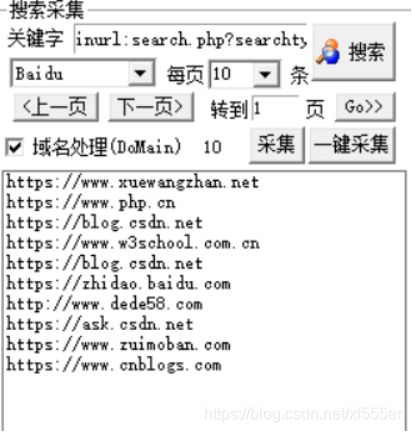
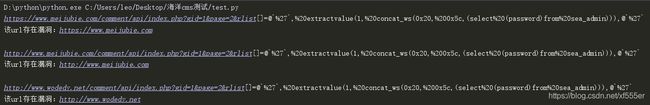
- 问题:Flask应用中的用户会话(Session)管理失效
m0_74823094
面试学习路线阿里巴巴flaskpython后端
我来分享一个常见的PythonWeb开发问题:问题:Flask应用中的用户会话(Session)管理失效这是一个在Flask开发中经常遇到的问题。当用户登录后,有时会话会意外失效,导致用户需要重复登录。解决方案:1.首先,确保正确设置了SecretKey:fromflaskimportFlask,sessionapp=Flask(__name__)设置一个安全的密钥pp.secret_key=‘y
- “单击以重新设置PIN”的解决方案
astragin
windows
win11“单击以重新设置PIN”解决方案1.BUG触发原因1)登录账户是“微软账户”,采用微软账户并联网进行确认登录。2)“手贱”或无聊进入安全模式:点击C:\Windows\System32\msconfig.exe进入了系统配置窗口,并在引导菜单选择了安全引导(F)下的最小(M)。3)进入安全模式后,电脑会关闭很多默认服务,并且无法启动。其中wlansvc也被禁止了,此时电脑无法联网,也就无
- 【PCL】vs2022配置PCL环境
IT小学僧
点云python数据结构算法
vs2022配置PCL环境前言一、安装教程二、路径python脚本前言vs2022配置PCL环境和路径Python脚本一、安装教程看这位兄弟写的就行二、路径python脚本因为我和他的版本并不一样,一个一个改太麻烦了,所以特此写了个python脚本。请注意要脚本中OpenNI2位置,修改成你的位置即可。importos#查找给定路径中的PCL依赖库defdependency(paths):#将输入
- Python入门教程丨3.5 正则表达式
凌小添
Python教程python正则表达式mysql
今天我们来学习Python里超实用的字符串匹配和正则表达式。这是处理文本数据的神器,无论是爬虫、数据清洗还是文本分析,都离不开它,我们从基础语法讲起,再到实战场景,深入体会正则的妙用。1.re库正则表达式(RegularExpression,简称regex或regexp)是一种用来匹配字符串的强大工具。它由一串字符和特殊符号组成,用于描述或匹配一系列符合某种模式的字符串。正则表达式广泛应用于文本搜
- Anconda/Poetry创建虚拟环境,并利用Pycharm设置该虚拟环境
up_learning
pycharmpython
一、当没有使用poetry做项目管理时1、通过cmd终端创建虚拟环境python-mvenv.venv#或者通过该方式安装虚拟环境(其中指定python版本,并安装两个必要软件):condacreate-nvenvpython=3.7.16setuptoolspip--offline#通过cd进入conda安装目录下可以查看所有的虚拟环境,或者下面命令condaenvlist#退出当前的虚拟环境c
- 算力网架构数字经济高质量发展引擎
智能计算研究中心
其他
内容概要在数字经济高速发展的背景下,算力网络作为新型基础设施的核心载体,正通过技术融合与架构革新重构产业生态。《算力网架构数字经济高质量发展引擎》基于国家“东数西算”战略框架,系统梳理了算力资源跨域调度、异构协同及绿色集约化的实现路径。从芯片制程突破到量子计算前沿探索,技术矩阵的持续迭代支撑着算力供给的可扩展性与可靠性提升,而标准体系与安全可信机制的完善则为产业链协同提供了制度保障。算力应用场景核
- 【python库】Pydantic
陆·柒
pythonpydantic
什么是PydanticPydantic是一个Python库,主要用于数据验证和设置管理。它使用Python的类型提示(typehints)来定义数据的结构,并在运行时验证数据是否符合定义的结构。简单来说,它可以确保数据的准确性和完整性,帮助开发人员在早期发现数据相关的问题。例如,在处理用户输入、API响应或者配置文件时,Pydantic可以验证数据的格式、类型和取值范围等是否正确用法总结数据定义和
- Python数据处理掌握Pandas.to_datetime函数时间序列(参数解析与实战)
步入烟尘
Python超入门指南全册pythonpandas开发语言时间函数参数解析
本文已收录于《Python超入门指南全册》本专栏专门针对零基础和需要进阶提升的同学所准备的一套完整教学,从基础到精通不断进阶深入,后续还有实战项目,轻松应对面试,专栏订阅地址:https://blog.csdn.net/mrdeam/category_12647587.html优点:订阅限时19.9付费专栏,私信博主还可进入全栈VIP答疑群,作者优先解答机会(代码指导、远程服务),群里大佬众多可以
- 【重要】如何使用Poetry做python项目开发:虚拟环境创建、软件分发?
fK0pS
经验分享
如何使用Poetry做python项目开发:虚拟环境创建、软件分发?#TraceVisualizationGUI#Step1:生成GUI*.ui文件对应的python文件cd.\visualizationgui\pyuic5-oTraceVisualization.py.\GUI\TraceVisualization.ui#Step2:Packagesoftwarepipinstallpoetry
- 芯谷D2761:为扬声器保护而生的音频限幅器
深圳市青牛科技实业有限公司 小芋圆
芯谷音视频机器人单片机嵌入式硬件人工智能科技
在音频设备中,扬声器的安全与音质表现一直是工程师们关注的重点。随着技术的发展,音频设备的应用场景越来越广泛,从个人电脑到便携式音响,都需要一种可靠的解决方案来保护扬声器免受过载信号的损害。芯谷的D2761音频限幅器正是为这一需求而设计。一、D2761简介D2761是一款专为保护扬声器设计的音频限幅器。它通过外接电阻调节限幅值,能够灵活适应不同的应用场景和扬声器特性。该芯片采用SSOP10、MSOP
- Python poetry 虚拟环境
IT小学僧
Python1024程序员节python
提示:文章写完后,目录可以自动生成,如何生成可参考右边的帮助文档文章目录一、Poetry是什么?二、使用步骤1.安装poetry2、初始化poetry3、创建虚拟环境启动和退出虚拟环境poetry常用指令总结一、Poetry是什么?Poetry是一个Python依赖管理和打包工具,它简化了项目的创建、依赖管理和发布流程。它的核心理念是将所有的依赖关系和项目配置集中在一个文件中,使得项目管理变得更加
- 2024-2025最新软考系统架构设计师的复习资料教材,解决如何快速高效通过该考试,试题的重点和难点在哪里?案例分析题和论文题的要点和踩坑点分析
九张算数
数字工匠系统架构学习方法职场和发展运维开发pat考试考研面试
目录引言考试概述考试结构考试内容复习策略制定复习计划学习资源知识点详解系统架构基础设计原则与模式系统分析与设计软件开发过程项目管理系统集成性能与优化安全性设计新兴技术试题解析选择题案例分析题论文题重点与难点分析模拟试题与答案参考资料总结引言系统架构设计师考试是软考高级资格考试之一,旨在考察考生在系统架构设计领域的综合能力和专业知识。通过该考试可以获得系统架构设计师资格认证,对职业发展有重要意义。本
- 库存python whl文件免费下载(4)
科技小游侠
pythonpython
库存pythonwhl文件免费下载(1)库存pythonwhl文件免费下载(2)库存pythonwhl文件免费下载(3)库存pythonwhl文件免费下载(4)库存pythonwhl文件免费下载(5)最近发现收藏的whl下载链接https://www.lfd.uci.edu/~gohlke/pythonlibs/已经走丢了,网上检索了下,还可以下载到历史的whl文件,为了防止下载链接再次失效,索性
- 库存python whl文件免费下载(3)
科技小游侠
pythonpython
库存pythonwhl文件免费下载(1)库存pythonwhl文件免费下载(2)库存pythonwhl文件免费下载(3)库存pythonwhl文件免费下载(4)库存pythonwhl文件免费下载(5)最近发现收藏的whl下载链接https://www.lfd.uci.edu/~gohlke/pythonlibs/已经走丢了,网上检索了下,还可以下载到历史的whl文件,为了防止下载链接再次失效,索性
- Netty Reactor 线程模型
Think_Higher
Netty从入门到理解
Reactor线程模型是Netty实现高性能的核心所在,在Netty中EventLoop是Reactor线程模型的核心处理引擎,那么EventLoop到底是如何实现的呢?又是如何保证高性能和线程安全性的呢?说明:本文参考的Netty源码版本为4.1.42.Final。文章目录Reactor线程执行的主流程轮询I/O事件处理I/O事件1.processSelectedKeysPlain2.proce
- 【实战记录】SSL证书部署到阿里云及注意事项
AntyRia
后端杂记阿里云sslhttps
目录前言正文部署流程注意事项总结前言原本正常的服务器在项目经过一次迭代之后突然无法使用https访问,一直显示不能提供安全的链接。先后检查了SSL证书状态、域名状态、服务器状态,都是没有问题的,甚至咨询了阿里的工程师,但是没有解决…于是狠下心来,备份数据,重装服务器…经过一番折腾,也算是可以访问了,特此记录一下。正文部署流程下载证书文件到本地部署到本地项目中下载的文件解压,里面有俩东西。全部复制到
- 【C#语言】Unity引擎
计算机学长
C#c#开发语言
引言在当今的游戏开发领域,C#语言与Unity引擎犹如一对黄金搭档,携手塑造了无数令人瞩目的游戏作品。C#作为一种简洁、类型安全且面向对象的编程语言,以其强大的功能和易于学习的特性,深受开发者喜爱。而Unity引擎,凭借其跨平台性、丰富的资源和强大的图形渲染能力,成为了游戏开发的首选平台之一。无论是小型独立游戏的灵动创意,还是大型3A游戏的震撼呈现,都能看到C#语言与Unity引擎的身影。它们的结
- python自动化办公
2501_90802096
python
好的!以下是一篇关于“Python自动化办公”的专业文章,介绍如何使用Python实现日常办公任务的自动化,包括处理Excel和Word文件、发送邮件、自动化网页操作等内容。这些技能可以帮助办公人员节省时间、提高效率。---Python自动化办公:高效处理日常任务一、引言在现代办公环境中,重复性任务占据了大量时间和精力,例如数据录入、文件整理、报表生成和邮件发送等。Python作为一种强大的编程语
- python在web开发中的应用
2501_90802096
python
Python在Web开发中的应用:框架、技术与实战案例一、引言Python作为一种简洁、高效且功能强大的编程语言,在Web开发领域备受开发者青睐。其丰富的生态系统和活跃的社区支持使得Python成为构建各类Web应用的理想选择。本文将介绍Python在Web开发中的应用,涵盖主流框架、开发技术以及实战案例,帮助读者快速掌握PythonWeb开发的核心技能。---二、PythonWeb开发框架Pyt
- python数据分析基础002 -使用matplotlib绘图(散点图,条形图,直方图)
2401_84139192
程序员python数据分析matplotlib
做了那么多年开发,自学了很多门编程语言,我很明白学习资源对于学一门新语言的重要性,这些年也收藏了不少的Python干货,对我来说这些东西确实已经用不到了,但对于准备自学Python的人来说,或许它就是一个宝藏,可以给你省去很多的时间和精力。别在网上瞎学了,我最近也做了一些资源的更新,只要你是我的粉丝,这期福利你都可拿走。我先来介绍一下这些东西怎么用,文末抱走。(1)Python所有方向的学习路线(
- 库存python whl文件免费下载(1)
科技小游侠
pythonpython
库存pythonwhl文件免费下载(1)库存pythonwhl文件免费下载(2)库存pythonwhl文件免费下载(3)库存pythonwhl文件免费下载(4)库存pythonwhl文件免费下载(5)最近发现收藏的whl下载链接https://www.lfd.uci.edu/~gohlke/pythonlibs/已经走丢了,网上检索了下,还可以下载到历史的whl文件,为了防止下载链接再次失效,索性
- 基于Python的冒泡排序,选择排序,插入排序(适合小白体质的宝宝们)
心碎小猫p
算法数据结构
一.冒泡排序:1.原理:相邻运算两两相比较,将大的向后移,第一轮全部两两比较完毕后,最大值就在最大索引处。依此类推,每轮都会找到一个"最大值",并将其置于当前轮次的最后位置,直到结束。2.具体思路:以下述列表为例:35472第一轮:第一次比较:位于0索引的数字3,将与位于1索引的数字5进行比较,数字5比数字3大,因此数字3和数字5的位置不需要改变。第二次比较:位于1索引的数字5和位于2索引的数字4
- 背包问题-动态规划算法(附带Python代码解析)
心碎小猫p
算法动态规划python
一.背包问题概述:给定n种物品和一个容量为capacity的背包,其中每一个物品的重量和价值已知。问:应该如何选择装入背包的物品,使得装入背包中的物品的总价值最大?二.分析过程:1.思路:对于每一个物品只有两种选择,第一种情况:装入当前物品;第二种情况:不装入当前物品。我们从第一个物品开始,将其重量和背包容量进行比较,如果比背包容量小,则选择将这个物品装入背包,记录它的价值(如果比背包容量大,忽略
- http 协议和 https 协议的区别是什么?
互联网之路.
知识点https
互联网各领域资料分享专区(不定期更新):Sheet正文HTTP(超文本传输协议)和HTTPS(安全超文本传输协议)的核心区别在于安全性,以下是两者的主要对比:1.协议与安全性HTTP:数据以明文形式传输,易被窃听、篡改或中间人攻击。HTTPS:通过SSL/TLS协议对数据进行加密,确保传输过程中的机密性和完整性,防止数据泄露或篡改。2.默认端口HTTP:使用80端口。HTTPS:使用443端口。3
- 逻辑回归分类python实例_Python逻辑回归原理及实际案例应用
Zcc四月
逻辑回归分类python实例
前言目录1.逻辑回归2.优缺点及优化问题3.实际案例应用4.总结正文在前面所介绍的线性回归,岭回归和Lasso回归这三种回归模型中,其输出变量均为连续型,比如常见的线性回归模型为:其写成矩阵形式为:现在这里的输出为连续型变量,但是实际中会有'输出为离散型变量'这样的需求,比如给定特征预测是否离职(1表示离职,0表示不离职).显然这时不能直接使用线性回归模型,而逻辑回归就派上用场了.1.逻辑回归引用
- 思迈特软件与海量数据库、红莲花安全浏览器完成兼容互认证
权lead er
数据库安全
近期,思迈特软件信创认证喜讯传来,思迈特商业智能与数据分析软件[简称:SmartbiInsight]V11在数据库、浏览器产品兼容互认取得新突破,SmartbiInsightV11分别同海量数据库G100管理系统[简称:VastbaseG100]V2.2及V3.0、红莲花安全浏览器V5.0实现产品兼容,再一次凸显了SmartbiInsight在产品性能、安全性、稳定性等方面的硬核实力,信创生态版图
- SpringSecurity系列——安全Http响应头day8-2(源于官网5.7.2版本)
简明编程
笔记#SpringSecurityJava学习安全httpjava
SpringSecurity系列——安全Http响应头day8-2(源于官网5.7.2版本)安全Http响应头默认的安全头默认包含的安全头自定义默认安全标头禁用默认安全头禁用所有安全头(完全无效)缓存控制默认的缓存控制响应头禁用默认安全头开启缓存控制禁用缓存控制(cacheControl)内容类型(Content-Type)禁用Content-TypeHSTS严格传输安全默认的标头默认的严格的传输
- Python的PyTorch+CNN深度学习技术在人脸识别项目中的应用
mosquito_lover1
python深度学习pytorchcnn
人脸识别技术是一种基于人脸特征进行身份识别的生物识别技术,其核心原理包括人脸检测、人脸对齐、特征提取、特征匹配、身份识别。一、应用场景安防:门禁、监控。金融:刷脸支付、身份验证。社交:自动标注、美颜。医疗:患者身份确认、情绪分析。二、关键技术深度学习:CNN在人脸检测、特征提取中表现优异。大数据:大规模数据集(如LFW、MegaFace)提升模型泛化能力。硬件加速:GPU、TPU等加速计算,提升实
- IDEA安装包(绿色版) IntelliJ全家桶(Min,Mac,Linux)
吃汤圆的抹香鲸
intellij-ideajavaideidea
目录一、核心价值定位1.1开发者选择逻辑1.2竞品对比优势二、环境配置规范2.1硬件基准要求2.2多版本管理方案三、效率革命性功能3.1智能编码体系3.2重构安全机制四、企业级开发适配4.1SpringBoot深度支持4.2微服务调试方案五、质量保障体系5.1静态检测配置5.2代码审查流程六、学习路径规划6.130天成长路线下载链接:https://pan.baidu.com/s/1cfkJf6Z
- PYTHON机器学习小项目教程:预测鸢尾花种类
jackispy
python机器学习人工智能
我们将使用经典的鸢尾花数据集来构建一个分类模型,该数据集包含150个样本,每个样本有四个特征:花萼长度、花萼宽度、花瓣长度和花瓣宽度。目标是根据这些特征预测鸢尾花的种类(山鸢尾、变色鸢尾或维吉尼亚鸢尾)。一、环境配置首先,确保你已经安装了必要的库。如:pandas、numpy等,命令如下所示pipinstallnumpypandasscikit-learnmatplotlib[-i镜像源网站]二、
- 对股票分析时要注意哪些主要因素?
会飞的奇葩猪
股票 分析 云掌股吧
众所周知,对散户投资者来说,股票技术分析是应战股市的核心武器,想学好股票的技术分析一定要知道哪些是重点学习的,其实非常简单,我们只要记住三个要素:成交量、价格趋势、振荡指标。
一、成交量
大盘的成交量状态。成交量大说明市场的获利机会较多,成交量小说明市场的获利机会较少。当沪市的成交量超过150亿时是强市市场状态,运用技术找综合买点较准;
- 【Scala十八】视图界定与上下文界定
bit1129
scala
Context Bound,上下文界定,是Scala为隐式参数引入的一种语法糖,使得隐式转换的编码更加简洁。
隐式参数
首先引入一个泛型函数max,用于取a和b的最大值
def max[T](a: T, b: T) = {
if (a > b) a else b
}
因为T是未知类型,只有运行时才会代入真正的类型,因此调用a >
- C语言的分支——Object-C程序设计阅读有感
darkblue086
applec框架cocoa
自从1972年贝尔实验室Dennis Ritchie开发了C语言,C语言已经有了很多版本和实现,从Borland到microsoft还是GNU、Apple都提供了不同时代的多种选择,我们知道C语言是基于Thompson开发的B语言的,Object-C是以SmallTalk-80为基础的。和C++不同的是,Object C并不是C的超集,因为有很多特性与C是不同的。
Object-C程序设计这本书
- 去除浏览器对表单值的记忆
周凡杨
html记忆autocompleteform浏览
&n
- java的树形通讯录
g21121
java
最近用到企业通讯录,虽然以前也开发过,但是用的是jsf,拼成的树形,及其笨重和难维护。后来就想到直接生成json格式字符串,页面上也好展现。
// 首先取出每个部门的联系人
for (int i = 0; i < depList.size(); i++) {
List<Contacts> list = getContactList(depList.get(i
- Nginx安装部署
510888780
nginxlinux
Nginx ("engine x") 是一个高性能的 HTTP 和 反向代理 服务器,也是一个 IMAP/POP3/SMTP 代理服务器。 Nginx 是由 Igor Sysoev 为俄罗斯访问量第二的 Rambler.ru 站点开发的,第一个公开版本0.1.0发布于2004年10月4日。其将源代码以类BSD许可证的形式发布,因它的稳定性、丰富的功能集、示例配置文件和低系统资源
- java servelet异步处理请求
墙头上一根草
java异步返回servlet
servlet3.0以后支持异步处理请求,具体是使用AsyncContext ,包装httpservletRequest以及httpservletResponse具有异步的功能,
final AsyncContext ac = request.startAsync(request, response);
ac.s
- 我的spring学习笔记8-Spring中Bean的实例化
aijuans
Spring 3
在Spring中要实例化一个Bean有几种方法:
1、最常用的(普通方法)
<bean id="myBean" class="www.6e6.org.MyBean" />
使用这样方法,按Spring就会使用Bean的默认构造方法,也就是把没有参数的构造方法来建立Bean实例。
(有构造方法的下个文细说)
2、还
- 为Mysql创建最优的索引
annan211
mysql索引
索引对于良好的性能非常关键,尤其是当数据规模越来越大的时候,索引的对性能的影响越发重要。
索引经常会被误解甚至忽略,而且经常被糟糕的设计。
索引优化应该是对查询性能优化最有效的手段了,索引能够轻易将查询性能提高几个数量级,最优的索引会比
较好的索引性能要好2个数量级。
1 索引的类型
(1) B-Tree
不出意外,这里提到的索引都是指 B-
- 日期函数
百合不是茶
oraclesql日期函数查询
ORACLE日期时间函数大全
TO_DATE格式(以时间:2007-11-02 13:45:25为例)
Year:
yy two digits 两位年 显示值:07
yyy three digits 三位年 显示值:007
- 线程优先级
bijian1013
javathread多线程java多线程
多线程运行时需要定义线程运行的先后顺序。
线程优先级是用数字表示,数字越大线程优先级越高,取值在1到10,默认优先级为5。
实例:
package com.bijian.study;
/**
* 因为在代码段当中把线程B的优先级设置高于线程A,所以运行结果先执行线程B的run()方法后再执行线程A的run()方法
* 但在实际中,JAVA的优先级不准,强烈不建议用此方法来控制执
- 适配器模式和代理模式的区别
bijian1013
java设计模式
一.简介 适配器模式:适配器模式(英语:adapter pattern)有时候也称包装样式或者包装。将一个类的接口转接成用户所期待的。一个适配使得因接口不兼容而不能在一起工作的类工作在一起,做法是将类别自己的接口包裹在一个已存在的类中。 &nbs
- 【持久化框架MyBatis3三】MyBatis3 SQL映射配置文件
bit1129
Mybatis3
SQL映射配置文件一方面类似于Hibernate的映射配置文件,通过定义实体与关系表的列之间的对应关系。另一方面使用<select>,<insert>,<delete>,<update>元素定义增删改查的SQL语句,
这些元素包含三方面内容
1. 要执行的SQL语句
2. SQL语句的入参,比如查询条件
3. SQL语句的返回结果
- oracle大数据表复制备份个人经验
bitcarter
oracle大表备份大表数据复制
前提:
数据库仓库A(就拿oracle11g为例)中有两个用户user1和user2,现在有user1中有表ldm_table1,且表ldm_table1有数据5千万以上,ldm_table1中的数据是从其他库B(数据源)中抽取过来的,前期业务理解不够或者需求有变,数据有变动需要重新从B中抽取数据到A库表ldm_table1中。
- HTTP加速器varnish安装小记
ronin47
http varnish 加速
上午共享的那个varnish安装手册,个人看了下,有点不知所云,好吧~看来还是先安装玩玩!
苦逼公司服务器没法连外网,不能用什么wget或yum命令直接下载安装,每每看到别人博客贴出的在线安装代码时,总有一股羡慕嫉妒“恨”冒了出来。。。好吧,既然没法上外网,那只能麻烦点通过下载源码来编译安装了!
Varnish 3.0.4下载地址: http://repo.varnish-cache.org/
- java-73-输入一个字符串,输出该字符串中对称的子字符串的最大长度
bylijinnan
java
public class LongestSymmtricalLength {
/*
* Q75题目:输入一个字符串,输出该字符串中对称的子字符串的最大长度。
* 比如输入字符串“google”,由于该字符串里最长的对称子字符串是“goog”,因此输出4。
*/
public static void main(String[] args) {
Str
- 学习编程的一点感想
Cb123456
编程感想Gis
写点感想,总结一些,也顺便激励一些自己.现在就是复习阶段,也做做项目.
本专业是GIS专业,当初觉得本专业太水,靠这个会活不下去的,所以就报了培训班。学习的时候,进入状态很慢,而且当初进去的时候,已经上到Java高级阶段了,所以.....,呵呵,之后有点感觉了,不过,还是不好好写代码,还眼高手低的,有
- [能源与安全]美国与中国
comsci
能源
现在有一个局面:地球上的石油只剩下N桶,这些油只够让中国和美国这两个国家中的一个顺利过渡到宇宙时代,但是如果这两个国家为争夺这些石油而发生战争,其结果是两个国家都无法平稳过渡到宇宙时代。。。。而且在战争中,剩下的石油也会被快速消耗在战争中,结果是两败俱伤。。。
在这个大
- SEMI-JOIN执行计划突然变成HASH JOIN了 的原因分析
cwqcwqmax9
oracle
甲说:
A B两个表总数据量都很大,在百万以上。
idx1 idx2字段表示是索引字段
A B 两表上都有
col1字段表示普通字段
select xxx from A
where A.idx1 between mmm and nnn
and exists (select 1 from B where B.idx2 =
- SpringMVC-ajax返回值乱码解决方案
dashuaifu
AjaxspringMVCresponse中文乱码
SpringMVC-ajax返回值乱码解决方案
一:(自己总结,测试过可行)
ajax返回如果含有中文汉字,则使用:(如下例:)
@RequestMapping(value="/xxx.do") public @ResponseBody void getPunishReasonB
- Linux系统中查看日志的常用命令
dcj3sjt126com
OS
因为在日常的工作中,出问题的时候查看日志是每个管理员的习惯,作为初学者,为了以后的需要,我今天将下面这些查看命令共享给各位
cat
tail -f
日 志 文 件 说 明
/var/log/message 系统启动后的信息和错误日志,是Red Hat Linux中最常用的日志之一
/var/log/secure 与安全相关的日志信息
/var/log/maillog 与邮件相关的日志信
- [应用结构]应用
dcj3sjt126com
PHPyii2
应用主体
应用主体是管理 Yii 应用系统整体结构和生命周期的对象。 每个Yii应用系统只能包含一个应用主体,应用主体在 入口脚本中创建并能通过表达式 \Yii::$app 全局范围内访问。
补充: 当我们说"一个应用",它可能是一个应用主体对象,也可能是一个应用系统,是根据上下文来决定[译:中文为避免歧义,Application翻译为应
- assertThat用法
eksliang
JUnitassertThat
junit4.0 assertThat用法
一般匹配符1、assertThat( testedNumber, allOf( greaterThan(8), lessThan(16) ) );
注释: allOf匹配符表明如果接下来的所有条件必须都成立测试才通过,相当于“与”(&&)
2、assertThat( testedNumber, anyOf( g
- android点滴2
gundumw100
应用服务器android网络应用OSHTC
如何让Drawable绕着中心旋转?
Animation a = new RotateAnimation(0.0f, 360.0f,
Animation.RELATIVE_TO_SELF, 0.5f, Animation.RELATIVE_TO_SELF,0.5f);
a.setRepeatCount(-1);
a.setDuration(1000);
如何控制Andro
- 超简洁的CSS下拉菜单
ini
htmlWeb工作html5css
效果体验:http://hovertree.com/texiao/css/3.htmHTML文件:
<!DOCTYPE html>
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<title>简洁的HTML+CSS下拉菜单-HoverTree</title>
- kafka consumer防止数据丢失
kane_xie
kafkaoffset commit
kafka最初是被LinkedIn设计用来处理log的分布式消息系统,因此它的着眼点不在数据的安全性(log偶尔丢几条无所谓),换句话说kafka并不能完全保证数据不丢失。
尽管kafka官网声称能够保证at-least-once,但如果consumer进程数小于partition_num,这个结论不一定成立。
考虑这样一个case,partiton_num=2
- @Repository、@Service、@Controller 和 @Component
mhtbbx
DAOspringbeanprototype
@Repository、@Service、@Controller 和 @Component 将类标识为Bean
Spring 自 2.0 版本开始,陆续引入了一些注解用于简化 Spring 的开发。@Repository注解便属于最先引入的一批,它用于将数据访问层 (DAO 层 ) 的类标识为 Spring Bean。具体只需将该注解标注在 DAO类上即可。同时,为了让 Spring 能够扫描类
- java 多线程高并发读写控制 误区
qifeifei
java thread
先看一下下面的错误代码,对写加了synchronized控制,保证了写的安全,但是问题在哪里呢?
public class testTh7 {
private String data;
public String read(){
System.out.println(Thread.currentThread().getName() + "read data "
- mongodb replica set(副本集)设置步骤
tcrct
javamongodb
网上已经有一大堆的设置步骤的了,根据我遇到的问题,整理一下,如下:
首先先去下载一个mongodb最新版,目前最新版应该是2.6
cd /usr/local/bin
wget http://fastdl.mongodb.org/linux/mongodb-linux-x86_64-2.6.0.tgz
tar -zxvf mongodb-linux-x86_64-2.6.0.t
- rust学习笔记
wudixiaotie
学习笔记
1.rust里绑定变量是let,默认绑定了的变量是不可更改的,所以如果想让变量可变就要加上mut。
let x = 1; let mut y = 2;
2.match 相当于erlang中的case,但是case的每一项后都是分号,但是rust的match却是逗号。
3.match 的每一项最后都要加逗号,但是最后一项不加也不会报错,所有结尾加逗号的用法都是类似。
4.每个语句结尾都要加分