理论+实操:防火墙双机热备
文章目录
- 一:双机热备的工作原理
-
- 1.1 双机热备概述
- 1.2 VRRP(虚拟路由冗余协议Virtual Router Redundancy Protocol)
- 1.3 VGMP
- 二:双机热备配置
-
- 2.1 双击热备的备份方式
- 2.2 开启双机热备功能
- 2.3 配置自动备份模式
- 2.4 配置手工批量备份模式
- 2.5 配置快速备份模式
- 2.6 连接路由器时的双机热备
- 三:实操配置
-
- 3.1 环境
- 3.2 需求
- 3.3 思路步骤
- 3.4 拓扑图
- 3.5 配置命令
一:双机热备的工作原理
1.1 双机热备概述
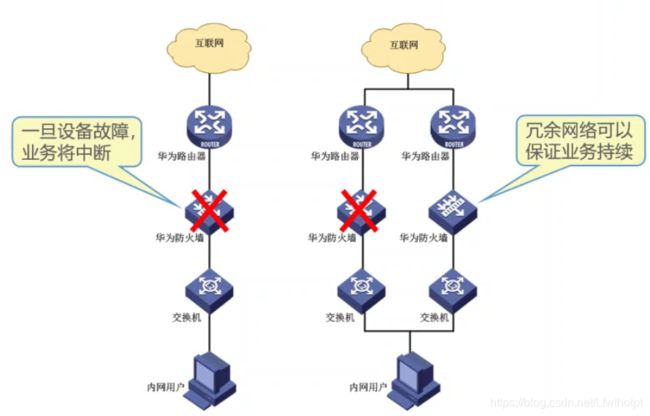
路由器双机热备:
数据从内部网络传输到外部网络,经过双机热备的主路由A(另一个为备路由器B),当A失效后路由网路收敛更新路由表,数据会从备路由B返回
防火墙:
数据从内部网络传输到外部网络,经过双机热备的防火墙A(另一个为备防火墙B),防火墙A生成会话表;当A失效后网路收敛更新路由表,数据会从防火墙B返回,但因为没有会话表,所以数据无法正常返回
————————————解决办法————————————————
- 华为防火墙的做双机热备模式
1.热备模式————一个防火墙为主,一个防火墙为备
2.负载均衡模式——————防火墙之间互为主备
通过另外一个接口互相连接构成心跳线,去备份会话表和server-map表
1.2 VRRP(虚拟路由冗余协议Virtual Router Redundancy Protocol)
- 专业术语
VRRP路由器
虚拟路由器
VRID
虚拟IP/MAC
IP地址拥有者
优先级
抢占模式
非抢占模式
| HSRP | VRRP | |
|---|---|---|
| 协议类型 | 专有协议 | 公有协议 |
| 虚拟IP | 不可以是成员路由器IP | 可以是成员路由器IP |
| 虚拟MAC | 00-00-07-AC-组号 | 00-00-5e-00-01-VRID |
| 状态机 | 五个 | 三个 |
| 报文 | 三种(hello、政变、辞职) | 一种(VRRP通告报文) |
| 特性 | 支持接口跟踪 | 不支持接口跟踪 |
- VRRP的角色
①MASTER路由器
ARP响应
数据包的转发
默认每隔1s向其他路由器通告master路由器当前的状态信息
②backup路由器
不提供数据包的转发
master路由器故障时,接替转发数据包的工作
- VRRP的状态机
Initialize状态————执行接口UP,优先级<255,变成backup状态
Initialize状态————执行接口UP,优先级=255,变成master状态
master状态————执行接口shutdown,变成initialize状态
master状态(此时优先级小于255)————接收到优先级更大的VRRP报文,变成initialize状态
backup状态————执行接口shutdown,变成initialize状态
backup状态————master_down_interval计时器超时,变成master状态
问题:VRRP的缺陷是master的内网链路出现问题时,上层路由器并不知道,此时依然会把数据发送给master,但是因为下行接口出现问题,数据无法正常通讯
这就是双机热备需要解决的问题,由此产生VGMP
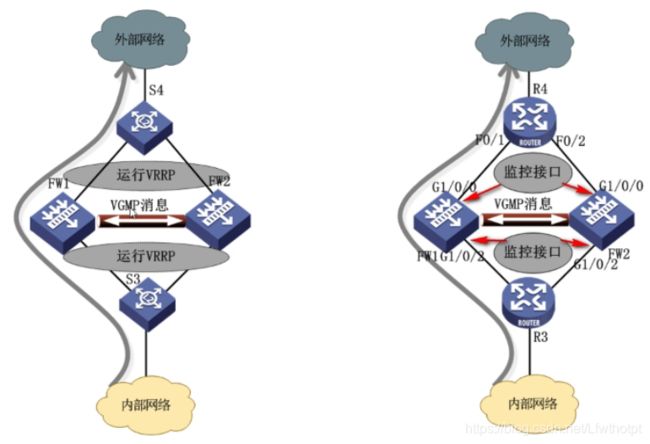
1.3 VGMP
- 概念
VRRP组管理协议
实现对VRRP备份组的统一管理
保证设备在各个备份组中的状态一致性
- 特点——VGMP工作思路
VGMP组的状态决定了VRRP备份组的状态
VGMP组的状态通过比较优先级决定
默认情况下,VGMP组的优先级为45000
通过心跳线协商VGMP状态信息
一旦检测到被分组的状态变成initialize,VGMP组的优先级会自动-2
备注:在加入了VGMP组之后,VRRP中状态标识从master和backup变成了active和standby状态
- VGMP报文封装
组播报文——组播穿二层
二层头-IP头-VRRP报文头-VGMP报文头-DATA
单播报文——单播报文可以穿越三层网络,接口有IP地址
二层头-IP头-UDP报文头-VRRP报文头-VGMP报文头-DATA
- 配置保温封装
hrp interface GigabitEthernet 1/0/0
配置心跳接口g 1/0/0,发送组播报文,但是ensp模拟器不支持该命令
hrp interface GigabitEthernet 1/0/0 remote 1.1.1.1
配置心跳接口g 1/0/0,发送单播报文,reote 表示对端口心跳接口IP,要求路由可达
备注:
华为防火墙在默认情况下放行组播流量,禁止单播流量,所以如果配置了remote参数,还需要配置local区域和心跳接口所在安全区域之间的安全策略
ensp模拟器中,即使心跳接口之间直接相连,也必须配置remote参数,否则无法配置
通常把心跳接口配置在DMZ
二:双机热备配置
2.1 双击热备的备份方式
- 自动备份
- 手动批量备份
- 快速备份
2.2 开启双机热备功能
hrp enable 注意,开启成功提示符会发生变化
2.3 配置自动备份模式
hrp auto-sync
security-policy (+B) +B表示该命令可以同步
rule name test (+B)
source-zone trust (+B)
action permit (+B)
quit
quit
2.4 配置手工批量备份模式
hrp sync 【config | connection-status】
用户模式下执行
2.5 配置快速备份模式
hrp sync 【config | connection-status】
2.6 连接路由器时的双机热备
VRRP通告报文(组播)无法通过路由器
接口直接加入VGMP组
检测到接口变化时,降低优先级
自动切换
Standby的VGMP组增加cost值
三:实操配置
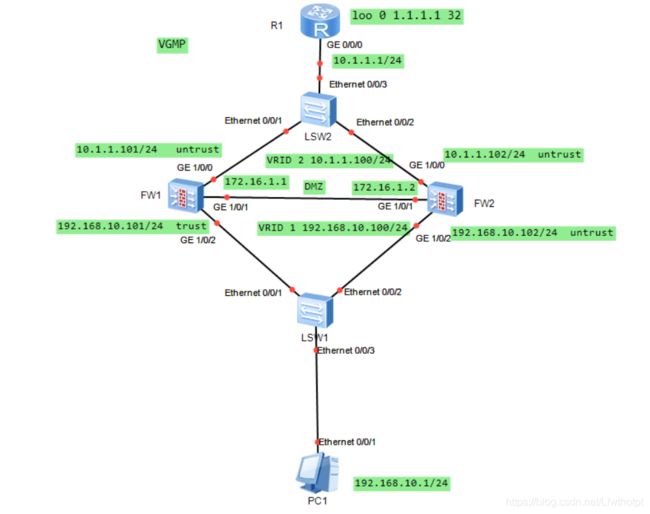
3.1 环境
FW1、FW2、S1、S2、组成双机热备网络
3.2 需求
正常情况下通过FW1转发
FW1故障时,通过FW2转发
3.3 思路步骤
1.基本的网络参数和路由配置
2.接口加入安全区域并配置安全策略
3.配置VRRP备份组
4.配置心跳接口
5.启用双机热备
6.配置备份方式
7.检查配置并验证
- 查看双机热备的状态信息
- 查看心跳接口状态
- PC1访问R1并查看安全规则及会话
- FW1断开G1/0/2,验证故障切换
3.4 拓扑图
3.5 配置命令
配置IP地址
R1
[R1]system-view
[R1]un in en
[R1]int g 0/0/0
[R1-GigabitEthernet0/0/0]ip add 10.1.1.1 24
[R1-GigabitEthernet0/0/0]q
[R1-LoopBack0]int loo 0
[R1-LoopBack0]ip add 1.1.1.1 32
[R1-LoopBack0]q
FW1
Username:admin
Password:Admin@123
The password needs to be changed. Change now? [Y/N]: y
Please enter old password:
Please enter new password:
Please confirm new password:
Info: Your password has been changed. Save the change to survive a reboot.
*************************************************************************
* Copyright (C) 2014-2018 Huawei Technologies Co., Ltd. *
* All rights reserved. *
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
*************************************************************************
system-view
Enter system view, return user view with Ctrl+Z.
[USG6000V1]un in en
Info: Saving log files...
Info: Information center is disabled.
[USG6000V1]sysname FW1
[FW1]int g 1/0/0
[FW1-GigabitEthernet1/0/0]ip add 10.1.1.101 24
[FW1-GigabitEthernet1/0/0]un sh
Info: Interface GigabitEthernet1/0/0 is not shutdown.
[FW1-GigabitEthernet1/0/0]q
[FW1]int g 1/0/1
[FW1-GigabitEthernet1/0/1]ip add 172.16.1.1 24
[FW1-GigabitEthernet1/0/1]un sh
Info: Interface GigabitEthernet1/0/1 is not shutdown.
[FW1-GigabitEthernet1/0/1]q
[FW1]int g 1/0/2
[FW1-GigabitEthernet1/0/2]ip add 192.168.10.101 24
[FW1-GigabitEthernet1/0/2]un sh
Info: Interface GigabitEthernet1/0/2 is not shutdown.
[FW1-GigabitEthernet1/0/2]q
FW2
system-view
Enter system view, return user view with Ctrl+Z.
[USG6000V1]un in en
Info: Saving log files...
Info: Information center is disabled.
[USG6000V1]sysname FW2
[FW2]int g 1/0/0
[FW2-GigabitEthernet1/0/0]ip add 10.1.1.102 24
[FW2-GigabitEthernet1/0/0]un sh
Info: Interface GigabitEthernet1/0/0 is not shutdown.
[FW2-GigabitEthernet1/0/0]q
[FW2]int g 1/0/1
[FW2-GigabitEthernet1/0/1]ip add 172.16.1.2 24
[FW2-GigabitEthernet1/0/1]un sh
Info: Interface GigabitEthernet1/0/1 is not shutdown.
[FW2-GigabitEthernet1/0/1]q
[FW2]int g 1/0/2
[FW2-GigabitEthernet1/0/2]ip add 192.168.10.102 24
[FW2-GigabitEthernet1/0/2]un sh
Info: Interface GigabitEthernet1/0/2 is not shutdown.
[FW2-GigabitEthernet1/0/2]q
开始配置接口所在的安全区域和策略
FW1
[FW1]firewall zone trust
[FW1-zone-trust]add int g 1/0/2
[FW1-zone-trust]q
[FW1]firewall zone dmz
[FW1-zone-dmz]add int g 1/0/1
[FW1-zone-dmz]q
[FW1]firewall zone untrust
[FW1-zone-untrust]add int g 1/0/0
[FW1-zone-untrust]q
[FW1]sec
[FW1-policy-security]rule name xintiao
[FW1-policy-security-rule-xintiao]source-zone local
[FW1-policy-security-rule-xintiao]destination-zone dmz
[FW1-policy-security-rule-xintiao]action permit
[FW1-policy-security-rule-xintiao]q
[FW1-policy-security]rule name trusttoun
[FW1-policy-security-rule-trusttoun]source-zone trust
[FW1-policy-security-rule-trusttoun]destination-zone untrus
[FW1-policy-security-rule-trusttoun]action permit
[FW1-policy-security-rule-trusttoun]q
FW2
[FW2]fire zon dmz
[FW2-zone-dmz]add int g 1/0/1
[FW2-zone-dmz]q
[FW2]firewall zone untrust
[FW2-zone-untrust]add int g 1/0/0
[FW2-zone-untrust]q
[FW2]firewall zone trust
[FW2-zone-trust]add int g 1/0/2
[FW2-zone-trust]q
[FW2]sec
[FW2-policy-security]rule name xintiao
[FW2-policy-security-rule-xintiao]source-zone local
[FW2-policy-security-rule-xintiao]destination-zone dmz
[FW2-policy-security-rule-xintiao]act per
[FW2-policy-security-rule-xintiao]q
[FW2-policy-security]rule name trusttoun
[FW2-policy-security-rule-trusttoun]source-zone trust
[FW2-policy-security-rule-trusttoun]destination-zone untrust
[FW2-policy-security-rule-trusttoun]act per
[FW2-policy-security-rule-trusttoun]q
配置静态路由
[FW1]ip route-static 0.0.0.0 0.0.0.0 10.1.1.1
[FW2]ip route-static 0.0.0.0 0.0.0.0 10.1.1.1
然后开始配置VRRP组
上联口vrid 2
[FW1]int g 1/0/0
[FW1-GigabitEthernet1/0/0]dis this
2020-02-14 15:44:34.070
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.1.1.101 255.255.255.0
#
return
[FW1-GigabitEthernet1/0/0]vrrp vrid 2 virtual-ip 10.1.1.100 active
[FW2]int g 1/0/0
[FW2-GigabitEthernet1/0/0]dis this
2020-02-14 15:46:06.630
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.1.1.102 255.255.255.0
#
return
[FW2-GigabitEthernet1/0/0]vrrp vrid 2 vi 10.1.1.100 standby
下联口vrid 1
[FW1]int g 1/0/2
[FW1-GigabitEthernet1/0/2]vrr vrid 1 vi 192.168.10.100 ac
[FW2]int g 1/0/2
[FW2-GigabitEthernet1/0/2]vrr vri 1 vi 192.168.10.100 st
接下来开始配置会话表同步,配置心跳线
[FW1]hrp int g 1/0/1 re 172.16.1.2 ?
heartbeat-only Indicate the interface is used only for transfering control
messages
[FW1]hrp int g 1/0/1 re 172.16.1.2
[FW2]hrp int g 1/0/1 remote 172.16.1.1
开启hrp双机热备
[FW1]hrp enable
Info: NAT IP detect function is disabled.
HRP_S[FW1]
[FW2]hrp en
Info: NAT IP detect function is disabled.
HRP_M[FW1]dis hrp state
2020-02-14 15:54:47.140
Role: active, peer: standby
Running priority: 45000, peer: 45000
Backup channel usage: 0.00%
Stable time: 0 days, 0 hours, 0 minutes
Last state change information: 2020-02-14 15:54:27 HRP core state changed, old_
state = abnormal(standby), new_state = normal, local_priority = 45000, peer_prio
rity = 45000.
HRP_S[FW2]dis hrp state
2020-02-14 15:55:33.730
Role: standby, peer: active
Running priority: 45000, peer: 45000
Backup channel usage: 0.00%
Stable time: 0 days, 0 hours, 1 minutes
Last state change information: 2020-02-14 15:54:26 HRP link changes to up.
双机热备中的自动备份模式
HRP_S[FW2] hrp auto-sync
HRP_M[FW1]hrp auto-sync
查看心跳线接口
HRP_M[FW1]dis hrp interface
2020-02-14 15:59:51.650
GigabitEthernet1/0/1 : running
HRP_S[FW2]dis hrp interface
2020-02-14 16:00:12.980
GigabitEthernet1/0/1 : running
HRP_M[FW1]dis hrp ?
configuration Check local configuration with remote firewall
history-information Indicate HRP history information
interface Indicate HRP backup channels infomation
state Indicate the HRP status infomation
statistic Indicate HRP statistic information
配置回城路由
[R1]ip route-static 192.168.10.0 24 10.1.1.100
HRP_M[FW1]dis firewall session table
2020-02-14 16:07:35.370
Current Total Sessions : 7
icmp VPN: public --> public 192.168.10.1:47813 --> 1.1.1.1:2048
udp VPN: public --> public 172.16.1.2:16384 --> 172.16.1.1:18514
icmp VPN: public --> public 192.168.10.1:48581 --> 1.1.1.1:2048
udp VPN: public --> public 172.16.1.2:49152 --> 172.16.1.1:18514
udp VPN: public --> public 172.16.1.1:49152 --> 172.16.1.2:18514
icmp VPN: public --> public 192.168.10.1:48325 --> 1.1.1.1:2048
icmp VPN: public --> public 192.168.10.1:48069 --> 1.1.1.1:2048
HRP_M[FW1]dis firewall server-map
2020-02-14 16:07:41.410
Current Total Server-map : 0
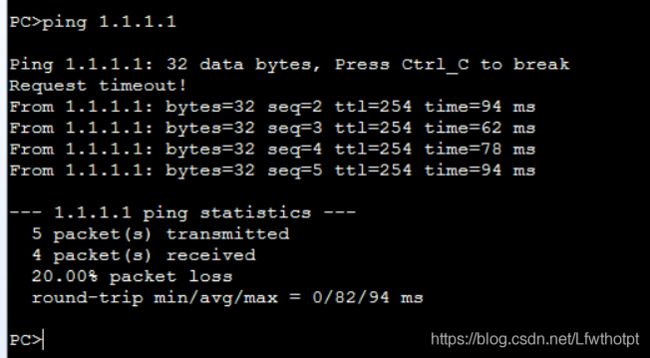
FW1断开G1/0/2,验证故障切换
HRP_M[FW1-GigabitEthernet1/0/2]shutdown
PCping1.1.1.1
HRP_S[FW1]dis firewall session table
2020-02-14 16:10:00.940
Current Total Sessions : 3
udp VPN: public --> public 172.16.1.2:16384 --> 172.16.1.1:18514
udp VPN: public --> public 172.16.1.2:49152 --> 172.16.1.1:18514
udp VPN: public --> public 172.16.1.1:49152 --> 172.16.1.2:18514
HRP_S[FW1]dis hrp state
2020-02-14 16:10:18.400
Role: standby, peer: active (should be "active-standby")
Running priority: 44998, peer: 45000
Backup channel usage: 0.00%
Stable time: 0 days, 0 hours, 1 minutes
Last state change information: 2020-02-14 16:09:03 HRP core state changed, old_
state = normal, new_state = abnormal(standby), local_priority = 44998, peer_prio
rity = 45000.
HRP_M[FW2]dis hrp state
2020-02-14 16:10:54.770
Role: active, peer: standby (should be "standby-active")
Running priority: 45000, peer: 44998
Backup channel usage: 0.00%
Stable time: 0 days, 0 hours, 1 minutes
Last state change information: 2020-02-14 16:09:02 HRP core state changed, old_
state = normal, new_state = abnormal(active), local_priority = 45000, peer_prior
ity = 44998.
HRP_S[FW1-GigabitEthernet1/0/2]un sh
HRP_S[FW1]dis hrp state
2020-02-14 16:12:10.980
Role: standby, peer: active (should be "active-standby")
Running priority: 45000, peer: 45000
Backup channel usage: 0.00%
Stable time: 0 days, 0 hours, 3 minutes
Last state change information: 2020-02-14 16:09:03 HRP core state changed, old_
state = normal, new_state = abnormal(standby), local_priority = 44998, peer_prio
rity = 45000.
过了一会,发现active回到了FW1
HRP_S[FW1]dis hrp state
2020-02-14 16:15:33.200
Role: active, peer: standby
Running priority: 45000, peer: 45000
Backup channel usage: 0.00%
Stable time: 0 days, 0 hours, 2 minutes
Last state change information: 2020-02-14 16:12:44 HRP core state changed, old_
state = abnormal(standby), new_state = normal, local_priority = 45000, peer_prio
rity = 45000.
HRP_M[FW2]dis hrp state
2020-02-14 16:16:11.400
Role: standby, peer: active
Running priority: 45000, peer: 45000
Backup channel usage: 0.00%
Stable time: 0 days, 0 hours, 3 minutes
Last state change information: 2020-02-14 16:12:44 HRP core state changed, old_
state = abnormal(active), new_state = normal, local_priority = 45000, peer_prior
ity = 45000.
原因是因为在接口处表明了active
在生产环境中,有可能会遇到心跳线闪断的问题,导致网络无法正常通讯
闪断原因大多数是因为接口或者网线解除不良,导致VRRP在两个接口之间来回切换,容易使控制报文不稳定,不可以正确指导数据层面的数据转发
tate = abnormal(standby), new_state = normal, local_priority = 45000, peer_prio
rity = 45000.
HRP_M[FW2]dis hrp state
2020-02-14 16:16:11.400
Role: standby, peer: active
Running priority: 45000, peer: 45000
Backup channel usage: 0.00%
Stable time: 0 days, 0 hours, 3 minutes
Last state change information: 2020-02-14 16:12:44 HRP core state changed, old_
state = abnormal(active), new_state = normal, local_priority = 45000, peer_prior
ity = 45000.
原因是因为在接口处表明了active
在生产环境中,有可能会遇到心跳线闪断的问题,导致网络无法正常通讯
闪断原因大多数是因为接口或者网线解除不良,导致VRRP在两个接口之间来回切换,容易使控制报文不稳定,不可以正确指导数据层面的数据转发
心跳线也可以使用ETH-TRUNK做