packet is sent to a closed UDP port. The objective is to extract an “ICMP port unreachable” message from the target machine. - Test 9 TSeq (TCP Sequence ability test)
This test tries to determine the sequence generation patterns of the TCP initial sequence numbers (also known as TCP ISN sampling), the IP identification numbers (also known as IPID sampling), and the TCP timestamp numbers. It sends six TCP packets with the SYN flag enabled to an open TCP port.
The objective of these tests is to find patterns in the initial sequence of numbers that the TCP implementations chose while responding to a connection request. They can be categorized into groups, such as traditional 64K (many old UNIX boxes), random increments (newer versions of Solaris, IRIX, FreeBSD, Digital UNIX, Cray, and many others), or true random (Linux 2.0.*, OpenVMS, newer AIX, etc.). Windows boxes use a “time-dependent” model in which the ISN is incremented by a fixed amount for each occurrence.
b. Passive Banner Grabbing
Like active banner grabbing, passive banner grabbing also depends on the differential implementation of the stack and the various ways in which an OS responds to packets. However, instead of relying on scanning the target host, passive fingerprinting captures packets from the target host via sniffing to study telltale signs(警告讯号) that can reveal an OS. Passive banner grabbing includes:
- Banner grabbing from error messages
Error messages provide information, such as type of server, type of OS, and SSL tools used by the target remote system. - Sniffing the network traffic
Capturing and analysing packets from the target enables an attacker to determine the OS used by the remote system. - Banner grabbing from page extensions
Looking for an extension in the URL may help in determining the application version. For example, .aspx => IIS server and Windows platform.
The four areas that typically determine the OS are given below:
- TTL (time to live) of the packets
- Window Size
- Whether the DF (Don’t Fragment) bit is set
- TOS (Type of Service)
Passive fingerprinting is neither fully accurate nor limited to these four signatures. However, one can improve its accuracy by looking at several signatures and combining the information. The following is an analysis of a sniffed packet described by Lance Spitzner in his paper on passive fingerprinting(https://www.symantec.com/connect/articles/passive-fingerprinting):
04/20-21:41:48.129662 129.142.224.3:659 -> 172.16.1.107:604
TCP TTL:45 TOS:0x0 ID:56257
FA Seq: 0x9DD90553
Ack: 0xE3C65D7 Win: 0x7D78
According to the four criteria, the following are identified:
- TTL: 45
- Windows Size: 0x7D78 (or 32120 in decimal)
- DF: The DF bit is set
- TOS: 0x0
Compare this information with a database of signatures.
- TTL
The TLL from the analysis is 45. The original packet went through 19 hops to get to the target, so it sets the original TTL to 64. Based on this TTL, it appears that the user sent the packet from a Linux or FreeBSD box (however, more system signatures need to be added to the database). This TTL confirms it by implementing a traceroute to the remote host. If the trace needs to be performed stealthily, the traceroute TTL (default 30 hops) can be set to one or two hops fewer than the remote host (-m option). Setting the traceroute in this manner reveals the path information (including the upstream provider) without actually contacting the remote host. - Windows Size
In this step, the window sizes are compared. The window size is another effective tool for determining precisely what window size is used and how often it is changed. In the previous signature, the window size is set at 0x7D78, which is the default window size used by Linux. In addition, FreeBSD and Solaris tend to maintain the same window size throughout a session. However, Cisco routers and Microsoft Windows NT window sizes constantly change. The window size is more accurate when measured after the initial three-way handshake (due to TCP slow start). - DF
Most systems use the DF bit set; hence, this is of limited value. However, this makes it easier to identify a few systems that do not use the DF flag (such as SCO or OpenBSD). - TOS
TOS is also of limited value, as it seems to be more session-based than OS-based. In other words, it is not so much the OS as the protocol used that determines the TOS to a large extent.
Using the information obtained from the packet, specifically the TTL and the window size, one can compare the results with the database of signatures and determine the OS with some degree of confidence (in this case, Linux kernel 2.2.x). Passive fingerprinting, like active fingerprinting, has some limitations. First, applications that build their own packets (e.g., Nmap, Hunt, Nemesis, etc.) will not use the same signatures as the OS. Second, it is relatively simple for a remote host to adjust the TTL, window size, DF, or TOS setting on the packets. Passive fingerprinting has several other uses. For example, attackers can use stealthy fingerprinting to determine the OS of a potential target such as a web server. A user only needs to request a web page from the server and then analyse the sniffer traces. This bypasses the need for using an active tool that various IDS systems can detect. Passive fingerprinting also helps in identifying remote proxy firewalls. It may be possible to ID proxy firewalls from the signatures as discussed above, simply because proxy firewalls rebuild connections for clients. Similarly, passive fingerprinting can be used to identify rogue(异常的) systems. Note: We will discuss passive banner grabbing in later modules.
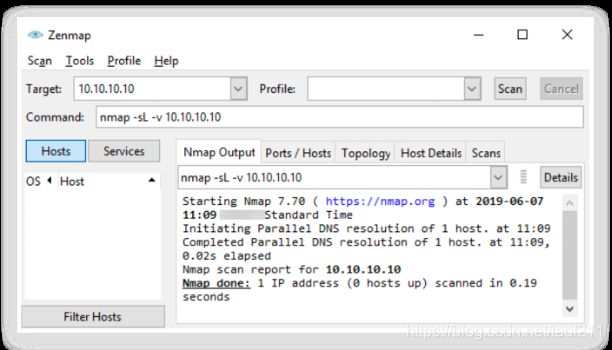
5.2. How to Identify Target System OS
Identifying the target OS is one of the important tasks for an attacker to compromise the target network/machine. In a network, various standards are implemented to allow different OSs to communicate with each other. These standards govern the functioning of various protocols such as IP, TCP, UDP, etc. By analysing certain parameters/fields in these protocols, one can reveal the details of the OS. Parameters such as Time to Live (TTL) and TCP window size in the IP header of the first packet in a TCP session help identify the OS running on the target machine. The TTL field determines the maximum time that a packet can remain in a network, and the TCP window size determines the length of the packet reported. These values vary among OSs, as described in the following table:
Attackers can use various tools to perform OS discovery on the target machine, including Wireshark, Nmap, Unicornscan, and Nmap Script Engine. Attackers can also adopt the IPv6 fingerprinting method to grab the target OS details.
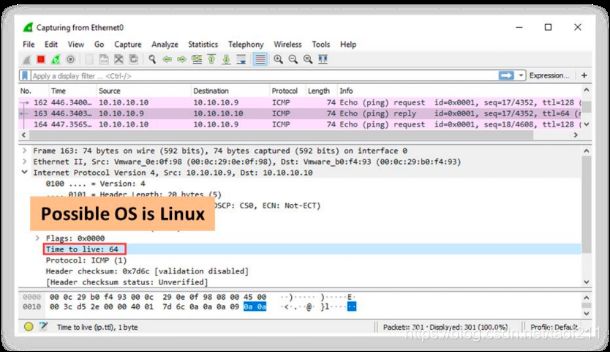
a. OS Discovery using Wireshark
To identify the target OS, sniff/capture the response generated from the target machine to the request-originated machine using packet-sniffing tools such as Wireshark, etc., and observe the TTL and TCP window size fields in the first captured TCP packet. By comparing these values with those in the above table, you can determine the target OS that has generated the response.

b. OS Discovery using Nmap
To exploit the target, it is highly essential to identify the OS running on the target machine. Attackers can employ various tools to acquire the OS details of the target. Nmap is one of the effective tools for performing OS discovery activities. In Zenmap, the -O option is used to perform OS discovery, which displays the OS details of the target machine.

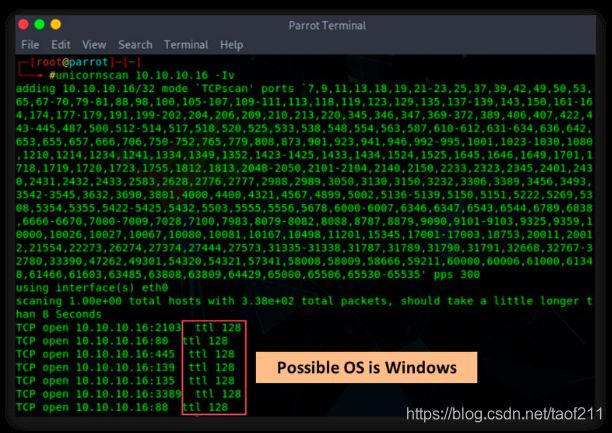
c. OS Discovery using Unicornscan
In Unicornscan, the OS of the target machine can be identified by observing the TTL values in the acquired scan result. To perform Unicornscan, the syntax #unicornscan is used. As shown in the screenshot, the TTL value acquired after the scan is 128; hence, the OS is possibly Microsoft Windows (Windows 7/8/8.1/10 or Windows Server 2008/12/16).
