得物(毒)加密算法解析 得物逆向
写在前面:
本文仅限交流学习使用,请勿使用在任何非法商业活动,禁止用于非法用途。否则后果自负。如有侵权,请告知删除,谢谢!
抓包分析:
本文以detailV3接口为例:
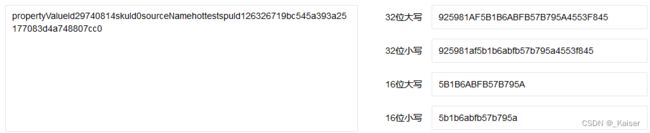
POST https://app.dewu.com/api/v1/h5/index/fire/flow/product/detailV3
{
"sign": "925981af5b1b6abfb57b795a4553f845",
"spuId": 1263267,
"propertyValueId": 29740814,
"sourceName": "hottest",
"skuId": 0
}
可以看到请求body里有一个sign加密参数,反编译小程序后用微信开发者工具打开,发现下面这段很可疑:
return e = Object.keys(t).sort().reduce((function (e, r) {
return void 0 === t[r] ? e : "".concat(e).concat(r).concat(n(t[r]))
}), ""), e += "19bc545a393a25177083d4a748807cc0", Object(r.md5)(e)大概就是json键值拼接后加上一段常量值,取其md5
果然一致
响应体解密:
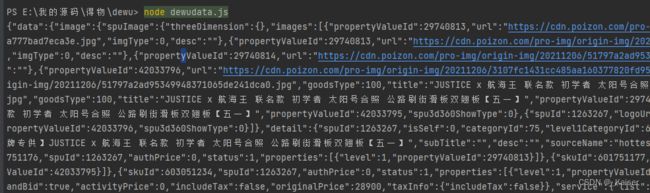
请求成功之后发现返回的是一段密文,由于比较长,这里摘抄一部分:
D352B3D6550E7A3443379AF45BA1EAD737CFA4DAC2562A71B3F62D454B07CF7EE813BF029F7677F9473BBBC7A55CC69E40670406D297EE6319467158FD579653C75C861473508C4C0437C5E52232387B52CC9B31849C022495964571ADD9E6615BEB74893EF89C74F62F9DC64A72F96552C56B9C500B74299A74F9C62BF38FCEC24B76D2E3D44611153FA1D42B1EFD9EE38410078B56797A1701D4F4BFE0DEDC50C6F923A41333915D23F1B3D5FC8B9F2D8F4268E89F4D12C9345C8125EAE4F14170AB70A5A4BD20E72339C980A1F6F12AB1716CA7F735DCA8AF566B1A3446F3A5EDF002E7B14236DD7A556A56091DD219FE60B532CBE90524A1A48E85FFF84E13F52CD9C2388D8B52625B7F8D3E9E1EB196EE92266B7609B84DA3F25A6AD861A3A8BFE5EC91EB1DA17214096E8C38879908A7C700D6C08A9E7F0B1CC48B455D40F088C39FD5EE9F6051F19B85CF078BEE7E35AAA7CA488BEC439C9825B7998C00962E7AC39B974EDED334E1796131145A4D42E5DD1BD1863ACD0B3BC42CDA1EFFB587AFE3ED0A37E7D6D738E85187AC5064F289E45486BDD1CE4F5018817D281062493D9CD26A3DC7D212A263E39F9DDF00758D428BAEF6B4D08176DA8C8E0170CD728C3966FC396BE73D6C0D8436DCF615688B506353E2CB67C69BCF1875074A98AA6DD8E9E39C7CB748B50D620286FA03B9D6DD360D2C49CA46C705C530AB7F13D52BD8AB32345AB436E9DBFE37EAEBA4DDB2131CC30023A9F8CB2BF320704AD386A79200B90A2ED21AE229E0227C31F9B2D386E1B94CD57354CC63BFC9D57F88EC7F2126799D94135A731A3C85F673790C31B3DF68C07E460895B179DE9DEE8BE9EB070EBC5ED4589C9569883C009FA50DAB7E400F0724693FD26799DEF1B7399F96DECFCC3C8640B7537F1AAA8E689F2C7106115700DB47D465F59FA3916E3D9F60B818B808E3A6D48F7492802F32EA7BEDF39DC6E68725F787DF2E40092606080EA16EE4816A786A587BA812E4A2F3AB11ED8E57561AACABD49A15BE6DED571CF252CF5A87D995DC1CF413D7845FED1A0748B363855B69FB69A2A2DA69D6C356DD64D143F2BE9329A2737FFE77BB463F2D7EAA4ED89282310693CF34B9E8F6AC13AA23F56E691B39292A20BA9C2CA5F0F35782075BA31B16B80EDA091A125BEEBF58812B10C3A508077363F7DE5404EFA0B073A324D3AA06118DC48EB099976C7FE4D9F36F925219F5479B4B00FC9FB64B8B04078171397667A5722B23FC96EA8FD182C164AE0C90B9EE0D7D9283A441DB8ED374B8CE1DF5360A458151617CB9F6F3A08459C1955CAF7D6EFE15D14CD65DEA5082FDD2E8D792498
我们需要后续的协议操作肯定离不开返回的内容,所以解密响应体非常重要,追踪函数后发现下面这个函数:
function Z(t, n, i, o, a) {
var s, c = m,
u = g,
l = t[u(574, "PY[)")] || t,
p = u(575, "Q)iM"),
f = e(i ? i[u(576, "BT!N")](",") : ["1", "1"], 2),
h = f[0],
d = f[1];
if ("wx" === o ? s = wx : "qq" === o ? s = qq : "dy" === o && (s = tt), a || (rt = d, s[c(577)](u(578, "A9qh"), d)), "1" === h) {
var v;
try {
var y = S[c(45)][c(579)][u(580, "GVzz")](l),
_ = S[u(581, "kYAm")][u(582, "s*Gd")][u(583, "vPY@")](y);
if (!(v = S.MM[u(584, "a%bJ")](_, S[u(585, "1VQD")][u(586, "2dNh")][c(235)](n[c(54)](10, 16)), {
iv: S[u(587, "PY[)")][c(62)][c(235)](n[u(588, "FCI6")](20, 16)),
mode: S[c(589)][c(568)],
padding: S[c(569)][u(590, "GA59")]
})[u(591, "^My#")](S[c(45)][c(62)])[c(20)]())) try {
var b = S[c(45)][c(579)][c(235)](l),
x = S[c(45)][c(159)][c(63)](b);
(v = S.MM[c(592)](x, S[c(45)][u(593, "Vih(")][u(594, "#Ace")](p[c(54)](10, 16)), {
iv: S[u(595, "3M![")][c(62)][u(596, "^My#")](p[c(54)](20, 16)),
mode: S[u(597, "3M![")][c(568)],
padding: S[u(598, "1VQD")][c(570)]
})[u(599, "IL7s")](S[u(600, "O@Bp")][c(62)])[u(601, "QHvF")]()) || (v = t)
} catch (e) {
v = t
}
} catch (e) {
try {
var w = S[c(45)][c(579)][c(235)](l),
k = S[c(45)][u(602, "8ByR")][c(63)](w);
(v = S.MM[u(603, "h]Ba")](k, S[u(604, "X9C9")][u(605, "JLqm")][c(235)](p[u(606, "BT!N")](10, 16)), {
iv: S[u(607, "wh7E")][u(608, "2a!b")][c(235)](p[c(54)](20, 16)),
mode: S[c(589)][c(568)],
padding: S[u(609, "FCI6")][c(570)]
})[c(20)](S[u(610, "X55z")][u(611, "BT!N")])[u(612, "dsUg")]()) || (v = t)
} catch (e) {
v = t
}
}
return r(v) === c(613) ? JSON[c(63)](v) : v
}
return r(t) === c(613) ? JSON[c(63)](t) : t
}通过调用该函数成功解密出如下数据: