- linux初始mysql_linux mysql初始化
隔壁王医生
linux初始mysql
一、mysql_install_db说明当MySQL的系统库(mysql系统库)发生故障或需要新加一个mysql实例时,需要初始化mysql数据库。需要使用的命令:/usr/local/mysql/bin/mysql_install_db#/usr/local/mysql/bin/mysql_install_db--help可以查看帮助信息如下Usage:/usr/local/mysql/bin/
- 修改mysql初始密码
「已注销」
数据库mysqljava
查看当前MySQL登录密码[root@liwenjingmysql]#greppassword/var/log/mysqld.log2022-09-22T19:20:12.368849Z6[Note][MY-010454][Server]Atemporarypasswordisgeneratedforroot@localhost:mmxuyPx%+2hC当前登录密码为:mmxuyPx%+2hC执行
- uefi和bios的区别_BIOS和UEFI有什么区别?
cuma2369
uefi和bios的区别BIOS:BasicInputOutputSystemsUEFI:UnifiedExtensibleFirmwareInterfaceBIOS:基本输入输出系统UEFI:统一可扩展固件接口UEFIistheadvancedBIOS,whichsolvessomelimitationsinBIOSsuchas1,16-bitprocessormode;2,1MBaddress
- 用SpringBoot+mysql+html实现ATM 系统总结与扩展
SAFE20242034
#一SpringBootspringbootmysqlhtml
这里写目录标题ATM系统总结与扩展项目概述主要功能模块1.用户注册2.用户登录3.账户查询4.存款与取款5.转账6.修改密码7.销户系统改进建议功能扩展技术优化完整代码实现数据库表设计后端代码(SpringBoot示例)1.Account实体类2.AccountRepository接口3.AccountController类前端代码(HTML+JavaScript示例)实际开发与部署步骤**1.开
- Invocation of init method failed; nested exception is java.sql.SQLException: com.mysql.cj.jdbc.Drive
weixin_42277889
mysqljavasql
代码更新后连不上数据库,前天都还可以,现在不行了,一直报错mysql没有。Pom文件全局搜也灭有。一开始是查不到的,但是实际上pom文件中引入了,maven没有更新。。。。
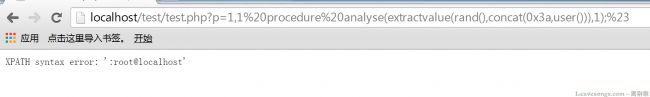
- 用友NC checkekey SQL 注入漏洞
403_found
漏洞复现sql数据库
免责声明本文旨在提供有关特定漏洞的深入信息,帮助用户充分了解潜在的安全风险。发布此信息的目的在于提升网络安全意识和推动技术进步,未经授权访问系统、网络或应用程序,可能会导致法律责任或严重后果。因此,作者不对读者基于本文内容所采取的任何行为承担责任。读者在使用本文信息时,必须严格遵循适用的法律法规及服务协议,自行承担一切风险与责任。如涉及侵权,请及时与我们联系,我们将尽快处理并删除相关内容。一,产品
- Kotlin 集合函数锦集,2021程序员进阶宝典
高级UI教学
Androidkotlinjavarust移动开发
postfix="的排名",limit=nameCollection.size,truncated="等")println(message)//在古代,根据人口数量和宗族的影响力,有刘一陈二张三李四王五赵六孙七周八吴九郑十的排名}####reduce函数将集合转换为单个结果如果希望将给定集合转换为单个结果,则可以使用reduce函数。例如,你可以计算列表中所有元素的和://将集合转换为单个结果fu
- mysql.sock.lock的作用_不能创建 mysql.sock.lock是怎么回事
0110君
15052003:26:57mysqld_safeStartingmysqlddaemonwithdatabasesfrom/usr/local/mysql/data2015-05-20T03:26:58.070269Z0[Warning]TIMESTAMPwithimplicitDEFAULTvalueisdeprecated.Pleaseuse--explicit_defaults_for_t
- mysql.sock.lock的作用,[轉帖]mysql.sock的作用
彩彩彩虹
2、socketmysql.sock的作用是server和client在同一台服務器,並且使用localhost進行鏈接的時候,就會使用socket來進行連接——僅此而已也就是:為主機名為localhost建立的MySQL連接,該連接過程通過一個套接字文件mysql.socket實現的。所以該文件被刪后,用localhost用戶是連接不到MySQL服務器的。必須建立一條tcp/ip連接,即使用12
- MongoDB 大俗大雅,上来问分片真三俗 -- 4 分什么分
Austindatabases
mongodb数据库
开头还是介绍一下群,如果感兴趣PolarDB,MongoDB,MySQL,PostgreSQL,Redis,OceanBase,SqlServer等有问题,有需求都可以加群群内有各大数据库行业大咖,可以解决你的问题。加群请联系liuaustin3,(共2710人左右1+2+3+4+5+6+7+8+9)(123456群均已爆满,7群400+,开8群9群)这是MongoDB宣传周的第五篇,这周真漫长,
- 导航与定位:室外导航技术_(11).室外导航技术在移动通信中的应用
zhubeibei168
机器人(二)php开发语言数据库运维机器人服务器
室外导航技术在移动通信中的应用1.移动通信中的定位技术1.1GPS定位技术GPS(全球定位系统)是目前最广泛使用的室外定位技术。GPS系统由空间段、控制段和用户段组成。空间段由24颗卫星组成,这些卫星在地球轨道上均匀分布,确保地球表面的任何位置都能接收到至少4颗卫星的信号。控制段包括地面监控站、注入站和主控站,负责监控卫星的运行状态并校正其位置和时间误差。用户段则是各种GPS接收设备,如智能手机、
- flask搜索mysql_数据库|Flask实现简单搜索功能
科技松鼠会
flask搜索mysql
数据库|Flask实现简单搜索功能2021-01-16问题描述用Flask实现简单搜索功能主要是通过form的方式传值,再到数据库中查询。下面是数据库的内容,主要是实现对content进行模糊匹配。图1数据库内容解决方案1.首先打开pycharm,构建一个最简单的flask应用。#search.pyfromflaskimportFlaskapp=Flask(__name__)@app.route(
- mybatis/mybatis-plus模糊查询语句特殊字符转义拦截器的实现
Java云海.
mysql数据库database
在开发中,我们通常会遇到这样的情况。用户在录入信息是录入了‘%’,而在查询时无法精确匹配‘%’。究其原因,‘%’是MySQL的关键字,如果我们想要精确匹配‘%’,那么需要对其进行转义,本文就详细的介绍一下目录1.使用mybatis提供的拦截器拦截所有的查询请求。2.定义SQL语句转义模板,分别对Map和Object对象进行处理mybatis/mybatis-plus模糊查询语句特殊字符转义拦截器在
- 阿里巴巴大数据系统体系架构
大连赵哥
大数据架构
数据应用层:这是最顶层,面向不同的用户群体提供服务,包括对内(公司内部使用)、对平台(平台用户)、对商家(商家使用)、对公众(普通消费者)。数据服务与基础工具层:这一层提供了一些基础服务和工具,例如:OneService:可能是一种服务或工具,用于统一数据服务。TDDL+MySQL:TDDL是淘宝分布式数据层的缩写,与MySQL结合使用,提供数据库服务。HBase:一个分布式列存储系统,适合于存储
- Redis与MySql的区别
GugarF95
redismysql数据库
Redis和MySQL是两种不同类型的数据库系统,它们在数据存储方式、性能特点、适用场景等方面存在诸多区别,以下是详细介绍:数据存储类型MySQL:是一种关系型数据库管理系统(RDBMS),以表格的形式组织数据,表由行和列组成,每行代表一个记录,每列代表一个属性。通过定义表结构,包括字段类型、长度、是否为主键等约束条件,来存储结构化数据,如用户信息表、订单表等。支持复杂的数据关系,如一对一、一对多
- MySQL UNION 操作详解
lsx202406
开发语言
MySQLUNION操作详解引言在数据库操作中,UNION是一个非常重要的概念,它允许我们在一个查询中合并多个SELECT语句的结果集。UNION操作通常用于将来自不同表的数据合并在一起,或者将同一表中的数据按照不同的条件进行合并。本文将详细介绍MySQL中的UNION操作,包括其语法、使用场景以及注意事项。UNION语法UNION语法的基本格式如下:SELECTcolumn_name(s)FRO
- C# EntityFramework 连接 MySQL
吃不胖的猫o(=^ェ^=)m
c#mysql
安装1.安装MySQL-connector-NET6.9.12.msi2.安装MySQL-for-visualstudio1.2.9.msi3.安装MySQL.Data(版本需要与MySQLConnector/NET相同):在VisualStudio的"程序包管理控制台"执行Install-PackageMySQL.Data6.9.124.安装MySql.Data.Entity(版本需要与MySQ
- C#使用实体类Entity Framework Core操作mysql入门:从数据库反向生成模型2 处理连接字符串
初级代码游戏
dotnet和C#数据库mysqlEntityFramework
初级代码游戏的专栏介绍与文章目录-CSDN博客我的github:codetoys,所有代码都将会位于ctfc库中。已经放入库中我会指出在库中的位置。这些代码大部分以Linux为目标但部分代码是纯C++的,可以在任何平台上使用。源码指引:github源码指引_初级代码游戏的博客-CSDN博客本文接上一篇:C#使用实体类EntityFrameworkCore操作mysql入门:从数据库反向生成模型-C
- 用自然语言与mysql数据库对话几种方案的思考
闲云野鹤_SG
数据库mysqlAItext2sql自然语言本地部署大模型
如何用自然语言与mysql数据库对话,而不是用sql语句去查询数据库?处于安全考虑,可训练一个本地大语言模型来完成此项任务,mysql服务器中的数据大约有两万多条记录,服务器的作用主要是记录设备的出库和回库的流水账(即以时间为序的记录),但有一些sql查询比较复杂,必须根据特定的sql语句查询,否则很难得到准确稳定的答案,调试和训练大模型的方法有多种方式,比如lora训练模型,提示词方式,rag方
- Django安装mysqlclient报错
Louis yeap
macosdjango后端python
系列文章目录文章目录系列文章目录前言总结前言CollectingmysqlclientUsingcachedmysqlclient-2.2.4.tar.gz(90kB)Installingbuilddependencies...doneGettingrequirementstobuildwheel...errorerror:subprocess-exited-with-error×Gettingr
- 开源OA办公系统
零起飞
ERP开源oa
介绍07FlyOA是一款基于TP5+HAdmin+Mysql打造的简单实用的开源的企业办公系统框架。可以帮助解决企业办公项目60%的重复工作,让开发更多关注业务逻辑。既能快速提高开发效率,帮助公司节省人力成本,同时又不失灵活性。使用07FLyOA可以简单快速地开发出企业级的Web应用系统。系统特点系统各功能模块,一目了然,操作简单;通用型的后台权限管理框架,员工的操作记录全覆盖跟踪,紧随潮流、极低
- 前端安全:构建坚不可摧的Web应用防线
CodeToGym
前端安全
引言在数字化时代,网络安全已成为每个Web开发者必须面对的挑战。前端安全不仅关乎用户体验,更是保护用户数据和企业资产的关键。本文将深入探讨前端安全的多个维度,包括跨站脚本攻击(XSS)、跨站请求伪造(CSRF)、内容安全策略(CSP)以及HTTPS的实施,旨在帮助开发者构建更加安全的Web应用。跨站脚本攻击(XSS)概述跨站脚本攻击(XSS)是一种代码注入攻击,攻击者通过在网页中注入恶意脚本,利用
- 【附源码】Java计算机毕业设计小说阅读网站(程序+LW+部署)
一念 计算机毕设源码程序
java课程设计mysql
项目运行环境配置:Jdk1.8+Tomcat7.0+Mysql+HBuilderX(Webstorm也行)+Eclispe(IntelliJIDEA,Eclispe,MyEclispe,Sts都支持)。项目技术:java+mybatis+Maven等等组成,B/S模式+Maven管理等等。环境需要1.运行环境:最好是javajdk1.8,我们在这个平台上运行的。其他版本理论上也可以。2.IDE环境
- mysql var目录很快_删除/var/lib/mysql目录的解决办法
逆铭
mysqlvar目录很快
在学习阶段偶尔会删除/var/lib/mysql/*目录来达到清除数据库管理员账户和密码的目的。but,对于新手来说经常会不小心删除/var/lib/mysql目录,导致重启mysql时找不到/var/lib/mysql。解决方法如下:mkdir/var/lib/mysqchownmysql:mysql/var/lib/mysqlsystemctlstartmysql此时如果还是失败,并产生如下提
- docker挂载mysql会失败_Docker Mysql 挂载 /var/lib/mysql 后无法启动
Joseph Holy
我也遇到相同的问题了`dockerrun\-p4406:3306\-eMYSQL_ROOT_PASSWORD=localDocker@mysql\-eTZ=Asia/Shanghai\-v/mnt/hgfs/docker/mysql/data:/var/lib/mysql\-v/mnt/hgfs/docker/mysql/log:/var/log/mysql:rw\-v/mnt/hgfs/dock
- 登录mysql出现/var/lib/mysql/mysql.sock不存在
小黄鸭007
mysql数据库
问题描述:1.mysql安装完成后,使用servicemysqldrestart总是出现stopmysqldservice失败。2.使用mysql-uroot-p登录出现找不到/var/lib/mysql/mysql.sock问题。3.使用servicemysqldstatus出现mysqldeadbutsubsyslocked解决方法:1.在my.cnf下[mysqld]前添加[client]p
- C语言连接Mysql
monGyrate
数据库相关c语言mysql
目录C语言连接Mysql下载mysql开发库方法介绍mysql_init()mysql_real_connect()mysql_query()mysql_store_result()mysql_num_fields()mysql_fetch_fields()mysql_fetch_row()mysql_free_result()mysql_close()完整代码C语言连接Mysql下载mysql开
- 构建一个有智能体参与的去中心化RWA零售生态系统商业模型
leijiwen
去中心化零售区块链
引言随着数字技术和区块链的快速发展,零售行业正在发生深刻变革。去中心化技术打破了传统的集中化零售模式,而智能体(AIAgents)的参与则为这个领域注入了全新的活力。本文提出了一种结合智能体与去中心化技术的RWA(Real-WorldAssets)零售生态系统商业模型,目标是通过区块链、联合曲线积分激励、智能推荐、NFT会员和社区治理等模块,构建一个高效透明、用户共创的零售生态。核心框架概述数据驱
- protoc-go-inject-tag 使用教程
农彩媛Louise
protoc-go-inject-tag使用教程项目地址:https://gitcode.com/gh_mirrors/pr/protoc-go-inject-tag项目介绍protoc-go-inject-tag是一个用于在生成的Go结构体中注入自定义标签的工具。在使用ProtocolBuffers(protobuf)生成Go代码时,默认情况下生成的结构体标签是固定的,无法灵活设置。protoc
- 【编程小白必看】MySQL 时间类型操作秘籍一文全掌握
6个q
mysql数据库mysqladb数据库
【编程小白必看】MySQL时间类型操作秘籍一文全掌握文章目录前言一、MySQL时间类型有哪些?二、时间类型详解1.DATE类型2.TIME类型3.DATETIME类型4.TIMESTAMP类型5.YEAR类型三、日期时间函数1.CURRENT_DATE()和CURRENT_TIME()2.NOW()和SYSDATE()3.DATE_ADD()和DATE_SUB()4.STR_TO_DATE()和D
- ASM系列五 利用TreeApi 解析生成Class
lijingyao8206
ASM字节码动态生成ClassNodeTreeAPI
前面CoreApi的介绍部分基本涵盖了ASMCore包下面的主要API及功能,其中还有一部分关于MetaData的解析和生成就不再赘述。这篇开始介绍ASM另一部分主要的Api。TreeApi。这一部分源码是关联的asm-tree-5.0.4的版本。
在介绍前,先要知道一点, Tree工程的接口基本可以完
- 链表树——复合数据结构应用实例
bardo
数据结构树型结构表结构设计链表菜单排序
我们清楚:数据库设计中,表结构设计的好坏,直接影响程序的复杂度。所以,本文就无限级分类(目录)树与链表的复合在表设计中的应用进行探讨。当然,什么是树,什么是链表,这里不作介绍。有兴趣可以去看相关的教材。
需求简介:
经常遇到这样的需求,我们希望能将保存在数据库中的树结构能够按确定的顺序读出来。比如,多级菜单、组织结构、商品分类。更具体的,我们希望某个二级菜单在这一级别中就是第一个。虽然它是最后
- 为啥要用位运算代替取模呢
chenchao051
位运算哈希汇编
在hash中查找key的时候,经常会发现用&取代%,先看两段代码吧,
JDK6中的HashMap中的indexFor方法:
/**
* Returns index for hash code h.
*/
static int indexFor(int h, int length) {
- 最近的情况
麦田的设计者
生活感悟计划软考想
今天是2015年4月27号
整理一下最近的思绪以及要完成的任务
1、最近在驾校科目二练车,每周四天,练三周。其实做什么都要用心,追求合理的途径解决。为
- PHP去掉字符串中最后一个字符的方法
IT独行者
PHP字符串
今天在PHP项目开发中遇到一个需求,去掉字符串中的最后一个字符 原字符串1,2,3,4,5,6, 去掉最后一个字符",",最终结果为1,2,3,4,5,6 代码如下:
$str = "1,2,3,4,5,6,";
$newstr = substr($str,0,strlen($str)-1);
echo $newstr;
- hadoop在linux上单机安装过程
_wy_
linuxhadoop
1、安装JDK
jdk版本最好是1.6以上,可以使用执行命令java -version查看当前JAVA版本号,如果报命令不存在或版本比较低,则需要安装一个高版本的JDK,并在/etc/profile的文件末尾,根据本机JDK实际的安装位置加上以下几行:
export JAVA_HOME=/usr/java/jdk1.7.0_25
- JAVA进阶----分布式事务的一种简单处理方法
无量
多系统交互分布式事务
每个方法都是原子操作:
提供第三方服务的系统,要同时提供执行方法和对应的回滚方法
A系统调用B,C,D系统完成分布式事务
=========执行开始========
A.aa();
try {
B.bb();
} catch(Exception e) {
A.rollbackAa();
}
try {
C.cc();
} catch(Excep
- 安墨移动广 告:移动DSP厚积薄发 引领未来广 告业发展命脉
矮蛋蛋
hadoop互联网
“谁掌握了强大的DSP技术,谁将引领未来的广 告行业发展命脉。”2014年,移动广 告行业的热点非移动DSP莫属。各个圈子都在纷纷谈论,认为移动DSP是行业突破点,一时间许多移动广 告联盟风起云涌,竞相推出专属移动DSP产品。
到底什么是移动DSP呢?
DSP(Demand-SidePlatform),就是需求方平台,为解决广 告主投放的各种需求,真正实现人群定位的精准广
- myelipse设置
alafqq
IP
在一个项目的完整的生命周期中,其维护费用,往往是其开发费用的数倍。因此项目的可维护性、可复用性是衡量一个项目好坏的关键。而注释则是可维护性中必不可少的一环。
注释模板导入步骤
安装方法:
打开eclipse/myeclipse
选择 window-->Preferences-->JAVA-->Code-->Code
- java数组
百合不是茶
java数组
java数组的 声明 创建 初始化; java支持C语言
数组中的每个数都有唯一的一个下标
一维数组的定义 声明: int[] a = new int[3];声明数组中有三个数int[3]
int[] a 中有三个数,下标从0开始,可以同过for来遍历数组中的数
- javascript读取表单数据
bijian1013
JavaScript
利用javascript读取表单数据,可以利用以下三种方法获取:
1、通过表单ID属性:var a = document.getElementByIdx_x_x("id");
2、通过表单名称属性:var b = document.getElementsByName("name");
3、直接通过表单名字获取:var c = form.content.
- 探索JUnit4扩展:使用Theory
bijian1013
javaJUnitTheory
理论机制(Theory)
一.为什么要引用理论机制(Theory)
当今软件开发中,测试驱动开发(TDD — Test-driven development)越发流行。为什么 TDD 会如此流行呢?因为它确实拥有很多优点,它允许开发人员通过简单的例子来指定和表明他们代码的行为意图。
TDD 的优点:
&nb
- [Spring Data Mongo一]Spring Mongo Template操作MongoDB
bit1129
template
什么是Spring Data Mongo
Spring Data MongoDB项目对访问MongoDB的Java客户端API进行了封装,这种封装类似于Spring封装Hibernate和JDBC而提供的HibernateTemplate和JDBCTemplate,主要能力包括
1. 封装客户端跟MongoDB的链接管理
2. 文档-对象映射,通过注解:@Document(collectio
- 【Kafka八】Zookeeper上关于Kafka的配置信息
bit1129
zookeeper
问题:
1. Kafka的哪些信息记录在Zookeeper中 2. Consumer Group消费的每个Partition的Offset信息存放在什么位置
3. Topic的每个Partition存放在哪个Broker上的信息存放在哪里
4. Producer跟Zookeeper究竟有没有关系?没有关系!!!
//consumers、config、brokers、cont
- java OOM内存异常的四种类型及异常与解决方案
ronin47
java OOM 内存异常
OOM异常的四种类型:
一: StackOverflowError :通常因为递归函数引起(死递归,递归太深)。-Xss 128k 一般够用。
二: out Of memory: PermGen Space:通常是动态类大多,比如web 服务器自动更新部署时引起。-Xmx
- java-实现链表反转-递归和非递归实现
bylijinnan
java
20120422更新:
对链表中部分节点进行反转操作,这些节点相隔k个:
0->1->2->3->4->5->6->7->8->9
k=2
8->1->6->3->4->5->2->7->0->9
注意1 3 5 7 9 位置是不变的。
解法:
将链表拆成两部分:
a.0-&
- Netty源码学习-DelimiterBasedFrameDecoder
bylijinnan
javanetty
看DelimiterBasedFrameDecoder的API,有举例:
接收到的ChannelBuffer如下:
+--------------+
| ABC\nDEF\r\n |
+--------------+
经过DelimiterBasedFrameDecoder(Delimiters.lineDelimiter())之后,得到:
+-----+----
- linux的一些命令 -查看cc攻击-网口ip统计等
hotsunshine
linux
Linux判断CC攻击命令详解
2011年12月23日 ⁄ 安全 ⁄ 暂无评论
查看所有80端口的连接数
netstat -nat|grep -i '80'|wc -l
对连接的IP按连接数量进行排序
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
查看TCP连接状态
n
- Spring获取SessionFactory
ctrain
sessionFactory
String sql = "select sysdate from dual";
WebApplicationContext wac = ContextLoader.getCurrentWebApplicationContext();
String[] names = wac.getBeanDefinitionNames();
for(int i=0; i&
- Hive几种导出数据方式
daizj
hive数据导出
Hive几种导出数据方式
1.拷贝文件
如果数据文件恰好是用户需要的格式,那么只需要拷贝文件或文件夹就可以。
hadoop fs –cp source_path target_path
2.导出到本地文件系统
--不能使用insert into local directory来导出数据,会报错
--只能使用
- 编程之美
dcj3sjt126com
编程PHP重构
我个人的 PHP 编程经验中,递归调用常常与静态变量使用。静态变量的含义可以参考 PHP 手册。希望下面的代码,会更有利于对递归以及静态变量的理解
header("Content-type: text/plain");
function static_function () {
static $i = 0;
if ($i++ < 1
- Android保存用户名和密码
dcj3sjt126com
android
转自:http://www.2cto.com/kf/201401/272336.html
我们不管在开发一个项目或者使用别人的项目,都有用户登录功能,为了让用户的体验效果更好,我们通常会做一个功能,叫做保存用户,这样做的目地就是为了让用户下一次再使用该程序不会重新输入用户名和密码,这里我使用3种方式来存储用户名和密码
1、通过普通 的txt文本存储
2、通过properties属性文件进行存
- Oracle 复习笔记之同义词
eksliang
Oracle 同义词Oracle synonym
转载请出自出处:http://eksliang.iteye.com/blog/2098861
1.什么是同义词
同义词是现有模式对象的一个别名。
概念性的东西,什么是模式呢?创建一个用户,就相应的创建了 一个模式。模式是指数据库对象,是对用户所创建的数据对象的总称。模式对象包括表、视图、索引、同义词、序列、过
- Ajax案例
gongmeitao
Ajaxjsp
数据库采用Sql Server2005
项目名称为:Ajax_Demo
1.com.demo.conn包
package com.demo.conn;
import java.sql.Connection;import java.sql.DriverManager;import java.sql.SQLException;
//获取数据库连接的类public class DBConnec
- ASP.NET中Request.RawUrl、Request.Url的区别
hvt
.netWebC#asp.nethovertree
如果访问的地址是:http://h.keleyi.com/guestbook/addmessage.aspx?key=hovertree%3C&n=myslider#zonemenu那么Request.Url.ToString() 的值是:http://h.keleyi.com/guestbook/addmessage.aspx?key=hovertree<&
- SVG 教程 (七)SVG 实例,SVG 参考手册
天梯梦
svg
SVG 实例 在线实例
下面的例子是把SVG代码直接嵌入到HTML代码中。
谷歌Chrome,火狐,Internet Explorer9,和Safari都支持。
注意:下面的例子将不会在Opera运行,即使Opera支持SVG - 它也不支持SVG在HTML代码中直接使用。 SVG 实例
SVG基本形状
一个圆
矩形
不透明矩形
一个矩形不透明2
一个带圆角矩
- 事务管理
luyulong
javaspring编程事务
事物管理
spring事物的好处
为不同的事物API提供了一致的编程模型
支持声明式事务管理
提供比大多数事务API更简单更易于使用的编程式事务管理API
整合spring的各种数据访问抽象
TransactionDefinition
定义了事务策略
int getIsolationLevel()得到当前事务的隔离级别
READ_COMMITTED
- 基础数据结构和算法十一:Red-black binary search tree
sunwinner
AlgorithmRed-black
The insertion algorithm for 2-3 trees just described is not difficult to understand; now, we will see that it is also not difficult to implement. We will consider a simple representation known
- centos同步时间
stunizhengjia
linux集群同步时间
做了集群,时间的同步就显得非常必要了。 以下是查到的如何做时间同步。 在CentOS 5不再区分客户端和服务器,只要配置了NTP,它就会提供NTP服务。 1)确认已经ntp程序包: # yum install ntp 2)配置时间源(默认就行,不需要修改) # vi /etc/ntp.conf server pool.ntp.o
- ITeye 9月技术图书有奖试读获奖名单公布
ITeye管理员
ITeye
ITeye携手博文视点举办的9月技术图书有奖试读活动已圆满结束,非常感谢广大用户对本次活动的关注与参与。 9月试读活动回顾:http://webmaster.iteye.com/blog/2118112本次技术图书试读活动的优秀奖获奖名单及相应作品如下(优秀文章有很多,但名额有限,没获奖并不代表不优秀):
《NFC:Arduino、Andro