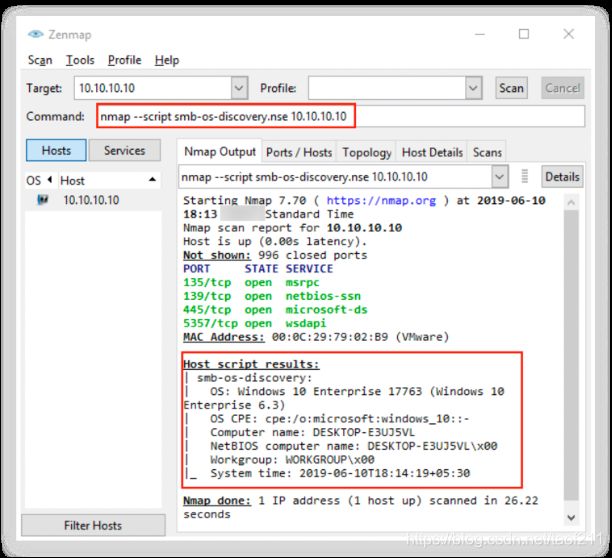
d.[OS Discovery using Nmap Script Engine
Nmap Scripting Engine (NSE) in Nmap can be used to automate a wide variety of networking tasks by allowing users to write and share scripts. These scripts can be executed parallelly with the same efficiency and speed as Nmap. Attackers can also use various scripts in the Nmap Script Engine for performing OS discovery on the target machine. For example, in Nmap, smb-os-discovery is an inbuilt script used for collecting OS information on the target machine through the SMB protocol. In Zenmap, NSE can be generally activated using the -sC option. If the custom scripts are to be specified, then attackers can use the --script option. The NSE results will be displayed with both the Nmap normal and XML outputs.
e. OS Discovery using IPv6 Fingerprinting
IPv6 Fingerprinting is another technique used to identify the OS running on the target machine. It has the same functionality as IPv4, such as sending probes, waiting and collecting the responses, and matching them with the database of fingerprints. The difference between IPv6 and IPv4 fingerprinting is that IPv6 uses several additional advanced IPv6-specific probes along with a separate IPv6-specifc OS detection engine. Nmap sends nearly 18 probes in the following order to identify the target OS using the IPv6 fingerprinting method.
- Sequence generation (S1–S6)
- ICMPv6 echo (IE1)
- ICMPv6 echo (IE2)
- Node Information Query (NI)
- Neighbour Solicitation (NS)
- UDP (U1)
- TCP explicit congestion notification (TECN)
- TCP (T2–T7)
In Zenmap, the -6 option along with -O option is used to perform OS discovery using the IPv6 fingerprinting method. Syntax: # nmap -6 -O
5.3. Banner Grabbing Countermeasures
a. Disabling or Changing Banner
Whenever a port is open, it implies that a service/banner is running on it. When attackers connect to the open port using banner grabbing techniques, the system presents a banner containing sensitive information such as OS, server type, and version. Using the information gathered, the attacker identifies specific vulnerabilities to exploit and then launches attacks. The countermeasures against banner grabbing attacks are as follows:
- Display false banners to mislead or deceive(欺骗) attackers.
- Turn off unnecessary services on the network host to limit information disclosure.
- Use ServerMask (https://www.port80software.com) tools to disable or change banner information.
- ServerMask removes unnecessary HTTP header and response data and camouflages(伪装) the server by providing false signatures. It also provides you with the option of eliminating(消除) file extensions such as .asp or .aspx, and it clearly indicates that a site is running on a Microsoft server.
- Apache 2.x with mod_headers module: use a directive(指令) in the httpd.conf file to change the banner information header and set the server as "New Server Name”.
- Alternatively, change the ServerSignature line to ServerSignatureOff in the httpd.conf file.
- The details of the vendor and version in the banners should be disabled.
b. Hiding File Extensions from Web Pages
File extensions reveal information about the underlying server technology that an attacker can use to launch attacks. The countermeasures against such banner grabbing attacks are as follows:
- Hide file extensions to mask the web technology.
- Replace application mappings such as .asp with .htm or .foo, etc., to disguise the identity of the servers.
- Apache users can use mod_negotiation directives.
- IIS users can use tools such as PageXchanger to manage the file extensions.
Note: It would be better if the file extensions are not used at all.
6. Scanning Beyond IDS & Firewall
6.1. IDS/Firewall Evasion(回避) Techniques
Although firewalls and IDS can prevent malicious traffic (packets) from entering a network, attackers can send intended packets to the target that evade the IDS/firewall by implementing the following techniques:
- Packet Fragmentation
The attacker sends fragmented probe packets to the intended target, which reassembles(重组) the fragments after receiving all of them. - Source Routing
The attacker specifies the routing path for the malformed packet to reach the intended target. - Source Port Manipulation
The attacker manipulates the actual source port with the common source port to evade the IDS/firewall. - IP Address Decoy(诱饵)
The attacker generates or manually specifies IP addresses of decoys so that the IDS/firewall cannot determine the actual IP address. - IP Address Spoofing
The attacker changes the source IP addresses so that the attack appears to be coming from someone else. - Creating Custom Packets
The attacker sends custom packets to scan the intended target beyond the firewalls. - Randomizing Host Order
The attacker scans the number of hosts in the target network in a random order to scan the intended target that lies beyond the firewall. - Sending Bad Checksums(检校和)
The attacker sends packets with bad or bogus TCP/UPD checksums to the intended target. - Proxy Servers
The attacker uses a chain of proxy servers to hide the actual source of a scan and evade certain IDS/firewall restrictions. - Anonymizers(匿名软件)
The attacker uses anonymizers, which allows them to bypass Internet censors and evade certain IDS and firewall rules.
6.2. Packet Fragmentation
Packet fragmentation refers to the splitting of a probe packet into several smaller packets (fragments) while sending it to a network. When these packets reach a host, the IDS and firewalls behind the host generally queue(使排队) all of them and process them one by one. However, since this method of processing involves greater CPU and network resource consumption, the configuration of most IDS causes them to skip fragmented packets during port scans. Therefore, attackers use packet fragmentation tools such as Nmap and fragroute to split the probe packet into smaller packets that circumvent(回避) the port-scanning techniques employed by IDS. Once these fragments reach the destined host, they are reassembled to form a single packet.
SYN/FIN Scanning Using IP Fragments
SYN/FIN scanning using IP fragments is not a new scanning method but a modification of previous techniques. This process of scanning was developed to avoid false positives generated by other scans because of a packet filtering device on the target system. The TCP header splits into several packets to evade the packet filter. For any transmission, every TCP header must have the source and destination port for the initial packet (8-octet, 64-bit). The initialized flags in the next packet allow the remote host to reassemble the packets upon receipt via an Internet protocol module that detects the fragmented data packets using field-equivalent values of the source, destination, protocol, and identification.
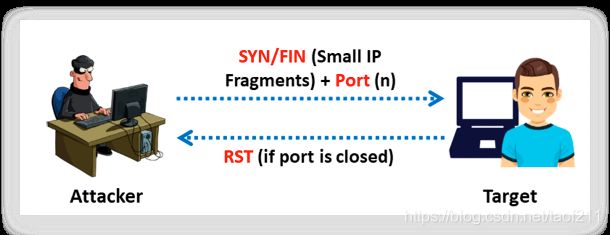
In this scan, the system splits the TCP header into several fragments and transmits them over the network. However, IP reassembly on the server side may result in unpredictable and abnormal results, such as fragmentation of the IP header data. Some hosts may fail to parse(解析) and reassemble the fragmented packets, which may lead to crashes, reboots, or even network device monitoring dumps.
Some firewalls might have rule sets that block IP fragmentation queues in the kernel (e.g., CONFIG_IP_ALWAYS_DEFRAG option in the Linux kernel), although this is not widely implemented because of its adverse(不利的) effects on performance. Since many IDS use signature-based methods to indicate scanning attempts on IP and/or TCP headers, the use of fragmentation will often evade this type of packet filtering and detection, resulting in a high probability of causing problems on the target network. Attackers use the SYN/FIN scanning method with IP fragmentation to evade this type of filtering and detection. The screenshot below shows the SYN/FIN scan using the Nmap tool.

6.3. Source Routing
An IP datagram contains various fields, including the IP options field, which stores source routing information and includes a list of IP addresses through which the packet travels to its destination. As the packet travels through the nodes in the network, each router examines the destination IP address and chooses the next hop to direct the packet to the destination. When attackers send malformed packets to a target, these packets hop through various routers and gateways to reach the destination. In some cases, the routers in the path might include configured firewalls and IDS that block such packets. To avoid them, attackers enforce a loose(松散的) or strict source routing mechanism, in which they manipulate the IP address path in the IP options field so that the packet takes the attacker-defined path (without firewall-/IDS-configured routers) to reach the destination, thereby evading firewalls and IDS. The figure below shows source routing, where the originator dictates the eventual route of the traffic.
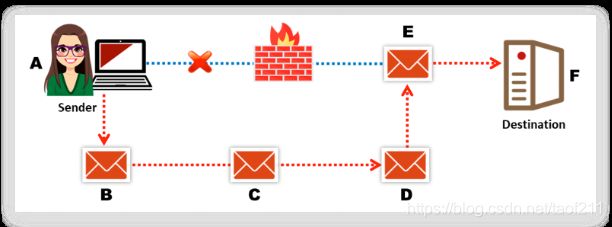
6.4. Source Port Manipulation
Source port manipulation is a technique used for bypassing the IDS/firewall, where the actual port numbers are manipulated with common port numbers for evading certain IDS and firewall rules. The main security misconfigurations occur because of blindly trusting the source port number. The administrator mostly configures the firewall by allowing the incoming traffic from well-known ports such as HTTP, DNS, FTP, etc. The firewall can simply allow the incoming traffic from the packets sent by the attackers using such common ports.

Although the firewalls can be made secure using application-level proxies or protocol-parsing firewall elements, this technique helps the attacker to bypass the firewall rules easily. The attacker tries to manipulate the original port number with the common port numbers, which can easily bypass the IDS/firewall. In Zenmap, the -g or --source-port option is used to perform source port manipulation.

6.5. IP Address Decoy
The IP address decoy technique refers to generating or manually specifying IP addresses of the decoys to evade IDS/firewalls. It appears to the target that the decoys as well as the host(s) are scanning the network. This technique makes it difficult for the IDS/firewall to determine which IP address is actually scanning the network and which IP addresses are decoys. The Nmap scanning tool comes with a built-in scan function called a decoy scan, which cloaks(遮掩) a scan with decoys. This technique generates multiple IP addresses to perform a scan, thus making it difficult for the target security mechanisms such as IDS, firewalls, etc., to identify the original source from the registered logs. The target IDS might report scanning from 5–0 IP addresses; however, it cannot differentiate between the actual scanning IP address and the innocuous(无害的) decoy IPs. You can perform two types of decoy scans using Nmap:
a. nmap -D RND:10 [target]
Using this command, Nmap automatically generates a random number of decoys for the scan and randomly positions the real IP address between the decoy IPs. Ex. Assume that 10.10.10.10 is the target IP address to be scanned. Thus, the Nmap decoy scan command will be: # nmap -D RND:10 10.10.10.10.
b. nmap -D decoy1,decoy2,decoy3,…,ME,… [target]
Using this command, you can manually specify the IP addresses of the decoys to scan the victim’s network. Here, you have to separate each decoy IP with a comma (,) and you can optionally use the ME command to position your real IP in the decoy list. If you place ME in the 4th position of the command, your real IP will be positioned at the 4th position accordingly. This is an optional command, and if you do not mention ME in your scan command, then Nmap will automatically place your real IP in any random position. For example, assume that 10.10.10.16 is the real source IP and 10.10.10.10 is the target IP address to be scanned. Then, the Nmap decoy command will be: Syntax:# nmap -D 192.168.0.1,172.120.2.8,192.168.2.8,10.10.10.16,10.10.10.5 10.10.10.10.

These decoys can be generated in both initial ping scans such as ICMP, SYN, ACK, etc., and during the actual port scanning phase. IP address decoy is a useful technique for hiding your IP address. However, it will not be successful if the target employs active mechanisms such as router path tracing, response dropping, etc. Moreover, using many decoys can slow down the scanning process and affect the accuracy of the scan.
6.6. IP Address Spoofing
Most firewalls filter packets based on the source IP address. These firewalls examine the source IP address and determine whether the packet is coming from a legitimate source or an illegitimate source. The IDS filters packets from illegitimate sources. Attackers use IP spoofing technique to bypass such IDS/firewalls. IP address spoofing is a hijacking(劫持) technique in which an attacker obtains a computer’s IP address, alters the packet headers, and sends request packets to a target machine, pretending to be a legitimate host. The packets appear to be sent from a legitimate machine but are actually sent from the attacker’s machine, while his/her machine’s IP address is concealed(隐藏的). When the victim replies to the address, it goes back to the spoofed address and not to the attacker’s real address. Attackers mostly use IP address spoofing to perform DoS attacks. When the attacker sends a connection request to the target host, the target host replies to the spoofed IP address. When spoofing a nonexistent address, the target replies to a nonexistent system and then hangs until the session times out, thus consuming a significant amount of its own resources.
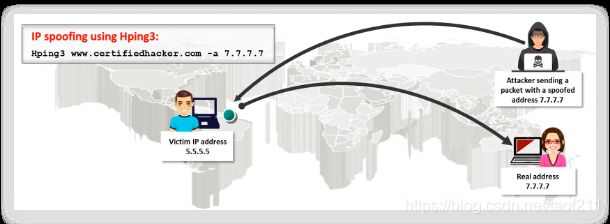
IP spoofing using Hping3: Hping3 www.certifiedhacker.com -a 7.7.7.7. You can use Hping3 to perform IP spoofing. The above command helps you to send arbitrary TCP/IP packets to network hosts. Note: You will not be able to complete the three-way handshake and open a successful TCP connection with spoofed IP addresses.
IP Spoofing Detection Techniques: Direct TTL Probes
In this technique, you initially send a packet (ping request) to the legitimate host and wait for a reply. Check whether the TTL value in the reply matches with that of the packet you are checking. Both will have the same TTL if they are using the same protocol. Although the initial TTL values vary according to the protocol used, a few initial TTL values are commonly used. For TCP/UDP, the values are 64 and 128; for ICMP, they are 128 and 255.
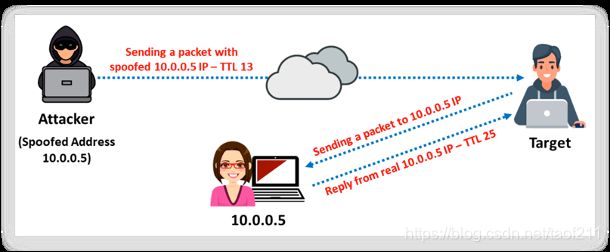
If the reply is from a different protocol, then you should check the actual hop count to detect the spoofed packets. Deduct the TTL value in the reply from the initial TTL value to determine the hop count. The packet is a spoofed packet if the reply TTL does not match the TTL of the packet. It will be very easy to launch an attack if the attacker knows the hop count between the source and the host. In this case, the test result is a false negative. This technique is successful when the attacker is in a different subnet from that of the victim. Note: Normal traffic from one host can contrast TTLs depending on traffic patterns.
IP Spoofing Detection Techniques: IP Identification Number
Users can identify spoofed packets by monitoring the IP identification (IPID) number in the IP packet headers. The IPID increases incrementally each time a system sends a packet. Every IP packet on the network has a “fragment identification” number, which is increased by one for every packet transmission. To identify whether a packet is spoofed, send a probe packet to the source IP address of the packet and observe the IPID number in the reply. The IPID value in the response packet must be close to but slightly greater than the IPID value of the probe packet. The source address of the IP packet is spoofed if the IPID of the response packet is not close to that of the probe packet. This method is effective even when both the attacker and the target are on the same subnet.

IP Spoofing Detection Techniques: TCP Flow Control Method
The TCP can optimize the flow control on both the sender’s and the receiver’s end with its algorithm. The algorithm accomplishes flow control using the sliding window principle. The user can control the flow of IP packets by the window size field in the TCP header. This field represents the maximum amount of data that the recipient can receive and the maximum amount of data that the sender can transmit without acknowledgement. Thus, this field helps to control data flow. The sender should stop sending data whenever the window size is set to zero. In general flow control, the sender should stop sending data once the initial window size is exhausted. The attacker, who is unaware of the ACK packet containing window size information, might continue to send data to the victim. If the victim receives data packets beyond the window size, they are spoofed packets. For effective flow control and early detection of spoofing, the initial window size must be very small. Most spoofing attacks occur during the handshake, as it is challenging to build multiple spoofing replies with the correct sequence number. Therefore, apply the flow control spoofed packet detection method to the handshake. In a TCP handshake, the host sending the initial SYN packet waits for SYN-ACK before sending the ACK packet. To check whether you are getting the SYN request from a genuine client or a spoofed one, set SYN-ACK to zero. If the sender sends an ACK with any data, it means that the sender is a spoofed one. This is because when SYN-ACK is set to zero, the sender must respond to it only with the ACK packet, without additional data.

Attackers sending spoofed TCP packets will not receive the target’s SYN-ACK packets. Attackers cannot respond to changes in the congestion window size. When the received traffic continues after a window size is exhausted, the packets are most likely spoofed.
IP Spoofing Countermeasures
In ethical hacking, the ethical hacker, also known as the “pen tester,” has to perform an additional task that a normal hacker does not follow (i.e., adopting countermeasures against the respective vulnerabilities determined through hacking). This is essential because knowing security loopholes in your network is worthless unless you adopt measures to protect them against real hackers. As mentioned previously, IP spoofing is one of the techniques that a hacker adopts to break into the target network. Therefore, to protect your network from external hackers, you should apply IP spoofing countermeasures to your network security settings. Some IP spoofing countermeasures that you can apply are as follows:
a. Avoid Trust Relationships
Do not rely on IP-based authentication. Attackers may spoof themselves as trusted hosts and send malicious packets to you. If you accept these packets under the assumption that they are “clean” because they are from your trusted host, the malicious code will infect your system. Therefore, it is advisable to test all packets, even when they come from one of your trusted hosts. You can avoid this problem by implementing password authentication along with trust-relationship-based authentication.
b. Use Firewalls & Filtering Mechanisms
As stated above, you should filter all the incoming and outgoing packets to avoid attacks and sensitive information loss. A firewall can restrict malicious packets from entering your private network and prevent severe(严重的) data loss. You can use access control lists (ACLs) to block unauthorized access. At the same time, there is a possibility of an insider attack. Inside attackers can send sensitive information about your business to your competitors, which could lead to monetary loss and other issues. Another risk of outgoing packets is that an attacker will succeed in installing a malicious sniffing program running in a hidden mode on your network. These programs gather and send all your network information to the attacker without any notification after filtering the outgoing packets. Therefore, you should assign the same importance to the scanning of outgoing packets as you would to that of incoming packets.
c. Use Random Initial Sequence Numbers
Most devices choose their ISN based on timed counters. This makes the ISNs predictable, as it is easy for an attacker to determine the concept of generating the ISN. The attacker can determine the ISN of the next TCP connection by analysing the ISN of the current session or connection. If the attacker can predict the ISN, then he/she can establish a malicious connection to the server and sniff out your network traffic. To avoid this risk, use random initial sequence numbers.
d. Ingress(进入) Filtering
Ingress filtering prevents spoofed traffic from entering the Internet. It is applied to routers because it enhances the functionality of the routers and blocks spoofed traffic. Configuring and using ACLs that drop packets with the source address outside the defined range is one method of implementing ingress filtering.
e. Egress(外出) Filtering
Egress filtering refers to a practice that aims to prevent IP spoofing by blocking outgoing packets with a source address that is not inside.
f. Use Encryption
If you want to attain maximum network security, then use strong encryption for all the traffic placed onto the transmission media without considering its type and location. This is the best way to prevent IP spoofing attacks. IPsec can be used to reduce the IP spoofing risk drastically, as it provides data authentication, integrity, and confidentiality. Furthermore, ACLs can be used for blocking private IP addresses at the downstream interfaces. Encryption sessions should be enabled on the router so that trusted hosts can communicate securely with local hosts. Attackers tend to focus on easy-to-compromise targets. If an attacker wants to break into the encrypted network, he or she has to decrypt a whole slew of(大量) encrypted packets, which is a difficult task. Therefore, the attacker is likely to move on and try to find another target that is easy to compromise or simply abort(使终止) the attempt. Moreover, use the latest encryption algorithms that provide strong security.
g. SYN Flooding Countermeasures
Countermeasures against SYN flooding attacks can also help you to avoid IP spoofing attacks.
6.7. Creating Custom Packets
The attacker creates and sends custom packets to scan the intended target beyond the IDS/firewalls. Various techniques are used to create custom packets. Some of them are mentioned below:
a. Using Packet Crafting Tools
Attackers create custom TCP packets to scan the target by bypassing the firewalls. Attackers use various packet crafting tools such as Colasoft packet builder, NetScanTools Pro , etc., to scan the target that is beyond the firewall. Packet crafting tools craft and send packet streams (custom packets) using different protocols at different transfer rates. Colasoft Packet Builder is a tool that allows an attacker to create custom network packets and helps security professionals assess the network. The attacker can select a TCP packet from the provided templates and change the parameters in the decoder, hexadecimal, or ASCII editor to create a packet. In addition to building packets, Colasoft Packet Builder supports saving packets to packet files and sending packets to the network.

There are three views in the Packet Builder:
- Packet List
Packet List displays all the constructed packets. When you select one or more packets in Packet List, the first highlighted packet is displayed in both Decode Editor and Hex Editor for editing. - Decode Editor
Decode Editor allows the attacker to edit packets without remembering the value length, byte order, and offsets. You can select a field and change the value in the edit box. - Hex Editor
In Hex Editor, the data of the packet are represented as hexadecimal values and ASCII characters; nonprintable characters are represented by a dot (".") in the ASCII section. You can edit either the hexadecimal values or the ASCII characters.
For creating a packet, you can use the add or insert packet command in the Edit menu or the Toolbar to create a new packet. The attacker can send a constructed packet to wire directly and control how Colasoft Packet Builder sends the packets, specifying, for example, the interval(间隔) between packets, loop times, and delay between loops. This packet builder audits networks and checks the network protection against attacks and intruders. Attackers may use this packet builder to create fragmented packets to bypass network firewalls and IDS systems. They can also create packets and flood the victim with a very large number of packets, which could result in DoS attacks.
b. Appending Custom Binary Data
Attackers send binary data (0’s and 1’s) as payloads in the packets sent to the target machine present behind the firewall. The option used by Nmap for appending custom binary data to the sent packets is --data . Any is specified in the formats 0xAABBCCDDEEFF<…>, AABBCCDDEEFF<…>, or \xAA\xBB\xCC\xDD\xEE\xFF<…>. To perform a byte-order conversion, the specified information should be based on the receiver’s expectations. Attackers can use this technique to scan the target by manipulating the firewalls by appending custom binary or hex data to the sent packets. Example: --data 0xdeadbeef (or) --data \xCA\xFE\x09

c. Appending Custom String
Attackers send regular strings as payloads in the packets sent to the target machine for scanning beyond the firewall. The option used by Nmap for appending a custom string to the sent packets is --data-string . The can contain any string and a few characters depend on the system’s location; however, it is not guaranteed whether the same information is retrieved. The string is enclosed with double quotes (“”) and special characters from the shell are not used. Attackers can use this technique to scan the target by manipulating the firewalls by appending custom string data to the sent packets. Example: --data-string "Scan conducted by Security Ops, extension 7192" (or) --data-string "Ph34r my l33t skills".
d. Appending Random Data
Attackers append a number of random data bytes to most packets sent without using any protocol-specific payloads. The option used by Nmap for appending random data to the sent packets is --data-length . For protocol-specific and no random payloads, --data-length 0 is used. The (-O) OS detection packets are not usually affected, as probe consistency is needed for it to be accurate. By default, a few UDP ports and IP protocols get a custom payload. Attackers can use this technique to scan the target by manipulating the firewalls by appending random data or numbers to the sent packets. Example: --data-string 1 (or) --data-string 5.

6.8. Randomizing Host Order & Sending Bad Checksums
a. Randomizing Host Order
The attacker scans the number of hosts in the target network in a random order to scan the intended target that is lying beyond the firewall. The option used by Nmap to scan with a random host order is --randomize-hosts. This technique instructs Nmap to shuffle(洗牌) each group of 16384 hosts before scanning with slow timing options, thus making the scan less notable to network monitoring systems and firewalls. If larger group sizes are randomized, the PING_GROUP_SZ should be increased in nmap.h and it should be compiled again. Another method can be followed by generating the target IP list with the list scan command -sL -n -oN and then randomizing it with a Perl script and providing the whole list to Nmap using the -iL command.
b. Sending Bad Checksums
The attacker sends packets with bad or bogus TCP/UPD checksums to the intended target to avoid certain firewall rule sets. TCP/UPD checksums are used to ensure data integrity. Sending packets with incorrect checksums can help attackers to acquire information from improperly configured systems by checking for any response. If there is a response, then it is from the IDS or firewall, which did not verify the obtained checksum. If there is no response or the packets are dropped, then it can be inferred(推断) that the system is configured. This technique instructs Nmap to send packets with invalid TCP, UDP, or SCTP checksums to the target host. The option used by Nmap is --badsum.
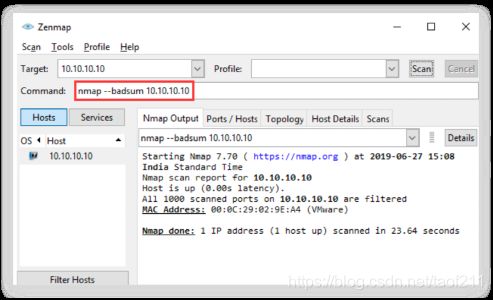
7. Draw Network Diagram
Drawing a network diagram helps an attacker to identify the topology or architecture of a target network. The network diagram also helps to trace the path to the target host in the network and enables the attacker to understand the positions of firewalls, IDS, routers, and other access control devices. Once the attacker has this information, he/she can try to find the vulnerabilities or weak points in these security mechanisms. Then, the attacker can exploit these weaknesses to find his/her way into the victim’s network. The network diagram also helps network administrators to manage their networks. Attackers use network discovery or mapping tools to draw network diagrams of target networks. An example of a network diagram is shown below.

7.1. Network Discovery and Mapping Tools
Network discovery and mapping tools allow you to view the map of your network. They help you to detect rogue hardware and software violations and notify you whenever a particular host becomes active or goes down. Thus, you can also determine server outages or problems related to performance. An attacker can use the same tools to draw a diagram of the target network, analyse the topology, find the vulnerabilities or weak points, and launch an attack by exploiting these weak points.
Network Topology Mapper
The Network Topology Mapper tool allows one to automatically discover and create a network map of the target network. It can also display in-depth connections such as OSI Layer 2 and Layer 3 topology data (e.g., switch-to-switch, switch-to-node, and switch-to-router connections). It can keep track of network changes and allow the user to perform inventory management of hardware and software assets. The features of the software include:
- Network Topology Discovery and Mapping
Automatically discovers the entire network and creates comprehensive and detailed network maps - Export Network Diagrams to Visio
Exports network diagrams to Microsoft Office® Visio®, Orion Network Atlas, PDF, and PNG formats - Network Mapping for Regulatory Compliance
Allows one to directly address PCI (Peripheral Component Interconnect) compliance and other regulations that require maintenance of an up-to-date network diagram - Multi-level Network Discovery
Performs multi-level network discovery to produce an integrated OSI Layer 2 and Layer 3 network map that includes detailed device information - Auto-detection of Changes to Network Topology
Automatically detects new devices and changes to a network topology with scheduled network scanning
Some network discovery and mapping tools that an attacker can use to create a network map are listed below: - OpManager
- The Dude
- NetSurveyor
- NetBrain
- Spiceworks Network Mapping Tool
7.2. Network Discovery Tools for Mobile
a. Scany
Scany, a network scanner app for iPhone and iPad, scans LAN, Wi-Fi networks, websites, and open ports, discovers network devices, and digs network info. It supports several networking protocols and anti-stealth technologies. It is a multifunctional networking instrument for finding connected devices, looking up detailed device information, network troubleshooting, scanning ports, and testing network security and firewalls. Attackers use this tool to scan both the LAN and the Internet, scan any IP address or network range, perform hostname, device name, MAC address, and hardware vendor lookups, ping/trace hosts with integrated tools and WHOIS hostnames, IP addresses, ASNs, etc.
b. Network Analyzer
Network Analyzer can diagnose(诊断) various problems in the Wi-Fi network setup or Internet connectivity, and it can also detect various issues in remote servers based on its wide range of in-built tools. Attackers can use it to perform ping, traceroute, port scanning, Whois, and DNS lookup activities.
c. PortDroid Network Analysis
Attackers can use PortDroid Network Analysis to perform local network discovery. It is also effective in analysing the network and performing port scanning as well as banner grabbing using certain protocols, including ssh, telnet, http, https, ftp, smb, etc.

应平台相关要求,6.9 Proxy Server和6.1 Anonymizers部分内容被删除