Istio安装与部署
本次环境搭建使用的Kubernetes版本为1.18.0,Istio版本为1.11.2
Kubernetes环境搭建参考:Kubernetes集群环境搭建&部署Dashboard
1、Istio安装
https://github.com/istio/istio/releases/tag/1.11.2下载Istio 1.11.2安装包
1)安装目录
[root@k8s-master istio-1.11.2]# ls
bin LICENSE manifests manifest.yaml README.md samples tools
解压后可以看到有4个目录(bin、manifests、samples、tools)及3个文件(LICENSE、README.md、manifest.yaml)
其中bin下是istioctl执行程序,manifests是Istio相关的主要部署组件,manifest.yaml是当前Istio版本中manifests目录下各组件的配置和依赖描述,samples是一套Istio应用样例,用来部署测试做功能校验的,tools是一些工具脚本
2)把istioctl加入环境变量
/etc/profile文件中添加:
export ISTIO_HOME=/istio-1.11.2
export PATH=$ISTIO_HOME/bin:$PATH
添加完毕后,加载配置使配置生效:
source /etc/profile
验证环境变量是否生效:
[root@k8s-master istio-1.11.2]# istioctl version
no running Istio pods in "istio-system"
1.11.2
3)使用demo配置安装Istio
istioctl install --set profile=demo -y
查看服务是否部署正常:
[root@k8s-master istio-1.11.2]# kubectl get pod -n istio-system
NAME READY STATUS RESTARTS AGE
istio-egressgateway-7784dc7fd4-plgpb 1/1 Running 0 6m17s
istio-ingressgateway-575fd95f88-8hpg6 1/1 Running 0 6m17s
istiod-6785d97f67-5mth2 1/1 Running 0 6m32s
2、部署Bookinfo示例
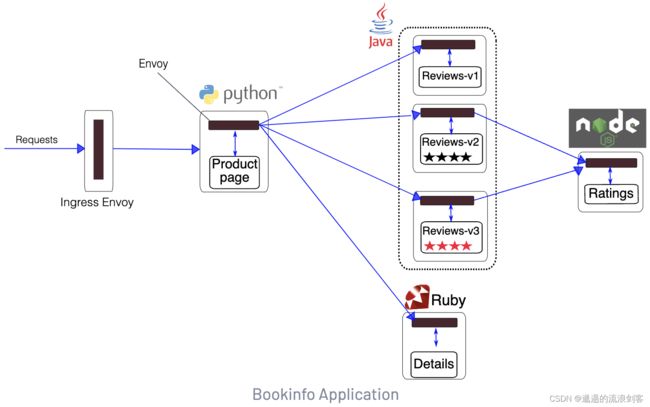
1)、Bookinfo应用说明
Bookinfo应用由4个单独的微服务构成:
- productpage会调用details和reviews两个微服务,用来生成页面
- details中包含了书籍的信息
- reviews中包含了书籍相关的评论。它还会调用ratings微服务
- ratings中包含了由书籍评价组成的评级信息
reviews微服务有3个版本:
- v1版本不会调用ratings服务
- v2版本会调用ratings服务,并使用1到5个黑色星形图标来显示评分信息
- v3版本会调用ratings服务,并使用1到5个红色星形图标来显示评分信息
下图展示了这个应用的端到端架构。Bookinfo应用中的几个微服务是由不同的语言编写的。 这些服务对Istio并无依赖,但是构成了一个有代表性的服务网格的例子:它由多个服务、多个语言构成,并且reviews服务具有多个版本
2)、部署Bookinfo
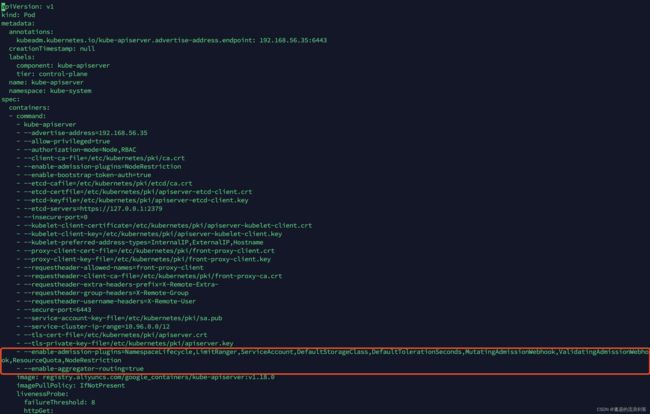
1)修改kube-apiserver启动参数
使用Kubernetes版本为1.18.0时,出现不能自动注入Sidecar的情况,报错信息如下:
Error creating: Internal error occurred: failed calling webhook "namespace.sidecar-injector.istio.io": Post https://istiod.istio-system.svc:443/inject?timeout=10s: context deadline exceeded
Error creating: Internal error occurred: failed calling webhook "namespace.sidecar-injector.istio.io": Post https://istiod.istio-system.svc:443/inject?timeout=10s: dial tcp 10.111.153.53:443: i/o timeout
需要修改kube-apiserver启动参数:
vi /etc/kubernetes/manifests/kube-apiserver.yaml
添加如下参数:
- --enable-admission-plugins=NamespaceLifecycle,LimitRanger,ServiceAccount,DefaultStorageClass,DefaultTolerationSeconds,MutatingAdmissionWebhook,ValidatingAdmissionWebhook,ResourceQuota,NodeRestriction
- --enable-aggregator-routing=true
2)default命名空间打标签
为default命名空间打上istio-injection=enabled标签,Istio自动注入Sidecar:
kubectl label namespace default istio-injection=enabled
3)部署Bookinfo
kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml
确认所有Pod正常启动:
[root@k8s-master istio-1.11.2]# kubectl get pod -n default
NAME READY STATUS RESTARTS AGE
details-v1-66b6955995-bjx2l 2/2 Running 0 3m1s
productpage-v1-5d9b4c9849-f6lds 2/2 Running 0 3m
ratings-v1-fd78f799f-wgbk6 2/2 Running 0 3m1s
reviews-v1-6549ddccc5-fsvbk 2/2 Running 0 3m
reviews-v2-76c4865449-td7rq 2/2 Running 0 3m
reviews-v3-6b554c875-67p26 2/2 Running 0 3m
4)对外开放Bookinfo
为应用程序定义Ingress网关:
kubectl apply -f samples/bookinfo/networking/bookinfo-gateway.yaml
确认网关创建完成:
[root@k8s-master istio-1.11.2]# kubectl get gateway -n=default
NAME AGE
bookinfo-gateway 30s
[root@k8s-master istio-1.11.2]# kubectl get svc -n=istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
istio-egressgateway ClusterIP 10.101.87.50 <none> 80/TCP,443/TCP 41m
istio-ingressgateway LoadBalancer 10.97.98.18 <pending> 15021:31896/TCP,80:31023/TCP,443:30496/TCP,31400:32584/TCP,15443:32442/TCP 41m
istiod ClusterIP 10.111.153.53 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 41m
将istio-ingressgateway Service的Type修改为NodePort:
[root@k8s-master istio-1.11.2]# kubectl edit svc istio-ingressgateway -n=istio-system
[root@k8s-master istio-1.11.2]# kubectl get svc -n=istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
istio-egressgateway ClusterIP 10.101.87.50 <none> 80/TCP,443/TCP 43m
istio-ingressgateway NodePort 10.97.98.18 <none> 15021:31896/TCP,80:31023/TCP,443:30496/TCP,31400:32584/TCP,15443:32442/TCP 43m
istiod ClusterIP 10.111.153.53 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 43m
浏览器访问http://192.168.56.35:31023/productpage(使用对应的NodeIp和NodePort)
3、安装Kiali和其他插件
kubectl apply -f samples/addons
确认所有Pod正常启动:
[root@k8s-master istio-1.11.2]# kubectl get pod -n istio-system
NAME READY STATUS RESTARTS AGE
grafana-6544947b77-qmg6k 1/1 Running 0 6m30s
istio-egressgateway-7784dc7fd4-plgpb 1/1 Running 0 68m
istio-ingressgateway-575fd95f88-8hpg6 1/1 Running 0 68m
istiod-6785d97f67-5mth2 1/1 Running 0 68m
jaeger-7f8cd55b4c-thdgg 1/1 Running 0 6m30s
kiali-74ff4c79f9-6wtd5 1/1 Running 0 6m30s
prometheus-6cfc5f58cd-7s44r 2/2 Running 0 6m29s
[root@k8s-master istio-1.11.2]# kubectl get svc -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
grafana ClusterIP 10.99.220.97 <none> 3000/TCP 14s
istio-egressgateway ClusterIP 10.101.87.50 <none> 80/TCP,443/TCP 62m
istio-ingressgateway NodePort 10.97.98.18 <none> 15021:31896/TCP,80:31023/TCP,443:30496/TCP,31400:32584/TCP,15443:32442/TCP 62m
istiod ClusterIP 10.111.153.53 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 62m
jaeger-collector ClusterIP 10.102.134.168 <none> 14268/TCP,14250/TCP,9411/TCP 13s
kiali ClusterIP 10.102.76.98 <none> 20001/TCP,9090/TCP 13s
prometheus ClusterIP 10.101.246.75 <none> 9090/TCP 12s
tracing ClusterIP 10.104.145.15 <none> 80/TCP,16685/TCP 13s
zipkin ClusterIP 10.104.30.51 <none> 9411/TCP 13s
将kiali Service的Type修改为NodePort:
kubectl edit svc kiali -n istio-system
[root@k8s-master istio-1.11.2]# kubectl get svc -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
grafana ClusterIP 10.99.220.97 <none> 3000/TCP 7m30s
istio-egressgateway ClusterIP 10.101.87.50 <none> 80/TCP,443/TCP 69m
istio-ingressgateway NodePort 10.97.98.18 <none> 15021:31896/TCP,80:31023/TCP,443:30496/TCP,31400:32584/TCP,15443:32442/TCP 69m
istiod ClusterIP 10.111.153.53 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 69m
jaeger-collector ClusterIP 10.102.134.168 <none> 14268/TCP,14250/TCP,9411/TCP 7m29s
kiali NodePort 10.102.76.98 <none> 20001:30141/TCP,9090:31080/TCP 7m29s
prometheus ClusterIP 10.101.246.75 <none> 9090/TCP 7m28s
tracing ClusterIP 10.104.145.15 <none> 80/TCP,16685/TCP 7m29s
zipkin ClusterIP 10.104.30.51 <none> 9411/TCP 7m29s
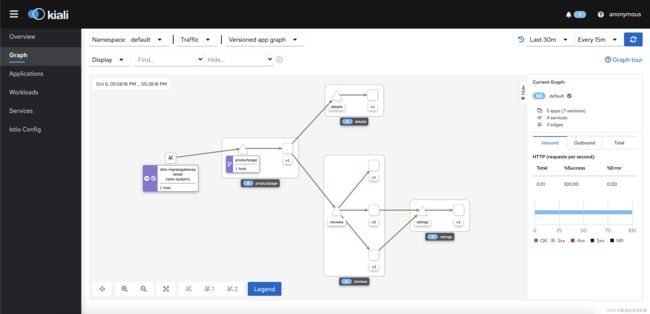
浏览器访问http://192.168.56.35:30141(使用对应的NodeIp和NodePort)
在kiali页面中展示了流量的访问关系: