物联网网络安全
This article is based on a guest lecture delivered at the Technical University of Denmark.
本文基于丹麦技术大学的客座演讲。
I’m an IoT researcher with more than 10 years of experience in low-power wireless networks and embedded systems. In the early days, often our main goal was to make things work at all. Security was an afterthought; besides the fact that many of the first uses of IoT were in “toy” applications, few people were even aware of the existence of these low-power wireless sensor networks, and fewer still had the means to attack them. Now, IoT becomes more and more widely used, and we start to make important decisions based on data coming from these low-cost low-power devices, IoT security must become now a sharp point of focus. Otherwise, our field risks to obtain and keep a troubled and untrustworthy reputation.
我是一名物联网研究员,在低功耗无线网络和嵌入式系统方面拥有超过10年的经验。 在早期,我们的主要目标通常是使一切正常运行。 安全是事后的想法; 除了IoT的许多首次使用是在“玩具”应用程序中的事实之外,很少有人甚至意识到这些低功率无线传感器网络的存在,并且很少有人能够攻击它们。 现在,物联网越来越广泛地使用,并且我们开始根据来自这些低成本,低功耗设备的数据做出重要决策,物联网安全现在必须成为重点。 否则,我们的领域就有可能获得并保持麻烦和不信任的声誉。
The problem is hard as IoT networks are vulnerable to all of the usual security threats affecting other, more traditional computer networks. On top of that, they are more severely vulnerable or additionally vulnerable to specific attacks, such as sniffing and jamming.
这个问题很难解决,因为物联网网络容易受到影响其他更传统的计算机网络的所有常规安全威胁的攻击。 最重要的是,它们更容易受到攻击,或者更容易受到特定攻击(例如嗅探和干扰)的攻击。
什么是物联网网络? (What is an IoT network?)
“Internet of Things” has many definitions. Here are some of my favorite:
“物联网”有许多定义。 这是我最喜欢的一些东西:
“A network of Internet connected objects able to collect and exchange data.” (source)
“一个互联网连接的对象网络,能够收集和交换数据。” (来源)
“A system of interrelated computing devices, mechanical and digital machines provided with unique identifiers and the ability to transfer data over a network without requiring human-to-human or human-to-computer interaction.” (source)
“由相互关联的计算设备,机械和数字机器组成的系统,具有唯一的标识符,并且能够通过网络传输数据,而无需人与人或人与计算机的交互。” (来源)
Clearly, networking is an essential aspect of IoT. Personally, I define an IoT network simply as a network of low-power wireless devices that may or may not be connected to the Internet.
显然,网络是物联网的重要方面。 就个人而言,我将IoT网络简单地定义为可能连接或可能不连接到Internet的低功率无线设备网络。
The applications of IoT include industrial monitoring and control (Industry 4.0), smart homes, smart cities, smart agriculture, as well as many use cases for healthcare and fitness, for example, in the form of body area networks composed of wearable sensors. Applications are also emerging for wireless in-car and in-airplane networks (for example, for on-board entertainment).
物联网的应用包括工业监测和控制(工业4.0 ),智能家居,智能城市,智能农业以及医疗保健和健身的许多用例,例如以可穿戴式传感器组成的人体局域网的形式。 无线车载和飞机网络(例如,车载娱乐)的应用也正在兴起。
The technologies used in IoT networks include both traditional WiFi and cellular communications and more specific protocols:
物联网网络中使用的技术包括传统的WiFi和蜂窝通信以及更具体的协议:
Short range protocols: IEEE 802.15.4, Bluetooth and Bluetooth Low Energy (BLE), and for some applications WiFi. While there are “low power” WiFi devices, the dedicated low-power protocols usually are better choice for battery powered devices, as its difficult to conform to the WiFi standards while saving a lot of energy. These are mainly used in body area, healthcare/fitness and smart home applications, as well as in industrial automation.
短程协议: IEEE 802.15.4,蓝牙和低功耗蓝牙(BLE),以及某些应用程序的WiFi。 尽管存在“低功耗” WiFi设备,但是专用的低功耗协议通常是电池供电设备的更好选择,因为它难以符合WiFi标准,同时又节省了大量能源。 这些主要用于人体区域,医疗保健/健身和智能家居应用,以及工业自动化。
Long range protocols: LoRa/LoRaWAN, NB-IoT, Sigfox, IEEE 802.15.4g, IEEE 802.11ah (“WiFi HaLow”). These are mainly used in smart agriculture, smart city, and smart home applications.
远程协议: LoRa / LoRaWAN,NB-IoT,Sigfox,IEEE 802.15.4g,IEEE 802.11ah(“ WiFi HaLow”)。 这些主要用于智慧农业,智慧城市和智慧家庭应用。
无线通讯 (Wireless communications)
Wireless communication usually uses electromagnetic waves as the communication medium. (Some other options are available, such as wireless communication using electric field or magnetic field alone, and wireless communication using sounds.) IoT devices typically use the 2.4 GHz band for short range network and 433, 868 or 915 MHz bands for longer range networks. The range is longer, but the achievable data rates are lower in the sub-GHz land.
无线通信通常使用电磁波作为通信介质。 (一些其他选项可用,例如仅使用电场或磁场进行无线通信,以及使用声音进行无线通信。)IoT设备通常将2.4 GHz频段用于短距离网络,将433、868或915 MHz频段用于远程网络。 范围更长,但在低于GHz的范围内可达到的数据速率较低。
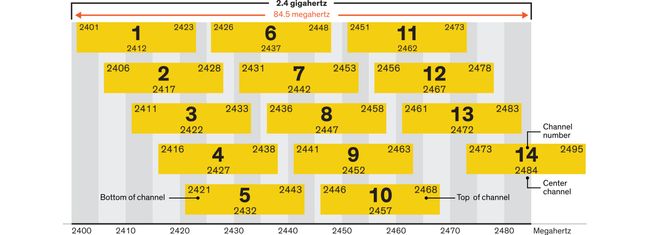
WiFI and BLE channels in the 2.4 GHz band 2.4 GHz频段中的WiFI和BLE通道 WiFi channels in the 2.4 GHz band 2.4 GHz频段中的WiFi通道An issue with the 2.4 GHz band is that its overloaded by signals. It is also heavily used by WiFi networks, as well as both by Bluetooth and IEEE 802.15.4 IoT networks. To sidetrack a bit: the 2.4 GHz is not so heavily used because it is free, and not because it is such a good frequency band — in contrast, this band is in fact bad for communication! It has a local maxima for absorption of electromagnetic waves by water vapor, hence, establishing long open-air radio links in the 2.4 GHz band is a bad idea. (The high interaction with water is also the reason why the 2.4 GHz frequency is used by microwave ovens — another device class which is “competing” for wireless spectrum in our homes and offices, albeit in the form of accidental and undesired leakage of electromagnetic radiation.) In fact, most of the frequency bands that are “bad” in some way (for example, with relatively high absorption by water vapor or by oxygen) are marked as free by international standard organizations. They are called ISM — industrial, scientific and medical — bands. Some of them, such as the 2.4 GHz band are free worldwide, others such as 868 MHz band are local to a region. As the name “ISM” implies, the original intention was to keep them for uses not related to communication; however, that ship has sailed long ago.
2.4 GHz频段的一个问题是信号过载。 WiFi网络,蓝牙和IEEE 802.15.4 IoT网络也大量使用它。 稍微回避一下:2.4 GHz并不是因为它是免费的而使用得太多,而不是因为它是一个很好的频带,相反,这个频带实际上不利于通信! 它具有一个局部最大值,可以被水蒸气吸收电磁波,因此,在2.4 GHz频带中建立较长的露天无线电链路是一个坏主意。 (与水的高相互作用也是微波炉使用2.4 GHz频率的原因-另一类设备正在“竞争”我们的家庭和办公室中的无线频谱,尽管其形式是意外和不希望的电磁辐射泄漏。)实际上,国际标准组织将大多数以某种方式“坏”的频段(例如,被水蒸气或氧气吸收相对较高的频段)标记为免费。 它们被称为ISM(工业,科学和医学)频段。 其中一些(例如2.4 GHz频段)在全球范围内是免费的,而其他一些(例如868 MHz频段)则在某个区域本地。 顾名思义,“ ISM”的初衷是将其保留与通讯无关的用途。 但是,那艘船已经航行很久了。
The communication technologies competing for the 2.4 GHz band don’t use the whole band at once. Instead, they separate it in channels. The sender and receiver devices must be on the same channel in order to communicate. The number of the channels depend on the technology:
争夺2.4 GHz频段的通信技术不会一次使用整个频段。 取而代之的是,它们将它们分隔在channel中。 发送方和接收方设备必须在同一通道上才能进行通信。 通道数取决于技术:
- WiFi: 13–14 channels (for 20 MHz channels, fewer for larger channels) WiFi:13–14个频道(用于20 MHz频道,用于较大频道的频道较少)
- Bluetooth Classic: 79 channels 蓝牙经典版:79个频道
- Bluetooth Low Energy (BLE): 40 channels低功耗蓝牙(BLE):40个通道
- 6LoWPAN: 16 channels6LoWPAN:16个频道
This gives opportunities for coexistence between multiple technologies, as it unlikely that a single technology is going to occupy all of the channels at once.
这为多种技术之间的共存提供了机会,因为单个技术不可能一次占据所有渠道。
嗅探攻击 (Sniffing attacks)
Sniffing is another name for eavesdropping — picking up signals not meant for you. Wireless communication makes sniffing much easier, as the attacker may do the attack remotely.
监听是监听的另一个名称-拾取不适合您的信号。 无线通信使嗅探变得容易得多,因为攻击者可以远程进行攻击。
Sniffing can be countered by encryption. However, even if encryption is enabled, opportunities for side-channel attacks remain:
嗅探可以通过加密来解决。 但是,即使启用了加密,仍然会出现旁道攻击的机会:
Signal strength correlates with the distance to the transmitter → location information becomes available; the variability of signal strength over time correlated with the movement patterns of the transmitter →signal variability can be used to determine the current activity of the human wearing the transmitter device, for example!
信号强度与到发射机的距离有关→位置信息可用; 例如,信号强度随时间的变化与发射机的运动模式相关联→信号变化可用于确定佩戴发射机设备的人的当前活动!
Packet sizes may encode information about the traffic, such as the types of events being reported over the encrypted connection.
数据包大小可以编码有关流量的信息,例如通过加密连接报告的事件类型。
Periods between packets may encode the dynamics of the processes being monitored.
分组之间的时间段可以编码被监视的过程的动态。
It may be tricky to sniff packets if the communication protocol uses multiple channels to communicate. Channel hopping is necessary to remain on the same channel as the transmitter. This is the main drawback of narrow-band sniffing. However, this kind of sniffing can can be done using any device with an appropriate transceiver — no dedicated hardware is needed.
如果通信协议使用多个通道进行通信,则嗅探数据包可能很棘手。 为了与发送器保持在同一信道上,必须进行信道跳变。 这是窄带嗅探的主要缺点。 但是,可以使用任何具有适当收发器的设备来完成这种嗅探-不需要专用硬件。
Using a software-defined radio (SDR) it may be possible to sniff the whole frequency band and decode all packets being transmitted on specific channels. This wide-band sniffing is a nontrivial task for sure, but one feasible in theory. SDR come in multiple price and capability levels — starting from simple ones like the RTL-SDR dongle (~25 USD), to HackRF (a couple hundred USD) to the more professional USPR (a couple thousand USD). If you’re a protocol developer or a serious hacker, you might even buy a dedicated wide-band Bluetooth sniffer that works out of the box (and costs a couple tens of thousands of USD).
使用软件定义的无线电(SDR),可以嗅探整个频带并对在特定信道上传输的所有数据包进行解码。 当然,这种宽带嗅探是一项艰巨的任务,但在理论上是可行的。 SDR具有多种价格和功能级别-从简单的RTL-SDR软件狗(约25美元)到HackRF (几百美元)再到更专业的USPR (几千美元)。 如果您是协议开发人员或认真的黑客,您甚至可以购买开箱即用的专用宽带蓝牙嗅探器(价格为数万美元)。
干扰攻击 (Jamming attacks)
In a jamming attack, the attacker interferes with the connection between the IoT devices. All wireless signals are vulnerable to jamming, however, IoT devices are especially vulnerable due to their low transmission power. For example, a typical transmission power for a WiFi device is 14 to 17 dBm (decibel-milliwatts). In contrast, IoT devices typically transmit at 0 dBm to 5 dBm — an order of magnitude difference. As a result, it is easy to drown the signal coming from an IoT transmitter even with a commodity WiFi hardware.
在干扰攻击中,攻击者会干扰物联网设备之间的连接。 所有无线信号都容易受到干扰,但是,IoT设备由于传输功率低而特别容易受到攻击。 例如,WiFi设备的典型传输功率为14到17 dBm (分贝-毫瓦)。 相比之下,物联网设备通常以0 dBm至5 dBm的传输速度-一个数量级的差异。 因此,即使使用商用WiFi硬件,也很容易淹没来自IoT发射机的信号。
There is a number of techniques how to counter jamming (as well as unintentional, benevolent cross-protocol interference):
有许多技术可以解决干扰(以及无意的,仁慈的跨协议干扰):
- Simple repetition, where the same data may be transmitted multiple times at different points of time; 简单重复,相同的数据可以在不同的时间点多次传输;
- Frequency diversity, where the same data may be transmitted at different frequencies (i.e. channels); 频率分集,其中相同的数据可以在不同的频率(即信道)上传输;
- Spatial diversity, where multiple nodes at different positions may transmit the same data; 空间分集,其中位于不同位置的多个节点可以传输相同的数据;
- Polarization diversity, where multiple antenna polarizations are used; 极化分集,其中使用多个天线极化;
- Coding redundancy, where on-the-air data is encoded in a way that allows to reconstruct the packet even if parts of it are corrupted. 编码冗余,其中空中数据的编码方式允许即使部分数据包已损坏也可以重建数据包。
However, a sufficiently advanced attacker will always be able to simply drown the communication within an IoT network using a sufficiently wide-band, sufficiently long and sufficiently strong jamming signal. It is not possible to fully counter this attack with any specific technique. As often in such situations, the fallback is to counter it via legal action. The specific laws are different to each frequency band, but in general it is simply not legal to transmit signals that are very strong, very long, or occupy very wide bandwidth. To give an example, the ETSI (European Telecommunications Standards Institute) regulations say that in for radio transmitters in Europe operating in the frequency from 865 MHz to 868 MHz, the maximum transmission duty cycle is 1%, and the maximum strength is 14 dBm. There are both national and international organizations that control the spectrum usage in each country. Since jamming is an active attack, it is always possible to detect and find the source of the jam signal. Violating the relevant laws may get you fined, or worse.
但是,足够先进的攻击者将始终能够使用足够宽带,足够长和足够强的干扰信号简单地淹没物联网网络中的通信。 无法使用任何特定技术来完全抵抗这种攻击。 通常在这种情况下,后备措施是通过法律行动加以应对。 具体的法律因每个频段而异,但是通常来说,传输非常强,非常长或占用非常宽的带宽的信号完全不合法。 举个例子,欧洲电信标准协会(ETSI)规定说,对于在865 MHz至868 MHz频率下工作的欧洲无线电发射机,最大传输占空比为1%,最大强度为14 dBm。 有国家和国际组织来控制每个国家的频谱使用。 由于干扰是主动攻击,因此始终可以检测并找到干扰信号的来源。 违反相关法律可能会被罚款,甚至更糟。
中间人攻击 (Man-in-the-middle attacks)
Jamming and sniffing can be combined to create a man-in-the-middle (MITM) attack. First, the attacker jams an existing connection. The connection can be between IoT devices, or between an IoT device and an external device. For the sake of the example, let’s pick a wearable device (smartwatch) connecting to a mobile phone.
可以将干扰和嗅探结合在一起以创建中间人(MITM)攻击。 首先,攻击者阻塞了现有连接。 连接可以在IoT设备之间,也可以在IoT设备与外部设备之间。 为了举例说明,让我们选择一个连接到手机的可穿戴设备(智能手表)。
The attacker then sniffs the packets coming from the devices trying to re-establish the connection. Based on the information collected via the sniffing or obtained otherwise (if the packets are encrypted, for example), the attacker is able to impersonate both devices. On the wearable device side, the attacker impersonates the mobile phone. On the phone side, the attacker impersonates the wearable device.
然后,攻击者会嗅探来自设备的数据包,以尝试重新建立连接。 基于通过嗅探收集的信息或以其他方式获得的信息(例如,如果数据包已加密),攻击者便可以冒充这两个设备。 在可穿戴设备方面,攻击者冒充了手机。 在电话方面,攻击者冒充了可穿戴设备。
The attacker can now pass data between the wearable device and phone. They have full access to the data — and without any of the devices being aware of what is happening. Moreover, they can selectively drop some packets, or insert new packets in the connection.
攻击者现在可以在可穿戴设备和手机之间传递数据。 他们具有对数据的完全访问权限-并且没有任何设备知道发生了什么。 而且,他们可以有选择地丢弃某些数据包,或在连接中插入新的数据包。
Some IoT protocols are vulnerable to the MITM attack by design. For example, the Bluetooth standard (version 4.0+) describes the Secure Simple Pairing (SSP) mechanism that allows to establish encrypted connection between multiple devices. This mechanism comes in four varieties. Three of these varieties which do protect against the MITM attack, but the remaining one, called “Just Works” offers no MITM protection, just protection against simple sniffing. Hence, it should not be used in security-sensitive applications.
某些IoT协议在设计上容易受到MITM攻击。 例如,蓝牙标准(版本4.0+)描述了安全简单配对(SSP)机制,该机制允许在多个设备之间建立加密连接。 此机制有四个变体。 其中有三种确实可以抵御MITM攻击,但是其余的一种叫做“ Just Works”,它没有提供MITM防护,只是提供了防止简单嗅探的保护。 因此,不应在对安全敏感的应用程序中使用它。
物联网加密和认证 (IoT encryption and authentication)
The asymmetry of attack and defense capabilities in IoT networks 物联网网络中攻击和防御能力的不对称性To me, the most amazing thing about IoT security is that encryption and authentication works at all. There is an astonishing power asymmetry between the defender, which may be a battery-powered IoT device capable of a few million operations per second, and the potential attackers, which may be supercomputers that are billions of times more powerful. However, to the best our current knowledge, no realistic attack is known affect the encryption and authentication cryptographic primitives that are currently used in IoT.
对我来说,物联网安全性最令人惊奇的事情是加密和身份验证完全起作用。 在防御者和潜在的攻击者之间可能存在惊人的功率不对称性,防御者可能是每秒能进行数百万次操作的电池供电的物联网设备,而潜在的攻击者可能是功能强大数十亿倍的超级计算机。 但是,就我们目前所知,没有已知的现实攻击会影响物联网中当前使用的加密和身份验证密码原语。
On the other hand, the actual IoT protocols are often vulnerable to various attacks due to the cryptographic primitives being used in less-than-perfect way. Similarly, key exchange is still not considered a solved problem in the context of IoT. It difficult to authenticate the devices for key distribution due to the scale of IoT networks; it even more difficult to keep the keys up-to-date as reprogramming and updating the IoT devices is often very difficult and sometime not even part of the operational budget.
另一方面,由于使用的加密原语不够完美,实际的物联网协议通常容易受到各种攻击。 同样,在物联网环境下,密钥交换仍未被视为已解决的问题。 由于物联网网络的规模,很难对用于密钥分发的设备进行身份验证; 由于对IoT设备进行重新编程和更新通常非常困难,有时甚至不属于运营预算的一部分,因此使密钥保持最新状态甚至更加困难。
Most IoT devices include some hardware components for accelerating cryptographic operations. Hardware acceleration allows to run the cryptographic primitives at a fraction of time and energy required to do the same operations in software. AES accelerators are especially common. Elliptic curve cryptography and hash functions (SHA-2) are also often accelerated. Elliptic curve are used to implement more light-weight alternatives to RSA, which is a prime-number based asymmetric cryptography algorithm and not highly used in the IoT context. In the future, more devices that include SHA-3 accelerators are expected.
大多数物联网设备包括一些用于加速加密操作的硬件组件。 硬件加速允许在软件中执行相同操作所需的时间和精力的一小部分上运行密码原语。 AES加速器尤其常见。 椭圆曲线加密和哈希函数(SHA-2)也经常被加速。 椭圆曲线用于实现RSA的更轻量级替代方案,后者是基于质数的非对称密码算法,在IoT上下文中使用率不高。 将来,预计会有更多包含SHA-3加速器的设备。
物联网网络与传统网络安全 (IoT network vs. traditional network security)
Compared with traditional wired networks, IoT networks are:• Man-in-the-middle, replay attacks — similarly severely vulnerable• Spoofing attacks — equally severely vulnerable• Denial of Service (DoS) attacks — more severely vulnerable• Sniffing — more severely vulnerable• Jamming — additionally vulnerable• Physical attacks — more severely vulnerable
与传统的有线网络相比,IoT网络具有:•中间人重放攻击-同样严重脆弱•欺骗攻击-同样严重脆弱•拒绝服务(DoS)攻击-更严重脆弱•嗅探-更严重脆弱•干扰-更加脆弱•物理攻击-更加严重
In short, IoT networks are vulnerable to all of the problems traditional networks, at least equally severely and in some cases more severely. Furthermore, they are additionally vulnerable to jamming attacks.
简而言之,物联网网络易受传统网络的所有问题的影响,至少同样严重,有时甚至更严重。 此外,它们还容易受到干扰攻击。
结论 (Conclusion)
It is clear that IoT security is not a fully solved research field. To sum up the current state:• The basics such as encryption and authentication work well. Things may change when the current algorithms are broken by quantum computers or by clever cryptographers (only asymmetric cryptography is vulnerable to the former), however, this challenge is not unique to IoT, and better & quantum-safe cryptographic algorithms are constantly being developed.• IoT security faces several additional difficulties compared with traditional wired networks. These difficulties mostly are due to the resource limitations on devices, wireless communication being used, operational complexity, network scale, and deployment longevity.• There are some open or partially solved challenges in IoT security, namely, secure key distribution, motivating users to keep their devices secure, and physical security.• More strict legislation and regulation may be needed. Some experts such as Bruce Schneier believe that a “free market” approach is not going to deliver good results in the IoT security field and that companies should be mandated by law to pay more attention to the security of their devices, including long support plans with automated security bugfixes being rolled out continuously.
显然,物联网安全性不是一个完全解决的研究领域。 总结当前状态:•诸如加密和身份验证之类的基础知识运行良好。 当当前的算法被量子计算机或聪明的密码学家破坏时,情况可能会发生变化(只有非对称密码技术才容易受到前者的攻击),但是,这一挑战并非物联网所独有,并且不断开发出更好的量子安全密码算法。 •与传统的有线网络相比,物联网安全性面临更多的困难。 这些困难主要是由于设备资源限制,正在使用的无线通信,操作复杂性,网络规模和部署寿命等原因造成的。• IoT安全中存在一些开放或部分解决的挑战,即安全密钥分发,促使用户保持安全它们的设备具有安全性和物理安全性。•可能需要更严格的法规。 布鲁斯·施耐尔(Bruce Schneier)等一些专家认为,“自由市场”方法不会在IoT安全领域取得良好的效果,法律应授权公司更加关注其设备的安全性,包括长期支持计划以及不断推出的自动化安全错误修正。
翻译自: https://medium.com/swlh/internet-of-things-networks-and-their-security-aa8db50202aa
物联网网络安全