网络入门-三层架构综合实验
238、三层架构的综合实验
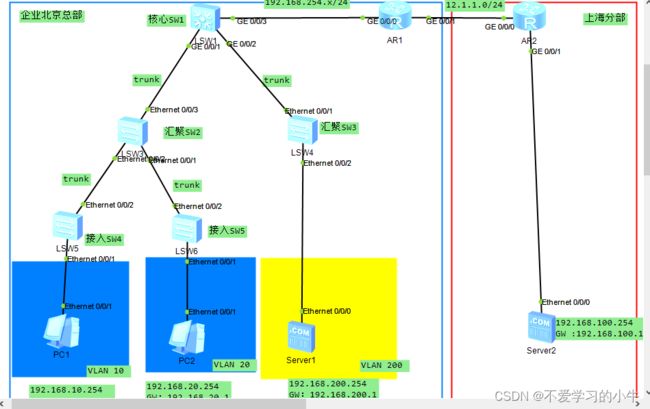
实验topo:
实验要求:
①用户的网关配置在核心交换机上;
②企业内网划分多个VLAN,减少广播域大小,提高网络稳定性;
③所有设备在任何位置均可以Telnet远程管理;
④出口配置NAT
⑤ 所有用户皆可自动获取IP地址
⑥企业总部和分部采用ppp广域网链路连接,并采用CHAP对链路进行验证;
⑦企业总部和分部采用OSPF路由协议连接;
一、配置DHCP服务器,让每个PC都能自动获取IP地址,并将网关配置到核心交换机上:
#
vlan batch 10 20 200
VLAN10
#
#
ip pool vlan10
gateway-list 192.168.10.1
network 192.168.10.0 mask 255.255.255.0
dns-list 192.168.10.1 8.8.8.8
#
#
interface Vlanif10
ip address 192.168.10.1 255.255.255.0
dhcp select global
#
VLAN20
#
ip pool vlan20
gateway-list 192.168.20.1
network 192.168.20.0 mask 255.255.255.0
dns-list 192.168.20.1 8.8.8.8
#
interface Vlanif20
ip address 192.168.20.1 255.255.255.0
dhcp select global
#
VLAN200
#
ip pool vlan200
gateway-list 192.168.200.1
network 192.168.200.0 mask 255.255.255.0
dns-list 192.168.200.1 8.8.8.8
#
interface Vlanif200
ip address 192.168.200.1 255.255.255.0
dhcp select global
#
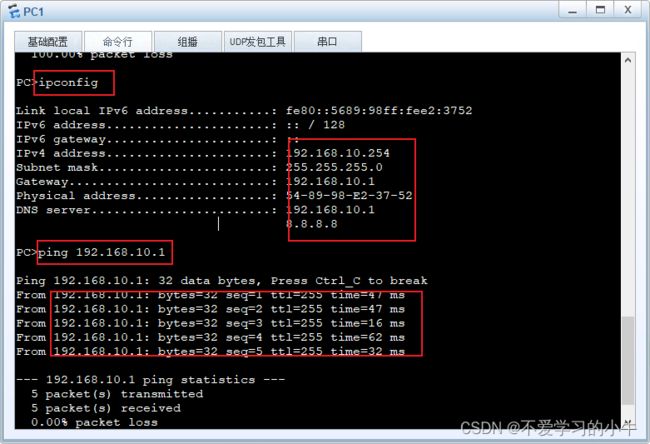
分别查看各PC的地址分配情况,以及连通性:
PC1
PC2 :
二、划分VLAN,将PC1 划分至VLAN 10 ,PC2划分至VLAN 20 PC3 划分至VLAN 200,其余的口打TRUNK;
SW1 :
#
vlan batch 10 20 200 254
#
#
interface Vlanif1
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 2 to 4094
#
SW2:
#
vlan batch 10
#
#
interface MEth0/0/1
#
interface Ethernet0/0/1
port link-type access
port default vlan 10
#
interface Ethernet0/0/2
port link-type access
port default vlan 20
#
interface Ethernet0/0/3
port link-type trunk
port trunk allow-pass vlan 2 to 4094
#
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 254
#
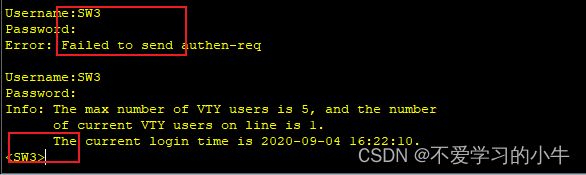
SW3:
#
vlan 200
#
#
interface Ethernet0/0/1
port link-type access
port default vlan 200
#
interface Ethernet0/0/2
port link-type trunk
port trunk allow-pass vlan 2 to 4094
#
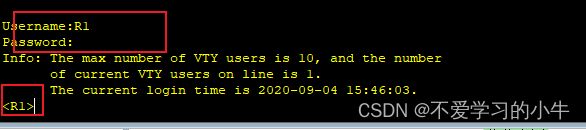
三、配置TELNET服务,让每一台设备都能被远程:
SW1:
#
aaa
local-user sw1 password cipher L^>),1:/2!ANZPO3JBXBHA!!
local-user sw1 privilege level 3
local-user sw1 service-type telnet
#
#
user-interface vty 0 4
authentication-mode aaa
#
SW2:
#
aaa
local-user sw2 password cipher L^>),1:/2!ANZPO3JBXBHA!!
local-user sw2 privilege level 3
local-user sw2 service-type telnet
#
#
user-interface vty 0 4
authentication-mode aaa
#
SW3:
#
aaa
local-user sw3 password cipher L^>),1:/2!ANZPO3JBXBHA!!
local-user sw3 privilege level 3
local-user sw3 service-type telnet
#
#
user-interface vty 0 4
authentication-mode aaa
#
R1:
#
aaa
local-user r1 password cipher _zbq@*N-\Pani^>"qh^;E*l#
local-user r1 privilege level 3
local-user r1 service-type telnet
#
#
user-interface vty 0 4
authentication-mode aaa
#
R2:
#
aaa
local-user r2 password cipher X9NFEG0TU%ajUn1vMEIB~.P#
local-user r2 privilege level 3
local-user r2 service-type telnet
#
#
user-interface vty 0 4
authentication-mode aaa
#
创建管理VLAN 999 :
SW 1:
#
vlan 999
int vlan 999
ip add 192.168.255.1 24
#
ip route-stacic 0.0.0.0 0 192.168.255.1 配置一条回包路由
#
SW2:
#
vlan 999
int vlan 999
ip add 192.168.255.1 24
#
ip route-stacic 0.0.0.0 0 192.168.255.1 配置一条回包路由
#
SW3:
#
vlan 999
int vlan 999
ip add 192.168.255.1 24
#
ip route-stacic 0.0.0.0 0 192.168.255.1 配置一条回包路由
#
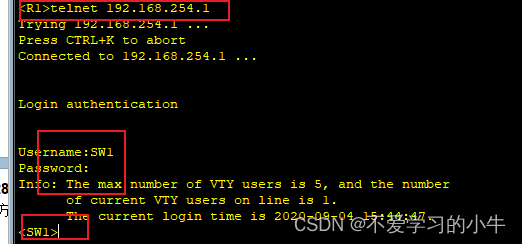
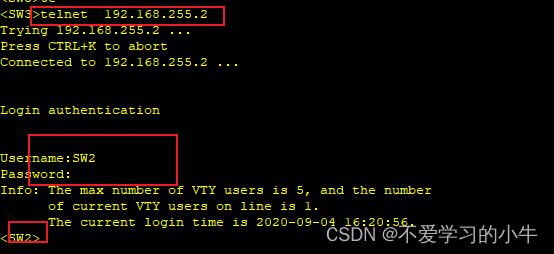
远程登录测试:
SW1:
SW2:
SW3:
R1:
四、出口配置NAT
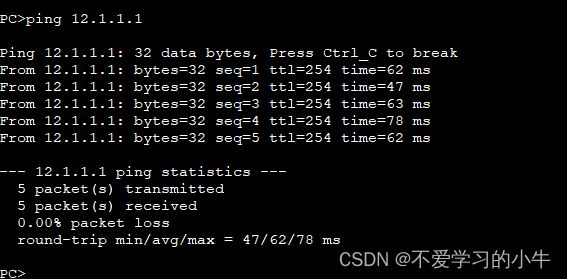
配置静态路由,打通内部网络:
SW1 :ip route-static 0.0.0.0 0 192.168.254.2
R1:
ip route-static 192.168.0.0 255.255.0.0 192.168.254.1 配置一条回包路由
ip route-static 0.0.0.0 0.0.0.0 12.1.1.6;将出口的所有的数据丢给运营商
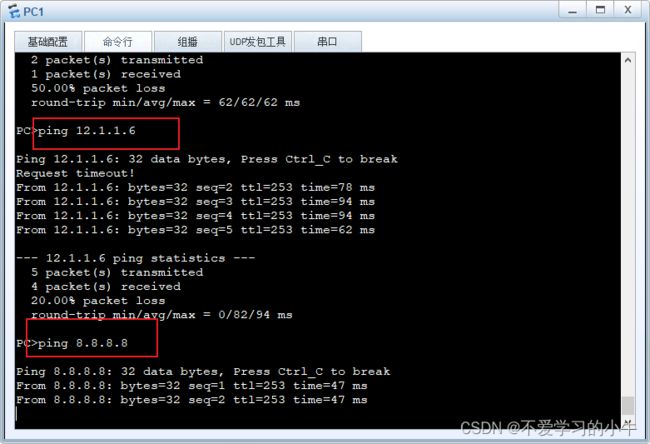
测试内网连通性:
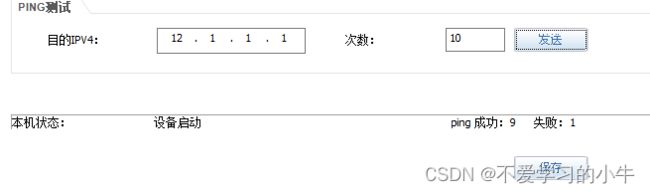
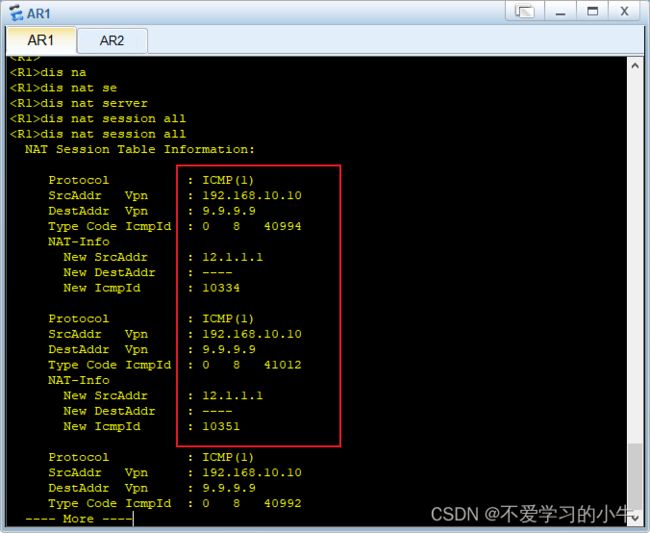
配置NAT,让内网与外网联通:
由于此处的内网有多个网段,所以我们使用easy ip,让多个内网地址段可以访问外网;
匹配内网地址段:
#
acl number 2000
rule 5 permit source 192.168.0.0 0.0.255.255
#
进入出接口,调用ACL
#
interface S4/0/0
nat outbound 2000
#
测试:
五、配置ppp认证:
认证端:
创建一个用户,用途为ppp认证:
#
aaa
local-user r1 password cipher %$%$TQX77;h$r/NiN(#d+4'!'D-^%$%$
local-user r1 service-type ppp
#
指定ppp认证的模式为:chap
#
interface Serial4/0/0
link-protocol ppp
ppp authentication-mode chap
#
客户端:
#
interface Serial4/0/0
link-protocol ppp
ppp chap user r1
ppp chap password simple R1
#
测试接口是否up:
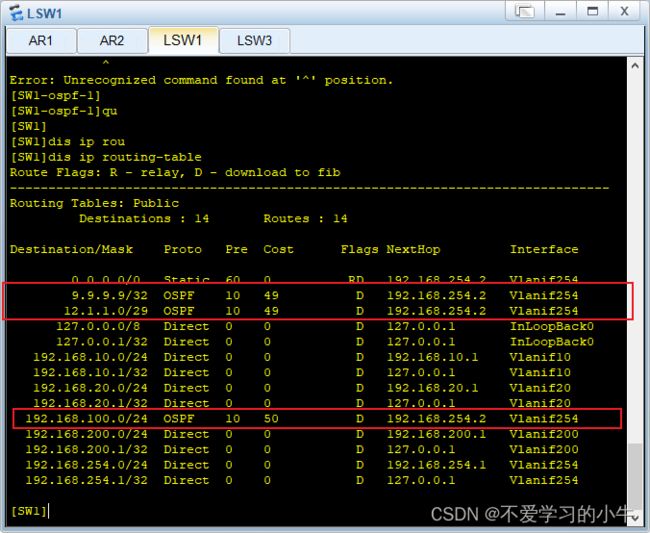
六、企业总部和分部采用OSPF路由协议连接;
各个设备宣告出自己的直连网段:
SW1 :
#
ospf 1
area 0.0.0.0
network 192.168.10.0 0.0.0.255
network 192.168.20.0 0.0.0.255
network 192.168.200.0 0.0.0.255
network 192.168.254.0 0.0.0.255
#
R1:
#
ospf 1
area 0.0.0.0
network 12.1.1.0 0.0.0.7
network 192.168.254.0 0.0.0.255
#
R2:
#
ospf 1
area 0.0.0.0
network 9.9.9.0 0.0.0.255
network 12.1.1.0 0.0.0.7
network 192.168.100.0 0.0.0.255
#
查看路由表: