Linux安装Metasploit与简单介绍
1 CentOS安装metasploit
切换到root命令
依次执行以下两句
[root@localhost ~]# cd /opt
[root@localhost opt]# curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && chmod 755 msfinstall && ./msfinstall
执行命令的结果
[root@localhost ~]# cd /opt
[root@localhost opt]# curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/me tasploit-framework-wrappers/msfupdate.erb > msfinstall && chmod 755 msfinstall && ./msfinstall
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 6034 100 6034 0 0 1428 0 0:00:04 0:00:04 --:--:-- 1429
Checking for and installing update..
Adding metasploit-framework to your repository list..Loaded plugins: fastestmirror, langpacks
base | 3.6 kB 00:00:00
extras | 2.9 kB 00:00:00
metasploit | 3.0 kB 00:00:00
updates | 2.9 kB 00:00:00
(1/2): metasploit/primary_db | 12 kB 00:00:01
(2/2): updates/7/x86_64/primary_db | 16 MB 00:00:03
Loading mirror speeds from cached hostfile
* base: mirrors.aliyun.com
* extras: mirrors.aliyun.com
* updates: mirrors.aliyun.com
Resolving Dependencies
--> Running transaction check
---> Package metasploit-framework.x86_64 0:6.2.9+20220728102816~1rapid7-1.el6 will be installed
--> Finished Dependency Resolution
Dependencies Resolved
=================================================================================================================
Package Arch Version Repository Size
=================================================================================================================
Installing:
metasploit-framework x86_64 6.2.9+20220728102816~1rapid7-1.el6 metasploit 269 M
Transaction Summary
=================================================================================================================
Install 1 Package
Total download size: 269 M
Installed size: 635 M
Downloading packages:
warning: /var/cache/yum/x86_64/7/metasploit/packages/metasploit-framework-6.2.9+20220728102816~1rapid7-1.el6.x86_ 64.rpm: Header V4 RSA/SHA256 Signature, key ID 2007b954: NOKEY
Public key for metasploit-framework-6.2.9+20220728102816~1rapid7-1.el6.x86_64.rpm is not installed
metasploit-framework-6.2.9+20220728102816~1rapid7-1.el6.x86_64.rpm | 269 MB 00:00:19
Retrieving key from file:///etc/pki/rpm-gpg/RPM-GPG-KEY-Metasploit
Importing GPG key 0x2007B954:
Userid : "Metasploit "
Fingerprint: 09e5 5faf 4f78 62cd 6d55 8997 cdfb 5fa5 2007 b954
From : /etc/pki/rpm-gpg/RPM-GPG-KEY-Metasploit
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : metasploit-framework-6.2.9+20220728102816~1rapid7-1.el6.x86_64 1/1
Run msfconsole to get started
Verifying : metasploit-framework-6.2.9+20220728102816~1rapid7-1.el6.x86_64 1/1
Installed:
metasploit-framework.x86_64 0:6.2.9+20220728102816~1rapid7-1.el6
Complete!
安装完成
用ls命令查看目录结构
[root@localhost opt]# ls
metasploit-framework msfinstall rh
[root@localhost opt]# ls ./metasploit-framework
bin embedded LICENSE LICENSES version-manifest.json version-manifest.txt
[root@localhost opt]# ls metasploit-framework
bin embedded LICENSE LICENSES version-manifest.json version-manifest.txt
启动控制台
[root@localhost opt]# msfconsole
______________________________________________________________________________
| |
| METASPLOIT CYBER MISSILE COMMAND V5 |
|______________________________________________________________________________|
\ / /
\ . / / x
\ / /
\ / + /
\ + / /
* / /
/ . /
X / / X
/ ###
/ # % #
/ ###
. /
. / . * .
/
*
+ *
^
#### __ __ __ ####### __ __ __ ####
#### / \ / \ / \ ########### / \ / \ / \ ####
################################################################################
################################################################################
# WAVE 5 ######## SCORE 31337 ################################## HIGH FFFFFFFF #
################################################################################
https://metasploit.com
=[ metasploit v6.2.9-dev- ]
+ -- --=[ 2230 exploits - 1177 auxiliary - 398 post ]
+ -- --=[ 864 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: View a module's description using
info, or the enhanced version in your browser with
info -d
msf6 > Interrupt: use the 'exit' command to quit
msf6 >
启动成功! metasploit v6.2.9-dev-
2 扩展——虚拟机安装Kali操作系统
Kali操作系统内置metasploit
2.1 Kali OS安装
下载64bit稳定版iso(https://www.kali.org/get-kali/#kali-bare-metal)

文件比较大,下载太慢,在阿里云镜像开源(https://mirrors.aliyun.com/kali-images/current/)中下载
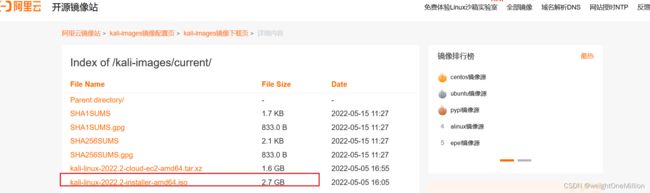 下载之后,利用vm虚拟机安装iso文件即可(https://blog.csdn.net/Python_caoboqiao/article/details/124284383)。
下载之后,利用vm虚拟机安装iso文件即可(https://blog.csdn.net/Python_caoboqiao/article/details/124284383)。
这里还有虚拟机资源kali-virtual

安装完成,启动msfconsole

2.2 kali更新msf
2.3Kali安装MSF图形化界面Viper
首先需要安装docker
apt-get update
# 使用apt安装docker
apt-get install -y docker.io
# 设置开机自启动
systemctl start docker
# 检测docker状态
docker version
安装docker-compose
# 拉脚本
curl -L https://get.daocloud.io/docker/compose/releases/download/1.25.5/docker-compose-`uname -s`-`uname -m` > /usr/bin/docker-compose
#赋可执行权限
chmod +x /usr/bin/docker-compose
安装启动Viper
# 设置Viper安装目录
export VIPER_DIR=/root/VIPER
# 生成安装目录 并进入目录
mkdir -p $VIPER_DIR && cd $VIPER_DIR
# 执行如下命令生成docker-compose.yml
tee docker-compose.yml <<-'EOF'
version: "3"
services:
viper:
image: registry.cn-shenzhen.aliyuncs.com/toys/viper:latest
container_name: viper-c
network_mode: "host"
restart: always
volumes:
- ${PWD}/loot:/root/.msf4/loot
- ${PWD}/db:/root/viper/Docker/db
- ${PWD}/module:/root/viper/Docker/module
- ${PWD}/log:/root/viper/Docker/log
- ${PWD}/nginxconfig:/root/viper/Docker/nginxconfig
command: ["VIPER_PASSWORD"]
EOF
设置登录密码
Viper不允许使用默认密码,diypassword替换为自定义密码密码且大于8位
export VIPER_PASSWORD=123456
写入密码到docker-compose.yml
sed -i "s/VIPER_PASSWORD/$VIPER_PASSWORD/g" docker-compose.yml
使用命令查看配置(目录如下:/root/VIPER/docker-compose.yml)
cat docker-compose.yml
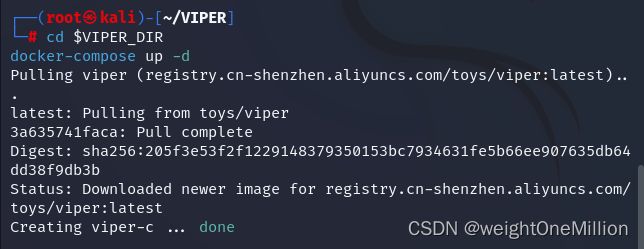
# 进入viper的目录($VIPER_DIR=/root/VIPER),第一次访问比较慢,需要下载一个G的文件
cd $VIPER_DIR
docker-compose up -d
# 启动viper
docker-compose start
所有的docker-compose命令必须在安装目录执行才会有效果
等待15s系统启动,访问 https://你的ip地址:60000 登录. 用户名:root 密码:刚才写入的密码
使用:ip a 命令查询自己的ip
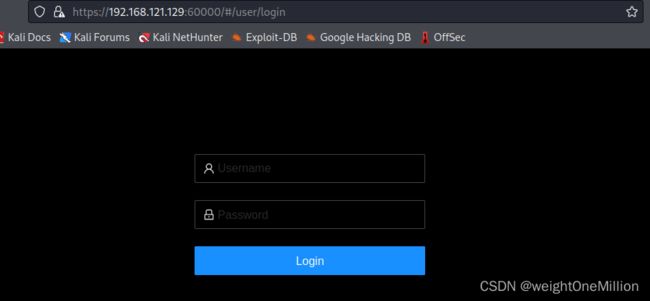
输入用户名密码,登录
进入如下界面(右侧切换中文)
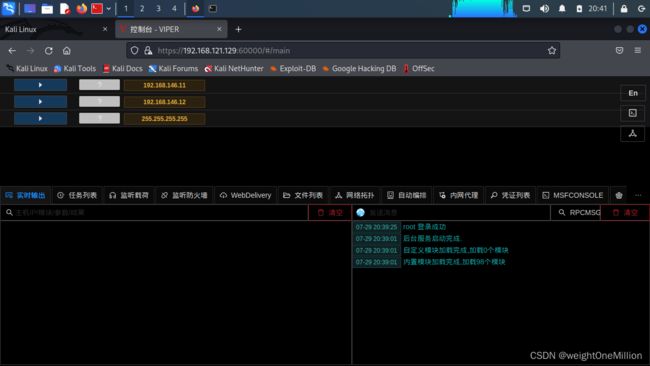 至此,安装成功!
至此,安装成功!
参考
Linux centos 安装metasploit(就两步):https://blog.csdn.net/FY10033/article/details/118439981
详细安装 kali 教程:https://blog.csdn.net/Python_caoboqiao/article/details/124284383
Metasploit图形界面Viper安装:https://blog.csdn.net/qq_45455136/article/details/123913044
MSF图形化界面Viper(炫彩蛇)下载与使用:https://blog.csdn.net/weixin_42489549/article/details/117514558?spm=1001.2101.3001.6650.2&utm_medium=distribute.pc_relevant.none-task-blog-2%7Edefault%7ECTRLIST%7Edefault-2-117514558-blog-123913044.pc_relevant_aa_2&depth_1-utm_source=distribute.pc_relevant.none-task-blog-2%7Edefault%7ECTRLIST%7Edefault-2-117514558-blog-123913044.pc_relevant_aa_2&utm_relevant_index=5