billu_b0x靶场通关
billu靶场通关
靶机ip:192.168.112.134
信息收集
端口开放
80
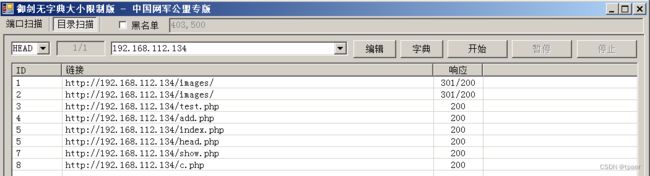
目录扫描
images目录存在目录遍历
test.php(任意文件下载)
add.php(文件上传)
index.php(主页)
head.php
show.php
c.php
这个工具的字典不全,换py脚本重新扫多出了以下目录
phpmy
in
panel.php
渗透阶段
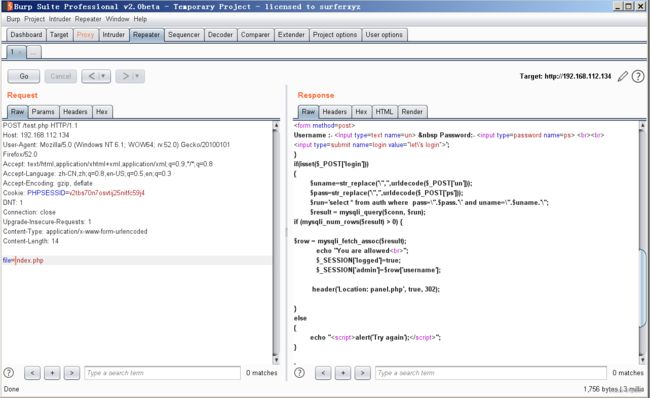
发现test.php存在任意文件下载,利用该漏洞读取其他文件
session_start();
include('c.php');
include('head.php');
if(@$_SESSION['logged']!=true)
{
$_SESSION['logged']='';
}
if($_SESSION['logged']==true && $_SESSION['admin']!='')
{
echo "you are logged in :)";
header('Location: panel.php', true, 302);
}
else
{
echo '
--==[[ billu b0x ]]==--
Show me your SQLI skills
你可能感兴趣的:(从入门到入狱,php,服务器,安全,web安全)
- 明天股市大盘走势预测
05ccd5c4766a
今天上证低开高走,收出缩量小阳线在五天线上方,成指也收复五天线,创业板收长阳线,大涨3.9%。从盘面看,早盘宽幅震荡,先上攻3590点附近受阻回落,午后再向上拉高,收复五天线。二市成交量9100亿,缩量严重,二市红盘家数1817家,一改前几天多数股上涨的格局。从早盘银行券商冲高回落,到稀土、钢铁、有色、汽车概念后接力上涨,权重交替拉抬下,让大盘收在3580点上方。但由于量能不续,明仍需提防冲击36
- 黄河,我的母亲——教读《黄河颂》有感
山城居士
黄河,你是巍巍昆仑孕育的女儿是生我,养我的母亲你如同黄沙般普通又朴实每天重复着同样的事——哺育我成长你伸出千万条柔弱的手臂,揽着我给我温暖与安全你是摇篮,我就是你摇篮里的婴孩你经历无数的狂风暴雨始终不变奔向黄海的志向把坚强融进了血脉这是你赋予我的期盼——博大胸怀这是你教会我的人生——坚强勇敢
- 孩子的未来在父母的手心上
感恩遇见0331
“孩子的未来在父母的手心上。”这句话出自张文质老师《父母改变,孩子改变》一书中的《每一个孩子来到世上,都希望遇到一个好父母》。从这个学期开始,学校的心理咨询室开启了一项新的活动,就是学生到心理咨询室寻求帮助的时候,可以点名找他信任的老师来给他进行心理辅导。学校里每一位有心理辅导资格的老师几乎都被点过名,已经帮助了很多孩子,我自己也遇到过两个孩子。最近办公室里老师们,尤其是和班主任们交流的时候,也都
- http协议
默笙666
浏览器向服务器发送的请求格式GET/HTTP/1.1请求目标协议版本(请求的时候至少要这个)第一个/表示根目录Host:127.0.0.1:8080服务器的IP地址和端口Connection:keep-alive长链接Upgrade-Insecure-Requests:1浏览器告诉服务器,自己可以处理https协议User-Agent:Mozilla/5.0(WindowsNT6.1;Win64;
- Linux利用多线程和线程同步实现一个简单的聊天服务器
1.概述本文实现一个基于TCP/IP的简单多人聊天室程序。它包含一个服务器端和一个客户端:服务器能够接收多个客户端的连接,并将任何一个客户端发来的消息广播给所有其他连接的客户端;客户端则可以连接到服务器,发送消息并接收来自其他人的消息。该Demo运用了网络编程(SocketAPI)、多线程(Pthreads)以及线程同步(互斥锁)技术,以实现并发处理和数据共享安全。2.核心技术网络编程(Socke
- uniapp打开导航软件并定位到目标位置的实现
界面架构师
uniappuni-app导航前端vue
/***打开导航*@paramlocation经纬度(例如:"117.214713,39.116884")*@paramaddress地址*/exportfunctionmapNavigation(location,address){constlocationArr=location.split(',')constlongitude=locationArr[0]constlatitude=loca
- ESG碳交易骗局揭秘!量化北恒私募实盘大赛周一丰郭沛源被骗历程!受骗不能出金!
易星辰分享普法
量化北恒私募实盘大赛周一丰投票项目安全吗?量化北恒私募实盘大赛周一丰积分投票已经亏损被骗了怎么办?警惕!量化北恒私募实盘大赛周一丰十选五项目合法吗——杀猪盘骗局!被骗提不了款!提不了现!出不来金!不要上当!自古有句话讲得好“人善被欺、马善被骑”,现如今也是被骗子利用到了极致,人善就真该被欺骗吗?狡猾的骗子们就利用到了这点,利用同情心、爱心去进行诈骗,宣传公益捐款、爱心慈善打比赛来骗取资金!正常的投
- 【每日精进】少了读书和运动,不是美好的一天
金台望道
6月25日星期六天气:晴好早晨:5点多起来,就整理发布“读毛年谱(176)”,顺便整理各个平台这个栏目的材料,均声明专栏是读书笔记,并非原创。以后这个栏目都不要放在宝贵的早上来做,完全放在晚上加工。早上做原创工作。以后每天还要安排读书和运动。少了这两样,这一天也不是美好的一天了!上午:到图书馆去,继续写小说第48章。下午:本想去图书馆,中午饭后,就在家里睡大觉了,一下午没做事。呜呼!晚上:完成“读
- Navicat 连接不上阿里云服务器中安装的宝塔面板中的Mysql服务器
一只程序熊
阿里云服务器云计算
项目场景:就今天在做宝塔的时候遇到一个新问题,在之前的阿里云服务器中都没有发现过这个问题!特此记录解决方案:本地连接不上云服务器主要是这几个原因:1.云服务器官方的安全组问题(安全组是否放行目标端口)2.云服务器内部的服务端口问题(服务器内部端口是否向外部开放)但是今天我又在云服务器安全组内部发现了一个新的问题:3.云服务器中设置了仅本机访问的ipv6的地址,但是仍然访问不了。可能是因为navic
- python学习路线(从菜鸟到起飞)
突突突然不会编了
python学习开发语言
以下是基于2025年最新技术趋势的Python学习路线,综合多个权威资源整理而成,涵盖从零基础到进阶应用的全流程,适合不同学习目标(如Web开发、数据分析、人工智能等)的学习者。路线分为基础、进阶、实战、高级、方向拓展五个阶段,并附学习资源推荐:一、基础阶段(1-2个月)目标:掌握Python核心语法与编程思维,熟悉开发环境。环境搭建安装Python3.10+,配置PyCharm或VSCode开发
- php(上传文件)
1、php文件上传配置指令(1)file_uploads=On/off(是否可以接受文件上传)(2)max_input_time=60在提示错误之前解析输入所花费的最长时间,以秒为单位,如果经常需要传输大文件,这个时限应该设置得合理一些。(3)max_file_uploads=20对可以同时上传文件数设置了一个上限。(4)memory_limit=128M设置脚本可以分配得最大内存,可以防止脚本独
- 阿里云2023年云服务器活动优惠价格文章汇总(历史价格对比)
阿里云最新优惠和活动汇总
2023年购买阿里云服务器需要多少钱?由于每个月阿里云服务器的活动优惠价格均有所不同,小编也在每个月都会分享几篇当月阿里云服务器活动优惠价格的文章,下面小编再将2023年1月到5月份,涉及阿里云服务器每个月优惠价格的文章做个汇总,以供大家了解阿里云服务器在2023年的历史优惠价格变化情况,知道哪些阿里云服务器涨价了,哪些阿里云服务器降价了,以供参考选择。说明:以下文章所涉及的阿里云服务器价格仅供参
- 小白带你部署LNMP分布式部署
刘俊涛liu
分布式
目录前言一、概述二、LNMP环境部署三、配置nginx1、yum安装2、编译安装四、安装1、编译安装nginx2、网络源3、稍作优化4、修改配置文件vim/usr/local/nginx/conf/nginx.conf5、书写测试页面五、部署应用前言LNMP平台指的是将Linux、Nginx、MySQL和PHP(或者其他的编程语言,如Python、Perl等)集成在一起的一种Web服务器环境。它是
- AI Agent开发学习系列 - langchain之示例选择器2:相关性与多样性兼得-MaxMarginalRelevanceExampleSelector在LangChain中的用法
alex100
AIAgent学习人工智能langchainprompt语言模型python
MaxMarginalRelevanceExampleSelectorMaxMarginalRelevanceExampleSelector是LangChain中用于Few-ShotPrompt的一种智能示例选择器。它的作用是:在众多示例中,自动选择与当前输入最相关、同时彼此多样性最大的示例,插入到prompt里。主要特点相关性优先:优先选择与用户输入最相似的示例。多样性保证:避免选到内容高度重复
- 微信投票平台怎么联系,一般多少钱一票
神州网络公司
微信投票平台怎么联系,一般多少钱一票微信真实人工拉票正常价格都是0.2-0.4一票,100票一次性收费在30块左右,1000票一次性收费在200元到400元之间,10000票一次性收费在3000元左右,当然因投票活动操作难度不同收费价络也不同的,然后团队的资源人次比你自己的资源人脉更多更广。人工代刷一般都是在几毛左右,直接买票这样比较方便一点,微信人工刷票真真实实的人工去操作投票,每人一票都不是同
- 语音识别开源项目推荐:GitHub热门仓库盘点
AGI大模型与大数据研究院
AI大模型应用开发实战语音识别开源githubai
2024年必看!GitHub热门语音识别开源项目全解析:从入门到实战关键词语音识别(ASR)、开源项目、GitHub、Whisper、FunASR、PaddleSpeech、深度学习摘要想象一下:开车时只需说一句话就能自动发消息,听英文演讲时实时获得中文翻译,给视障人士读文本时精准转换——这些场景的背后,语音识别(AutomaticSpeechRecognition,ASR)技术正在改变我们与机器
- MySQL学习----Explain
典孝赢麻崩乐急
mysql学习数据库
使用Explain可以查看sql的性能瓶颈信息,并根据结果进行sql的相关优化。当使用Explain分析SQL查询时,MySQL会返回一个包含多个字段的结果集,每个字段都提供了查询执行计划的重要信息。主要输出字段详解(1)id含义:SELECT标识符作用:表示查询中SELECT子句的执行顺序值说明:id相同:执行顺序从上到下id不同:从大到小执行id为NULL:表示结果集,如UNION结果(2)s
- Python 进阶学习之全栈开发学习路线
Microi风闲
【胶水语言】Pythonpython学习开发语言
文章目录前言一、Python全栈开发技术栈1.前端技术选型2.后端框架选择3.数据库访问二、开发环境配置1.工具链推荐2.VSCode终极配置3.项目依赖管理三、现代Python工程实践1.项目结构规范2.自动化测试策略3.CI/CD流水线四、部署策略大全1.传统服务器部署2.容器化部署3.无服务器部署五、性能优化技巧1.数据库优化2.异步处理3.静态资源优化结语前言Python作为当今最流行的编
- 骑昆明到北海—94 蒙自市海关旧址
61清风i
每年春季详细规划好线路,夏季出行,2020年因为疫情迟迟不能确定线路和行程。总算到了暑期疫情逐渐消失,规划了50多天的云南昆明—广西北海计划。2020年9月13日傍晚点从延平站出发,9月15日到达云南昆明开始这一旅程,一直到11月4日下午从北海市飞回福州顺利结束。虽然在云南骑过二次长途(一次从昆明往香格里拉方向。一次从泸沽湖往腾冲方向,)而这次选择往广西这一路,可以说路上每天都是新鲜的。确定线路和
- 【日记星球第532篇】——感恩日记
神秘园的简书
2021年10月30日星期六趁着新一期的瑜伽班还没开营,给自己放个假,睡个大懒觉。一下到7点多才自然醒,还躺着拿手机看了会儿信息,磨磨蹭蹭到八点才起来。生活常常给我们比想要的更多,那就清点一下自己拥有什么,记录下这些值得感恩的事吧:1.感恩上周末邻居送来几颗刚摘的新鲜大柿子给我们,真好!2.感恩上周末妈妈给我做了美味的大锅菜和千丝饼!3.感恩这周工作一切顺利开心!4.感恩同事经常分享好吃的零食水果
- 从无人问津,到被打赏,我们一起努力
小暖阳光
今天是在码字的第32天。最近已经习惯了睁眼先看疫情进展,期盼着疫情突然就过去了。第二件事则是打开看看文章下面的小钻石有没有增加。说来可笑,在混了一个月,我依然没整明白那些钻旁边的小数字是怎么增加的,但每天看着它在增长,阅读人数也变多,心里就会很满足。然而今天早上却把我惊呆了。今天除了有比往常多很多的互动点赞消息外,居然多了8个关注,最最吃惊的是有4个简友居然给我送了呗,被送贝的那篇文章下面的小钻石
- 计算机网络学习----Https协议
典孝赢麻崩乐急
计算机网络学习https
在互联网通信中,数据安全始终是核心需求。当用户在浏览器中输入https://访问网站时,背后隐藏着一套复杂的安全机制——HTTPS(HypertextTransferProtocolSecure)。它通过TLS/SSL协议对HTTP通信加密,而支撑这一加密体系的核心正是证书体系。本文将详细解析HTTPS的证书体系、加密通信流程、核心作用、优缺点,并结合代码示例说明其实现逻辑。HTTPS是什么?HT
- 【0425读书感悟】3366-引力-HR-合肥
精力满满
书名:《思维导图》作者:东尼·博赞金句:在做出选择之前,思维导图对理清思路是一个特别有用的工具。分享:思维导图能让大脑马上接受一系列复杂而又相互联系的信息,问题的重点一目了然。它们能给大脑带来一个事先构造好的框架,以便于产生联想,确保所有相关的因素都被考虑进去。尤其到图中的色彩和图像,把一些重要的情感因素考虑到决策中去,有助于突出重要的比较点。在整体决策的时候,思维导图可以帮你平衡彼此冲突的一些因
- 《味道》
卧龙饮水
很久很久以来一直迷恋于某种味道说不清她的起源感觉始自于母亲的怀抱不知道要陪我走多久山一程水一程在心里深处陪我路遥遥她就像母亲身上的奶香慢慢浸透包裹我的襁褓就像风吹过成熟的麦田那种气味让人魂牵梦绕也像当年槐花开时你在树下阳光里对我的嫣然一笑世界上任何一种感情都有自己独特的味道也许只有真正懂得才能感觉到春风滋润了枝头的花蕾却是秋雨品味果实挂满树梢轮回中的味觉会陪伴我们到地荒天老
- 2021-05-04 2021年5月9日考试顺利通过毕业
kellying
不知什么时候,我每逢考试,我非常的紧张,考试之前根本无法入睡,精神也不再状态里,这是我一直来的毛病,在读小学,中学,中专,考试的时候,经常丢东西,丢三丢四,因此掉了很多的东西,经常抱怨自己,恨自己,结果我一点不自信,缺乏安全感,走进社会,混的不好。是自己记忆性不如别人,所以做任何事情不如别人,现在经过自己的努力终于找到一点自信了,希望我的今后的日子好过点,谢谢
- 《小醉蜻蜓龙》第二章 第一节 神迷海遇难 揭露神迷海与聂潇琴感情纠葛
Z龙小贱Z
神迷海躺在床上辗转反侧难以入眠,那日在穴龙湖与聂潇琴一别后就再没见过她,神迷海对聂潇琴的痴迷不悟到什么地步或许只有神迷海自己才知道了,然而那日聂潇琴奶奶仙幻凤的话语却让他五味杂陈,他想把这一切的来龙去脉搞清楚。神迷海拿起手机,打开微信,翻看着聂潇琴的朋友圈,发现她已有一段时日没有更新了,聂潇琴喜欢晒美食、晒日常,晒游山玩水……之前每天都会有更新,如今却没了动态,神迷海自然会有疑惑,想发信息给她却不
- 基于单片机智能消毒柜设计
小新单片机
单片机设计库单片机嵌入式硬件stm32消毒柜
传送门其他作品题目速选一览表其他作品题目功能速览概述本设计实现了一种基于单片机的高效智能消毒柜系统,集精准灭菌、安全防护与能耗管理于一体。系统以微控制器(如STM32)为核心,集成多模式消毒模块、环境传感器及人机交互单元。所以想通过本次设计真正意义上去感受智能产品的魅力;更加深刻了解单片机以及嵌入式操作系的主要特点在于功能性强实用、操作简单、价格低并且还易于安装这些特点。一、系统核心组成模块功能说
- 《穿越:抢了皇位后,我带大明起飞》&朱允熥、朱元璋(全文阅读)
今日推文
书名《穿越:抢了皇位后,我带大明起飞》主角:朱允熥、朱元璋※※※※※※※※※※※※※※阅读建议:下拉至文章最底部看全文——※※※※※※※※※※※※※朱允熥脑子里正想着这件事,犹豫着要如何开口,碰巧就有人先开口问了起来。“三殿下但说无妨!”众人心中正是热情高涨的时候,不疑有他,立刻应声道。朱允熥微微沉吟了片刻,然后摇头轻叹了口气,露出一副为难的神色来,到:“这……说起来算是个不情之请,可能会令舅爷、
- 煤海放飞青春梦
尘飞扬兮
青春像一首诗,任凭年青的心灵创作;青春像一碗心灵鸡汤,令失去它的人午夜梦回念念不忘;青春更像一个梦,让无数选煤儿女兢兢业业为之奋斗,为之耕耘!在美丽的准格尔煤田,一批批怀揣青春梦的青年们前仆后继破碎站——梦开始的地方驰骋煤海,他们在这里播种青春梦,收获了事业的成功更实现了人生的价值!阳光倾洒而下,轻柔曼妙,轻地仿佛怕惊动了沉睡的煤尘。嘎吱一声响,岗位室的门开了,一个头戴红色安全帽,系黑色帽带,穿橘
- 今日份小确幸2023-05-16
兮若耶
今日份小确幸202305161.噢耶,我终于做到了早睡早起了耶,白天把要做的事情全部完成,为了入睡容易些,晚上到外面散步消耗能量了,在困到打哈欠的时候我在22:53躺在了床上,比以前早了一个小时,入睡有些许困难,但好在没有辗转反侧太久。睡早了,在生物钟的作用下,我也起早了,早到了凌晨三点多就醒来,真正做到了早睡早起。我可以做到自嘲了耶,好棒呀!2.又重新看了一遍《罗小黑战记》,都已经记不清第几遍了
- C/C++Win32编程基础详解视频下载
择善Zach
编程C++Win32
课题视频:C/C++Win32编程基础详解 视频知识:win32窗口的创建 windows事件机制 主讲:择善Uncle老师 学习交流群:386620625 验证码:625 --
- Guava Cache使用笔记
bylijinnan
javaguavacache
1.Guava Cache的get/getIfPresent方法当参数为null时会抛空指针异常 我刚开始使用时还以为Guava Cache跟HashMap一样,get(null)返回null。 实际上Guava整体设计思想就是拒绝null的,很多地方都会执行com.google.common.base.Preconditions.checkNotNull的检查。 2.Guava
- 解决ora-01652无法通过128(在temp表空间中)
0624chenhong
oracle
解决ora-01652无法通过128(在temp表空间中)扩展temp段的过程 一个sql语句后,大约花了10分钟,好不容易有一个结果,但是报了一个ora-01652错误,查阅了oracle的错误代码说明:意思是指temp表空间无法自动扩展temp段。这种问题一般有两种原因:一是临时表空间空间太小,二是不能自动扩展。 分析过程: 既然是temp表空间有问题,那当
- Struct在jsp标签
不懂事的小屁孩
struct
非UI标签介绍: 控制类标签: 1:程序流程控制标签 if elseif else <s:if test="isUsed"> <span class="label label-success">True</span> </
- 按对象属性排序
换个号韩国红果果
JavaScript对象排序
利用JavaScript进行对象排序,根据用户的年龄排序展示 <script> var bob={ name;bob, age:30 } var peter={ name;peter, age:30 } var amy={ name;amy, age:24 } var mike={ name;mike, age:29 } var john={
- 大数据分析让个性化的客户体验不再遥远
蓝儿唯美
数据分析
顾客通过多种渠道制造大量数据,企业则热衷于利用这些信息来实现更为个性化的体验。 分析公司Gartner表示,高级分析会成为客户服务的关键,但是大数据分析的采用目前仅局限于不到一成的企业。 挑战在于企业还在努力适应结构化数据,疲于根据自身的客户关系管理(CRM)系统部署有效的分析框架,以及集成不同的内外部信息源。 然而,面对顾客通过数字技术参与而产生的快速变化的信息,企业需要及时作出反应。要想实
- java笔记4
a-john
java
操作符 1,使用java操作符 操作符接受一个或多个参数,并生成一个新值。参数的形式与普通的方法调用不用,但是效果是相同的。加号和一元的正号(+)、减号和一元的负号(-)、乘号(*)、除号(/)以及赋值号(=)的用法与其他编程语言类似。 操作符作用于操作数,生成一个新值。另外,有些操作符可能会改变操作数自身的
- 从裸机编程到嵌入式Linux编程思想的转变------分而治之:驱动和应用程序
aijuans
嵌入式学习
笔者学习嵌入式Linux也有一段时间了,很奇怪的是很多书讲驱动编程方面的知识,也有很多书将ARM9方面的知识,但是从以前51形式的(对寄存器直接操作,初始化芯片的功能模块)编程方法,和思维模式,变换为基于Linux操作系统编程,讲这个思想转变的书几乎没有,让初学者走了很多弯路,撞了很多难墙。 笔者因此写上自己的学习心得,希望能给和我一样转变
- 在springmvc中解决FastJson循环引用的问题
asialee
循环引用fastjson
我们先来看一个例子: package com.elong.bms; import java.io.OutputStream; import java.util.HashMap; import java.util.Map; import co
- ArrayAdapter和SimpleAdapter技术总结
百合不是茶
androidSimpleAdapterArrayAdapter高级组件基础
ArrayAdapter比较简单,但它只能用于显示文字。而SimpleAdapter则有很强的扩展性,可以自定义出各种效果 ArrayAdapter;的数据可以是数组或者是队列 // 获得下拉框对象 AutoCompleteTextView textview = (AutoCompleteTextView) this
- 九封信
bijian1013
人生励志
有时候,莫名的心情不好,不想和任何人说话,只想一个人静静的发呆。有时候,想一个人躲起来脆弱,不愿别人看到自己的伤口。有时候,走过熟悉的街角,看到熟悉的背影,突然想起一个人的脸。有时候,发现自己一夜之间就长大了。 2014,写给人
- Linux下安装MySQL Web 管理工具phpMyAdmin
sunjing
PHPInstallphpMyAdmin
PHP http://php.net/ phpMyAdmin http://www.phpmyadmin.net Error compiling PHP on CentOS x64 一、安装Apache 请参阅http://billben.iteye.com/admin/blogs/1985244 二、安装依赖包 sudo yum install gd
- 分布式系统理论
bit1129
分布式
FLP One famous theory in distributed computing, known as FLP after the authors Fischer, Lynch, and Patterson, proved that in a distributed system with asynchronous communication and process crashes,
- ssh2整合(spring+struts2+hibernate)-附源码
白糖_
eclipsespringHibernatemysql项目管理
最近抽空又整理了一套ssh2框架,主要使用的技术如下: spring做容器,管理了三层(dao,service,actioin)的对象 struts2实现与页面交互(MVC),自己做了一个异常拦截器,能拦截Action层抛出的异常 hibernate与数据库交互 BoneCp数据库连接池,据说比其它数据库连接池快20倍,仅仅是据说 MySql数据库 项目用eclipse
- treetable bug记录
braveCS
table
// 插入子节点删除再插入时不能正常显示。修改: //不知改后有没有错,先做个备忘 Tree.prototype.removeNode = function(node) { // Recursively remove all descendants of +node+ this.unloadBranch(node); // Remove
- 编程之美-电话号码对应英语单词
bylijinnan
java算法编程之美
import java.util.Arrays; public class NumberToWord { /** * 编程之美 电话号码对应英语单词 * 题目: * 手机上的拨号盘,每个数字都对应一些字母,比如2对应ABC,3对应DEF.........,8对应TUV,9对应WXYZ, * 要求对一段数字,输出其代表的所有可能的字母组合
- jquery ajax读书笔记
chengxuyuancsdn
jQuery ajax
1、jsp页面 <%@ page language="java" import="java.util.*" pageEncoding="GBK"%> <% String path = request.getContextPath(); String basePath = request.getScheme()
- JWFD工作流拓扑结构解析伪码描述算法
comsci
数据结构算法工作活动J#
对工作流拓扑结构解析感兴趣的朋友可以下载附件,或者下载JWFD的全部代码进行分析 /* 流程图拓扑结构解析伪码描述算法 public java.util.ArrayList DFS(String graphid, String stepid, int j)
- oracle I/O 从属进程
daizj
oracle
I/O 从属进程 I/O从属进程用于为不支持异步I/O的系统或设备模拟异步I/O.例如,磁带设备(相当慢)就不支持异步I/O.通过使用I/O 从属进程,可以让磁带机模仿通常只为磁盘驱动器提供的功能。就好像支持真正的异步I/O 一样,写设备的进程(调用者)会收集大量数据,并交由写入器写出。数据成功地写出时,写入器(此时写入器是I/O 从属进程,而不是操作系统)会通知原来的调用者,调用者则会
- 高级排序:希尔排序
dieslrae
希尔排序
public void shellSort(int[] array){ int limit = 1; int temp; int index; while(limit <= array.length/3){ limit = limit * 3 + 1;
- 初二下学期难记忆单词
dcj3sjt126com
englishword
kitchen 厨房 cupboard 厨柜 salt 盐 sugar 糖 oil 油 fork 叉;餐叉 spoon 匙;调羹 chopsticks 筷子 cabbage 卷心菜;洋白菜 soup 汤 Italian 意大利的 Indian 印度的 workplace 工作场所 even 甚至;更 Italy 意大利 laugh 笑 m
- Go语言使用MySQL数据库进行增删改查
dcj3sjt126com
mysql
目前Internet上流行的网站构架方式是LAMP,其中的M即MySQL, 作为数据库,MySQL以免费、开源、使用方便为优势成为了很多Web开发的后端数据库存储引擎。MySQL驱动Go中支持MySQL的驱动目前比较多,有如下几种,有些是支持database/sql标准,而有些是采用了自己的实现接口,常用的有如下几种: http://code.google.c...o-mysql-dri
- git命令
shuizhaosi888
git
---------------设置全局用户名: git config --global user.name "HanShuliang" //设置用户名 git config --global user.email "[email protected]" //设置邮箱 ---------------查看环境配置 git config --li
- qemu-kvm 网络 nat模式 (四)
haoningabc
kvmqemu
qemu-ifup-NAT #!/bin/bash BRIDGE=virbr0 NETWORK=192.168.122.0 GATEWAY=192.168.122.1 NETMASK=255.255.255.0 DHCPRANGE=192.168.122.2,192.168.122.254 TFTPROOT= BOOTP= function check_bridge()
- 不要让未来的你,讨厌现在的自己
jingjing0907
生活 奋斗 工作 梦想
故事one 23岁,他大学毕业,放弃了父母安排的稳定工作,独闯京城,在家小公司混个小职位,工作还算顺手,月薪三千,混了混,混走了一年的光阴。 24岁,有了女朋友,从二环12人的集体宿舍搬到香山民居,一间平房,二人世界,爱爱爱。偶然约三朋四友,打扑克搓麻将,日子快乐似神仙; 25岁,出了几次差,调了两次岗,薪水涨了不过百,生猛狂飙的物价让现实血淋淋,无力为心爱银儿购件大牌
- 枚举类型详解
一路欢笑一路走
enum枚举详解enumsetenumMap
枚举类型详解 一.Enum详解 1.1枚举类型的介绍 JDK1.5加入了一个全新的类型的”类”—枚举类型,为此JDK1.5引入了一个新的关键字enum,我们可以这样定义一个枚举类型。 Demo:一个最简单的枚举类 public enum ColorType { RED
- 第11章 动画效果(上)
onestopweb
动画
index.html <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"> <html xmlns="http://www.w3.org/
- Eclipse中jsp、js文件编辑时,卡死现象解决汇总
ljf_home
eclipsejsp卡死js卡死
使用Eclipse编辑jsp、js文件时,经常出现卡死现象,在网上百度了N次,经过N次优化调整后,卡死现象逐步好转,具体那个方法起到作用,不太好讲。将所有用过的方法罗列如下: 1、取消验证 windows–>perferences–>validation 把 除了manual 下面的全部点掉,build下只留 classpath dependency Valida
- MySQL编程中的6个重要的实用技巧
tomcat_oracle
mysql
每一行命令都是用分号(;)作为结束 对于MySQL,第一件你必须牢记的是它的每一行命令都是用分号(;)作为结束的,但当一行MySQL被插入在PHP代码中时,最好把后面的分号省略掉,例如: mysql_query("INSERT INTO tablename(first_name,last_name)VALUES('$first_name',$last_name')");
- zoj 3820 Building Fire Stations(二分+bfs)
阿尔萨斯
Build
题目链接:zoj 3820 Building Fire Stations 题目大意:给定一棵树,选取两个建立加油站,问说所有点距离加油站距离的最大值的最小值是多少,并且任意输出一种建立加油站的方式。 解题思路:二分距离判断,判断函数的复杂度是o(n),这样的复杂度应该是o(nlogn),即使常数系数偏大,但是居然跑了4.5s,也是醉了。 判断函数里面做了3次bfs,但是每次bfs节点最多