nmap教程—1—确定目标
文章目录
- 一、指定单一主机
-
- 1. Ip地址
- 2. 域名
- 二、指定多个主机
-
- 1. CIDR格式
- 2. 连续的主机
- 3. 不连续的主机
- 4.使用列表文件
- 5. 指定扫描主机的所有IP地址
- 三、排除主机被扫描
- 四、使用随机主机方式实施扫描
- 五、扫描方式
-
- 1. 全部扫描
- 2. 发包模式
- 3. 恢复扫描
一、指定单一主机
1. Ip地址
ifconfig
nmap [通过ifconfig查看本机ip]
hostname
nmap [通过hostname查看主机名]
2. 域名
--dns-servers:指定特定的DNS服务器地址--system-dns:使用操作系统的DNS解析器
┌──(rootkali)-[~]
└─# nmap --dns-servers 114.114.114.114 www.baidu.com
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 02:40 CST
Nmap scan report for www.baidu.com (180.101.49.12)
Host is up (0.0055s latency).
Other addresses for www.baidu.com (not scanned): 180.101.49.11
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 37.46 seconds
┌──(rootkali)-[~]
└─# nmap --system-dns www.baidu.com
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 02:41 CST
Nmap scan report for www.baidu.com (180.101.49.11)
Host is up (0.0050s latency).
Other addresses for www.baidu.com (not scanned): 180.101.49.12
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 4.72 seconds
二、指定多个主机
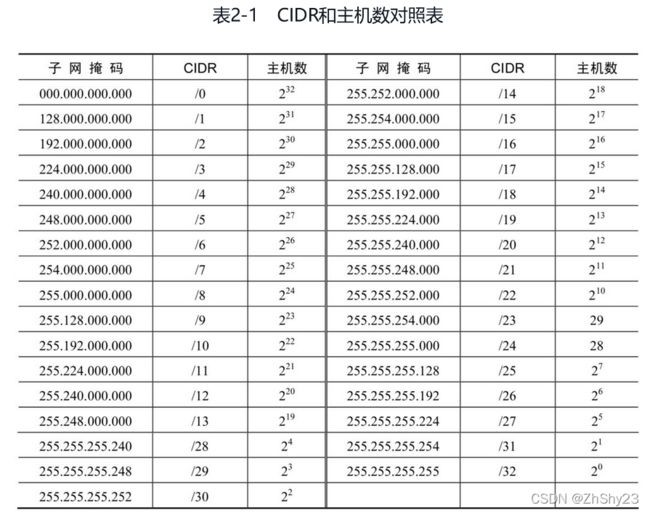
1. CIDR格式
-
CIDR换算
组成:网络地址/子网掩码
使用格式:IP/掩码长度(192.168.1.0/24),主机名/掩码长度(baidu.com/24)netmask [options] [address]在以上语法中,options参数表示可用的选项,address用于指定计算的地址。
netmask工具支持的选项及其含义如下:-d,--debug:显示调试信息。-s,--standard:输出“地址/掩码对”。-c,--cidr:输出CIDR格式地址列表。-i,--cisco:输出Cisco类地址列表。-r,--range:输出一个IP地址范围。-x,--hex:以十六进制格式输出“地址/掩码对”。-o,--octal:以十进制格式输出“地址/掩码对”。-b,--binary:以二进制格式输出“地址/掩码对”。-n,--nodns:禁用DNS查询。
查看CIDR地址10.10.10.0/8对应的网络范围:共有16777216个主机 ┌──(rootkali)-[~] └─# netmask -r 10.10.10.0/8 10.0.0.0-10.255.255.255 (16777216) 查看地址范围192.168.1.0=255对应的CIDR值:192.168.1.0/24 ┌──(rootkali)-[~] └─# netmask -c 192.168.1.0:192.168.1.255 192.168.1.0/24 -
验证扫描目标
语法:nmap -sL [address] 列出扫描的目标验证192.168.1.0/24范围的目标主机列表。由于掩码长度为24,因此主机数为256,范围是192.168.1.0到192.168.1.255。 ┌──(rootkali)-[~] └─# nmap -sL 192.168.1.0/24 Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 03:03 CST Nmap scan report for 192.168.1.0 Nmap scan report for 192.168.1.1 Nmap scan report for 192.168.1.2 Nmap scan report for 192.168.1.3 Nmap scan report for 192.168.1.4 Nmap scan report for 192.168.1.5 Nmap scan report for 192.168.1.6 Nmap scan report for 192.168.1.7 Nmap scan report for 192.168.1.8 Nmap scan report for 192.168.1.9 Nmap scan report for 192.168.1.10 ........ Nmap scan report for 192.168.1.250 Nmap scan report for 192.168.1.251 Nmap scan report for 192.168.1.252 Nmap scan report for 192.168.1.253 Nmap scan report for 192.168.1.254 Nmap scan report for 192.168.1.255 Nmap done: 256 IP addresses (0 hosts up) scanned in 2.14 seconds
2. 连续的主机
指定连续的主机IP地址为192.168.198.100到192.168.198.110
┌──(rootkali)-[~]
└─# nmap -sL 192.168.198.100-110
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 20:09 CST
Nmap scan report for 192.168.198.100
Nmap scan report for 192.168.198.101
Nmap scan report for 192.168.198.102
Nmap scan report for 192.168.198.103
Nmap scan report for 192.168.198.104
Nmap scan report for 192.168.198.105
Nmap scan report for 192.168.198.106
Nmap scan report for 192.168.198.107
Nmap scan report for 192.168.198.108
Nmap scan report for 192.168.198.109
Nmap scan report for 192.168.198.110
Nmap done: 11 IP addresses (0 hosts up) scanned in 0.02 seconds
3. 不连续的主机
IP地址之间使用空格分隔
指定扫描主机192.168.198.132和192.168.198.134
┌──(rootkali)-[~]
└─# nmap -sL 192.168.198.132 192.168.198.134
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 20:11 CST
Nmap scan report for 192.168.198.132
Nmap scan report for 192.168.198.134
Nmap done: 2 IP addresses (0 hosts up) scanned in 0.01 seconds
4.使用列表文件
语法:
-iL <inputfilename>:指定主机或网络列表文件。
使用列表文件制定多个目标主机
- 将扫描的目标主机写入hosts.txt文件
首先vim编辑hosts.txt文件,写入ip ┌──(rootkali)-[~] └─# cat hosts.txt 198.168.198.132 198.168.198.134 198.168.198.135 - 指定列表文件hosts.txt进行扫描
┌──(rootkali)-[~] └─# nmap -iL hosts.txt -sL Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 20:26 CST Nmap scan report for 198.168.198.132 Nmap scan report for 198.168.198.134 Nmap scan report for 198.168.198.135 Nmap done: 3 IP addresses (0 hosts up) scanned in 0.56 seconds
5. 指定扫描主机的所有IP地址
在DNS服务器中,一个域名可以解析到多个IP地址。如果一个域名有多个IP地址时,Nmap默认仅探测第一个IP地址。为了能够探测到所有的IP地址,可以使用--resolve-all选项指定扫描主机中的所有IP地址。
扫描主机www.baidu.com中的所有ip地址
┌──(rootkali)-[~]
└─# nmap --resolve-all www.baidu.com -sL
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 20:28 CST
Nmap scan report for www.baidu.com (180.101.49.11)
Nmap scan report for www.baidu.com (180.101.49.12)
Nmap done: 2 IP addresses (0 hosts up) scanned in 0.21 seconds
从输出信息中可以看到,成功扫描出了目标主机www.baidu.com中的所有IP地址。其中,该主机对应两个IP地址,分别是180.101.49.11和180.101.49.12。
三、排除主机被扫描
当用户在扫描主机时,为了方便输入,可以使用CIDR格式直接指定整个网络或连续的网段。如果在该网络中有一些主机不需要扫描,比如该主机自身、防火墙设备或重要的主机等,为了提高扫描效率,那么可以排除这些主机。
Nmap提供了两个选项用来排除主机被扫描。这两个选项及其含义如下:
--exclude <host1,host2...>:指定排除的主机。其中,用户可以指定排除单个目标、多个目标或一个目标范围。
--excludefile <exclude_file>:指定排除的主机文件列表。
扫描192.168.198.0/24网络中的所有主机,但是不扫描192.168.1-100范围内的主机
┌──(rootkali)-[~]
└─# nmap 192.168.198.0/24 --exclude 192.168.198.0-100 -sL
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 20:34 CST
Nmap scan report for 192.168.198.101
Nmap scan report for 192.168.198.102
Nmap scan report for 192.168.198.103
Nmap scan report for 192.168.198.104
Nmap scan report for 192.168.198.105
Nmap scan report for 192.168.198.106
Nmap scan report for 192.168.198.107
Nmap scan report for 192.168.198.108
Nmap scan report for 192.168.198.109
Nmap scan report for 192.168.198.110
......
Nmap scan report for 192.168.198.250
Nmap scan report for 192.168.198.251
Nmap scan report for 192.168.198.252
Nmap scan report for 192.168.198.253
Nmap scan report for 192.168.198.254
Nmap scan report for 192.168.198.255
Nmap done: 155 IP addresses (0 hosts up) scanned in 2.10 seconds
从最后一行信息中可以看到,扫描的目标主机地址有155个,即排除了100个目标主机(192.168.198.0-100)。从显示的目标列表中可以看到,扫描的目标地址为192.168.1. 101-255。
四、使用随机主机方式实施扫描
如果没有一个合适的目标主机,可以使用随机主机方式来实施扫描。Nmap提供了一个选项-iR,用于指定随机扫描的主机数并进行扫描。
-iR <num hosts>:指定随机扫描的主机数,指定的参数值必须是一个整数,如果指定值为0,则表示一直扫描。
使用Nmap随机扫描5个主机
┌──(rootkali)-[~]
└─# nmap -iR 5 -sL
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 20:37 CST
Nmap scan report for 66.151.63.45
Nmap scan report for 42.7.156.124
Nmap scan report for host-81-119-5-48.business.telecomitalia.it (81.119.5.48)
Nmap scan report for 1.183.121.68
Nmap scan report for 48.45.210.68
Nmap done: 5 IP addresses (0 hosts up) scanned in 2.67 seconds
[当再次执行该命令时,将会重新随机生成5个不同的IP地址]
┌──(rootkali)-[~]
└─# nmap -iR 5 -sL
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 20:39 CST
Nmap scan report for 125.182.218.88
Nmap scan report for 2-107-168-188-static.dk.customer.tdc.net (2.107.168.188)
Nmap scan report for 65-33-187-26.res.bhn.net (65.33.187.26)
Nmap scan report for 139.251.136.26
Nmap scan report for 129.238.212.216
Nmap done: 5 IP addresses (0 hosts up) scanned in 5.06 seconds
五、扫描方式
1. 全部扫描
-A :[实施全部扫描,以探测目标主机的操作系统和版本信息]
将对目标主机220.181.38.251实施全部扫描
┌──(rootkali)-[~]
└─# nmap -A 220.181.38.251
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 20:47 CST
Nmap scan report for 220.181.38.251
Host is up (0.0079s latency).
# 主机状态
Not shown: 998 filtered tcp ports (no-response)
# 关闭的端口
PORT STATE SERVICE VERSION
# 开放的端口
80/tcp open http Apache httpd
|_http-title: Site doesn't have a title (text/html).
| http-robots.txt: 8 disallowed entries
|_/baidu /s? /ulink? /link? /shifen/ /homepage/ /cpro /
|_http-server-header: Apache
443/tcp open ssl/http Baidu Front End httpd 1.0.8.18
| tls-nextprotoneg:
| spdy/3.1
|_ http/1.1
|_http-title: 405 Not Allowed
| ssl-cert: Subject: commonName=www.baidu.cn/organizationName=BeiJing Baidu Netcom Science Technology Co., Ltd/stateOrProvinceName=Beijing/countryName=CN
| Subject Alternative Name: DNS:www.baidu.cn, DNS:baidu.cn, DNS:baidu.com, DNS:baidu.com.cn, DNS:w.baidu.com, DNS:ww.baidu.com, DNS:www.baidu.com.cn, DNS:www.baidu.com.hk, DNS:www.baidu.hk, DNS:www.baidu.net.au, DNS:www.baidu.net.ph, DNS:www.baidu.net.tw, DNS:www.baidu.net.vn, DNS:wwww.baidu.com, DNS:wwww.baidu.com.cn
| Not valid before: 2022-02-11T00:00:00
|_Not valid after: 2023-02-25T23:59:59
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
|_http-server-header: bfe/1.0.8.18
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: WAP|general purpose
Running: Actiontec embedded, Linux 2.4.X
OS CPE: cpe:/h:actiontec:mi424wr-gen3i cpe:/o:linux:linux_kernel cpe:/o:linux:linux_kernel:2.4.37
OS details: Actiontec MI424WR-GEN3I WAP, DD-WRT v24-sp2 (Linux 2.4.37)
Network Distance: 2 hops
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 0.04 ms 192.168.220.2
2 0.06 ms 220.181.38.251
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 89.57 seconds
2. 发包模式
-
发包格式
用户在扫描时,可以设置发包格式为以太网帧或IP包。用于指定发包格式的选项及其含义如下:--send-eth/--send-ip:设置发送包为原始的以太网帧或IP包。使用Nmap对目标192.168.198.132实施扫描,指定发送的包格式为以太网帧。
┌──(rootkali)-[~] └─# nmap --send-eth 192.168.198.132 Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 20:55 CST Nmap scan report for 192.168.198.132 Host is up (0.032s latency). All 1000 scanned ports on 192.168.198.132 are in ignored states. Not shown: 1000 filtered tcp ports (no-response) Nmap done: 1 IP address (1 host up) scanned in 54.46 seconds使用Nmap对目标192.168.198.132实施扫描,指定发送的包格式为IP包。
┌──(rootkali)-[~] └─# nmap --send-ip 192.168.198.132 Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 21:01 CST Nmap scan report for 192.168.198.132 Host is up (0.00062s latency). All 1000 scanned ports on 192.168.198.132 are in ignored states. Not shown: 1000 filtered tcp ports (no-response) Nmap done: 1 IP address (1 host up) scanned in 4.17 seconds -
发包权限
--privileged: 假设用户拥有所有权限
--unprivileged:假设用户缺少构建原始套接字权限,如:不是root用户
使用Nmap对目标192.168.198.132实施扫描,设置扫描的用户拥有所有的权限。
┌──(rootkali)-[~]
└─# nmap --privileged 192.168.198.132
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 21:03 CST
Nmap scan report for 192.168.198.132
Host is up (0.00060s latency).
All 1000 scanned ports on 192.168.198.132 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
Nmap done: 1 IP address (1 host up) scanned in 7.71 seconds
3. 恢复扫描
使用Nmap扫描网络需要的时间很长,用户可能会分成多个时间段进行扫描,或者由于其他原因中断扫描。此时,如果希望继续之前的扫描,可以使用–resume选项恢复扫描,即继续扫描。
--resume <filename>:恢复被放弃的扫描。使用该选项时必须与-oN或者-oG选项配合使用。